Regular readers of Webroot’s Threat Blog are familiar with our series of posts detailing the proliferation of social engineering driven, privacy-violating campaigns serving W32/Casino variants. Relying on affiliate based revenue sharing schemes and spamvertised campaigns as the primary distribution vectors, the rogue operators behind them continue tricking tens of thousands of gullible users into installing the malicious applications.
We’ve recently intercepted a series of spamvertised campaigns distributing W32/Casino variants. Let’s profile the campaigns, provide actionable intelligence on the rogue domains involved in the campaigns, as well as related MD5s known to have interacted with the same rogue infrastructure.
More details:
Sample screenshots of the landing pages for the rogue casinos: 



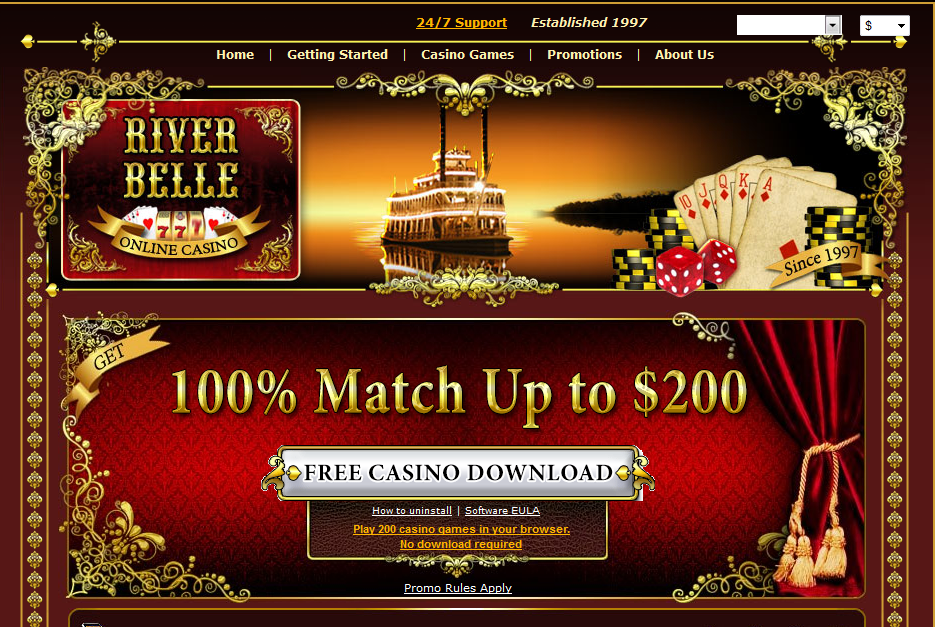

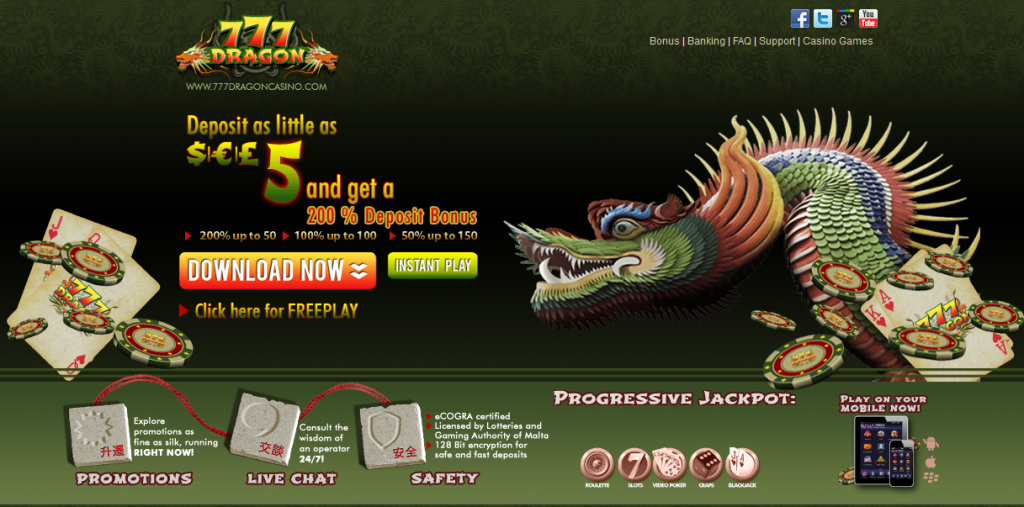
Spamvertised URLs:
hxxp://bit.ly/1brCoxg
hxxp://bit.ly/1bQRudq
hxxp://bit.ly/1mLQr5I
hxxp://bit.ly/MCOyaL
hxxp://bit.ly/1ec3UMN
hxxp://bit.ly/1hN6Vbd
hxxp://bit.ly/1mQ3XFu
hxxp://bit.ly/17DJ4pZ
hxxp://bit.ly/1ec2JNa
hxxp://bit.ly/1fBY6d5
W32.Casino PUA domains reconnaisance:
hxxp://rubyfortune.com – 78.24.211.177
hxxp://grandparkerpromo.com – 95.215.61.160
hxxp://kingneptunescasino1.com – 67.211.111.169
hxxp://riverbelle1.com – 193.169.206.233
hxxp://europacasino.com – 87.252.217.13
hxxp://vegaspartnerlounge.com – 66.212.242.136
Sample detection rates for the W32/Casino PUA:
MD5: b80db6ec0e6c968499ce01232fbfdc5c – detected by 3 out of 50 antivirus scanners as as W32/Casino.P.gen!Eldorado
MD5: 8326886267203e07145f63adf2e8f0a1 – detected by 3 out of 50 antivirus scanners as Heuristic.BehavesLike.Win32.Suspicious-DTR.S
MD5: a2a545adf4498e409f7971f326333333 – detected by 3 out of 50 antivirus scanners as W32/Casino.P.gen!Eldorado
MD5: 1cd6db7edbbc07d1c68968f584c0ac82 – detected by 3 out of 49 antivirus scanners as W32/Casino.P.gen!Eldorado
Once executed the sample phones back to:
clatz.fileslldl.eu – 87.248.203.254
Known to have been downloaded from the same IP (87.248.203.254) are also the following W32/Casonline variants:
MD5: 06c6b0381cde4720a5204ac38a5f22b9
MD5: 1022bef242c7361866f7af512ec893e0
MD5: c1a6055f5d240d3681febc6bd77701eb
MD5: e5fd6aa437b3520f35337d2dd7139f9a
MD5: 6f6713077249800818f26b7469eaf175
MD5: 6ebdf6f7187effe7b52463cf7241297a
MD5: 6ed118798a19a5dbf63a9279f33e0542
MD5: 6b651437a4553b91139178a930247035
MD5: e1beeae4d07942c7fca6eea945c9bdcd
MD5: 6ab968f86300ca677e9700f7c2dee8be
MD5: 6a872111b70e401cf083a7d27b45a74e
MD5: f85fa2bb2dff0333650db371e323e962
Webroot SecureAnywhere users are proactively protected from these threats.







Gatifloxacin side effects caused concern
<a href=”http://www.medchemexpress.com/Gatifloxacin.html">Gatifloxacin</a> is a broad-spectrum fluoroquinolone antibiotic drugs in recent years developed a new antibiotic . But since 1999, the drug has been approved for listing the world how patients taking gatifloxacin in patients with symptoms of hypoglycemia and hyperglycemia . The researchers began to notice last year that the drug caused health problems, especially changes in glucose metabolism .
Gatifloxacin in 1999 by the U.S. Food and Drug Administration (FDA) approved for listing in April 2002 in Japan approved for listing . Gatifloxacin for the treatment of pneumonia, bronchitis and urinary tract , kidney , skin, and other infectious diseases , and generally for the treatment of gonorrhea , and urinary tract infection in the lungs . Doctors often in the nature of the infection is not very clear circumstances to prescribe this drug ,<a href=”http://www.medchemexpress.com/Gatifloxacin-hydrochloride.html">Gatifloxacin hydrochloride</a> the main consideration of its wider antibacterial spectrum . However, in clinical use, found that the drug can lead to changes in glucose metabolism , and changes in blood sugar can cause coma and other serious problems , even death. Patients with symptoms usually begin within 5 to 10 days after taking the drug .
According to the U.S. “Los Angeles Times ” Web site on March 2 , entitled ” Antibiotics may cause elderly glucose ,” the article reads : Elderly patients taking the widely used antibiotic gatifloxacin (Gatifloxacin) can cause elevated blood sugar, may be hospitalized resistance will increase nearly 16 -fold ; this drug can also cause lower blood sugar , increase the likelihood of patients hospitalized three times .<a href=”http://www.medchemexpress.com/Gatifloxacin-mesylate.html">Gatifloxacin mesylate</a> This conclusion on the cause of some doctors recommend this drug will be withdrawn from the market .
“New England Journal of Medicine” website published a research report this year showed that: the patients taking the drug 1% of hospitalization . Several previous studies have shown that diabetes increases the risk of blood sugar abnormalities occur after taking this antibiotic , also appeared several deaths. This latest study suggests that all patients taking the drug are at risk , not even in patients with diabetes as well. Authors of the study said, because other antibiotics have the same effect, there is no reason to continue using this drug.
U.S. drug manufacturer Bristol-Myers Squibb Company also said: The study concluded that ” after-sales experience to date is consistent with our ” so that they take into account when applying changes to the specification of these conclusions .
February 16 ,<a href=”http://www.medchemexpress.com/Clotrimazole.html">Clotrimazole</a> the official FDA website message : add a new contraindication in gatifloxacin TEQUIN (Gatifloxacin) SmPC : diabetes drug may cause side effects, increased patient symptoms of hypoglycemia or hyperglycemia risks, this may result in premature aging , degradation of renal function , diabetes disabled.
March , Health Canada and Bristol-Myers Squibb Company jointly issued the relevant gatifloxacin safety alert bulletins.
And there are four of these drugs similar to fluoroquinolones , some of which have been withdrawn from the market or severely restricted , respectively temafloxacin (Temaflloxacin), grepafloxacin (Grepafloxacin), sparfloxacin (Sparfloxacin ) and Qu difloxacin (Trovafloxacin).
May 12 , FDA website “Drug shortages bar” in the release of the Bristol-Myers Squibb Company announced VincentJ.Bilinsky vice president of trade on the Canadian market gatifloxacin termination statement . <a href=”http://www.medchemexpress.com/Meropenem.html">Meropenem</a>The statement to consumers , said: The company decided to terminate TEQUIN Paradox (Gatifloxacin) plus gatifloxacin tablets for business behavior and injection , based on global trends in the U.S. market structure and commercial considerations and the antibiotic products , as well as restructuring the company strategy the company will from June 2 to stop the supply of drugs to the U.S. pharmaceutical wholesalers.
Medchemexpress Can provide the above product,its website:<a href=”http://www.medchemexpress.com">www.medchemexpress.com</a>