By Marco Giuliani
 In our previous technical analysis of the ZeroAccess rootkit, we highlighted how it acts as a framework by infecting the machine — setting up its own private space in the disk, first through a dedicated file system on the disk, and more recently by using a hidden and locked directory. This is where the rootkit stores the modules it downloads from the command and control servers. Until now, the plugins we’ve monitored have been ad-clickers and search engine hijackers.
In our previous technical analysis of the ZeroAccess rootkit, we highlighted how it acts as a framework by infecting the machine — setting up its own private space in the disk, first through a dedicated file system on the disk, and more recently by using a hidden and locked directory. This is where the rootkit stores the modules it downloads from the command and control servers. Until now, the plugins we’ve monitored have been ad-clickers and search engine hijackers.
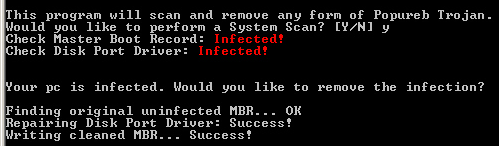
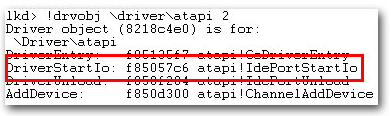
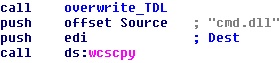
We have also noted how the ZeroAccess rootkit acts very similar to the TDL3 rootkit, either by infecting a random system driver, using its own file system to store its plugins or by filtering the disk I/O by analysing the SCSI packets – though in a pretty different way. It’s more effective in the TDL3 rootkit and less effective in the ZeroAccess rootkit, however ZeroAccess has many more self-protection mechanisms in place.
While analyzing the ZeroAccess rootkit, I’ve always had the feeling it was inspired by the TDL3 rootkit. But while looking at the latest updates of it I’ve found something pretty interesting: The ZeroAccess team is looking at TDL rootkit as an enemy that needs to be defeated. The questions remains, is there a link between the two rootkits? We suspect the answer is yes.