With millions of Android users continuing to acquire new apps through Google Play, cybercriminals continue looking for efficient and profitable ways to infiltrate Android’s marketplace using a variety of TTPs (tactics, techniques and procedures). Largely relying on the ubiquitous for the cybercrime ecosystem, affiliate network based revenue sharing scheme, segmented cybercrime-friendly underground traffic exchanges, as well as mass and efficient compromise of legitimate Web sites, for the purpose of hijacking legitimate traffic, the market segment for Android malware continues flourishing.
We’ve recently spotted, yet another, commercially available DIY cybercrime-friendly (legitimate) APK injecting/decompiling app. The tool is capable of facilitating premium-rate SMS fraud on a large scale through the direct modification of legitimate apps to be later on embedded on Google Play through compromised/data mined publisher accounts.
Let’s take a peek at the tool, discuss its features, and relevance in an Android malware market segment which is largely dominated by DIY mobile malware generating revenue sharing affiliate based networks.
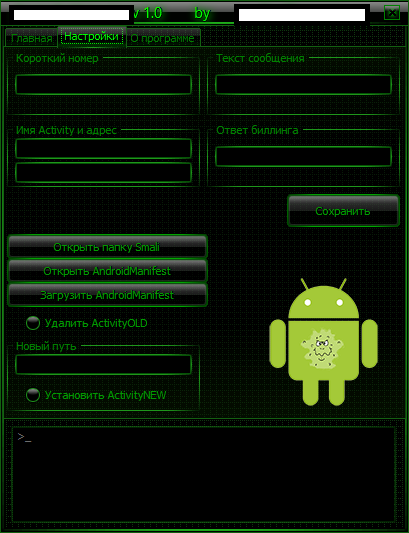
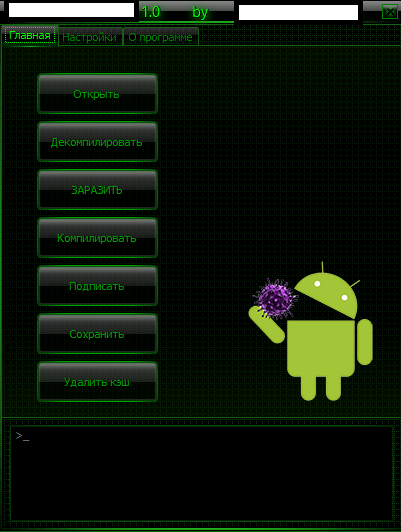
Sample screenshot of the DIY cybercrime-friendly (legitimate) APK injecting/decompiling app:
Basically, the tool is capable of directly injecting premium-rate type of SMS functions into a legitimate app. Once infected, the next step is to socially engineering a gullible end user into installing it which can be easily accomplished by taking advantage of a legitimate marketplace’s reputation. It’s currently priced at $1,403.
Despite the availability of built-in protection features on Android devices, such as the prevention of installation of apps from unknown sources, and advanced item validation checks, we’re certain that cybercriminals will continue to efficiently populate the Android marketplace with rogue/malicious/fraudulent apps. Despite the centralized nature of the Android app marketplace, in 2014, among the most popular traffic acquisition tactics remains cybercrime-friendly traffic exchanges as well as injected/embedded legitimate Web sites participating in massive Web malware based campaigns for the purpose of hijacking/abusing legitimate traffic.
We’ll continue monitoring the development of the tool, and post updates as soon as new developments take place.