The rise of boutique cybercrime-friendly E-shops, which we’ve extensively profiled in our “A Peek Inside a Boutique Cybercrime-Friendly E-Shop” series, continues further expanding as a market segment within the underground marketplace. Driven by the proliferation of public/commercially obtainable DIY (do it yourself) type of malware/botnet generating tools along side the ongoing standardization of the monetization process offered by opportunistic cybercriminals acting as intermediaries between those possessing the fraudulently obtained assets and their prospective customers, the market segment is prone to expand.
Having already profiled a managed hosting service, empowering novice cybercriminals possessing compromised/hacked accounting information with efficient ways to monetize the stolen data, we continue finding factual evidence that further confirms an ongoing standardization of the monetization process. In this post, I’ll discuss a market leading managed hosting service that is currently hosting 2500+ boutique E-shops offering access to a vast amount of compromised/hacked accounting data, with hosting services, through a convenient Web-based E-shop management interface.
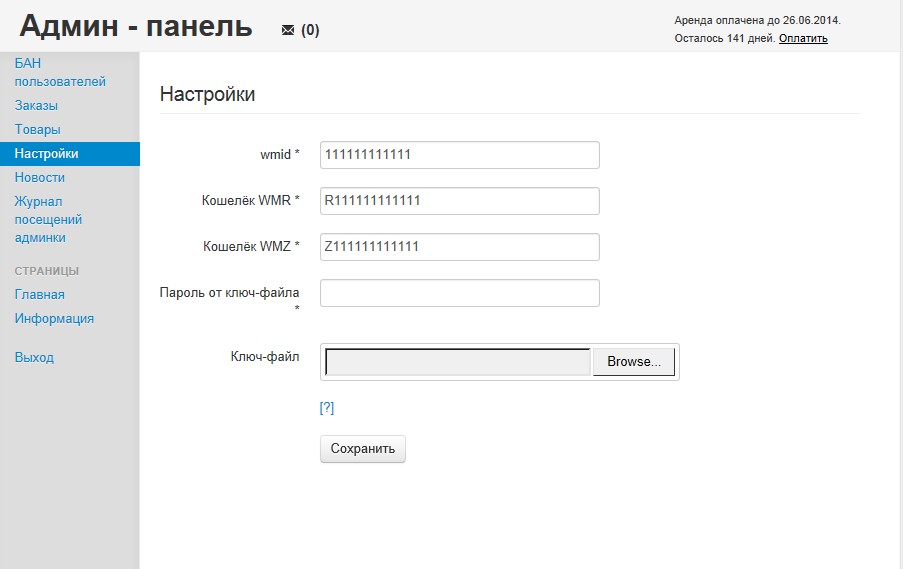
Sample screenshot of the entry page for the managed cybercrime-friendly managed E-shop hosting service:
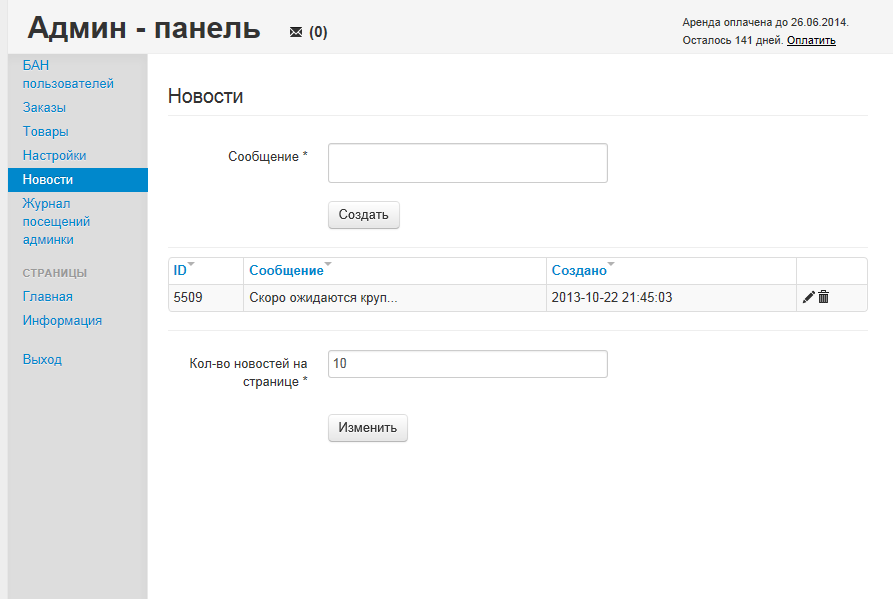
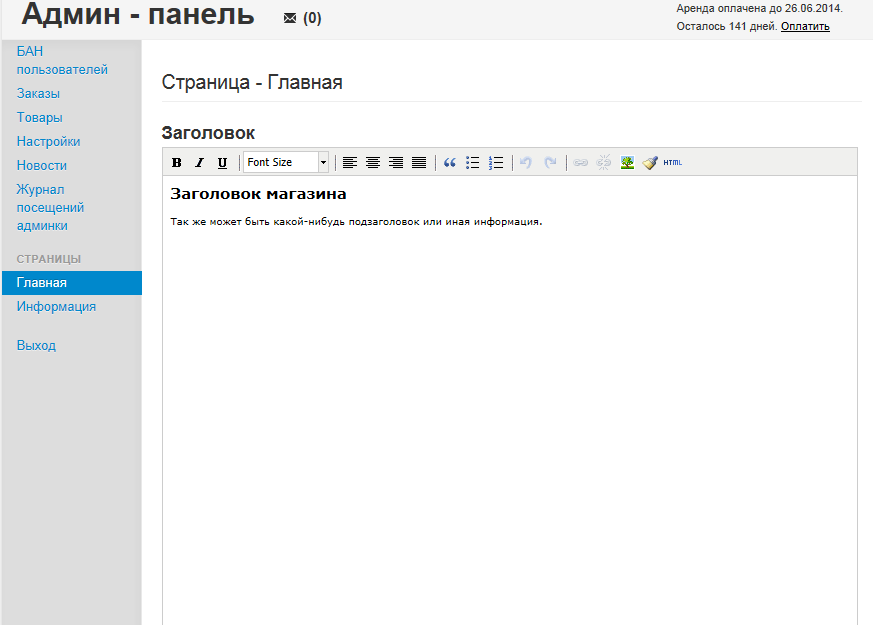
Sample screenshots of the Web based management interface, that potential cybercriminals get access to for the purpose of configuring their E-shops+sample E-shop:
Next to its core feature, basically consisting of a sub domain based on the cybercriminal’s preferences, the service also allows potential customers to use their own domains, insisting they use a Russian domain registration service and CloudFlare as the DNS provider. The monthly price for hosting an E-shop is 333 rubles ($9.55). The simplistic Web-based interface provides cybercriminals with an easy way to integrate their compromised/hacked accounting data into the service. Not surprisingly, due to the relatively low price, the service has already positioned itself as a market leader in the newly emerging standardized monetization model, having already empowered 2500+ boutique E-shops with the necessary infrastructure. The evident standardization of the monetizing process is a trend aiming to directly/indirectly centralize what was once a largely decentralized market segment, case in point, virtually all the boutique cybercrime-friendly E-shops that we’ve profiled and tracked throughout 2012.
The market leading service discussed in this post is currently relying on CloudFlare’s legitimate infrastructure, something we believe is definitely prone to change over time, largely due to the trade off between centralization and the service’s ability to remain online. As such, we expect them — including the competition — to start exclusively utilizing the ubiquitous for the cybercrime ecosystem, bulletproof hosting providers.
As always, we’re keeping an eye on the future development of the service, the E-shops it’s hosting, and will be posting updates as soon as new developments take place.