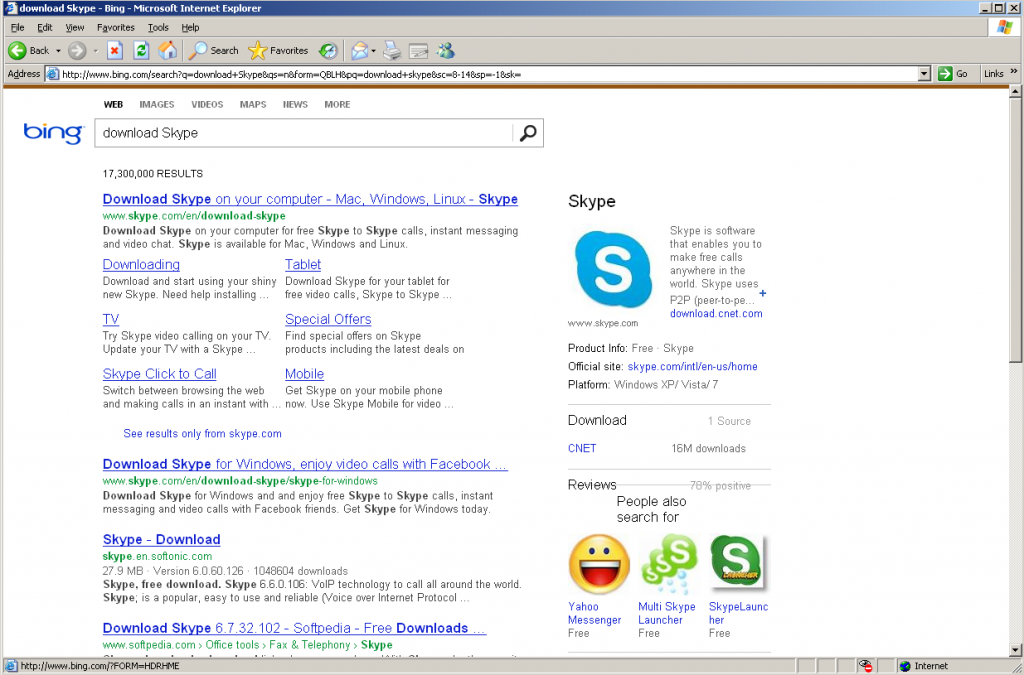
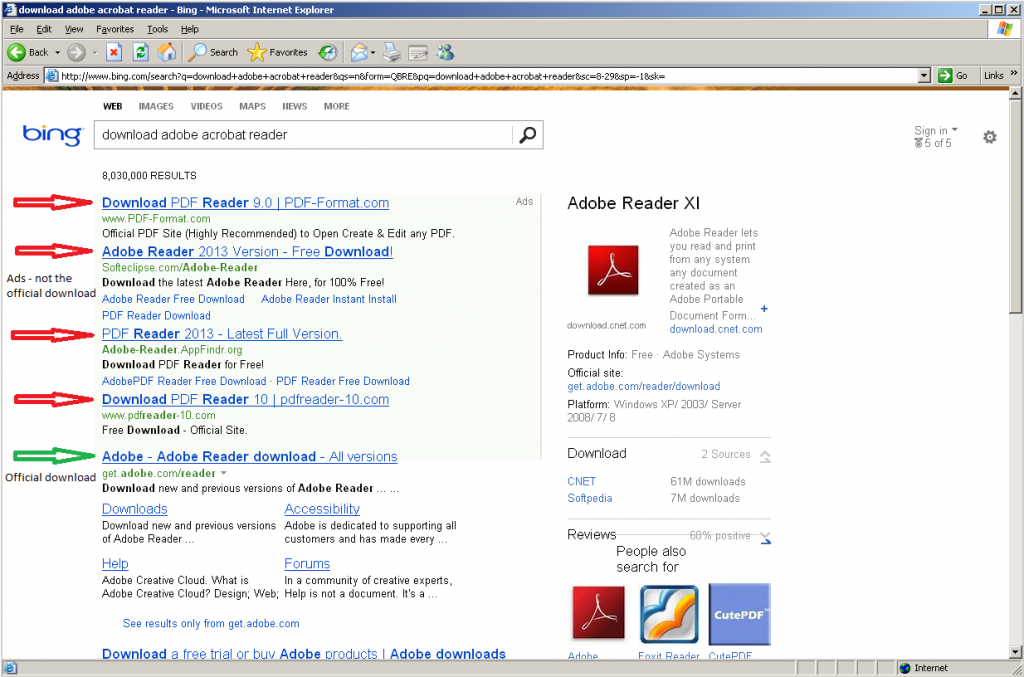
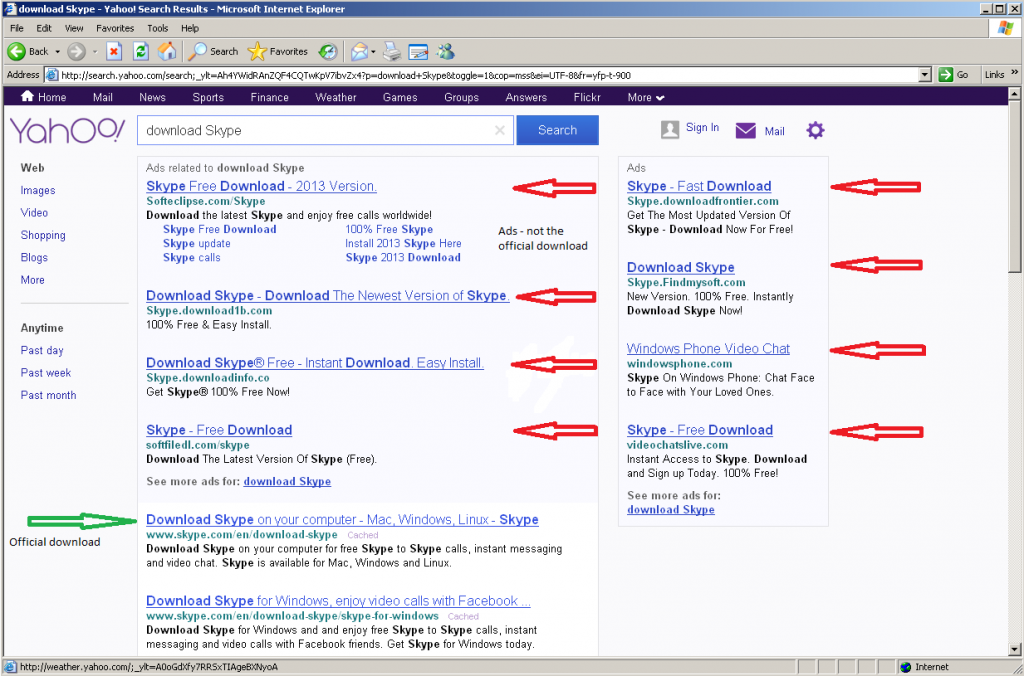
It’s National Cybersecurity Awareness Month in the US and Stay Smart Online Week in Australia, so you might say that security is on the minds of more people around this time. So as we start taking the lessons in and changing some of our habits, there is another area that could use more attention; our personal data.
With a large variety of social networks available around the world, the opportunities to share are endless, but with that, so is the opportunity for information gathering by malicious parties as well as chances that private information could be revealed in a breach. One way to avoid this from occurring is by being careful with your information and be aware with what information you give out. An example of this can be seen from the recent Ashley Madison scandal where people not only posted their real names and personal details, but also linked their work email in some cases, embarrassing not just themselves but the organisations they work for. Also the less information you give out (like emails and phone numbers) the less likely you’re hit with spam.
And then there comes the personal data that you carry with you, be it from home to the office or on your next big vacation. This data could be stolen and compromised for malicious intent such as stolen identities, financial fraud, or even blackmail.
It’s always handy to encrypt your drive, whether you travel with your device or not. It is vital to encrypt a drive if it has sensitive data on it relating to you or the organisation you work for. There has been quite a few cases in this country where unencrypted devices from organisations go missing with customer data on it, then the Data Protection Commissioner will get involved and likely impose penalties on the organisation. An example of this: http://www.independent.ie/irish-news/three-eircom-laptops-containing-customers-data-including-bank-details-stolen-26820140.html. As well as encrypting your drive, don’t keep sensitive data (passwords, security questions, info you don’t want other people to see, etc.) in unencrypted text files lying around your system. If anyone gets access to the computer these files will be compromised.
In this day and age it can never be too much effort to keep personal data personal, and with a few steps, you can help minimize the risk to that information. While some might take time to get used to, a healthy habit of being aware will only help in the long run.