What Now After Black Hat 2015?
It’s good to see that at last some alternatives to traditional AV endpoint protection are gaining traction. A lot of the questions I was asked at the show were to compare Webroot to other exhibitors who were making similar claims. (But because we lead the Predict, Prevent, Detect, and Respond model there are really no true one to one comparisons. There is however a lot of plagiarism on our market positioning, which I take as an indirect compliment, as does my CMO).
My primary concern now is efficacy, just how good are other solutions at stopping attacks and infections? The other vendors have little or no track record and are in light use. Nor do Webroot or I really care about a kill chain, it’s too damn late if you’re looking at a kill chain. As the Financial Services industry keep saying your investment may well go up or down.
Another annoyance I and the people I talked to have is that there is also no real ‘independent’ testing of next generation AV. We have tried unsuccessfully for over three years to get endpoint tests by all the ‘big’ testers updated. But, there is too much self-interest in their keeping things the same. That’s a shame, as their credibility is truly shot as any security professional sees day in and day out the disconnect between 100% detection test results and their real-life infection rates.
Perhaps the most surprising event (given other infamous events) was the pertinence of John McAfee’s speech quickly followed by the weaknesses in Android being at last partly admitted in Public. Google are willing to let you share your full contacts with a flashlight app and still don’t see any issues. Yet the people who say “don’t worry you’ve nothing to fear if you’ve nothing to hide” are all the actors I want to stay as far away from as possible – as they are ALWAYS up to no good.
So what now after Black Hat 2015? Are we turning failure into success? I’m afraid the answer is still no. Commercial, Government and Hacker interests are still harmoniously aligned and we will not see success until they are hoisted on their own petard. Frankly that cannot come soon enough (as long as they don’t take us all down with them).
Why are we using biometrics as passwords?
After seeing a great presentation on newly discovered biometrics/fingerprint vulnerabilities (“Fingerprints On Mobile Devices: Abusing And Leaking”, by Tao Wei and Yulong Zhang) at Blackhat 2015, I have to wonder why we are even using a lone fingerprint as a password. Wouldn’t fingerprints be better implemented as a username?
When your fingerprint is compromised, it is compromised forever. We’re talking about something associated with criminal records, banking, and other fairly-critical segments of one’s identity. It only makes sense your fingerprint remain part of your identity and not some password you hope to remain secret for the rest of your life. You can’t change them. Not easily, anyways… As your username, it would simply remain a part of your identity, unable to be used against you without the secrets you can more easily hide and change: passwords, pins, etc.
 Fingerprints would normally need to be physically gathered, dusting for prints and all that, making their compromise a less-than-likely situation. The issues outlined in the presentation I saw, however, showed it could be possible for their digital counterparts to be gathered remotely and en masse. Imagine if a fingerprint wasn’t the password, but only the login. That wouldn’t be that big of a deal anymore. So they know your username, so what? They still can’t log in. Email addresses are scraped up off the internet all the time. Someone’s email address is bound to be in many places they don’t want it to be, but the threat of compromise is still extremely low if they’re securing their account properly. In reality, a leaked fingerprint is a big deal because you can do things like pay someone via PayPal with it. The fingerprint is the password and the username can be gotten easily (they’re almost always stored insecurely and most of the time it’s just an email address anyways).
Fingerprints would normally need to be physically gathered, dusting for prints and all that, making their compromise a less-than-likely situation. The issues outlined in the presentation I saw, however, showed it could be possible for their digital counterparts to be gathered remotely and en masse. Imagine if a fingerprint wasn’t the password, but only the login. That wouldn’t be that big of a deal anymore. So they know your username, so what? They still can’t log in. Email addresses are scraped up off the internet all the time. Someone’s email address is bound to be in many places they don’t want it to be, but the threat of compromise is still extremely low if they’re securing their account properly. In reality, a leaked fingerprint is a big deal because you can do things like pay someone via PayPal with it. The fingerprint is the password and the username can be gotten easily (they’re almost always stored insecurely and most of the time it’s just an email address anyways).
Other situations and issues involving fingerprints being used as a mix authentication and authorization – depending on what app you’re in – are outlined in the presentation as well. In one example, they showed malicious actors’ ability to snag fingerprints in the background, causing you to authorize a payment when unlocking your phone, for instance. Yet another situation where, if the print was your username, there wouldn’t be an issue.
At the very least, there clearly needs to be better security standards around fingerprint data and sensors. Still, making them less powerful (read: not the sole password used to access banking information) would be the best way to go.
Recap of Black Hat 2015, Day 1
This is hacker week. Well, not really that officially, but with Black Hat USA and DefCon happening in Vegas, the biggest collection of black and white hat hackers have come together with experts and companies in the security sector to talk protection, exploits, and hacking. Coming at the conference with a big approach, our threat team has attended sessions all day, taking in the lessons being shared in hopes of continuing our advancement of our threat intelligence.
So coming out of the sessions, I have asked our attending team to share their takeaways of Black Hat 2015 Day 1.
On Internet of Things
Attended the, Intel security presentation on attacking hypervisors through firmware and guest operating systerms. The data they presented verified the work we are doing in the IOT (internet of things) field in bring real time behavior monitoring to industrial endpoints. John Sirianni – Vice President, Strategic Partners, Internet of Things
On Endpoints
Windows updates for drivers can lead to execution of malware. This isvVery interesting, but requires a proxy configured. None the less, I’d love to test this myself. Tyler Moffitt – Senior Threat Research Analyst
On Mobile
With regards to Stagefright, everyone is going to need patches to be 100% safe. But the good news is both Google and Samsung have announced 30-day update schedules, and upates for older devices are looking more and more likely. Google is acknowledging this issue much more than we expected and things are going in a good direction for android security. Cameron Palan – Senior Mobile Threat Research Analyst
On Exploits and Malware
The game over Zeus presentation was great. It was interesting to see the collaboration it took to take the botnet down. The FBI is offering $3 million USD for info leading to the arrest of the main guy they attribute to the botnet. The same guy also wrote CryptoLocker. Brenden Vaughan made a good observation that the same guy is probably behind Poweliks as it came out very shortly after game over was taken offline. Grayson Milbourne – Security Intelligence Director
Direct from the team, there is no mistaking the value of Black Hat and the surrounding events. From revelations to new ideas and concepts, day 1 has been packed with incredible information. We look forward to tomorrow and what it has in store.
If you have any questions for our team, comment below and we will respond with our thoughts and answers.
Security in the Rough
This week marks the 18th annual BlackHat USA conference where many of the world’s brightest security minds come together to discuss and showcase techniques capable of defeating and compromising a wide array of technologies. This year’s show arrives at a critical time in the world of online security and privacy, with near daily headlines of massive breaches and widespread critical vulnerabilities, all undermining the viability of mitigating today’s threats. All the while technology marches forward, integrating itself into new devices that will make up the future Internet of Things.
There were three headlines from the past few weeks which were especially concerning. The first was the discovery of the DYLD_PRINT_TO_FILE vulnerability affecting OS X Yosemite. What is so alarming about this vulnerability is that, with a single command, you are able to modify any file as a root user, including the sudoers file which stores usernames and passwords. This vulnerability is a perfect example of security oversight during the development process and how such an oversight can have a massive impact on security integrity. At least in this case, the exploit is specific to Yosemite and has been fixed in the latest OS X release.
The second alarming headline talked about 950 million Android phones being at risk of compromise by simply receiving a MMS. The exploit exists within a piece of code, called Stagefright, which is responsible for playing MMS messages. This vulnerable piece of code is part of all Android versions between 2.2 and 5.1, with an update needed to address the flaw. Unfortunately, it is very difficult to patch all devices as updates flow through network carriers at different speeds for different devices. While there are no current examples of this exploit being used in the wild, this won’t be the case for long; and the result of this vulnerability is that there will be millions of Android devices which are vulnerable to being remotely hacked.
The third, and most alarming, headline was for the recall of 1.4 million cars by Fiat Chrysler due to the demonstrated ability to remotely hack and control vehicles through the Uconnect infotainment system. What is so concerning about this hack is that so many critical systems could be controlled remotely. Everything from the wiper blades to the brakes to killing the engine. This begs the questions of, “Why does Uconnect need to have access to the brakes or engine?” It seems obvious that for basic security, these systems would be separated. However this hack demonstrated otherwise.
But as concerning as these headlines are, there is a silver lining. Unlike many headlines, these were all the result of security researchers who were looking to validate that proper security is in place. Thankfully in these cases, the researchers came forward to disclose their findings to improve security for everyone else. I cannot stress how important this type of behavior is to the viability of the future of security. The reality is that it is very difficult to design a bulletproof OS or application and that mistakes will be made. What is important is that when mistakes are discovered, that they are disclosed and addressed rather than sold on hacking forums to be used for malicious purposes. Some companies have done a great job in creating bug bounty programs to encourage the disclosure of vulnerabilities and I hope to see more of this in the future.
So back to BlackHat and why this year’s event is so timely and important. It is because BlackHat drives awareness and attention to the critical issues facing security from all angles. The conference also provides a common ground for collaboration and innovation that often finds its way into the products and technologies of the future.
As we move forward and embrace the Internet of Things, we must learn from our past mistakes and focus on ensuring we integrate the convenience technology has to offer without losing our privacy or security along the way.
10 Tips To Survive Black Hat 2015
Black Hat USA is next week, and with it will come some of the biggest hacker news of the year. From cars to mobile devices, all the way to the hotel HVAC, nothing is really out of the reach of the teams of white hat and black hat security researchers that are about to make their way to this conference. With that though will be the thousands of attendees outside those main groups looking to still get a bit of work done while at the conference. Well, we don’t want to encourage you avoiding it all together, but want to give you some tips to survive the event even with all your devices that you need. So below you will find 10 tips to survive Black Hat 2015. You are welcome to reuse them and share them with your team going, or even as reminders of the digital landscape and threats around.
Back to School Means Back to Security
Not a week goes by where we are not hearing about, reporting on, or providing comment to another major breach. From big box chains to mom and pop shops, it seems to be a constant source of news. Beyond the commercial and financial industries though are the education sectors, with colleges and private schools under attack at the same rate as their commercial distant-cousins. And with school less than a month away for most students, we think it is time for some reminders on personal security. While you will not be able to impact the local educational institutes security layer, you can add layers to your personal protection.
- Use two-factor authentication whenever possible.
We talk about this a lot because it is one of the easiest aspects of security to implement. Two-factor authentication adds another layer of security when logging into a website, be it e-mail, banking, or other websites. Some websites, such as Google, will text you a code when you login to verify your identity, while others have small devices that you can carry around to generate the code. Authentication apps are also available on all major smartphone platforms. Other types of two-factor authentication do exist as well, so look in the settings of your banking, shopping, and e-mail hosts for the option.
- Signup for login notifications
This security layer is often used in place of two-factor authentication, including by websites such as Facebook. If your account is accessed from an unfamiliar location, a notification is sent via e-mail, app, or text-message to the account holder. This is a great layer of security that offers you on-the-go protection. This feature, if offered, can usually be found in the security settings of the website, such as banking and social media, you are accessing.
- Change your passwords before school starts
There is a reason your office requires regular password changes for your e-mail. Even if your password is compromised, by changing it regularly across all your accounts, you remove the chance of your account being accessed. A pro-tip would be to set a reminder for every 90 days on your calendar with a link to all your accounts settings pages. It makes it easiest to click through and make the changes regularly.
- Increase junk filtering and avoid clicking through on e-mails
You just received an e-mail from a teacher asking for you to login and verify your school credentials. Many phishing schemes start with something looking very innocent and official, but lead unassuming users to websites designed to collect the information direct from you. If you receive an e-mail from one of the account-holding websites, or even a known person, open a new tab and go direct to the website instead of clicking the links provided. It adds only a few seconds to the access, but keeps you out of any legit-looking phishing websites. Most legitimate services will never ask you for your login credentials, so make sure to avoid giving out this information.
- Use an up-to-date security program
Whether you use Webroot SecureAnywhere or another product on the market today, ensure you have the most up-to-date version and have the correct security settings enabled. Security programs are designed to keep the malicious files such as keyloggers and data-miners off your computer and the user protected. This direct layer of security ensures your devices, from phones to tablets to computers, are all protected when you are downloading and accessing files. Note that some programs, such as Webroot SecureAnywhere, are always up-to-date and require no further action from the user..
While schools will continue to be a target, you can work to minimize any breach impact on your personal data by following these steps. And if you were to receive news that your education institution has been breached, use these steps to go back and conduct a personal audit, while also taking advantage of credit alerts and other tools out there.
Encryptor RaaS (Ransomware as a Service)
A new ransomware has emerged and its very similar to tox as it is created for hackers to easily design encrypting ransomware payloads to distrube from their botnets. Since the creator of Tox was selling his operation, this could very well be the end result of that. The idea is to contract hackers with already operational botnets and campaigns use this page to create encrypting ransomware binaries to their specifications and then hand off 20% of their succussful scams to the Encryptor RaaS author.
All a hacker has to do with this page is just input the bitcoin wallet address they want the funds to go to. Then customize the price they want for immediate payment, late payment, and lastly a timer for what is considered a late payment.
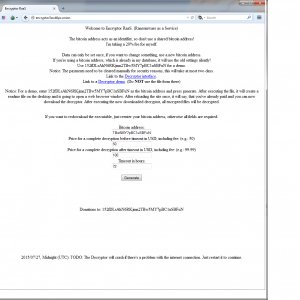
Skip forward to infecting a victim and there is no GUI popup. Just all your documents are now encrypted and you have this new instructions text at every directory.

Typically you have to install a layered tor browser to get to here, but tor2web currently is supporting a gateway to the page even if you’re just using a normal browser like firefox or chrome. Here is what you’ll be presented with.

Instructions are fairly clear on how to install a bitcoin wallet and send money to the hackers holding your files ransom. If you wait too long then the price will go up – and is set by the generator we showed earlier. Once you have paid the ransom this page will update showing “PAYED” and will then have a link to the decryptor. The decryptor doesn’t have a GUI either and will just run in the background until all files are decrypted.
MD5 Analyzed: D87BA0BFCE1CDB17FD243B8B1D247E88
Additonal MD5 Analyzed: ECDACE57A6660D1BF75CD13CFEBEDAEE
Webroot will catch this specific variant in real time and heuristically before any encryption takes place. We’re always on the look out for more, but just in case of new zero day variants, remember that with encrypting ransomware the best protection is going to be a good backup solution. This can be either through the cloud or offline external storage. Keeping it up to date is key so as not to lose productivity. Webroot has backup features built into our consumer product that allow you to have directories constantly synced to the cloud. If you were to get infected by a zero day variant of encrypting ransomware you can just restore your files back as we save a snapshot history for each of your files up to ten previous copies. Please see our community post on best practices for securing your environment against encrypting ransomware.
Macs are immune to malware? Yet another Apple exploit…
Yesterday information was published online through www.theregister.co.uk discussing an exploit that was discovered in the Mac OSX 10.10 Yosemite operating system. The discovered exploit allows a user to gain root access on a machine without any admin credentials. The exploit uses an environment variable called DYLD_PRINT_TO_FILE that was added in the Yosemite operating system, and is used by the OS to specify where the dynamic linker logs error messages. It was discovered however that the environment variable can be used maliciously in order to modify files that are owned by the “root user” account. The bottom line is that with one basic line of code a malware author could easily do away with the password requirement for the user account being compromised, therefore giving them full reign on the system.
While this exploit has not yet been seen implemented into any new malware in the wild, it is important to be aware that such a huge vulnerability exists. As usual, Mac users should always exercise prudence when downloading and installing software onto their machines, as well as download a reliable internet security app. In addition, the exploit is not present in older versions of Mac OSX, such as Mavericks, and is not present on the 10.11 beta of El Capitan.
The vulnerable code is found below
echo ‘echo “$(whoami) ALL=(ALL) NOPASSWD:ALL” >&3’ | DYLD_PRINT_TO_FILE=/etc/sudoers newgrp; sudo -s
Another Hacking Team exploit that is CRITICAL for ALL Windows systems – CVE-2015-2426
 It just doesn’t seem to end with all the exploits being revealed by the Hacking Team dump earlier this month. This vulnerability could allow remote code execution if a user opens a specially crafted document or visits an untrusted webpage that contains embedded OpenType fonts. The Adobe Type Manager module contains a memory corruption vulnerability, which can allow an attacker to obtain system privileges on an affected Windows system.
It just doesn’t seem to end with all the exploits being revealed by the Hacking Team dump earlier this month. This vulnerability could allow remote code execution if a user opens a specially crafted document or visits an untrusted webpage that contains embedded OpenType fonts. The Adobe Type Manager module contains a memory corruption vulnerability, which can allow an attacker to obtain system privileges on an affected Windows system.
Adobe Type Manager, which is provided by atmfd.dll, is a kernel module that is provided by Windows and provides support for OpenType fonts. A memory-corruption flaw (buffer underflow) in Adobe Type Manager allows for manipulation of Windows kernel memory, which can result in a wide range of impacts. This vulnerability can allow an attacker to gain SYSTEM privileges on an affected Windows system. Hackers would use this to infect users systems with any type of malware and gain remote control access if they desired – all without notifying the user. Also, this vulnerability can be used to bypass web browser and other OS-level sandboxing and protections.
This is a confirmed exploit on Windows XP and up and Windows Server 2003 and up. Since Windows XP and Windows Server 2003 are no longer supported by Microsoft, there is no patch for users on those operating systems so we HIGHLY advise that you migrate to a newer operating system. Windows Vista, 7, and 8 users are going to have an update rolled out shortly that will patch this vulnerability so make sure you keep an eye out for updates. More info here
Turning failure into success
As a security professional it’s hard to say ‘I told you so’ but as far back as 2009-2010 Webroot was saying that the endpoint market was broken and that a new approach to stopping malware infections on endpoints was needed. At that time the rest of the endpoint security market was particularly quiet on their efficacy at stopping attacks they just kept pointing at meaningless and some would say gamed ‘independent’ test results about how great their efficacy was.
Of course the ‘chickens came home to roost’ and that efficacy was thrown under a Mack Truck over the past couple of years by the volume and frequency of new malware and its variants that was hitting endpoints. The attack patterns changed too. No longer did you have broad-based attacks now you had targeted, individualized and especially in 2014 continuous attacks aimed at known individuals in organizations.
The availability and open nature of today’s communications plus the exploitation by the big Internet players and other actors has meant everyone’s life can be pried into and used to make life more convenient, but with that convenience comes a dark side (that for many observers is seemingly winning and cannot be thwarted.) Frankly neither I, nor Webroot believe that.
Attackers’ methods can be turned against them and the attentions of the priers thwarted by only allowing them to access what you want them to access. Lots of security vendors believe that too. If those who want manipulate get smart then we need to get smarter. We can have smarter cybersecurity and we can make it consciously work together to make life very difficult indeed.
At Black Hat Webroot will be demonstrating and talking about some of the security solutions and collective threat intelligence that by working together make endpoints, servers, networks and the Internet safer for us all and are turning previous failures into success. In the end its choosing battles and winning the wars that will matter.
Happy Video Game Day 2015
Webroot would like to wish our fellow gamers a happy Video Game Day! To celebrate this epic game playing day, we want to help keep you safe and highlight the top motivation for PC gaming attacks.

Gamers are being targeted more and more by malware, trojans, and keyloggers, especially those that participate in pay-to-play games and MMORPGs (Massively Multiplayer Online Role-Playing Game). Your accounts, personal identity, banking information and even credit card numbers can be stolen if you are playing without a cyber-security solution. The PC gaming market is increasing rapidly and is expected to reach $30.9 Billion in 2016, and with that, the targets are getting bigger and more lucrative.
Top Motivations for PC Gaming Attacks:
- Financial Gain: To obtain records of your secure data
- Digital Assets: Take control of your account to sell or trade
- Social Hacking: Damage to user reputation and identity theft
- Free Gaming: Access to your user account for free gameplay
So the motivation is there, but some people might insist that the threats do not exist. But already this year, we have seen a large variety of attacks targeting gamers through a variety of methods. Some are simple, others more advanced, but the threats against gamers and their accounts do exist.
Top Threats in 2015:
- Spear Phishing: Targeted attacks via email and game chat to steal login information
- Keylogging: Captures keystroke information and sends it to the attacker
- Chat Attack: Hacking attempts where the attacker embeds the attack via chat systems on Skype, TeamSpeak, Steam, League of Legends, etc.
- Ransomware: Malware that restricts access to a system until the ransom is paid
- Trojans: The attacker sends the system instructions to install malicious software or remote execution of system commands and other data intrusion
Some gamers defend the idea of installing no antivirus security one their machines, citing claims of slowed performance and interruptions. While traditional security solutions often have gamer modes, they still impact security, and others will turn off security layers during game play, rendering machines less secure.
Top Reasons Why Gamers Don’t Use a Security Program:
- They rely on free diagnostic and clean-up tools
- There are too many alerts and interruptions during gameplay
- It slows down their gameplay
- They aren’t concerned about infections
- It requires switching to a gamer mode
But new technologies do exist that are designed to keep gamers safe while playing online, even in this ever increasing threat world. Webroot SecureAnywhere for Gamers will not scan or update during your game and does not require a gamer mode.
Using real-time protection without sacrificing performance be using the cloud, Webroot SecureAnywhere ® Antivirus for PC Gamers reduces maintains a small footprint the PC increasing drive space, decreasing hard drive read/writes, and improving overall performance. No longer do gamers need to make the sacrifice of turning off security software to increase their speeds. One of a gamer’s worst nightmares is being milliseconds away from a kill shot or reaching a checkpoint when their screen minimizes for a Windows Update or a system scan from their antivirus solution. That’s why Webroot’s gamer security will not alert you or minimize your screen during gameplay. We understand the importance of lightning fast internet connections and zero slowdowns during gameplay.
To learn more about Webroot SecureAnywhere ® Antivirus for PC Gamers, click here.
The OPM data breach was probably inevitable
Breaches big and small have been in the news, from small organizations losing banking files to global groups like Sony losing seemingly everything to hackers. But with the recent Office of Personnel Management (OPM) hack that was revealed recently, with anywhere between 18 and 32 billion individual records stolen by digital infiltrators, we have not seen a breach to this scale.
The scary, and somewhat disappointing aspect, is that the breach was probably inevitable.
Encryption Not Present
While OPM Director Katherine Archuleta had noted the need for an upgrade in the technology and implementation of encryption on all the data 18 months prior, the need was dismissed due to the age of the networks. During testimony today with the House Oversight and Government Reform Committee, she said “It is not feasible to implement on networks that are too old.”
Contractors Credentials
On the other side, would encryption had helped as the breach all started with compromised contractors credentials? Dr. Andy Ozment, assistant secretary, Office of Cybersecurity and Communications stated during the same hearing that encryption would “not have helped in this case” as the attackers would have had the data encrypted once they accessed the machine.
Previously Breached
In July of 2014, the OPM had a breach of its networks, apparently with the breach being traced back to China. OPM downplayed the breach stating that no personal data was stolen but provided credit monitoring to employees. Following this breach, the Office of the Inspector General completed an audit of the whole department, finding significant failures in the security layers. The full investigation also found that there was no inventory of the endpoints, devices, databases, and investigators were not able to see if OPM was scanning for breach and vulnerabilities.
Two-Factor Authentication
During the same audit “We believe that the volume and sensitivity of OPM systems that are operating without an active Authorization represents a material weakness in the internal control structure of the agency’s IT security program,” the report concluded. In a day and age when two-factor has become a standard recommendation from the local IT friend to even the CIO of the US Department of Energy (http://energy.gov/cio/two-factor-authentication), this is one of the biggest failures within the OPM’s security layer. Lacking a physical CAC card or even phone authentication for login into the local machines and thus into the network could have saved the data from falling into the wrong hands.
These are just four of the issues leading up to this breach, areas often and exhaustively preached by security companies and professionals worldwide as the biggest and most vulnerable areas of attack. Beyond this, the audit itself not only highlighted the areas in need of immense improvement and increased security, but essentially laid the groundwork for the hackers, exposing all the weaknesses that have since been exploited, resulting in this breach.
For the full Inspector General report cited above from 2014, please click here: https://www.opm.gov/our-inspector-general/reports/2014/federal-information-security-management-act-audit-fy-2014-4a-ci-00-14-016.pdf