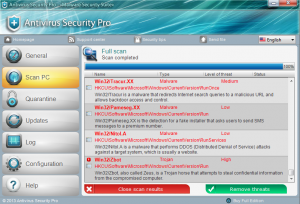
Recently we heard of a rogue fake antivirus that takes screenshots and webcam images in an attempt to further scare you into succumbing to it’s scam. We gathered a sample and sure enough, given some time it will indeed use the webcam and take a picture of what’s in front of the camera at that time. This variant is called “Antivirus Security Pro” and it’s as nasty as you can get.
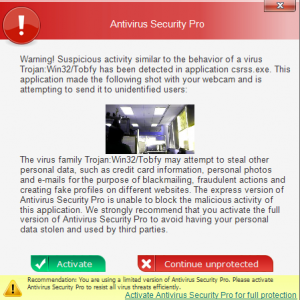
The rogue locks down any of the Advanced Boot Options: Safe Mode, Safe mode with Networking, Safe mode with Command prompt, directory services restore mode, ect. As soon as these are picked the computer will just restart back into normal mode where all executables are flagged as malicious. If you don’t purchase the scam in a few minutes it will take a picture with the web cam and then warn you that [insert name of good process].exe is “malicious” and attempting to send it to unidentified users. This is a really impressive step in social engineering to scare people and I’m sure has increased the percentage of people who pay out to the scam.
However, this is false and there is no trace of the webcam images being sent anywhere. The only network traffic this Rogue has is during initial drop to download all of its components.
Removal
If you have Webroot SecureAnywhere installed then not to worry, this virus should be blocked in real time as soon as it is written to your hard drive; the only notification you’ll receive is a notice that it was quarantined.
However, removing this virus once it has infected you is a little trickier without the comforts of the safe modes. Those of you that try system restore, you’ll notice that this virus disables it. All the file does is disable System Restore. It does not delete any restore points so you can just turn it back on and restore to a previous point. To turn on System restore: Click Start > Right click computer > select properties > Click System protection > Select your OS Drive (Typically C:) > Click Configure > Check “Restore system settings and previous version of files.” Please note that once you restore to a previous point only the registry entries are going to be removed, so although the virus no longer starts up when your computer does, you will still have to manually delete the files.
Location of Files:
%CommonAppData%\”random name”\
%CommonAppData%\”random name”\DD1
%CommonAppData%\”random name”\”random name”.exe
%CommonAppData%\”random name”\”random name”.exe.manifest
%CommonAppData%\”random name”\”random name”.ico
%CommonAppData%\”random name”\”random name”kassgxDq.in
%CommonAppData%\”random name”\”random name”kassgxDq.lg
%CommonAppData% = C:\Documents and Settings\All Users\Application Data\ in Windows XP and C:\ProgramData\ in Vista/7/8
Webroot support is always more than happy to help with removal and any questions regarding infections.
Webroot SecureAnywhere users are proactively protected from these threats.







Thank You for this great post, this is really helpful to find out about how we software going to do these listed activities. I also use antiviruses like avast, avg, optimo defender, etc to detect it and they also helpful in other way. Really Thank You
Thank you for such a great article. It is nice post.
Antivirus is very important specially for the machine on witch we used internet or save important data to kept safe.
<a href=”http://tip-for-computer.blogspot.com/2012/01/gaming-computer-purchasing-tips.html”>Gaming Computer purchasing Tips </a>