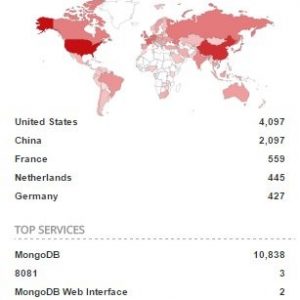
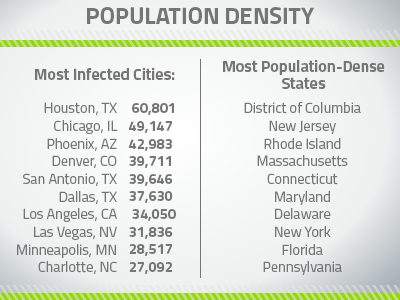
News of yet another breach at Target or Yahoo seems pretty commonplace these days. Sometimes, the frequency of big, newsworthy hacks can make us forget about more personal threats we face: the people close to us who have easy access to our financial info, social media accounts, online identity, and even our computer password.
Exponential growth
According to Pew Research Center, the use of social media has seen tenfold growth over the last decade, with nearly 68% of U.S. adults at the end of 2016 reporting they have a Facebook account (let alone any of the other social media outlets, such as Twitter, LinkedIn, Instagram, etc.) This growth represents a turning point in the way we consume news and share information with our friends and family members. But as the world becomes increasingly connected, it’s also becoming increasingly hackable.
In a survey conducted by the University of Phoenix, it was found that 70% of social media scams in 2016 were shared manually, meaning people voluntarily and unwittingly shared posts that linked to malicious or affiliate sites. Moreover, the study found that 9 out of 10 people limit their personal information shared on social media due to fear of being hacked.
9 out of 10 people limit their personal information shared on social media due to fear of being hacked.” – Survey results, University of Phoenix, 2016
Friends don’t let friends get hacked
To increase your personal security when browsing and sharing online, we recommend you take just a few simple steps.
Enable an automatic lock on your computer.
It sounds so simple, right? But seriously, adding a lock to your computer will keep friends and foes alike from accessing your everyday accounts that you may have forgotten to close or sign out of. We recommend rotating your Windows or Apple password and making it unique and very different from others that you may use on financial or data sensitive accounts.
Use a secure password manager.
They’re easy to find and easy to use. So what’s standing in your way? Using a password manager like Google Chrome’s built-in features or the Webroot SecureAnywhere password manager enables another layer of protection that you can sign out of when you’re done browsing or paying your bills. This will also help keep you from using the same password across all of your accounts for ease of access.
Don’t enter passwords on other people’s computers.
Be wary of logging into your social media accounts on your friends’ computers. You might forget to click “no” or “never” when prompted to save your login credentials, and you wouldn’t want an embarrassing Snap or Facebook post to haunt you.
If your password gets hacked
First, don’t panic, but don’t hesitate to take action either. Change all relevant passwords immediately, including any to other accounts where you may have reused the same credentials. Inform your friends and family members immediately of the situation, and to disregard messages or posts that were sent from your account during the period of exposure. Finally, don’t forget to notify the support team for the associated social network so that they can investigate and help prevent others from becoming victims of the same types of attack.