Cybercriminals continue populating their botnets through the persistent spamvertising of tens of thousands of legitimately looking malicious emails, impersonating popular brands, in an attempt to trick socially engineered users into clicking on the malicious links found within the emails.
We’ve recently intercepted an actively circulating spamvertised campaign which is impersonating HM’s Revenue & Customs Department and enticing users into clicking on the malware-serving links found in the emails.
More details:
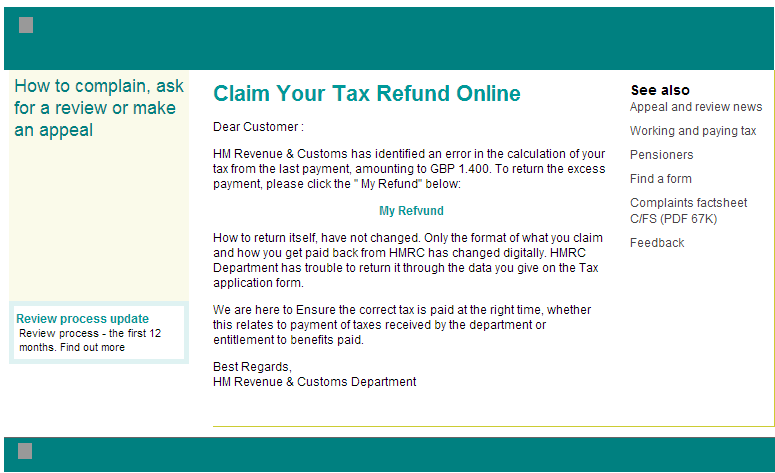
Sample screenshot of the spamvertised email:
Malicious URL redirection chain: hxxp://shotoku.ed.jp/attc.html -> hxxp://85.143.166.215/2p/p.exe
Related malicious MD5s known to have been downloaded from the same IP (85.143.166.215):
MD5: c1d33139ad48ff5bb58273396eea364b
MD5: da9ce0b472be4568d5749ea6fc6d6099
MD5: 552b4880e0ab13784ab2c0ba06f4e1fd
MD5: 3d6807e96cfcae7816234d06cb65df0c
MD5: 94ca63cd8a32096e5eddfd262e88d705
MD5: 1f8c347071f2dcabe45469dd9db98039
MD5: 0dfb50204737f8df26a899dcb47c42ce
Detection rate for the sampled malware: MD5: 2192aeb3c4707015ef3bc3e2e8ca6da9 – detected by 3 out of 51 antivirus scanners as Mal/Zbot-QU
Once executed, the sample starts listening on ports 2661 and 5668.
Once executed, the sample creates the following Mutexes on the affected hosts:
CTF.TimListCache.FMPDefaultS-1-5-21-1547161642-507921405-839522115-1004MUTEX.DefaultS-1-5-21-1547161642-507921405-839522115-1004
Local\{0BB5ADEF-9D8E-F058-DBC9-BE58FA349D4A}
Local\{911F9FCD-AFAC-6AF2-DBC9-BE58FA349D4A}
Local\{D15F4CE9-7C88-2AB2-DBC9-BE58FA349D4A}
Local\{D15F4CEE-7C8F-2AB2-DBC9-BE58FA349D4A}
Local\{B0B9FAFC-CA9D-4B54-DBC9-BE58FA349D4A}
Local\{B0B9FAFD-CA9C-4B54-DBC9-BE58FA349D4A}
Global\{2E06BA86-8AE7-D5EB-DBC9-BE58FA349D4A}
Global\{B0B9FAFD-CA9C-4B54-DBC9-BE58FA349D4A}
Global\{B0B9FAFC-CA9D-4B54-DBC9-BE58FA349D4A}
Global\{D15F4CEE-7C8F-2AB2-DBC9-BE58FA349D4A}
Global\{D15F4CE9-7C88-2AB2-DBC9-BE58FA349D4A}
Global\{0BB5ADEF-9D8E-F058-DBC9-BE58FA349D4A}
Global\{BFDEF9F0-C991-4433-11EB-B06D3016937F}
Global\{BFDEF9F0-C991-4433-75EA-B06D5417937F}
Global\{BFDEF9F0-C991-4433-4DE9-B06D6C14937F}
Global\{BFDEF9F0-C991-4433-65E9-B06D4414937F}
Global\{BFDEF9F0-C991-4433-89E9-B06DA814937F}
Global\{BFDEF9F0-C991-4433-BDE9-B06D9C14937F}
Global\{BFDEF9F0-C991-4433-51E8-B06D7015937F}
Global\{BFDEF9F0-C991-4433-81E8-B06DA015937F}
Global\{BFDEF9F0-C991-4433-FDE8-B06DDC15937F}
Global\{BFDEF9F0-C991-4433-0DEF-B06D2C12937F}
Global\{BFDEF9F0-C991-4433-5DEF-B06D7C12937F}
Global\{BFDEF9F0-C991-4433-95EE-B06DB413937F}
Global\{BFDEF9F0-C991-4433-F1EE-B06DD013937F}
Global\{BFDEF9F0-C991-4433-89EB-B06DA816937F}
Global\{BFDEF9F0-C991-4433-F9EF-B06DD812937F}
Global\{BFDEF9F0-C991-4433-E5EF-B06DC412937F}
Global\{BFDEF9F0-C991-4433-0DEE-B06D2C13937F}
Global\{BFDEF9F0-C991-4433-09ED-B06D2810937F}
Global\{BFDEF9F0-C991-4433-51EF-B06D7012937F}
Global\{BFDEF9F0-C991-4433-35EC-B06D1411937F}
Global\{DDB39BDC-ABBD-265E-DBC9-BE58FA349D4A}
Global\{BB67AFC4-9FA5-408A-DBC9-BE58FA349D4A}
Global\{BFDEF9F0-C991-4433-79EC-B06D5811937F}
Global\{2E1C200D-106C-D5F1-DBC9-BE58FA349D4A}
It drops the following MD5s on the affected hosts:
MD5: 1dc247518c06ab38441a226dc9a63cf4
It then phones back to the following C&C servers:
174.89.110.91
86.131.158.222
98.202.88.224
77.239.59.243
23.98.42.224
23.98.64.182
130.37.198.100
99.73.173.219
138.91.18.14
94.88.99.85
109.153.212.95
143.225.154.3
213.120.146.245
37.57.41.161
76.22.162.44
221.193.254.122
37.203.28.115
75.1.220.146
191.234.52.206
168.63.62.72
168.61.87.1
137.135.218.230
58.72.156.251
114.189.115.181
191.236.81.175
137.116.225.57
2.135.155.255
71.49.172.208
138.91.187.61
137.117.72.80
37.213.4.238
93.77.3.231
220.227.80.53
81.130.195.125
204.80.1.48
105.237.41.92
119.150.7.131
188.10.35.153
14.99.133.100
89.44.180.213
188.25.71.232
137.117.197.32
168.62.182.150
23.96.34.43
109.64.20.153
118.96.3.224
Related malicious MD5s known to have phoned back to the same C&C servers:
MD5: b7383b0464ad36f2ed8a6481df2ad9a2
MD5: 98bda54bf4dcffbe606b0c5dbfdf769d
MD5: 4bb673a1445b945a96b155ec8b83fc27
MD5: 6b8ecdbfe7594678e3005e6d7e770d27
MD5: fa3551284c281abefada9c8e6cf27ec9
MD5: 44abf0f5ddb012c5a315f842e806d5e1
MD5: ccdb6afa7366cfd21e54f63f6f26241b
MD5: f3322d923826bc18d41dee67e1428e18
MD5: 1dd70251fbfad01ee4dcba178d71b03a
MD5: f8d354d15501d7835ef6bbc9f1404ea4
MD5: e90f10b35c99b43bfa0cb9216d8bcee1
MD5: ec97ed628d2a45be07412aed9d262b0c
MD5: 194300c46b331ff59f5361560a5865f8
MD5: 28ab4d1f4891c446434b58ff31b55a23
We’ll continue monitoring the malicious campaign, and post updates as soon as new developments take place.
Webroot SecureAnywhere users are proactively protected from these threats.