Researchers spot Citadel, a ZeuS crimeware variant
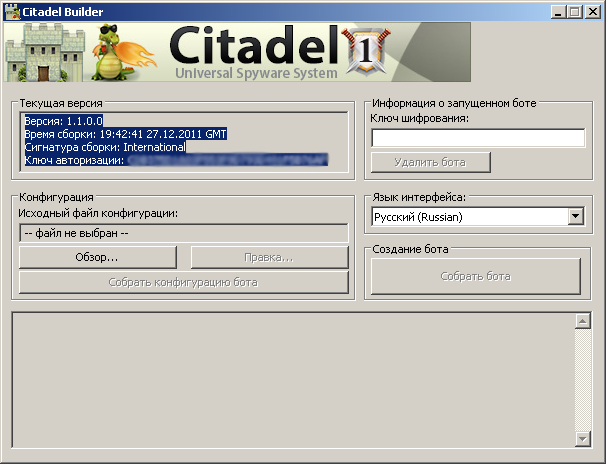
Security researchers from “Tracking Cyber Crime” have spotted a new ZeuS crimeware variant, that’s based on the leaked ZeuS source code from last year.
Dubbed Citadel, the crimeware is positioned as a universal spyware system, whose modular nature allows cybercriminals to offer flexibly priced value-added services such as managed malware crypting, and managed web injects as a service.
Some of Citadel’s core features include:
A peek inside the Smoke Malware Loader
The competitive arms race between security vendors and malicious cybercriminals constantly produces new defensive mechanisms, next to new attack platforms and malicious tools aiming to efficiently exploit and infect as many people as possible.
Continuing the “A peek inside…” series, in this post I will profile yet another malware loader. This time it’s the Smoke Malware Loader.
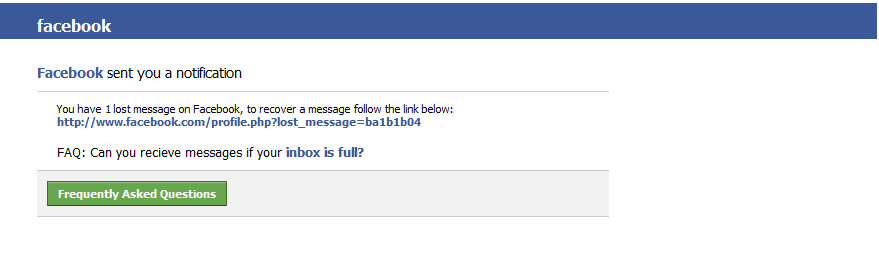
Spamvertised ‘You have 1 lost message on Facebook’ campaign leads to pharmaceutical scams
A currently spamvertised spam campaign is redirecting users to pharmaceutical scams, in an attempt to trick them into purchasing counterfeit pharmaceutical items.
More details:
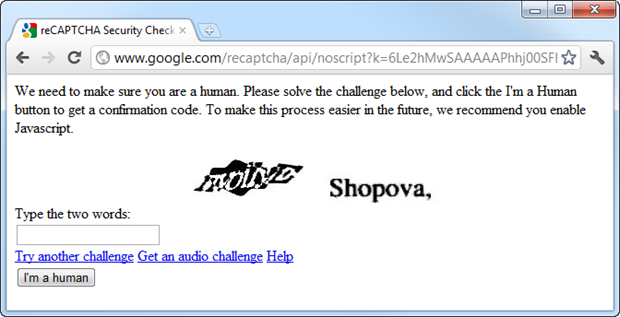
Research: Google’s reCAPTCHA under fire
Who needs automated bots solving CAPTCHAs, when you have teams of low-waged humans recognizing them for pennies?
In an underground cybercrime ecosystem dominated by managed services and countless outsourcing opportunities, it’s fairly logical to assume that Google’s reCAPTCHA is under constant fire.
Just how easy is it to recognize reCAPTCHA images for malicious account registration and service abuse purposes? Let’s find out.
Cybercriminals generate malicious Java applets using DIY tools
Who said there’s such a thing as a trusted Java applet?
In situations where malicious attackers cannot directly exploit client-side vulnerabilities on the targeted host, they will turn to social engineering tricks, like legitimate-looking Java Applets, which will on the other hand silently download the malicious payload of the attacker, once the user confirms he trusts the Applet.
Let’s profile a DIY (do-it-yourself) malicious Java Applet generator currently available for download at selected cybercrime-friendly online communities:
Cisco releases ‘Cisco Global Threat Report’ for 4Q11
Cisco Systems, recently announced the release of ‘Cisco Global Threat Report’ for 4Q11, containing threat intelligence based on Cisco’s observation of the malicious threat landscape.
Key summary points:
A peek inside the uBot malware bot
Participants in the dynamic cybercrime underground ecosystem are constantly working on new cybercrime-friendly releases in the form of malware bots, Remote Access Tools (RATs) and malware loaders.
Continuing the “A peek inside…” series, in this post I will profile yet another DIY (do-it-yourself) malware bot, available at the disposal of cybercriminals at selected cybercrime-friendly online communities.
Researchers intercept a client-side exploits serving malware campaign
Security researchers from Webroot have intercepted a currently active, client-side exploits-serving malicious campaign that has already managed to infect 18,544 computers across the globe, through the BlackHole web malware exploitation kit.
More details:
How phishers launch phishing attacks
Just like in every other industry, participants in the cybercrime ecosystem are no strangers to the concept of standardization. Standardization results in efficiencies, which on the other hand results in economies of scale. In this case, malicious economies of scale.
Just how easy is it to launch a phishing attack nowadays? What tools, and tactics are at the disposal of phishers aiming to efficiently socially engineer hundreds of thousands of users?
In this post, I will profile the Ninja V0.4 Social Engineering Phishing Framework – an advanced platform for executing phishing attacks in a DIY (do-it-yourself) fashion.
A peek inside the Umbra malware loader
The thriving cybercrime underground marketplace has a lot to offer. From DIY botnet builders, DIY DDoS platforms, to platforms for executing clickjacking and likejacking campaigns, next to drive-by malware attacks, the ecosystem is always a step ahead of the industry established to fight back.
Continuing the “A peek inside…” series, in this post I will profile yet another freely available DIY Botnet building tool – the Umbra Malware Loader.
How malware authors evade antivirus detection
Aiming to ensure that their malware doesn’t end up in the hands of vendors and researchers, cybercriminals are actively experimenting with different quality assurance processes whose objective is to increase the probability of their campaigns successfully propagating in the wild without detection.
Some of these techniques include multiple offline antivirus scanning interfaces offering the cybercriminal a guarantee that their malicious program would remain undetected, before they launch their malicious campaign in the wild.
In the wild since 2006, Kim’s Multiple Antivirus Scanner is still actively used among cybercriminals wanting to ensure that their malicious software is pre-scanned against the signature-based scanning techniques offered by multile antivirus vendors.
Let’s review Kim’s Multiple Antivirus Scanner, and discuss when it’s an important tool in the arsenal of the malicious cybercriminal spreading malware for profit.
Inside AnonJDB – a Java based malware distribution platforms for drive-by downloads
by Dancho Danchev
With the even decreasing prices of underground tools and services, thanks to the commoditization of these very same market items, the price for renting a botnet, or purchasing access to already infected hosts, is constantly decreasing.
Although the majority of cybercriminals are actively exploiting end and corporate users while using client-side vulnerabilities in outdated third-party applications and browser plugins, there’s a separate branch of cybercriminals who specialize in delivering their payload using nothing else but good old fashioned social engineering attacks.
Following my previous post Inside a clickjacking/likejacking scam distribution platform for Facebook, in this post I will profile AnonJDB – a Java based malware distribution platform for drive-by downloads.