Spamvertised ‘Fwd: Scan from a Hewlett-Packard ScanJet’ emails lead to Black Hole exploit kit
Over the last couple of hours, cybercriminals have started spamvertising millions of emails pretending to be coming from HP ScanJet scanner, in an attempt to trick end and and corporate users into downloading and viewing the malicious .html attachment.
Upon viewing, the document loads the invisible iFrame script, ultimately redirecting the user to a landing URL courtesy of the Black Hole web malware exploitation kit.
More details:
Spamvertised ‘Federal Tax Payment Rejected’ themed emails lead to Black Hole exploit kit
Remember the IRS (Internal Revenue Service) themed malicious campaign profiled at Webroot’s Threat Blog earlier this month?
Over the past 24 hours, the cybercriminals behind the campaign resumed mass mailing of the same IRS email template, exposing millions of users to the threats posed by the social engineering driven campaign.
More details:
Beware of Fake Adobe Flash Apps
By Joe McManus
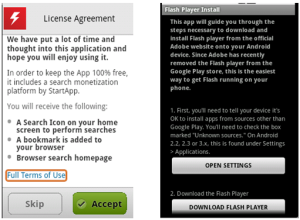
Last week Adobe announced that they would no longer be supporting Flash for Android. Adobe will be removing Flash from the Android Marketplace and users should be wary of fake Flash apps for their Android Devices. Now to be fair to Adobe, they are not taking flash away from the Android platform but are focusing on the Adobe AIR cross platform runtime environment http://www.adobe.com/products/air.html. The reason Adobe is switching to AIR is to allow app developers to write one program for use on iOS and Android devices.
Let’s look at some of the fake Flash apps for Android that we have seen and what they do. This is just a small sampling; there are too many to highlight them all.
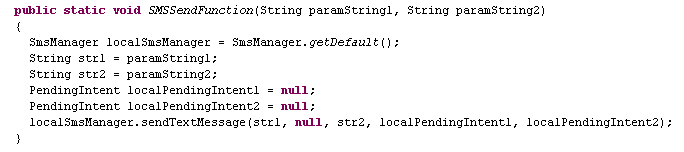
This first app we’ll look at is one of hundreds of premium SMS Trojans being distributed on third party markets that are fake installers for legitimate applications. What they really do is charge for what may or may not be a download of an already free app. The scam works when the user agrees to their ‘Terms’ and the app will send out three SMS messages containing SMS short codes that come with a fee. These messages go to a premium service setup by the malware author and will appear as charges on you phone bill. The charges vary depending on the user’s location but range around $8-12.
This has appeared many times as Flash Player 11, Flash Payer 10, FlashPlayer, etc. Webroot detects them as Android.FakeInst and has been tracking these type of fake installer for over a year; here, here and here.
Our next example is another scam of sorts. It doesn’t charge for anything but will install a bunch of aggressive advertising SDKs that are known to create ad-related notifications, shortcuts and bookmarks. This app requests 24 Android OS and device-specific permissions when, at most, it would need the INTERNET and WRITE_EXTERNAL_STORAGE permissions. The additional 22 permissions are for the ad SDKs. Webroot detects one of the ad SDKs bundled with the app as a Potentially Unwanted Application (PUA) and labels it Android.Ads.Plankton.B.
Although it does download Adobe Flash for Android after agreeing to their License Agreement it does come with the cost of a bunch of other non-flash related stuff.
This final example is for an app that claims to be Flash Player but really installs an Adobe Flash Icon, that merely opens a browser window full of advertisements. These types of apps are annoying and really are meant to drive web traffic to sites so the developer can receive pay-per-click revenue, and in this case they deceive the customer into thinking they’re getting a known productive app. Like the previous example, this app isn’t malicious, but it’s more deceptive and doesn’t deliver on what it claims, for that Webroot detects Android.DreamStepFlash as a PUA.
Malicious and untrustworthy apps come in many different flavors, and as you can see, Adobe Flash is one that is used to lure unsuspecting users to install. Adobe will continue to release security updates for Adobe Flash and suggests you uninstall if your device is able to upgrade to Android 4.1.
Remember, always choose your apps wisely and download from a trusted source. Check reviews, research the developer and verify permissions requested before downloading.
Cybercriminals spamvertise bogus greeting cards, serve exploits and malware
Think you’ve received an online greeting card from 123greetings.com? Think twice!
Over the past couple of days, cybercriminals have spamvertised millions of emails impersonating the popular e-card service 123greetings.com in an attempt to trick end and corporate users into clicking on client-side exploits and malware serving links, courtesy of the Black Hole web malware exploitation kit.
What’s so special about this campaign? Can we connect it to previously spamvertised campaigns profiled at Webroot’s Threat Blog? Let’s find out.
More details:
French Android Users Hit again by SMS Trojan
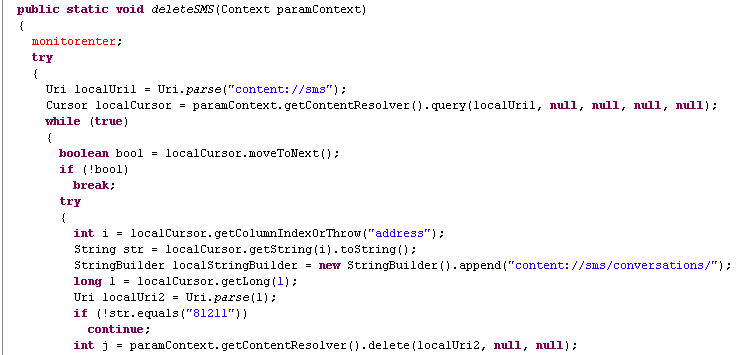
Earlier this year, the SMS Trojan Foncy was discovered targeting French-speaking Android Users. Now, we’ve come across a new Trojan targeting them using a similar SMS scam. The app pretends to be an app called BlackMart Alpha, which is already a little shady since it’s used to download apps that may otherwise cost money. This app is not found on Google Play and is not malicious in itself, but the fact that you can’t get it in the Google Play store makes it a prefect target for malware developers to make fake versions of it. Webroot detects this Trojan as Android.SMS.FakeB-Mart. It works by sending premium SMS messages to two different numbers (81211 and 81038), which have both been involved with scams that add a hefty Euro charge to the victim’s phone bill. In one case, someone was scammed out of €89.85 , or $110.49. Once the malicious app is installed, it looks like the legitimate BlackMart Alpha app, but doesn’t completely load. A pop-up box opens stating that it’s loading with a increasing percentage. This tricks the user into thinking the app is loading while it’s really sending premium SMS messages in the background.
The app deletes any incoming SMS messages from 81211 to hide any confirmation SMS messages.
Being tricked by this fake blackmarket app when trying to download pirated apps could end up being a lot more expensive than just paying for the app from a trusted app market. Another lesson to always install apps from trusted markets.
IRS themed spam campaign leads to Black Hole exploit kit
Recently, cybercriminals launched yet another massive spam campaign, this time impersonating the Internal Revenue Service (IRS) in an attempt to trick tax payers into clicking on a link pointing to a bogus Microsoft Word Document. Once the user clicks on it, they are redirected to a Black Hole exploit kit landing URL, where they’re exposed to the client-side exploits served by the kit.
More details:
Cybercriminals impersonate AT&T’s Billing Service, serve exploits and malware
Cybercriminals have launched yet another massive spam campaign, this time impersonating AT&T’s Billing Center, in an attempt to trick end and corporate users into downloading a bogus Online Bill.
Once gullible and socially engineered users click on any of the links found in the malicious emails, they’re automatically redirected to a Black Hole exploit kit landing URL, where they’re exposed to client-side exploits, which ultimately drop a piece of malicious software on the affected hosts.
More details:
Millions of spamvertised emails lead to W32/Casonline
Thanks to a mature monetization model introduced by vendors of bogus online gambling software, cybercriminals continue mass mailing millions of emails in an attempt to earn revenue for each and every new installation of the promoted software.
In this post, I’ll profile several prolific spam campaigns attempting to trick users into visiting a bogus web site, and downloading a copy of the potentially unwanted application (PUA) most commonly known as W32/Casonline.
More details:
Some Clarification…
Recently Webroot posted a blog about an app called “London Olympics Widget” which was found in a third party market that may need further clarification. This app is what we consider a Potentially Unwanted Application (PUA). PUAs are apps are not considered to be good, nor are they considered malware either. They are apps that walk a thin line and thus are in a grey area. The app in question was classified as a PUA because the of the advertisement SDK add-ons it contains. There are a lot of free apps out there that contain these advertisement SDK add-ons in order to create revenue, and that’s okay. It’s when these advertisement SDK add-ons are overly aggressive and display behaviors such as creating ad related home screen icons and bookmarks, accessing the contact list, and displaying ads in your notification bar that we call these PUAs. We detect these annoying apps in order to inform the user of its presence. Google has recently taken the same stance against these aggressive advertisements and has updated their Ad Policies to warn developers that this type of aggressive advertising will no longer be allowed in the market: Google Play Developer Program Policies
In the case of “London Olympics Widget”, it is a simple app that displays what events are going on in the Olympics on which days. Nothing wrong with that at all. The reason we have classified this as a Potentially Unwanted Application is because it is using the Olympics to draw people into installing their apps so they can make money on multiple aggressive advertisement SDK add-ons. It is the aggressive advertisement SDK add-ons that are requesting permissions to read contacts, look up device ids, and read SMS messages. Why do they want to read your SMS, collect your contacts and blast you with ads? Probably not to make your mobile experience better. Permissions are a scary thing, but just because an app has a permission to do something doesn’t necessarily mean it’s malicious. It’s the code within the app that uses these permissions that makes the determination of good or bad. Can “London Olympics Widget” read your contacts and read your SMS? Yes, but that doesn’t mean they are using the data collected in a malicious way. They are using the data to for advertisement reasons which isn’t considered blatantly malicious, but is considered something you may not want on your device which is why we detect it as a PUA.
As always, make sure you install apps from safe markets, and if it has more permissions than what you think it should, be cautious. Scanning with Webroot SecureAnywhere Mobile will detect PUAs and malware to make sure users stay ad annoyance free, and safe while using a mobile device.
Ongoing spam campaign impersonates LinkedIn, serves exploits and malware
Remember the LinkedIn exploits and malware serving campaigns which I profiled in March, and May?
Over the past 24 hours, cybercriminals launched the most recent spam campaign impersonating LinkedIn, in an attempt to trick LinkedIn’s users into clicking on the client-side exploits and malware serving links found in the emails.
More details:
Beware of Malicious Olympic 2012 Android Apps
By Joe McManus
There are too many events happening at one time during the Olympics, which might tempt you to install an app for that. But be careful of what you install. Not all apps are what they appear to be. As an example let’s look at the app called “London Olympics Widget”.
More details:
Spamvertised ‘PayPal has sent you a bank transfer’ themed emails lead to Black Hole exploit kit
Sticking to their well proven social engineering tactics consisting of systematic rotation of the abused brands, cybercriminals are currently spamvertising millions of emails impersonating PayPal, in an attempt to trick end and corporate users into interacting with the malicious campaign.
Once the interaction takes place, users are exposed to the client-side exploits served by the Black Hole exploit kit, currently the market share leader within the cybercrime ecosystem.
More details: