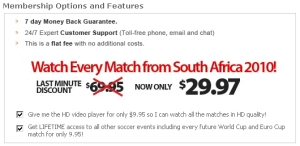
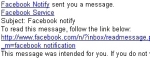
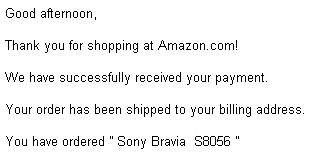
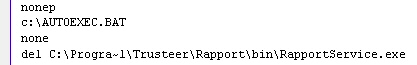Money drives the motivation for most cybercrime, but it’s been a while since we’ve seen a criminal try to earn their money by driving traffic to a Web site, rather than just taking your cyberwallet.
Money drives the motivation for most cybercrime, but it’s been a while since we’ve seen a criminal try to earn their money by driving traffic to a Web site, rather than just taking your cyberwallet.
Some anonymous Trojan creator has taken a bold new approach towards a malware work ethic with his or her new browser hijacker Trojan: It creates an entirely new file suffix, and handling instructions within Windows, so that the new (.nak) file suffix integrates seamlessly into the operating system. The Trojan then replaces just the file suffix on any Shortcut that points to either the IE or Firefox browser, on the desktop or in the Start menu, with the new suffix. You may not even have realized that Shortcut files have file extensions. They’re normally hidden.
The net effect is that, on an infected computer, if you launch IE or Firefox by double-clicking one of the shortcuts on the desktop or in the Start menu, it opens a page to a Chinese portal — regardless of the Home Page settings in either browser.
It sounds more impressive than it turned out to be, even if it was kind of surprising at first, and despite the fact that the creators walked three sides of a square to get there. The only good news is that the changes the Trojan makes to the system are easily reversible. And you can still open IE and Firefox normally by launching them from the command line, navigating to the application itself in Explorer, or by creating new shortcuts to the applications.