In order for cybercriminals to launch, spam, phishing and targeted attacks, they would first have to obtain access to a “touch point”, in this case, your valid email address, IM screen name, or social networking account.
Throughout the years, they’ve been experimenting with multiple techniques to obtain usernames (YouTube user names, IM screen names, Hotmail email addresses) and valid email addresses from unsuspecting end and corporate users.
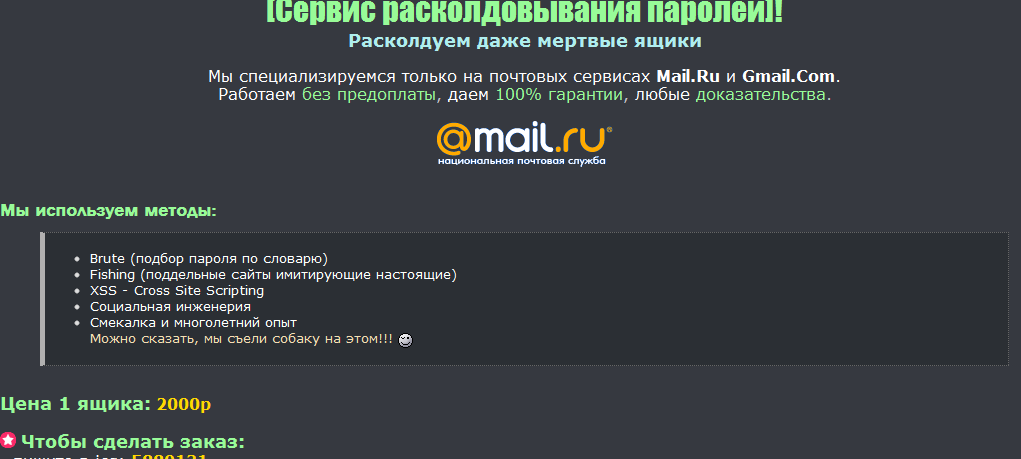
In this post we’ll profile a recently released Russian DIY email harvester, and emphasize on the difference between notice and experienced cybercriminals in the context of the tactics and techniques they use to obtain a potential victim’s email address.
More details: