For years, whenever I needed a fresh sample of pharmaceutical scams, I always sampled the Web sites of major educational institutions, where a thriving ecosystem relying on compromised Web shells, continues to enjoy the high page ranks of the affected Web sites for blackhat SEO (search engine optimization) purposes. How are cybercriminals managing these campaigns? What type of tools and tactics do they use? In a cybercrime ecosystem that has logically migrated to Web-based platforms for a variety of reasons over the last couple of years, there are still those who’re keeping it old school, by releasing host-based DIY cybercrime-friendly applications. In this post, I’ll discuss a commercially available Windows-based compromised/hacked Web shells management application.
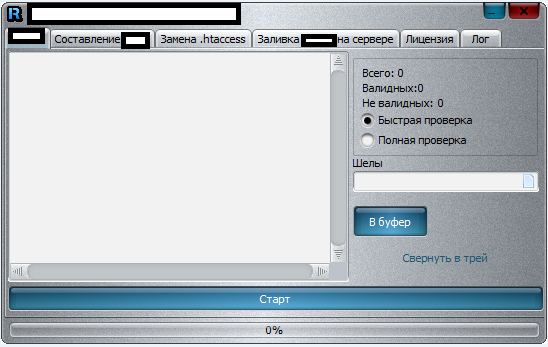
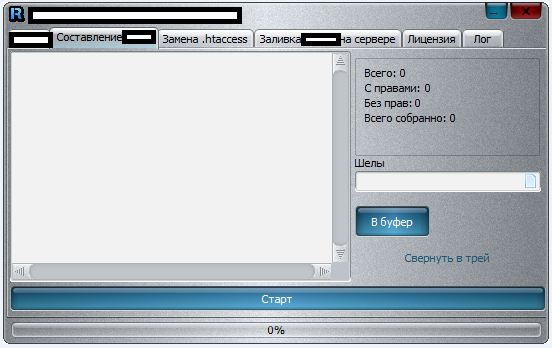
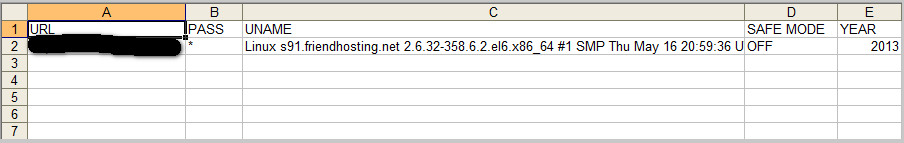
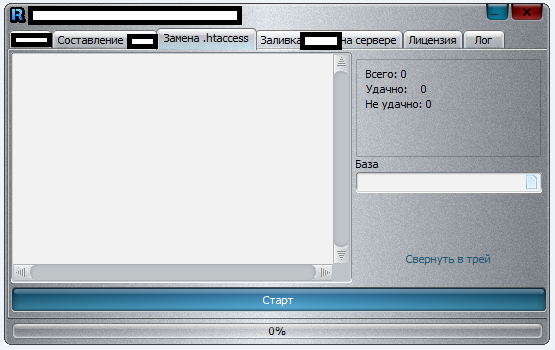
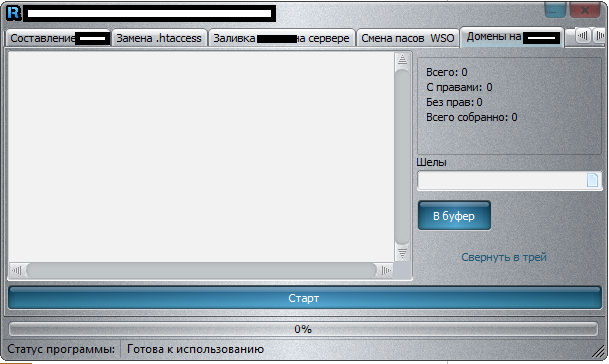
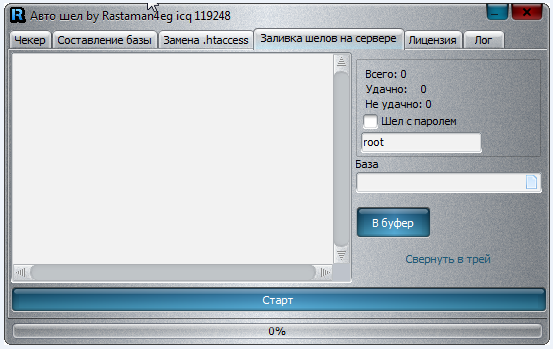
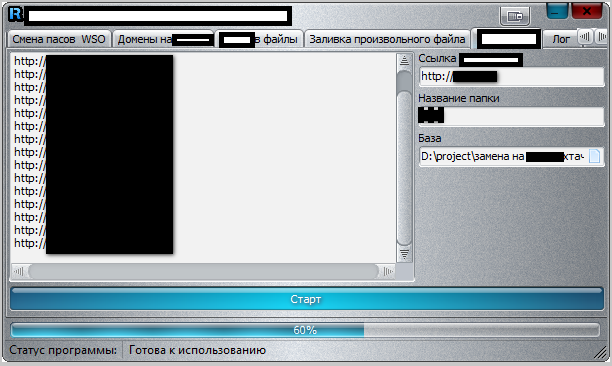
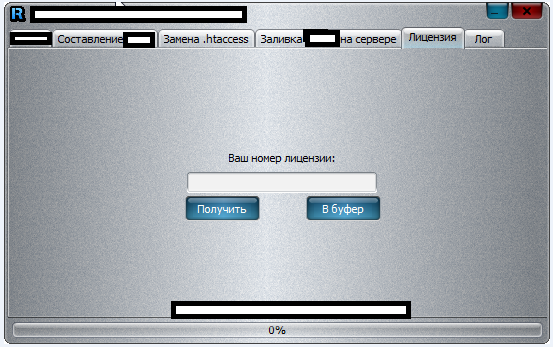
Sample screenshots of the application in action:
Among the tool’s unique features, is the ability to check the validity of the supplied compromised/hacked shells, various modification options like changing passwords and updating the redirectors, as well as the ability to change .htaccess. Compared to a similar application, which we profiled in July, 2013, we believe that in its current form, the tool profiled in this post doesn’t have the capacity to be utilized for widespread, hard-to-detected mass abuse of compromised/hacked shells.
In 2013, insecurely configured Web applications susceptible to remote exploitation for fraudulent and malicious purposes — think Remote File Inclusion — the active data mining of a botnet’s infected population, as well as good old fashioned brute-forcing attempts, continue supplying the market segment for compromised/hacked Web shells, with new accounting data, most commonly abused in a typical blackhat SEO style, with the actual campaigns monetized through an affiliate network. We expect that this trend will continue, in combination with what we believe is a resurrection of a proven process for monetizing compromised access to a legitimate Web site, namely, cybercrime-friendly traffic exchanges.