In a cybercrime ecosystem dominated by DIY(do-it-yourself) malware/botnet generating releases, populating multiple market segments on a systematic basis, cybercriminals continue seeking new ways to acquire and efficiently monetize fraudulently obtained accounting data, for the purpose of achieving a positive ROI (Return on Investment) on their fraudulent operations. In a series of blog posts, we’ve been detailing the existence of commercially available server-based malicious script/iframe injecting/embedding releases/platforms utilizing legitimate infrastructure for the purpose of hijacking legitimate traffic, ultimately infecting tens of thousands of legitimate users.
We’ve recently spotted a long-run Web-based managed malicious/iframe injecting/embedding service relying on compromised accounting data for legitimate traffic acquisition purposes. Let’s discuss the managed service, its features, and take a peek inside the (still running) malicious infrastructure behind it.
More details:
In terms of Q&A (Quality Assurance), the key differentiation features of the service include: automatic URL AV/blacklist detection through a third-party managed service, (compromised) legitimate Web site page rank checker, metrics based statistical system, IM notifications, as well as (compromised) login validation.
Affected CMS platforms:
Joomla.Site
WordPress
DataLife Engine
Drupal
cmsimple
BBpress
phpBB
postnuke
e107
PHP-NUKE
PunBB
Simple Machines Forum (SMF)
MODX Revolution
FluxBB
cmsmadesimple
nucleus
Contao Open Source CMS
slaed
The managed service is currently priced at $250 on a monthly basis, $1,500 for six months, and $2,500 for one year subscription. It’s capable of maintaining up to 500 simultaneous threads. Let’s take a peek inside the fraudulent infrastructure behind it.
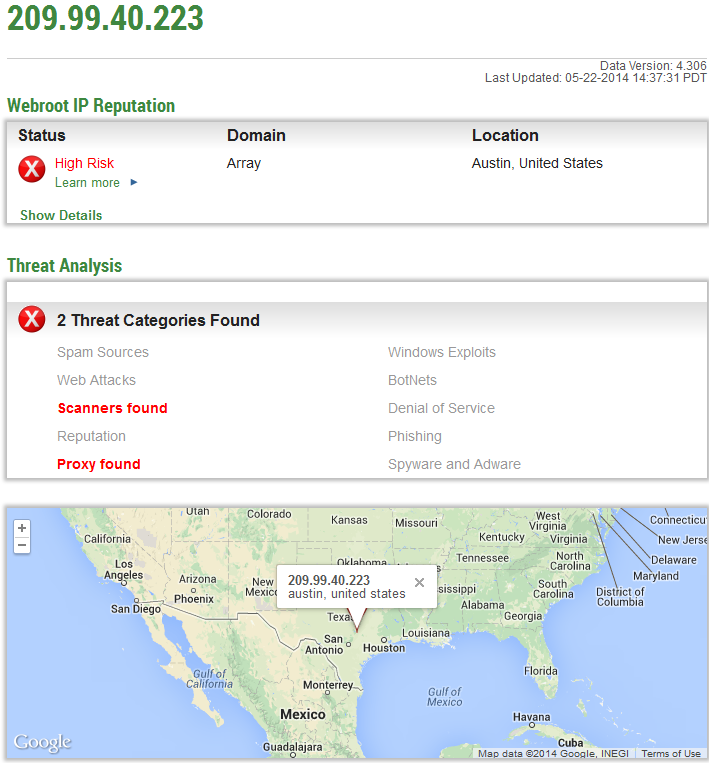
Known to have responded to the same IP (209.99.40.222; 209.99.40.223) as the original hosting location are also the following fraudulent/typosquatted domains:
hxxp://11si0s8.t3.d.googleadservice.net
hxxp://11si0se.t3.d.googleadservice.net
hxxp://11si0u9.t3.d.googleadservice.net
hxxp://11si0vh.t3.d.googleadservice.net
hxxp://11si0vo.t3.d.googleadservice.net
hxxp://11si0vu.t3.d.googleadservice.net
hxxp://11sl2nr.t3.d.googleadservice.net
hxxp://11sl9jv.t3.d.googleadservice.net
hxxp://11sl9k0.t3.d.googleadservice.net
Known to have phoned back to the same IP (209.99.40.222) as also the following malicious MD5s:
MD5: 35908d4fb26949b2431849d3d8165740
MD5: 1e47a4a9744fff22b54077bfbb588aed
MD5: 4d9cc9ff385732f9f61ca926acb5ff1d
MD5: aa4057d07e1fcf258779be5d26ce99cb
MD5: 5f9b815eb20c49b57a7cc7fa8d144e00
MD5: 015208aa2fc88b176be1281fdaac6d24
MD5: 175c12348d05d8bfdeaae607db2cd0a9
MD5: cb0699ecf69598e822e8f8d68b13817d
MD5: b4c5b5e5c5e00dcf78bb5027af03766f
Once executed MD5: 35908d4fb26949b2431849d3d8165740 phones back to:
31.170.179.179
209.99.40.222
208.91.196.252
208.91.196.4
144.76.167.153
31.170.178.179
148.251.97.163
69.195.129.70
195.22.26.252
200.98.255.192
Related malicious MD5s known to have phoned back to the same C&C server (31.170.179.179):
MD5: 35908d4fb26949b2431849d3d8165740
MD5: c358eab15a24b50769f31130d82f81ad
MD5: 757661a1ebfec599bbbff8e7eb9ef36f
MD5: 64eadeaf41536d3db4abd65fb7efa4c0
MD5: ca1219813e7a190f310a3c599adb3031
Known to have phoned back to the same IP (209.99.40.223) as the original hosting location are also the following fraudulent domains:
MD5: 655cbf254d476fa1b5ac8e8b8f8d1300
MD5: 2c4d569539a3732a5e37b2f01305c87b
MD5: 6271df03b4074daf92a9ae75fd572c70
MD5: 559c4869c327726ff7d2566874569a46
MD5: 65f189242a45493c162b375bd4d1446f
Webroot SecureAnywhere users are proactively protected from these threats.