by Tyler Moffitt | May 3, 2013 | Threat Lab
By Tyler Moffitt
Recently we have seen an increase in fake installer scams attempting to trick computer users into installing disguised rootkits directly on their machines. In this post, we want to highlight how a scam like this can be installed and infect a machine, including behavior to watch out for as well as how to remedy the situation if it were to arise.
In the case of this infection, we are utilizing a bogus Adobe Flash Player installer. Normally, this file would be downloaded from a website after a message stating “You need the latest version of Flash to view this video” appears. The file being downloaded would have a random name, such as ‘flashplayerinstallerxxxx.exe’.
(more…)

by Blog Staff | May 3, 2013 | Threat Lab
Everyday, new vendors offering malicious software enter the underground marketplace. And although many will fail to differentiate their underground market proposition in market crowded with reputable, trusted and verified sellers, others will quickly build their reputation on the basis of their “innovative” work, potentially stealing some market share and becoming rich by offering the tools necessary to facilitate cybercrime.
Publicly announced in late 2012, the IRC/HTTP based DDoS bot that I’ll profile in this post has been under constant development. From its initial IRC-based version, the bot has evolved into a HTTP-based one, supporting 10 different DDoS attack techniques as well as possessing a featuring allowing it to heuristically and proactively remove competing malware on the affected hosts, such as, for instance, ZeuS, Citadel or SpyEye.
More details:
(more…)

by Blog Staff | May 2, 2013 | Threat Lab
On a regular basis we profile various DIY (do it yourself) releases offered for sale on the underground marketplace with the idea to highlight the re-emergence of this concept which allows virtually anyone obtaining the leaked tools, or purchasing them, to launch targeted malware attacks.
Can DIY exploit generating tools be considered as a threat to the market domination of Web malware exploitation kits? What’s the driving force behind their popularity? Let’s find out by profiling a tool that’s successfully generating an exploit (CVE-2013-0422) embedded Web page, relying on malicious Java applets.
More details:
(more…)

by Blog Staff | May 1, 2013 | Threat Lab
Over the last day, cybercriminals have launched yet another massive email campaign to impersonate FedWire in an attempt to trick users into thinking that their wire transfer was processed incorrectly. Once they execute the malicious attachment, their PCs automatically become part of the botnet operated by the cybercriminal/gang of cybercriminals.
More details: (more…)

by Blog Staff | Apr 30, 2013 | Threat Lab
Recently we have seen an increase in fake Microsoft security scams, which function by tricking people into thinking that their PC is infected. With these types of scams there are a number of things to remember:
- Microsoft will never call you telling you that your PC is infected
- Never allow strangers to connect to your PC
- Do not give any credit card info to somebody claiming to be from Microsoft
- If in doubt, shut down your PC and call Webroot
The current scam will display a webpage that is very similar to the one in Figure 1. There are a number of ways to figure out that this is a false alert. The first is that it’s a website message and not a program; the second is that location of the web site will be a random string of letters.
These websites will normally only stay active for 24-48hrs before they are pulled down. The websites’ primary function is to get you to run a “removal tool” called “security cleaner”. This file is the infection and, if ran, will infect the PC and start displaying pop-ups (like the one in Figure 2).
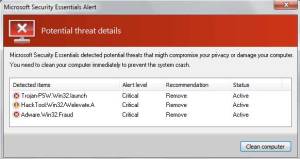
Figure 1: Fake Alert
At this stage, the PC is not infected so it’s safe to close the browser and ignore any alerts from the website. Noting the website that displayed the message is good idea as you can notify the webmaster (if it’s a legitimate website).
I have seen examples of this type of fake webpage being linked from advertising links. Using a browser that has a pop-up blocker will reduce the likelihood of encountering a bad advertising link. With scams like this, the most important way to stop getting infected is to be diligent when you’re online.
If a website asks you to run a file that you haven’t asked for, be extremely cautious. The same goes for emails (even from friends). Do not open executable files unless you are 100% sure they are good.
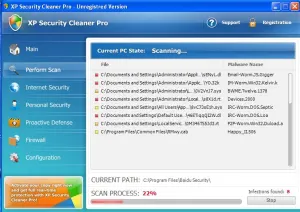
Figure 2: Fake AV Pop-up
Behavior
The info below is only a guideline as the payload can change. However, it follows the same pattern of dropping a fake AV that stops you from opening most programs.
- Drops a randomly named file in the current users folder (Fake AV payload)
- Creates a service for the above file
- Disables Windows Firewall or modifies the settings to allow the file full access to the PC
- Creates a number of files in the windows recycler folder (usually Zero Access)
- Flags any opened program as an infection (by modifying the open shell reg key)
- Fake AV will then prompt the user to pay to remove the detected “infections”
Webroot Detection logs:
Infection detected:
c:usersownerappdatalocalmicrosoftwindowstemporary internet filescontent.ie5wckxi56gsecurity_cleaner[1].exe
MD5: 68D9F9C6741CCF4ED9F77EE0275ACDA9
Detection rate of the file 28/46 Vendors on Virus Total.
Registry Changes:
Below is an example of some of the changes. The first shows how it modifies the open shell command so when you open any file it will run the Fake AV. The second shows the security center notifications that are disabled.
hkcrw1shellopencommand”C:UsersUserAppDataLocalgpt.exe
hklmsoftwareclientsstartmenuinternetiexplore.exeshellopencommand
HKLMSOFTWAREMicrosoftSecurity Center AntiVirusDisableNotify 00000001
HKLMSOFTWAREMicrosoftSecurity Center AntiVirusOverride 00000001
How to protect yourself from these scams
There are a number of ways to ensure your PC is protected from these types of scams. The first step is simply being aware that these scams exist! Also, make sure to:
- Use Webroot Secure Anywhere
- Keep Windows updates turned on and set them to automatically update
- Use a modern secure browser like Firefox or Chrome
- Update any 3rd party plugins (Java/Adobe Reader/Flash player)
- Use an ad-blocker add-on in Firefox/Chrome
I have seen a number of infections that would have been prevented if Windows was up to date. Microsoft is constantly updating Windows to patch various security updates.
Removal
Webroot SecureAnywhere automatically blocks the installation of the infection so it won’t even run (Figure 3). If the PC has no AV software installed, booting into Safe Mode with networking and installing Webroot Secure Anywhere will remove the threat. Manually removing this threat is possible; however, there may be some system damage that will need to be repaired.
Webroot support is always available to help with removal and questions regarding this infection. Please visit the Webroot support web site for more detail at: http://www.webroot.com/support/.
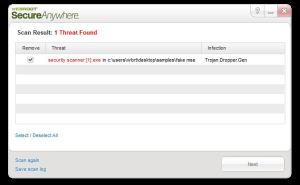
Figure 3: SecureAnywhere Removal

by Blog Staff | Apr 30, 2013 | Threat Lab
By Dancho Danchev
In 2013, you no longer need to posses sophisticated programming skills to manage a ransomware botnet, potentially tricking tens of thousands of gullible users, per day, into initiating a micro-payment to pay the ransom for having their PC locked down. You’ve got managed ransomware services doing it for you.
In this post I’ll profile a recently spotted underground market proposition detailing the success story of a ransomware botnet master that’s been in business for over 4 years, claiming to be earning over five hundred thousands rubles per month.
More details: (more…)

by Blog Staff | Apr 29, 2013 | Threat Lab
How are cybercriminals most commonly abusing legitimate Web traffic?
On the majority of occasions, some will either directly embed malicious iFrames on as many legitimate Web sites as possible, target server farms and the thousands of customers that they offer services to, or generate and upload invisible doorways on legitimate, high pagerank-ed Web properties, in an attempt to monetize the hijacked search traffic.
In this post I’ll profile a DIY blackhat SEO doorway generator, that surprisingly, has a built-in module allowing the cybercriminal using it to detect and remove 21 known Web backdoors (shells) from the legitimate Web site about to be abused, just in case a fellow cybercriminal has already managed to compromise the same site.
Are turf wars back in (the cybercrime) business? Let’s find out.
More details: (more…)

by Blog Staff | Apr 26, 2013 | Threat Lab
Relying on tens of thousands of fake “Your transaction is completed” emails, cybercriminals have just launched yet another malicious spam campaign attempting to socially engineer Bank of America’s (BofA) customers into executing a malicious attachment. Once unsuspecting users do so, their PCs automatically join the botnet operated by the cybercriminal/gang of cybercriminals operating it, leading to a successful compromise of their hosts.
More details: (more…)

by Blog Staff | Apr 25, 2013 | Threat Lab
Over the past couple of days, cybercriminals have launched two consecutive malware campaigns impersonating DHL in an attempt to trick users into thinking that they’ve received a parcel delivery notification. The first campaign comes with a malicious attachment, whereas in the second, the actual malicious archive is located on a compromised domain.
More details: (more…)

by Blog Staff | Apr 24, 2013 | Threat Lab
Following the recent events, opportunistic cybercriminals have been spamvertising tens of thousands of malicious emails in an attempt to capitalize on on the latest breaking news.
We’re currently aware of two “Boston marathon explosion” themed campaigns that took place last week, one of which is impersonating CNN, and another is using the “fertilizer plant exposion in Texas” theme, both of which redirect to either the RedKit or the market leading Black Hole Exploit Kit.
Let’s profile the campaigns that took place last week, with the idea to assist in the ongoing attack attribution process.
More details:
(more…)










