Telephony Denial of Service Attacks (TDoS) continue representing a growing market segment within the Russian/Eastern European underground market, with more vendors populating it with propositions for products and services aiming to disrupt the phone communications of prospective victims. From purely malicious in-house infrastructure — dozens of USB hubs with 3G USB modems using fraudulently obtained, non-attributable SIM cards — abuse of legitimate infrastructure, like Skype, ICQ, a mobile carrier’s legitimate service functionality, or compromised accounts of SIP account owners, the market continues growing to the point where even Distributed Denial of Service Attack (DDoS) providers start ‘vertically integrating’.
A new, commercially available multi-threaded SIP-based TDoS tool released by what appears to be an experienced TDoS vendor that’s also offering managed TDoS services, is prone to empower not just lone attackers, but also, potential new vendors who’d use the tool as a primarily vehicle for the the future growth of their business model. Let’s profile the tool, discuss its features, as well as what might have prompted the vendor of managed TDoS services to start selling copies of it, instead of exclusively using it in-house.
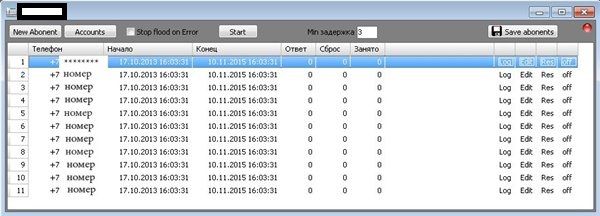
Sample screenshots of the newly released TDoS tool:
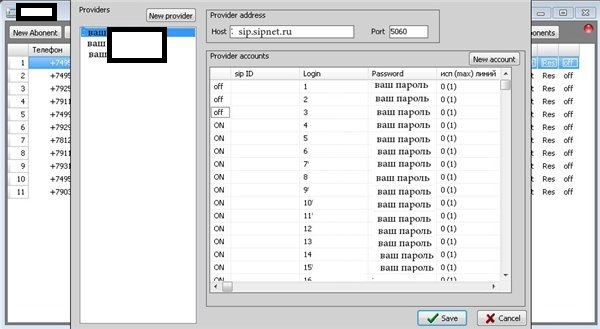
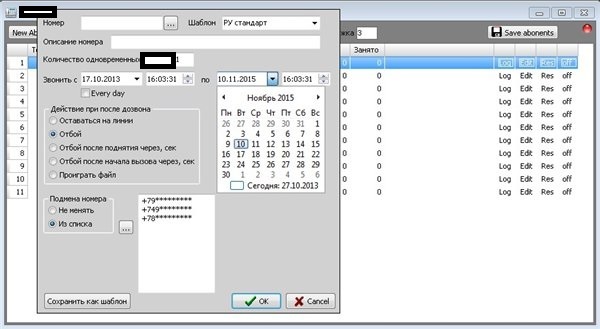
Next to multi-threading, simultaneous use/abuse of multiple compromised/legitimate accounts at multiple SIP providers, the tools also has a cron-like type of scheduling for a particular attack allowing queuing of campaigns and accepting multiple orders at a time. The price? 10,000 rubles ($304.92), including a hardware ID enabled type of license for a single PC. The tool is just the tip of the iceberg of TDoS products/services offered by the same vendor, and we believe that it’s been publicly pitched in an attempt by the vendor to generate more revenue, while preserving the actual ‘know-how’, in-house type of custom-coded TDoS tools, the ones primarily driving its business model.
Sample screenshot of the actual TDoS equipment operated by the vendor:

We believe that the Russian/Eastern European TDoS market would continue flourishing, with more vendors serving the growing demand for such type of services. As we’ve already seen in the past, they are known to have been directly used against emergency phone lines, a modern day’s alternative to perhaps the first known such case, namely, the 911/chode worm (2000).