This is the third of a three-part report on the state of three malware categories: miners, ransomware and information stealers.
Ransomware is any malware that holds your data ransom. These days it usually involves encrypting a victim’s data before asking for cash (typically cryptocurrency) to decrypt it. Ransomware ruled the malware world since late 2013, but finally saw a decline last year. The general drop in malware numbers, along with defensive improvements by the IT world in general (such as more widespread backup adoption), were factors, but have also led this threat to become more targeted and ruthless.
Delivery methods
When ransomware first appeared, it was typically distributed via huge email and exploit kit campaigns. Consumer and business users alike were struck without much discretion.
Today, many ransomware criminals prefer to select their targets to maximise their payouts. There’s a cost to doing business when it comes to infecting people, and the larger the group of people you are trying to hit, the more it costs.
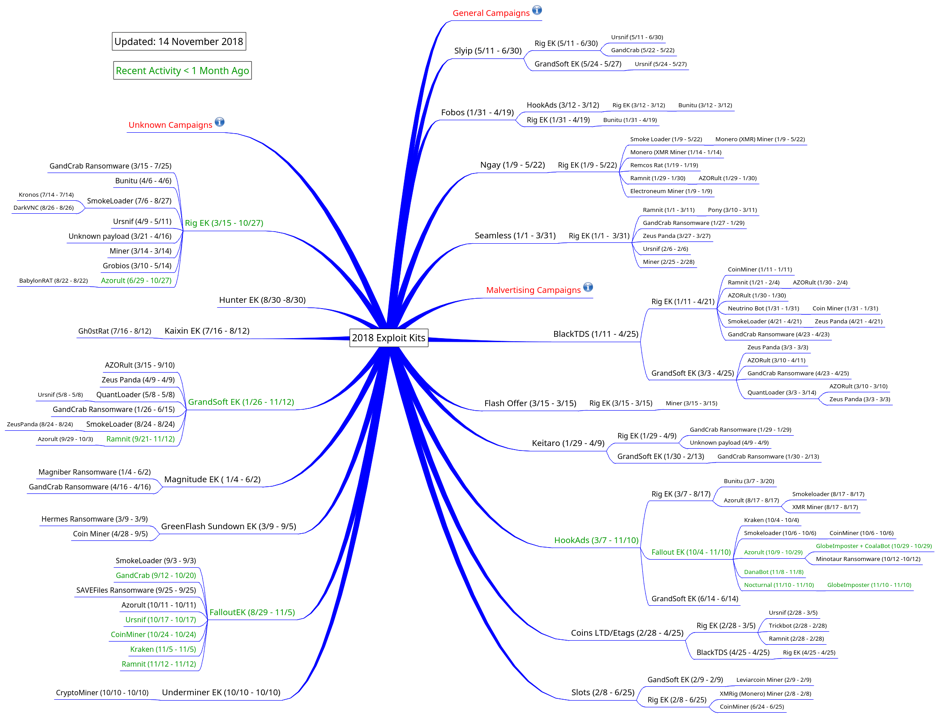
Exploit kits
Simply visiting some websites can get you infected, even if you don’t try to download anything. This is usually done by exploiting weaknesses in the software used to browse the web such as your browser, Java, or Flash. Content management and development tools like WordPress and Microsoft Silverlight, respectively, are also common sources of vulnerabilities. But there’s a lot of software and web trickery involved in delivering infections this way, so the bulk of this work is packaged into an exploit kit which can be rented out to criminals to help them spread their malware.
Renting an exploit kit can cost $1,000 a month, so this method of delivery isn’t for everyone. Only those cybercriminals who’re sufficiently motivated and funded.
“Because the cost of exploitation has risen so dramatically over the course of the last decade, we’ll continue to see a drop in the use of 0-days in the wild (as well as associated private exploit leaks). Without a doubt, state actors will continue to hoard these for use on the highest-value targets, but expect to see a stop to Shadowbrokers-esque occurrences. The mentioned leaks probably served as a powerful wake-up call internally with regards to who has access to these utilities (or, perhaps, where they’re left behind).” – Eric Klonowski, Webroot Principal Threat Research Analyst
Exploits for use in both malware and web threats are harder to come by these days and, accordingly, we are seeing a drop in the number of exploit kits and a rise in the cost of exploits in the wild. This threat isn’t going anywhere, but it is declining.
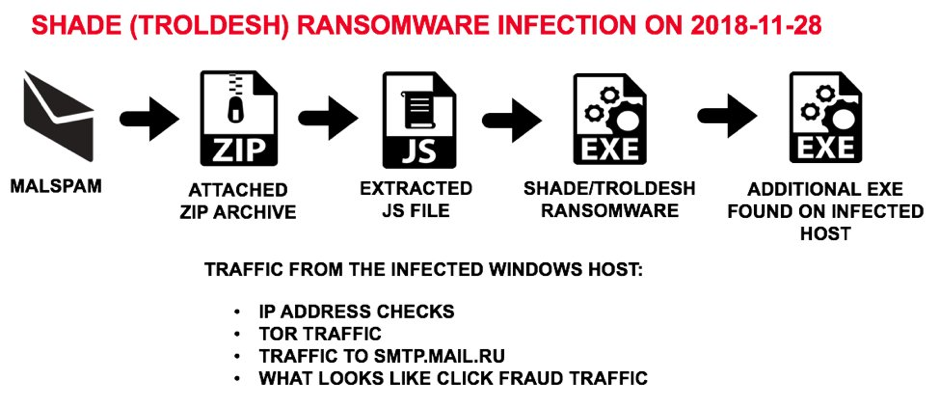
Email campaigns
Spam emails are a great way of spreading malware. They’re advantageous for criminals, as they can hit millions of victims at a time. Beating email filters, creating a convincing phishing message, crafting a dropper, and beating security in general is tough to do on a large scale, however. Running these big campaigns requires work and expertise so, much like an exploit kit, they are expensive to rent.
Targeted attacks
The likelihood of a target paying a ransom and how much that ransom is likely to be is subject to a number of factors, including:
- The country of the victim. The GDP of the victim’s home nation is correlated to a campaign’s success, as victims in richer countries are more likely to shell out for ransoms
- The importance of the data encrypted
- The costs associated with downtime
- The operating system in use. Windows 7 users are twice as likely to be hit by malware as those with Windows 10, according to Webroot data
- Whether the target is a business or a private citizen. Business customers are more likely to pay, and pay big
Since the probability of success varies based on the target’s circumstances, it’s important to note that there are ways of narrowing target selection using exploit kits or email campaigns, but they are more scattershot than other, more targeted attacks.
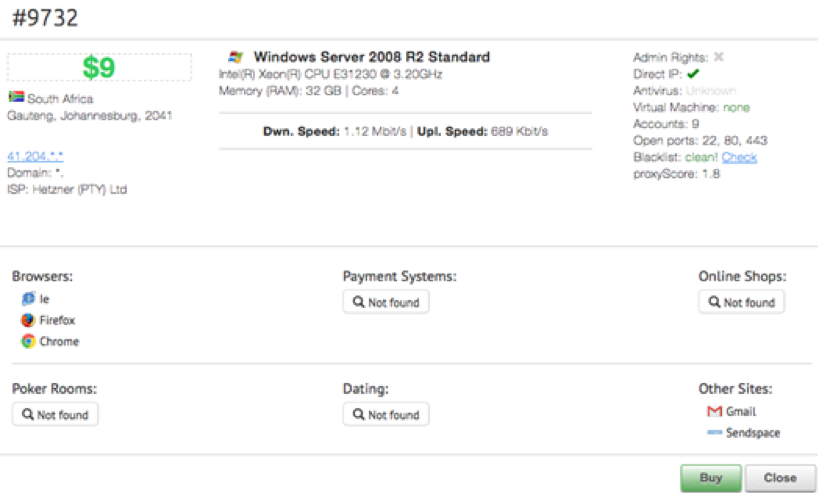
RDP
Remote Desktop Protocol, or RDP, is a popular Microsoft system used mainly by admins to connect remotely to servers and other endpoints. When enabled by poor setups and poor password policies, cybercriminals can easily hack them. RDP breaches are nothing new, but sadly the business world (and particularly the small business sector) has been ignoring the threat for years. Recently, government agencies in the U.S. and UK have issued warnings about this completely preventable attack. Less sophisticated cybercriminals can buy RDP access to already hacked machines on the dark web. Access to machines in major airports has been spotted on dark web marketplaces for just a few dollars.
Spear phishing
If you know your target, you can tailor an email specifically to fool them. This is known as spear phishing, and it’s an extremely effective technique that’s used in a lot of headline ransomware cases.
Modular malware
Modular malware attacks a system in different stages. After running on a machine, some reconnaissance is done before the malware reinitiates its communications with its base and additional payloads are downloaded.
Trickbot
The modular banking Trojan Trickbot has also been seen dropping ransomware like Bitpaymer onto machines. Recently it’s been used to test a company’s worth before allowing attackers to deploy remote access tools and Ryuk (ransomware) to encrypt the most valuable information they have. The actors behind this Trickbot/Ryuk campaign only pursue large, lucrative targets they know they can cripple.
Trickbot itself is often dropped by another piece of modular malware, Emotet.
What are the current trends?
As we’ve noted, ransomware use may be on the decline due to heightened defences and greater awareness of the threat, but the broader, more noteworthy trend is to pursue more carefully selected targets. RDP breaches have been the largest source of ransomware calls to our support teams in the last 2 years. They are totally devastating to those hit, so ransoms are often paid.
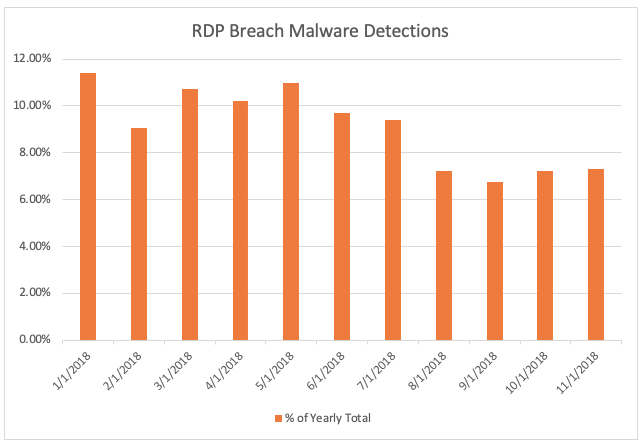
Modular malware involves researching a target before deciding if or how to execute and, as noted in our last blog on information stealers,they have been surging as a threat for the last six months.
Automation
When we talk about selecting targets, you might be inclined to assume that there is a human involved. But, wherever practical, the attack will be coded to free up manpower. Malware routinely will decide not to run if it is in a virtualised environment or if there are analysis tools installed on machines. Slick automation is used by Trickbot and Emotet to keep botnets running and to spread using stolen credentials. RDP breaches are easier than ever due to automated processes scouring the internet for targets to exploit. Expect more and more intelligent automation from ransomware and other malware in future.
What can I do?
- Secure your RDP
- Use proper password policy. This ties in with RDP ransomware threats and especially applies to admins.
- Update everything
- Back up everything. Is this backup physically connected to your environment (as in USB storage)? If so, it can easily be encrypted by malware and malicious actors. Make sure to air gap backups or back up to the cloud.
- If you feel you have been the victim of a breach, it’s possible there are decryption tools available. Despite the brilliant efforts of the researchers in decryption, this is only the case in some instances.
What can Webroot do?
- Detect and stop ransomware. Prevention is always best, and it’s what we’re best at.
- Block malicious URLs and web traffic.
- Rollback changes made by some ransomware.
- Offer support. Our support is excellent and easy to reach. As well as helping to tackle any possible ransomware attack, our team will investigate the root cause and help you secure your organisation against future attacks. Specialised security hardening tools that can be deployed from your console to your machines in a few clicks.
- For more technical details see our Ransomware Prevention Guide.