 Bootlegged copies of Civilization 5, the highly anticipated, just-released real time strategy game, are already popping up in file sharing services. And, as we’ve come to expect, some of the pirated copies of the game come with that little something special — malicious components.
Bootlegged copies of Civilization 5, the highly anticipated, just-released real time strategy game, are already popping up in file sharing services. And, as we’ve come to expect, some of the pirated copies of the game come with that little something special — malicious components.
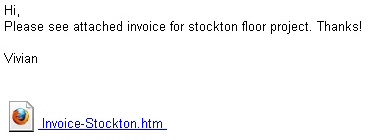
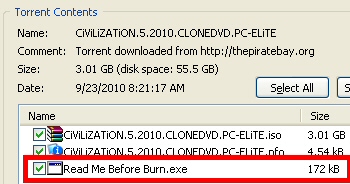
One of our Threat Research Analysts, who also happens to be an avid gamer, started looking for pirated copies of the game Friday morning and, within five minutes of looking, found Trojans in some of the torrents in circulation. I’ve chosen to focus on one of these files, not only because it was the first we saw, but also the most interesting. The Trojan, bundled in a torrent with the ISO image of the Civ 5 installation disc, is called ‘read me before burn.exe‘ (MD5: 2f7ff2ecef4b5cf1c9679f79d9b72518).
On a typical Windows system, the file appears to be a text document, but only because it uses a file icon of a text document. With the file extension visible, however, it’s clearly an .exe with a mission.