A typical campaign attempting to trick users into installing Potentially Unwanted Software (PUA), would usually consist of a single social engineering vector, which on the majority of cases would represent something in the lines of a catchy “Play Now/Missing Video Plugin” type of advertisement. Not the one we’ll discuss in this blog post. Relying on deceptive “visual social engineering” practices, a popular French torrent portal is knowingly — the actual directory structure explicitly says /fakeplayer — enticing users into installing the BubbleDock/Downware/DownloadWare PUA. What kind of social engineering tactics is the portal relying on? Let’s find out.
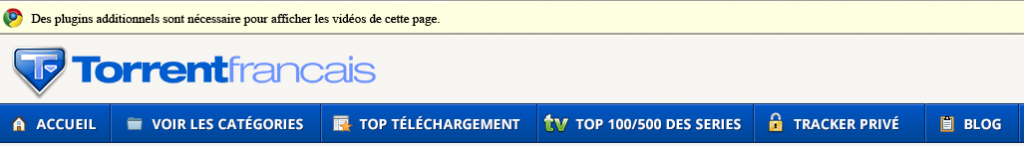
Sample screenshot of the fake and localized to French “Missing Plugin” presented on the top of the page:
As you can see in the attached screenshot, the portal attempts to convince the user that he/she is missing a plugin required to display the content. Once users attempt to download it by clicking on the link, they’re automatically exposed to the executable hosted within One Install’s affiliate based type of revenue sharing platform.
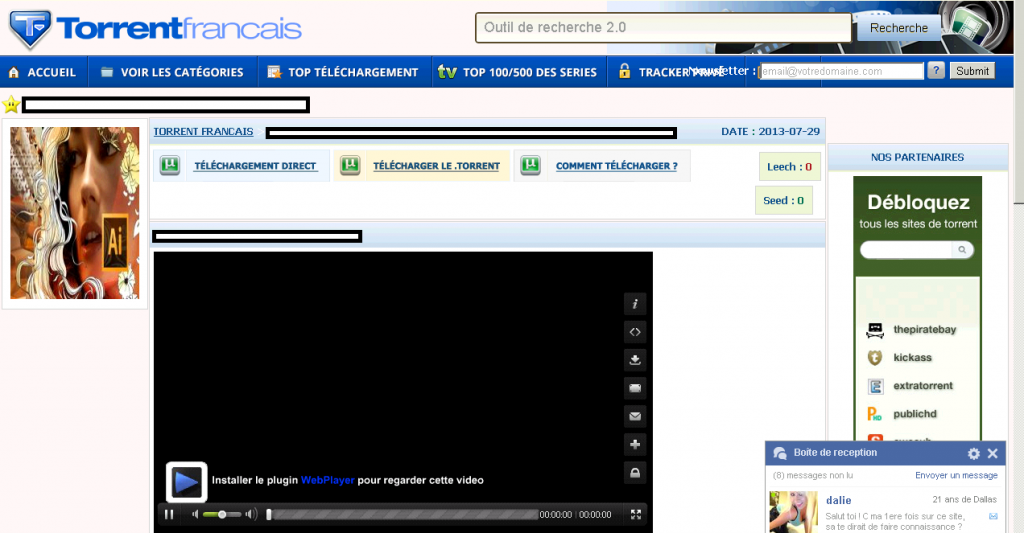
Sample screenshots of the fake WebPlugin video window:
The second “visual social engineering” vector relies on the ubiquitous for such type of social engineering campaigns, “Install the WebPlayer plugin” type of fake flash content.
PUA located at: download.oneinstaller.com/installer/?iid=270&nsoft=14 (affiliate network participant at the One Install network)
Detection rate for the PUA: MD5: 14de165a402ea6e13282c1195c24290f – detected by 8 out of 47 antivirus scanners as NSIS:Adware-KQ [PUP]; Adware.Downware.1265; Win32/AdWare.DownloadWare.I; BubbleDock (fs)
Once executed, the sample phones back to the following domains, where it not just obtains the legitimate Adobe Flash Player, but also, drops additional PUAs on the hosts of socially engineered users:
stats.oinst.com – 93.189.35.66
cdninst.com – 109.70.132.26
app.updatesafe.net – 46.232.206.17
ads.oneinstaller.com – 93.189.35.51
media.oneinstaller.com – 109.70.132.26
d.delivery49.com – 166.78.35.128
install.xaven.info – 70.186.131.70
wpc.0952.edgecastcdn.net – 68.232.34.163
hxxp://www.808116.com – 50.97.129.8
ajax.googleapis.com – 74.125.136.95
cdn.delivery49.com – 77.67.4.16
counter.d.delivery49.com – 54.243.81.17
media.vitjvitj.com – 93.189.32.145
hxxp://www.uplstatsone.com – 93.189.33.84
hxxp://www.282208.com – 174.36.200.167
stats.srvmystats.com – 176.32.99.220
csc3-2010-crl.verisign.com – 23.36.149.163
get.adobe.com – 192.150.16.58
www.googletagservices.com – 74.125.136.156
partner.googleadservices.com – 74.125.136.156
pubads.g.doubleclick.net – 74.125.136.154
pagead2.googlesyndication.com – 74.125.136.154
crl.verisign.com – 23.36.149.163
www.adobetag.com – 23.66.241.169
dlmping2.adobe.com – 88.221.216.105
stats.adobe.com – 66.117.29.34
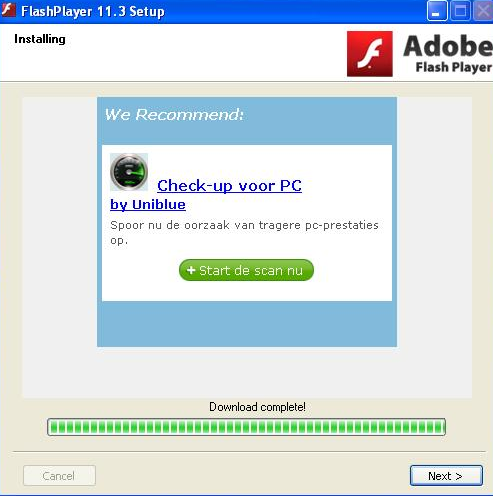
Sample screenshots of the installation:
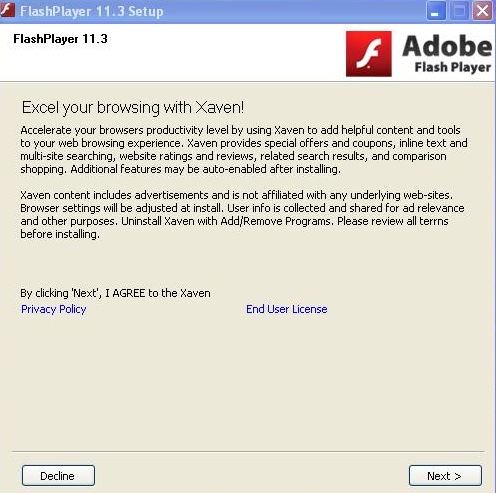
It also downloads and installs the following related Potentially Unwanted Applications (PUAs):
cdninst.com/offers/Mobogenie/Mobogenie.exe – MD5: a99dac9961a6ea4b50009e6485badb19 – detected by 1 out of 46 antivirus scanners as Trojan.Win32.Generic!SB.0
cdninst.com/offers/V9/Qone8.exe – MD5: f06c4455c740b192fd37cee9501327f2 – detected by 19 out of 47 antivirus scanners as Trojan.Win32.StartPage.choy; Elex Installer (fs)
cdninst.com/offers/SoftwareUpdater/SoftwareUpdater.exe – MD5: 80c3202212cef845931452fede347ee1 – detected by 22 out of 46 antivirus scanners as Trojan-Downloader.Win32.Genome.ffcs; PUP.Optional.Onekit.A
cdninst.com/offers/QuickShare/QuickShare.exe – MD5: e6f281b58cf026716a66098189595bc4 – detected by 4 out of 46 antivirus scanners as Adware.Win32.Linkury.83; PUP.Optional.QuickShare.A
cdninst.com/offers/Okitspace/Okitspace.exe – MD5: 2c908d624618f70304574f56c6dd73e6 23 out of 47 antivirus scanners as Trojan.Win32.MSIL.BrowserProtectIU.A
cdninst.com/offers/Diamonddata/Xaven.exe – MD5: fedad72d67c0c4cf7dcf1401a1421bf3 – detected by 5 out of 47 antivirus scanners as Win32/BrowseFox.C
app.updatesafe.net/u/v122/TubeSing_1060-2015_v122.exe – MD5: c074d4c0bde7e63d5f2330d7b0c4fd36 – detected by 3 out of 47 antivirus scanners as Trojan.Crossrider.10; PUP.Optional.Tubesing
Webroot SecureAnywhere users are proactively protected from these PUAs.