Operational Security (OPSEC) has always been an inseparable part of the cybercrime ecosystem, especially in the context of preventing law enforcement agencies from tracking down the activities of fraudulent and malicious adversaries online. Throughout the years, the industry has witnessed active utilization of malware-infected hosts (Socks4/Socks5) as anonymization ‘stepping stones’ and the use of cybercrime-friendly VPN providers, bypassing internationally accepted data retention regulations, as some of the primary anonymization tactics used by cybercriminals. Nowadays, this set of tactics has evolved into a diversified mix of legitimate and purely malicious infrastructure that provides value-added services such as APIs supporting Socks4/Socks5 services, DIY real-time Socks4/Socks5 syndicating tools, and the development of hybrid based type of anonymous ‘solutions’. These services empower cybercriminals with the necessary ‘know-how’ to conceal their activities online, and there is a as clear attempt to standardize this ‘know-how’ through the distribution of commercial OPSEC training manuals.
With digital forensics playing a crucial role when assessing cybercrime incidents, in the context of attribution, and ‘case-building’, it shouldn’t be surprising that, for years, sophisticated adversaries have been actively applying off-the-shelf anti-forensics tactics, techniques and procedures (TTPs). The very existence and utilization of these tactics successfully undermines the currently accepted techniques for attributing cybercrime campaigns to the correct parties.
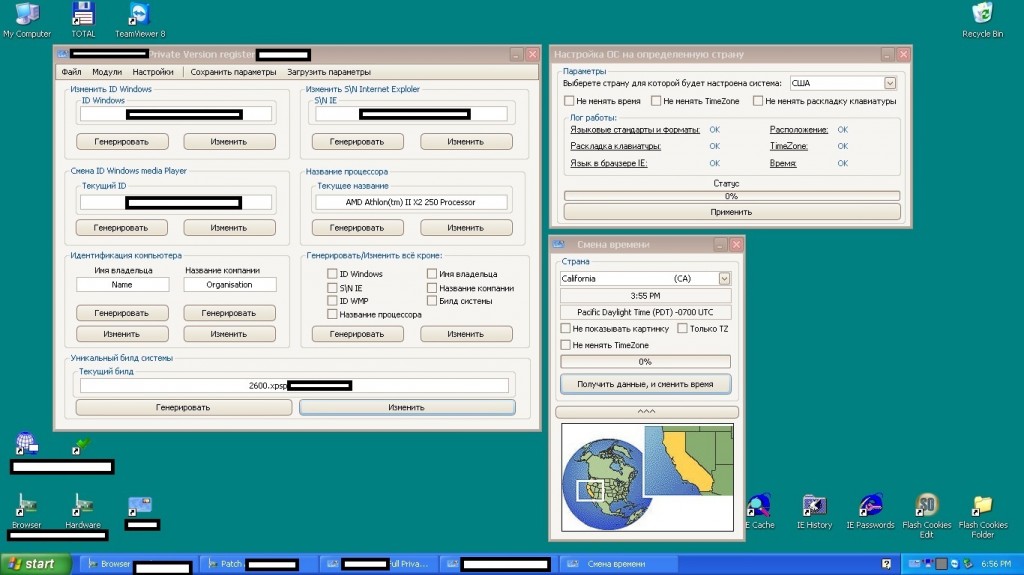
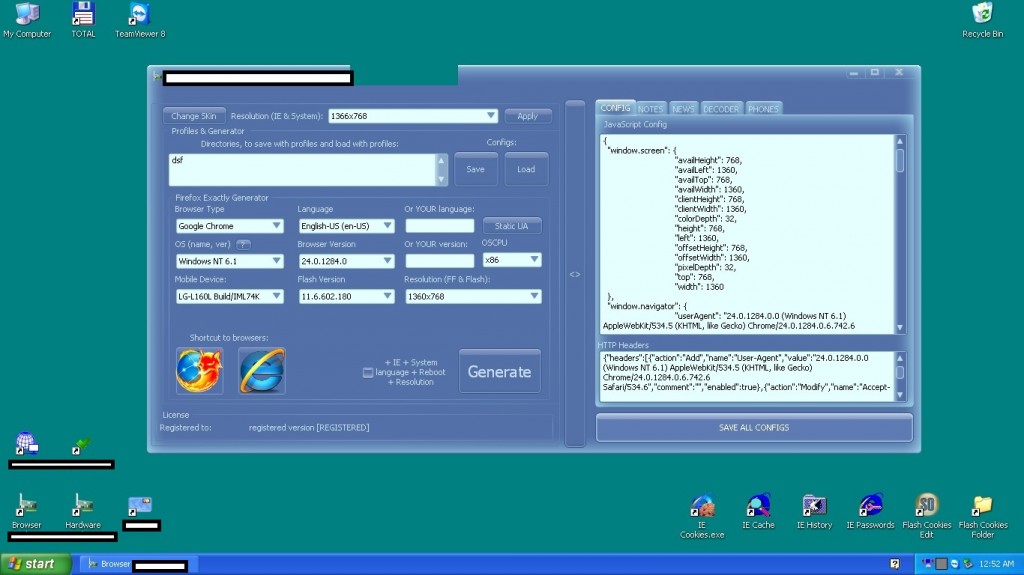
We’ve been tracking an extremely sophisticated — in terms of its potential application when orchestrating fraudulent and malicious campaigns — TeamViewer-based managed service that offers virtual machines pre-loaded with a district set of anti-forensics tools, including many private versions. This service empowers a potential cybercriminal with the necessary point’n’click capabilities to completely anonymize the virtual machine. By modifying the host’s hardware specifications, the service completely anonymizes its interaction with the Internet. System settings can be set through sophisticated patching/hooking of legitimate applications to mimic any given set of preferences — including the pseudo-random generation of preferences — such as the following:
- Windows ID
- Internet Explorer’s Serial Number
- Windows Media Player’s ID
- Processor’s Name
- Computer’s Identification
- System’s build
- System’s Country Settings
- Language formats
- Keyboard language
- Browser’s language
- Geographical Location
- System’s TimeZone
- System’s Time
- Browser’s Resolution
- Browser’s Language
- Browser’s Version
- Mobile Device’s Version
- Flash Version
Sample screenshots of a sample virtual box accessed through TeamViewer, showcasing the inventory of anti-forensic tools/applications available at the disposal of potential cybercriminals:
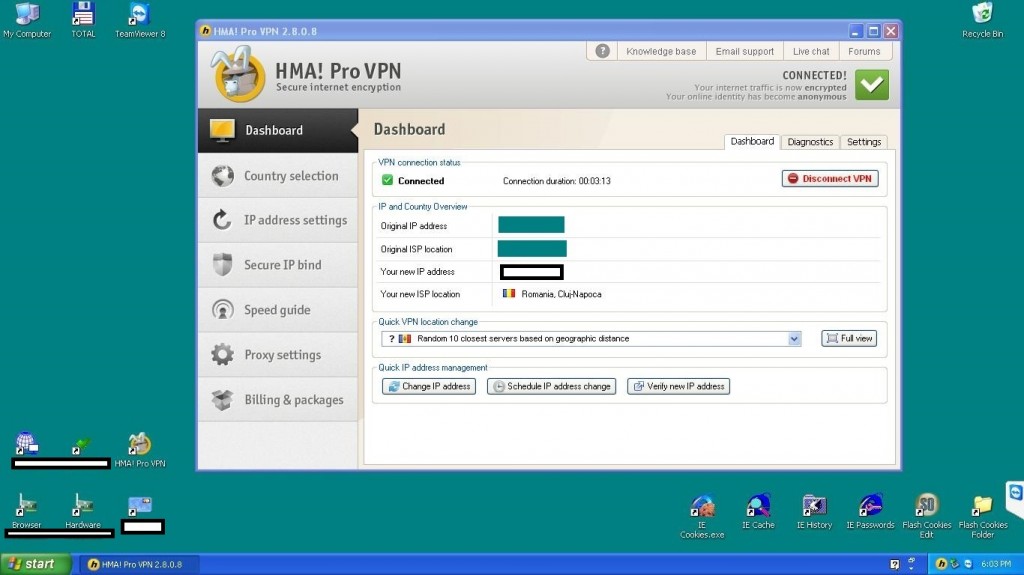
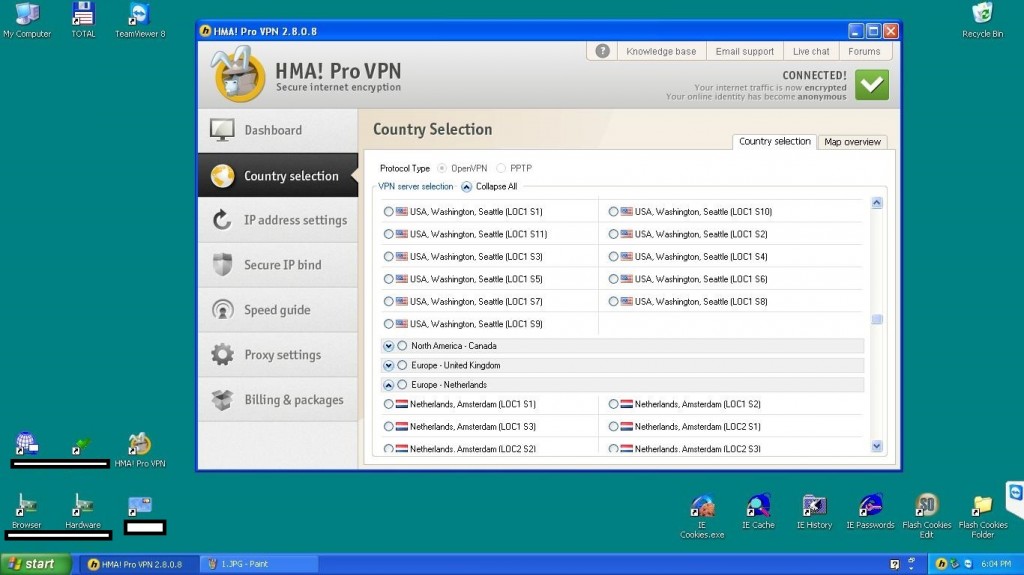
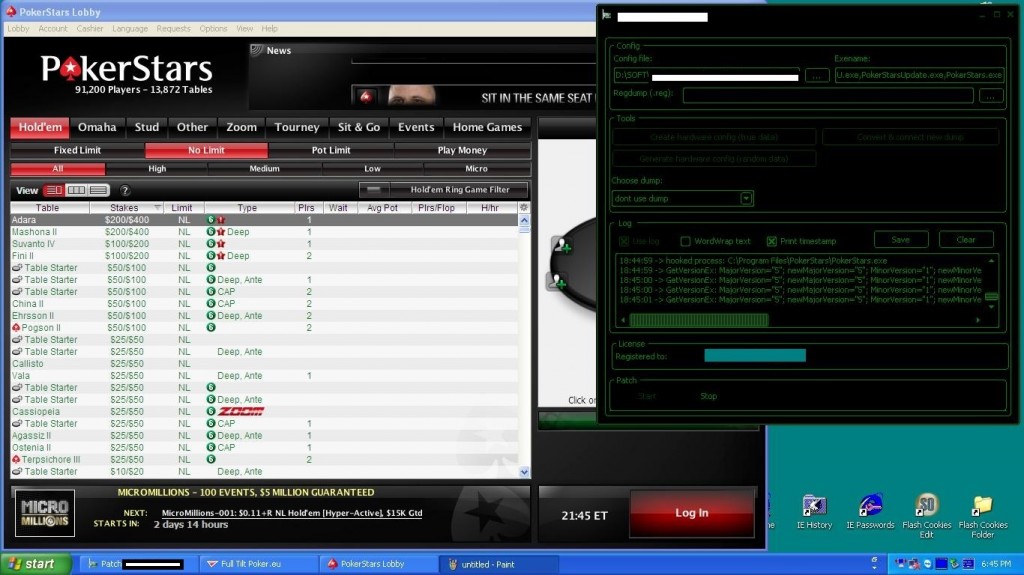
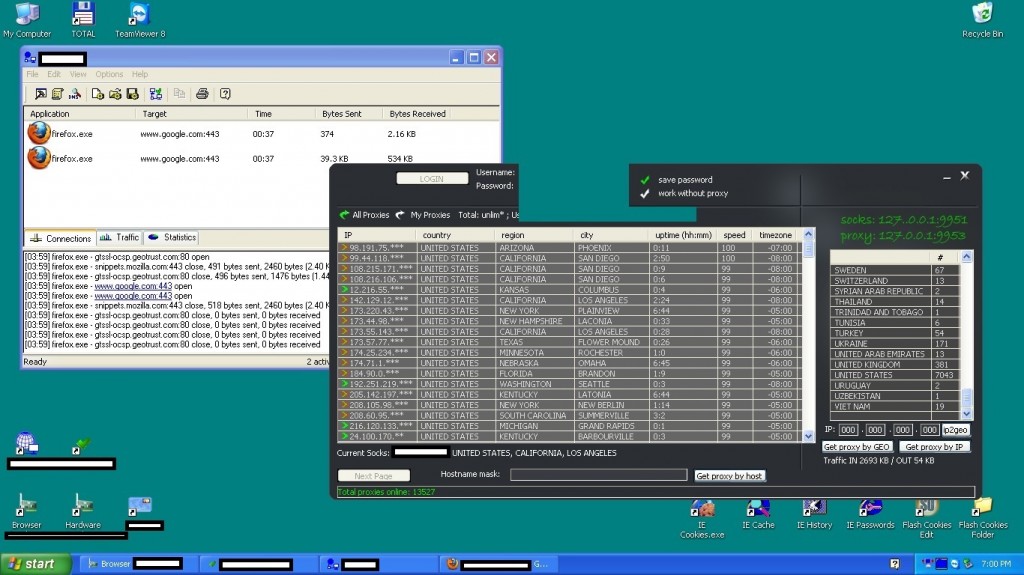
Thanks to these virtualized TeamViewer accessed machines, in combination with the utilization of, both, commercially obtainable Virtual Private Network (VPN) software (HMA Pro as showcased by the vendor in this particular case), next to good old fashion cybercrime-friendly Socks4/Socks5 enabled malware-infected hosts for the purpose of ‘proxifying’ the, now, anti-forensics empowered connection (the service showcased by the vendor is already listing 13,527 malware-infected hosts, the majority of which are U.S based), the cybercriminals using the service are now empowered with sophisticated anti-forensics capabilities allowing them to successfully execute fraudulent and malicious campaigns while making attribution virtually impossible.
Go through related posts, detailing the anonymization tactics, techniques and procedures (TTPs) of cybercrimnals, throughout the years:
- The Cost of Anonymizing a Cybercriminal’s Internet Activities
- The Cost of Anonymizing a Cybercriminal’s Internet Activities – Part Two
- The Cost of Anonymizing a Cybercriminal’s Internet Activities – Part Three
- The Cost of Anonymizing a Cybercriminal’s Internet Activities – Part Four
The price? The disturbingly low $35 for a week, with additional ‘rent schedules’, based on negotiations. This service is a great example of the ongoing diversification within, what we can best describe as, the stagnated market segment for bulletproof hosting services. With vendors constantly looking for new ways to differentiate their value-added propositions, now that virtually every cybercriminal can easily purchase access to such type of hosting, in fact, even enjoy a decent degree of underground market transparency, in the context of having a cost-effective choice to pick up from.
As always, we’re keeping an eye on the future development of the service, in particular, the anticipated emergence of competing propositions.