 Windows 10 has been notorious about automatically installing updates on users’ machines and now there is a ransomware that aims to capitalize on it. The new ransomware, Fantom, is based on the EDA2 open-source ransomware project on GitHub called hidden tear that’s recently been abandoned.
Windows 10 has been notorious about automatically installing updates on users’ machines and now there is a ransomware that aims to capitalize on it. The new ransomware, Fantom, is based on the EDA2 open-source ransomware project on GitHub called hidden tear that’s recently been abandoned.
Fantom behind the scenes
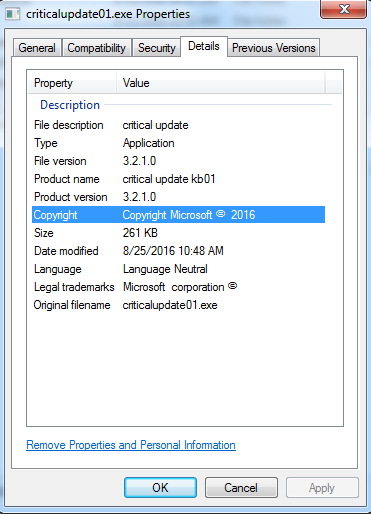
In an attempt to conceal malicious intention, the authors of this ransomware modified the file properties to show copyright and legal trademarks mimicking a Windows update.
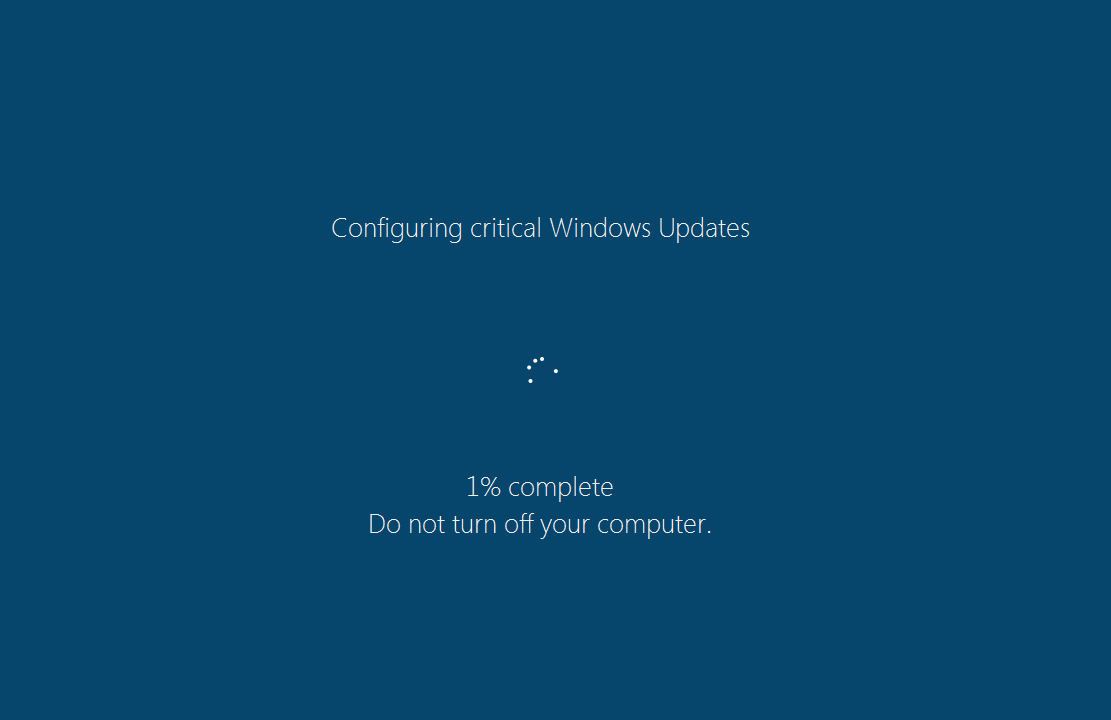
Once this dropper is executed, the payload “WindowsUpdate.exe” is dropped in AppData\Local\Temp displaying the fake Windows Update screen as shown below. This screen locks you out of doing anything else on your computer, keeping in line with the scam that Windows 10 doing its normal interrupt of updates.
The percentage counter does work and will go up at about a percent per minute. However, it’s fake and doesn’t represent anything other than to communicate to you that this “Windows update” will take a while and that you shouldn’t be alarmed of CPU usage and hard drive activity. You can close this fake update overlay by ending the process “WindowsUpdate.exe” using task manager, but the encryption of your files is unaffected.
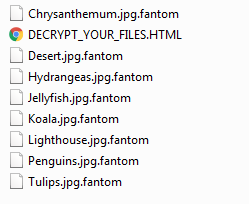 DECRYPT_YOUR_FILES.HTML ransom note
DECRYPT_YOUR_FILES.HTML ransom note
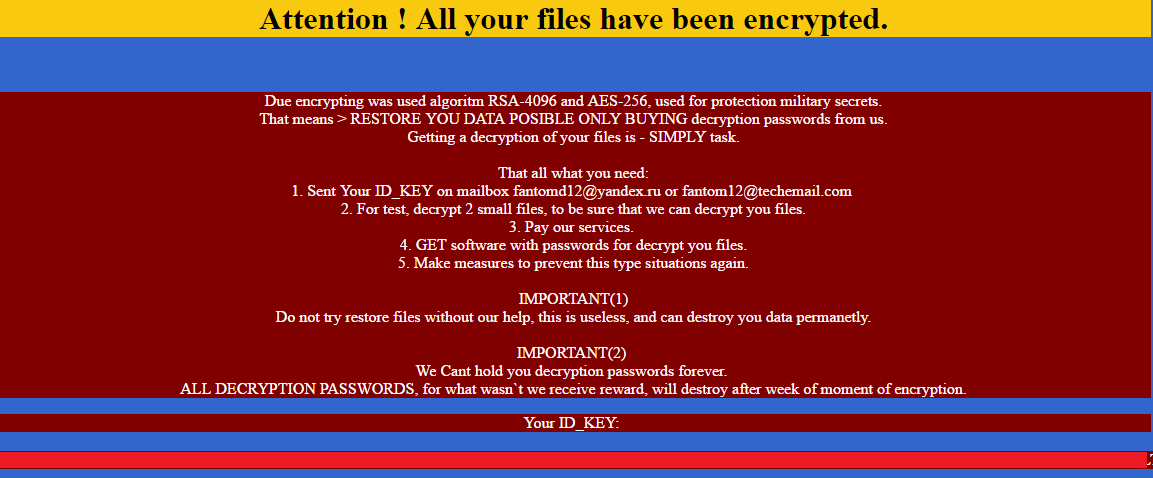
Encryption is done using AES-128 encryption and when a file is encrypted it will append “.fantom” to the extension of the file. Also in every directory that a file is encrypted, a standard ransom note “DECRYPT_YOUR_FILES.HTML” is created.
The ransom note doesn’t have an onion link as your payment portal for your files – a standard for most encrypting ransomware. Instead, you’re asked to email the cyber criminals and await response. This tactic is meant to target less savvy computer users who would be intimidated by creating a bitcoin wallet address and using a tor browser to connect to the darknet for ransom payment. To increase odds of gaining trust, two “freebie” files for decryption are allowed.
However, it’s clear that these cyber criminals have a very loose grip on the English language so we don’t anticipate much traction with their scams through email. We also reached out as a test and have yet to hear back in over 24 hours.
Employ a backup solution
Webroot will catch this specific variant in real time before any encryption takes place. We’re always on the lookout for new threats, but just in case of new zero-day variants, remember that with encrypting ransomware, the best protection is going to be a good backup solution. This can be either through the cloud or offline external storage. Keeping it up to date is key so as not to lose productivity. Webroot has backup features built into our consumer product that allow you to have directories constantly synced to the cloud. If you were to get infected by a zero-day variant of encrypting ransomware, you can just restore your files back as we save a snapshot history for each of your files up to ten previous copies. Please see our community post on best practices for securing your environment against encrypting ransomware.
MD5 Analyzed: 7D80230DF68CCBA871815D68F016C282
Additional MD5 seen: 4AC83757EBF7ACD787F732AA398E6D53
65E9E1566DEC1586358BEC5DE9905065
60DBBC069931FB82C7F8818E08C85164
86313D2C01DC48D617D52BC2C388957F






i have this onmy serverer,? how do we solve this?
Solve it by keeping a backup of all your data for at least 30 days. if you’re on a thin budget then download VEEAM free edition and backup to a basic external hard drive. Restoring your files or entire system is really easy.
Great suggestions and points, Travis!
We appreciate you being so proactive to help out 🙂
Warm Regards,
Josh P.
Webroot Community Support
i have this ransomwae
Hello Gedzu,
Please reach out to our Technical Support Team directly for further assistance:
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Regards,
Josh P.
Webroot Community Support
Not tech savvy – how do I exactly find out if we have this ransomware / virus – whatever it is
Debi, please reach out to our Customer Support Team directly for assistance. They will be able to remotely review your system to ensure we remediate any infection if present.
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Social Media Coordinator
Another thing that I do is employ a External USB Backup drive. I don’t leave this drive connected to my home network. I attach the drive and about twice a month, I run a full image backup.
The reason for the image backup is that it will also restore the Operating System.
I also have Webroot Internet Complete Security. In addition I use all of the following FREE programs. CCleaner, Malwarebytes, SuperAntiSpyware. Now I have found that I don’t always find any additional issues between Malwarbytes and SuperAntiSpyware but on an occasion, I do.
Before I run any of these programs, I always make sure that I update any definitions that are available and then run the program. I do this at least twice a week.
This is the best advice I’ve seen given on all of our Blog Posts to date, Scott. Awesome job.
Cheers,
Josh P.
Social Media Coordinator
Hi Scott, where can I purchase a USB Backup Drive? and does it give instructions on how to do a full image backup? Is there a website where I can read abut it? Thanks, Madison
Hello, Madison.
You can purchase a USB Drive at any electronics store, or I always recommend doing your research by looking at reviews on Amazon.
https://www.amazon.com/Best-Sellers-Computers-Accessories-USB-Flash-Drives/zgbs/pc/3151491
I found this article that gives 4 solutions that are very straight forward in detailing the image backup process:
https://www.raymond.cc/blog/make-full-backup-of-your-ipod-usb-flash-drive-and-mp3-players-by-imaging/
I hope this helps!
Warm Regards,
Josh P.
Digital Care Coordinator
My laptop did a fairly long Windows 10 update yesterday, and then again when I turned it on this morning. But I don’t see any “.fantom” files, or ransom note. I have a directory under C:/Program Files/Application Data that I can’t open (“Access is denied”). How do I know if I got hit with this one?
John, please contact our Technical Support Team directly at your earliest convenience for any threat related concerns/inquiries:
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Social Media Coordinator
My computer was hacked by one of those update messages for windows 10. I clicked on the “x” to dismiss it and everything just stopped and froze up. No curser, couldn”t turn the computer off, nothing worked. Pulled the plug, waited for 15 minutes and tried to restart the computer. Nothing will work, just a message saying diagnostics unable to restart the computer. so that computer is sitting in a brown box rusting away with all my data in it. Bummer!
So sorry to hear that, Joseph!
For future reference for you, any threat related concerns/questions can always be directed to our Advanced Malware Removal Team for review. This is a service we offer to all of our Customers with an active subscription at no charge.
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Social Media Coodinator
I have two questions:
Josh, I have a Webroot subscription still on my old XP computer and would like to transfer it to my W-7 laptop. Do I call tech support to do this? Do I have your backup feature too as mentioned above?
I use a Seagate external HD for my PC backups. Will this suffice to reinstall everything in the event I’m hit with the ransomware? Thanks, Jim J.
Hello,
You will absolutely be able to transfer your subscription to your new laptop as long as it is still active.
You can email me directly with the account I can find you with: socialcare@webroot.com
or reach out to Tech Support directly as you mentioned for assistance with transferring your Webroot Security:
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
In regards to the external hard-drive backups, that is the most optimal way to mitigate risk of Ransomware. Whatever you have backed up externally is completely safe from intruders.
Please let me know if I can help answer anything else for you at all.
Warm Regards,
Josh P.
Social Media Coodinator
Is the backup data really safe IF the external hard drive stays connected to the computer? I would think the malware would just see it as another drive and encrypt that too. No?
You are absolutely correct, Prince.
All backups should be offline and not connected to any devices/networks.
Warm Regards,
Josh P.
Digital Care Coordinator
Several days ago a red screen came on with the Windows 10 upgrade.I wasn’t asked to do anything nor had an opportunity to decline.it lasted quite sometime.Next day it came on again and I just shut off the computer.Why wasn’t I ever informed ahead of time that this maybe a bogus upgrade.what is web root worth if only after you e-mail meand tell me of it.
Ken, any message like the one you mentioned needs to be reviewed be our Technical Support Team at your earliest convenience:
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Social Media Coordinator
So to be clear. Is this automatically installed like a real windows update or does a user have to choose to “update” How is it delivered.
The user has to execute the “update”. It is not installed automatically like Genuine Microsoft Windows Updates.
Warm Regards,
Josh P.
Social Media Coordindator
Does this ransomware execute automatically during bootup like other Windows updates or does the victim have to execute it manually?
The user has to execute the “update”. It is not installed automatically like Genuine Microsoft Windows Updates.
Warm Regards,
Josh P.
Social Media Coordindator
This article fails to mention how the ransomware makes it on to our computers. Do we have to click a link to download, or have they found a way to place it without the user actually clicking or downloading?
Melissa, like most Ransomware, they are typically distributed through click-bait emails and/or harmful pop-ups you can come across when browsing unsafe websites.
https://www.wired.com/2016/05/4-ways-protect-ransomware-youre-target/
Warm Regards,
Josh P.
Social Media Coordinator
I had this blue screen, but not the bottom red screen. Am I infected?
Larry,
For any issues or concerns related to threats, please reach out to our Technical Support Team directly for assistance:
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Social Media Coordinator
When Windows update starts how can I tell if it is real or fake?
It should be fairly obvious if the “update” takes place inside a browser window. Genuine Window Updates are found through your Control Panel, coming from anywhere else would be quite suspicious.
http://answers.microsoft.com/en-us/windows/forum/windows_vista-update/how-can-i-tell-if-a-windows-update-is-genuine/eab83c2c-506b-456e-b1f6-2d450cf88033?auth=1
Warm Regards,
Josh P.
Social Media Coordinator
Have been hit with this fake-Windows-10-Update ransomware twice. Managed to fix it myself (NOT a tech pro), but it was very time-consuming and many-expletives-deleted annoying. An ounce of prevention is worth a pound of cure, so how does this type of ransomware get on our computers in the first place, and how can we avoid it? Thanks!
Susan, please visit the following sites for more infomation on how to better protect yourself against Ransomware:
https://www.wired.com/2016/05/4-ways-protect-ransomware-youre-target/
https://www.cnet.com/forums/discussions/ransomware-how-do-you-prevent-it-from-happening-632541/2/
TL;DR: Backups are your best friend and don’t click on shady stuff!
Warm Regards,
Josh P.
Social Media Coordinator
I have webroot so will they know if i have been hit. i don’t know for sure but i think i may have fallen for it yesterday. I was told to update when asked but i don’t really know what is what. in beginning i never did update on my old computer, it fell so behind i could not use some programs. I think i may have Kapersky and Geek squad. or who is supposed to help me?
Kar, please reach out to our Technical Support Team directly for any concerns or questions relating to Threats:
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Social Media Coordinator
I got a Windows update message about my settings. Is that ransomware?
Tonia, please direct all threat-related concerns or questions to our Support Team directly. They’ll take a deeper look and give you a definitive answer.
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send a Support Ticket: http://wbrt.io/eyqx
Warm Regards,
Josh P.
Digital Care Coordinator
I have a multi-boot laptop. This is worth noting: I just experienced this looong update to Win 8.1 by choosing Microsoft update within Windows 8.1. The looong update would not end so I CTRL-ALt-Deleted. Afterwards, My Linux grub was destroyed. Win 8.1 booted then after awhile began the long update. I killed it. After that the laptop would not boot. I I reformatted the laptop and installed Linux only.
This update came officially from Redmond.