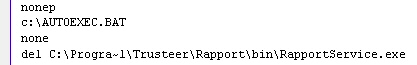Ransomware is nothing new, but a Ukrainian ransomware Trojan that came over the transom last week demonstrated that the concept of “payment” can extend to services other than banking or finance. In this case, the Trojan (which we and several other AV companies call Trojan-Ransom-Krotten) thoroughly locks down the infected system then demands payment—in the form of credit paid to the Ukrainian mobile phone provider Kyivstar, which the victim then has to transfer to the malware distributor’s account.
Ransomware is nothing new, but a Ukrainian ransomware Trojan that came over the transom last week demonstrated that the concept of “payment” can extend to services other than banking or finance. In this case, the Trojan (which we and several other AV companies call Trojan-Ransom-Krotten) thoroughly locks down the infected system then demands payment—in the form of credit paid to the Ukrainian mobile phone provider Kyivstar, which the victim then has to transfer to the malware distributor’s account.
Yes, Alice, the hacker wants you to pay his cellphone bill.
Once the ransomware has taken hold on a victim’s computer, it locks down the operating system in dozens of different ways, as well as changing several registry keys that add juvenile, profane text to Internet Explorer’s title bar and elsewhere on the desktop and in folders.
Paying the ransom in these cases simply emboldens the malware creator to continue his crime spree. Of course, even once a victim hypothetically pays this ransom, there’s also no guarantee that there’s any way at all for the malware distributor to reverse the damage — which takes the form of significant levels of annoyance — caused by this insipid Trojan.
Fortunately for the victim, the creator of this Trojan isn’t the sharpest tack in the box. Not only were we easily able to tease out the Trojan’s payloads and add signatures which would prevent the Trojan from delivering its payload files to a victim’s computer, but we’re able to see exactly how the author (ineffectively) tries to frustrate the kinds of behavioral analysis we and other antivirus vendors perform.