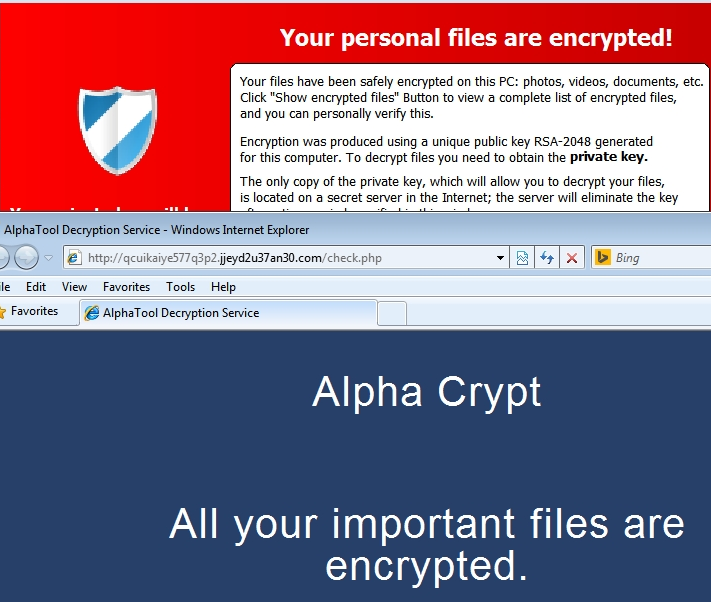
Search: Ransomware


Threat Recap: Week of January 24th
Reading Time: ~ 2 min.
Threat Recap: Week of January 3rd
Reading Time: ~ 2 min.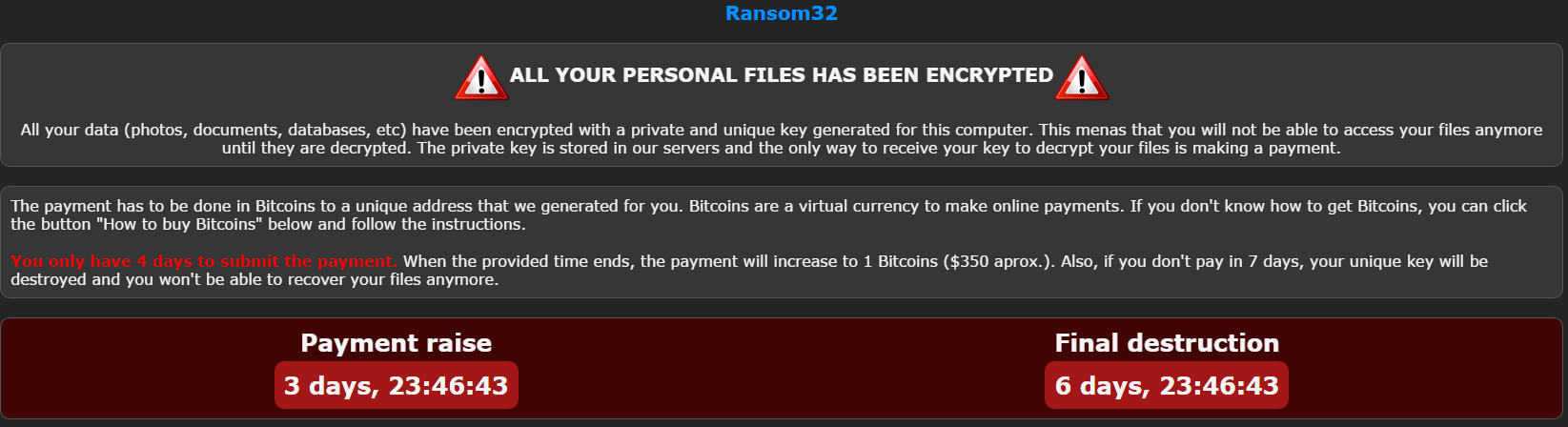
Ransom32 – A RaaS that could be used on multiple OS
Reading Time: ~ 3 min.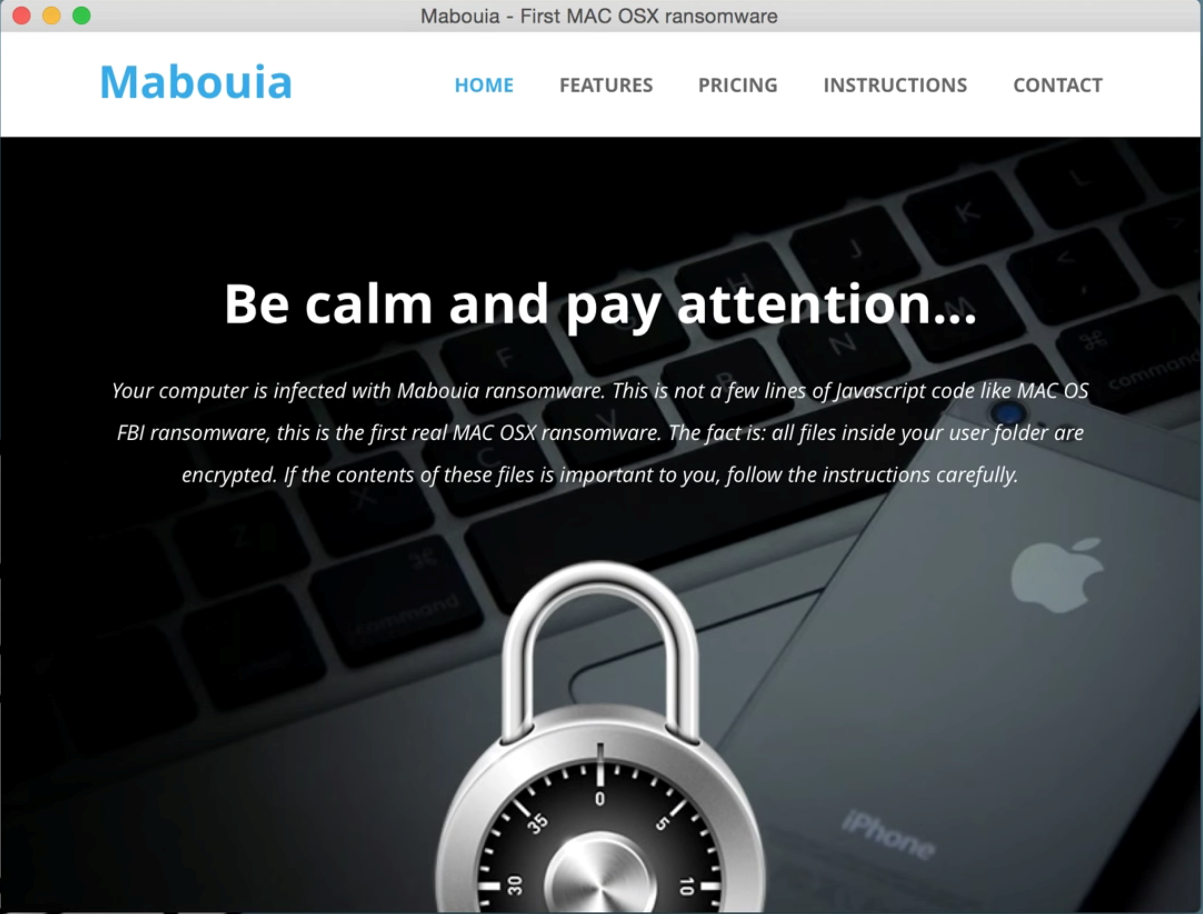
Is 2015 the Year of Mac Malware?
Reading Time: ~ 2 min.
CRYPTOWALL 4.0 (updated)
Reading Time: ~ 3 min.
FBI says to just pay the ransom
Reading Time: ~ 2 min.
ORX Locker
Reading Time: ~ 3 min.
Security Advice is fundamentally the same
Reading Time: ~ 2 min.
Happy Video Game Day 2015
Reading Time: ~ 3 min.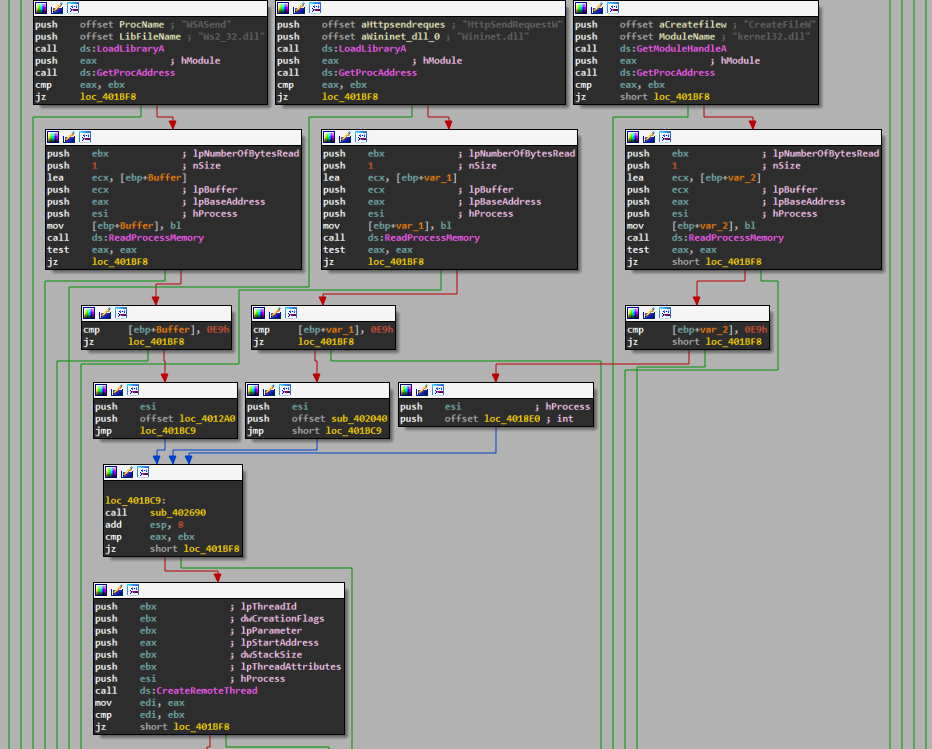
Rombertik
Reading Time: ~ 3 min.