We’ve just intercepted a currently circulating malicious spam campaign impersonating WhatsApp — yet again — in an attempt to trick its users into thinking that they’ve received a voice mail. Once socially engineered users execute the malicious attachment found in the fake emails, their PCs automatically join the botnet operated by the cybercriminal(s) behind the campaign.
Sample screenshot of the spamvertised malicious email:
Detection rate for the spamvertised attachment: MD5: 41ca9645233648b3d59cb52e08a4e22a – detected by 10 out of 47 antivirus scanners as TrojanDownloader:Win32/Kuluoz.D.
Once executed, it phones back to:
hxxp://103.4.18.215:8080/460326245047F2B6E405E92260B09AA0E35D7CA2B1
70.32.79.44
84.94.187.245
172.245.44.180
103.4.18.215
172.245.44.2
We’re also aware of the following malicious MD5s that are known to have phoned back to the same C&C servers as well:
MD5: 4014d1ee9e038b312dfcebf58f84968f
MD5: b82c2a96c5b3deccb46825507026ec39
MD5: 210096af9d8049bf3bae51d000c2ab76
MD5: e1b68d32e92bddb356a9917ea8e07e83
MD5: a5fb88ee735eab458bcbff287e36d590
MD5: c8b9b6e0a3257130e5842dd0840577c9
MD5: 38fc3178363b9d16174cc1565745d57f
MD5: bf5bdca7ef67b9c85a4413a8126ecb22
MD5: 53e568fe21ef96918853bc8404fef458
MD5: 3471d59f6f99f5676714cfac595e2aad
MD5: 91ade7d94244104d8cd6fc26be839c62
MD5: 40cb1f0111b4f4c8136404d4d351ceb5
MD5: 9c122673e98a487f8cd65746f03237aa
MD5: 7d53d47982fd62a37009b9a3e5fad42f
MD5: 2226cf5ead414b156e0b8b99f761ef83
Webroot SecureAnywhere users are proactively protected from these threats.







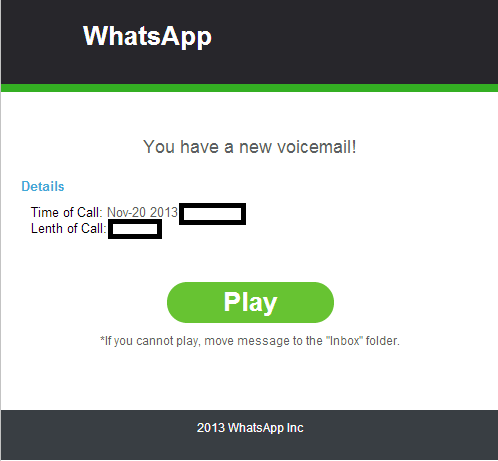
I have clicked the PLAY link button but I never clicked anything on the website that was opened or downloaded anything or entered any info… Will this still affect me? Should I change my gmail’s password? I am using a PC (Windows 7) when I clicked the link.
X0X0 Are you thinking that your machine is infected? Be sure to clear out your Temporary Internet Files and Cache within your browser if you have small performance issues.
is there any thing i can do if i’ve clicked on Win 7 machine other than clearing Temp internet data to save laptop from this virus?