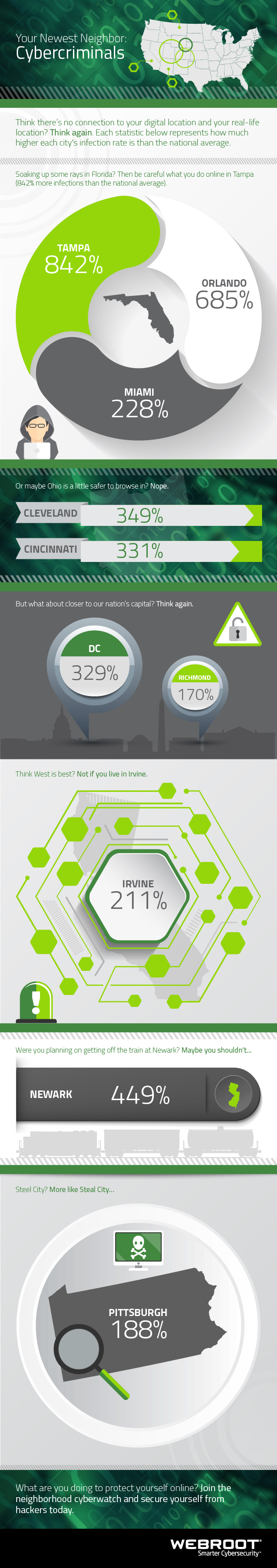
It was only a matter of time before phone hacking rose to the top of the media-driven hysteria list
Thanks to the rapid growth of mobile device adoption and the subsequent rapid growth in mobile threats, phone hacking prevention is a hot topic. A headache reserved for celebrities in the past, smartphone-infiltration concerns have crossed the VIP vs. everyone else blood-brain barrier and now potentially impacts anyone who owns a smartphone.
But is this really a serious problem for us regular folks? Are our voicemail messages so interesting that someone would invade our privacy to listen in? Before we go barking up the narcissism tree, it’s best to examine what phone hacking is and whether you really need to worry about it.
With everything I’ve got going on, do I need to worry about my phone’s security?
This security threat can be broken down into two types: hacking into a live conversation or into someone’s voicemail, and hacking into data stored on one’s smartphone. Just as the majority of abductions are carried out by a member of the abductee’s family—unless you go by code name POTUS or are Hugh Grant—the person most likely to hack into your live conversation or voicemail will be someone that you know who has an ax to grind.
And in today’s mobile world, mobile security is a growing issue. As people increasingly store sensitive data on their mobile devices, the opportunity to exploit privacy weaknesses becomes more tempting to unscrupulous ‘frenemies’, exes or the occasional stranger.
It doesn’t help that there is a cottage industry of software ostensibly developed for legal uses but is easily abused (password crackers aptly named ‘John the Ripper’ and ‘Cain and Abel’ are two examples). Opportunistic hackers can wreak havoc with data deletion or install malicious software that gathers bank account logins and confidential business emails.
So what’s a smartphone owner to do?
If you want to be proactive, there are several measures you can take to protect yourself against this threat, most of which involve common sense. For example:
- Don’t leave your phone unattended in a public place.
- Be sure to change the default password that comes with a new phone to something more complex (resist the usual “1234,” “0000” and 2580)
- Avoid using unprotected Bluetooth networks and turn off your Bluetooth when you aren’t using it.
- Use a protected app to store pin numbers and credit cards, or better yet, don’t store them on the phone at all.
Throwing the baby out with the bathwater
If you’re still worried about your smartphone’s security, there are further steps you can take to protect yourself. However, taking things too far will defeat the purpose of having a smartphone at all.
- Avoid accessing important locations such as bank accounts via public Wi-Fi that may not be secure.
- Turn off your auto complete feature so critical personal data isn’t stored on the phone and must be re-entered every time you need it.
- Regularly delete your browsing history, cookies and cache so your virtual footprint is not available for prying eyes.
- If you have an iPhone, you can enable ‘Find My iPhone’ in your settings, and it will locate your phone if you misplace it before the hackers can lay their hands on it.
- Use a security app that increases protection. For Android owners, Webroot offers the all-in-one SecureAnywhere Mobile app that provides antivirus protection and allows you to remotely locate, lock and wipe your phone in the event you lose track of it.
Remember—if the thought of your smartphone getting breached has you tossing and turning at night, you can just turn the phone off, remove the battery and hide it under your pillow for some sweet lithium-ion induced dreams.