
by Connor Madsen | Feb 9, 2018 | Threat Lab
The Cyber News Rundown brings you the latest happenings in cybersecurity news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst and a guy with a passion for all things security. Any questions? Just ask.
New Variant of Scarab Ransomware
With a few interesting changes to the original Scarab ransomware, Scarabey is quickly targeting Russian-speaking users with brute force attacks on unsecured RDP connections, rather than with the spam email campaigns used by its predecessor. Additionally,
Botnets Used to Spread Cryptocurrency Miners
Following the Shadow Brokers release of NSA exploits last summer, the use of EternalBlue continues with the latest trend of using the exploit to compromise machines and turn them into cryptocurrency miners. By expanding the botnet to cover over 500,000 unique machines, the attackers have successfully brought in more than $3 million since May of 2017. The use of such a large-scale botnet can effectively mine for the more resource-intensive currencies with ease and even disrupt businesses from their normal workflow for days at a time.
Bitcoin Ads Circumvent Facebook Ban
In the past week, Facebook officially implemented a ban on all cryptocurrency-related advertisements on their site. However, the ads have continued to appear for many users with characters in the phrase ‘bitcoin’ simply misspelled. The ban was initially set to block misleading financial services and products that unknowing users might click on due to the apparent legitimacy of the ads.
Mac Software Sites Distributing Crypto Miners
As crypto miners continue to gain popularity among cyber criminals, it was inevitable that they would begin focusing on Macs. MacUpdate, a well-known software download site, was recently found to be bundling miners with commonly used applications. Luckily, some of these bundles are poorly written and often fail to launch the decoy app, which is intended to draw users’ attention away from the malicious activity. To make matters worse, several other download sites were also affected and waited far too long to remove the malicious download links from their servers.
Tech Scammers Exploit Chrome Flaw
Tech scammers have long been the bane of legitimate software companies and their support teams. The latest trick, however, can easily bring an unsuspecting user to a full panic attack by simply rendering a Chrome browser completely unusable. First it displays an error message and then silently forces the browser to save a random file to disk at such a pace that the machine’s CPU maxes out and leaves the computer in a ‘locked’ state in the hopes that the victim will actually contact the phony support number being displayed.

by Sophia Carmien | Feb 6, 2018 | Webroot Blog
Who doesn’t like a good mobile game? Especially a free one! They allow you to blow off steam while fine-tuning your skills, competing with others or maybe even winning bragging rights among friends.
Free games can be fun to play, yet there are some common-sense guidelines to make sure these apps don’t surprise you with unexpected costs or other problems.
Like anything digital, opportunities for malware and other cyber threats do exist. Here are some things to beware of as you protect your privacy, well-being and wallet.
In-app purchases and unauthorized transactions
Free game providers make revenue by selling upgrades to the games’ cosmetic value or the means to advance to another level of play. For example, on a popular kids’ game, players can buy special coins that help boost their overall gaming experience.
But according to a 2017 Tech Crunch article, Amazon recently agreed to refund millions of these types of in-app purchases because they were technically unauthorized – made by children on mobile devices linked to its site. Much to the parents’ regret, these transactions did not require passwords.
Apple and Google have settled similar agreements with the Federal Trade Commission.
So, keep an eye on transactions, banking records and your kids as they play. Most mobile devices even have the option of disabling or PIN-protecting in-app purchases so the little ones aren’t able to make purchasing decisions on their own.
Little extras can add up to a big cost for mom or dad. Or, in a more malicious case, someone with bad intentions could be purposely adding unwanted charges to your credit card.
Malware and privacy threats
Free mobile apps typically feature advertising and, of course, users can pay a premium to turn that off. That’s another transaction-based upgrade that turns free into not-so-free.
However, beyond the clutter and interruptions caused by real ads, malware can deliver a darker spin on free-to-play games through fake ads.
The Economic Times reports that Google has removed nearly 60 games, many of which were aimed at children, from its Play Store. The games were found to be infected with malware and bogus ads.
The malware displayed images that looked like real advertisements, causing concern and prompting users to download fake security software. The users were then encouraged to click on other links that would require payment.
Along with encouraging users to download scareware and pay for premium services, the malware also stole personal information. Those types of sensitive, personal records could include passwords, device ID’s and credit card information.
And that can lead to identity theft and even larger financial threats.
So remember, only use trusted providers, read the reviews before installing the game and there’s never any need to allow extensive access to your device or personal information. You’re just playing free mobile game apps after all.
Free-to-Play mobile gaming security tips
Transaction-based issues and malicious malware are two of the most common concerns associated with free-to-play mobile games. But by no means do they make up a complete list of potential risk factors.
This doesn’t mean you shouldn’t play free games online. But use caution. Scrutinize games labeled as free and realize that paying a reasonable price for software versus getting it for no charge is sometimes worth it.
Here are some more detailed security tips from US-CERT, the United States Government Computer Readiness Team:
- Use antivirus software
- Be cautious about opening web files
- Verify download authenticity
- Configure web browsers securely
- Back up personal data
- Use strong passwords
- Update operating and application software

by Connor Madsen | Feb 2, 2018 | Threat Lab
The Cyber News Rundown brings you the latest happenings in cybersecurity news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst and a guy with a passion for all things security. Any questions? Just ask.
Multiple Dutch Banks Fall Victim to Week-long Cyberattack String
Over the last week, several of the largest banks in the Netherlands have been targeted by a string of DDoS attacks that have shut down much of the country’s banking services, affecting millions of customers. Officials have confirmed that no personal data has been compromised, and it appears they have been able to repair their website issues, allowing customers to slowly resume normal banking activity.
YouTube Removes ‘Cryptojacking’ Ads with Crypto Miners
Researchers recently discovered that YouTube has been displaying advertisements that come with a cryptocurrency miner, which is being used to generate revenue for the attackers. In addition to draining the victim’s CPU, the scripts used for the mining process were also generating ads for fake antivirus programs, in hopes of further cashing in on victims. Fortunately, Google was quick to respond and had the malicious ads taken down within a matter of hours.
Tracking Service Displays Military Bases Around the World
With the modern prominence of social media, less and less of our daily activities remains truly private. But how far will it go? When Strava, a fitness activity network that logs the activity of billions of users, posted a global “heat map” showing that activity, it also revealed the locations of dozens of military bases around the world. By viewing the map, it is easy to discover patrol routes, commonly visited locations, and the daily patterns for almost anyone using the app, from anywhere in the world.
Cisco VPNs Contain Severe Flaw
At least ten Cisco devices that run their Adaptive Security Appliance software were found with a flaw so severe that it was given the highest possible vulnerability rating. The vulnerability, which has since been patched, allowed for extremely simple remote exploitation and required no user authorization. Luckily, the flaw is only accessible if the user has enabled the WebVPN functionality on the device, and Cisco provided documentation on how to verify whether it is enabled, and if a device has been affected.
ATM Jackpotting Finally Arrives in the US
While it has spread through Europe and Asia for the past several years, the act of jackpotting an ATM has only recently made its way to the US. Jackpotting an ATM is as simple as gaining access to the device’s hard drive and either swapping it for a compromised drive, or infecting it with malware to give the attacker full control. By disguising themselves as ATM technicians, attackers gain easier access to the ATM and can even return later to quickly dispense the entirety of the ATMs cash reserves.

by Connor Madsen | Jan 26, 2018 | Threat Lab
The Cyber News Rundown brings you the latest happenings in cybersecurity news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst and a guy with a passion for all things security. Any questions? Just ask.
New Trojan Alters Bitcoin Addresses
A newly discovered trojan variant targets Bitcoin users and, more specifically, any Bitcoin addresses that may be copied into the device’s clipboard. The trojan “Evrial” can alter the address in the clipboard so funds are transferred elsewhere when a user performs a Bitcoin transaction.[/inlinetweet] Additionally, Evrial is capable of stealing cookies and any credentials that are being stored within web browsersto further compromise any purchases made on the device.
Paradise Ransomware is Anything But
In a recent return, new attacks have been linked to Paradise ransomware, which had been relatively quiet since its initial burst of attacks last year. Not much has changed for the variant since its previous reveal; it still requires a user to open a phony email attachment and unzip the packed infection. Unfortunately, there is no easy way to decrypt any of the affected files, and the user would need to either restore everything from a clean backup or pay the ransom, which varies based on the victim’s reply time.
Top UK Law Firms Face Massive Breach
Researchers have recently discovered several data dumps that contain over a million email credentials from several of the largest law firms in the UK. Based on the information found in the dumps, roughly 2,000 credentials belonged to each of the companies; the largest company is responsible for over 30,000 of them. Even worse, many of the dumps were released just in the last six months, though most come from third-party breaches.

Major Twitter Accounts Hacked
Several high-profile Twitter accounts were compromised over the last week and used to spread Turkish and Palestinian propaganda while attempting to phish the credentials of related accounts. Along with the credentials, it appears that private messages and other sensitive information were breached as well, leaving the compromised accounts even more vulnerable.
Business Security Moving Forward
Following a Ponemon Institute study from late last year, many were shocked at the results from the companies who responded. Over half of the 1,000 IT professionals surveyed claimed to have suffered a ransomware attack within the last year, and the majority of those reported the cause to be phishing and social engineering tactics. Even more worrisome, the average data breach involved the compromise of an average of 9,000 unique records, costing victims several million dollars to return to normal.

by Austin Castle | Jan 25, 2018 | Threat Lab
Earlier this month, CES attendees got a taste of the future with dazzling displays of toy robots, smart assistants, and various AI/VR/8K gadgetry. But amid all the remarkable tech innovations on the horizon, one thing is left off the menu: user privacy. As we anticipate the rocky road ahead, there are three major pitfalls that have privacy experts concerned.
Bio hazard
Biometric authentication—using traits like fingerprints, iris, and voice to unlock devices—will prove to be a significant threat to user privacy in 2018 and beyond. From a user’s perspective, this technology streamlines the authentication process. Convenience, after all, is the primary commodity exchanged for privacy.
Mainstream consumer adoption of biometric tech has grown leaps and bounds recently, with features such as fingerprint readers becoming a mainstay on modern smartphones. Last fall, Apple revealed its Face ID technology, causing some alarm among privacy experts. You can’t change your fingerprints, after all. Biometric access is essentially akin to using the same password across multiple accounts.
“Imagine a scenario where an attacker gains access to a database containing biometric data,” said Webroot Sr. Advanced Threat Research Analyst Eric Klonowski. “That attacker can then potentially replay the attack against a variety of other authenticators.”
That’s not to say that biometrics are dead on arrival. Privacy enthusiasts can find solace in using biometrics in situations such as a two-factor authentication supplement. And forward-thinking efforts within the tech industry, such as partnerships forged by the FIDO Alliance, can help cement authentication standards that truly protect users. For the foreseeable future, however, this new tech has the potential to introduce privacy risks, particularly when it comes to safely storing biometric data.
Big data, big breaches
2017 was kind of a big year for data breaches. Equifax, of course, reined king by exposing the personal information (including Social Security Numbers) of some 140 million people in a spectacular display of shear incompetence. The Equifax breach was so massive that it overshadowed other big-data breaches from the likes of Whole Foods, Uber, and the Republican National Committee.
It seems no one—including the government agencies we trust to guard against the most dangerous online threats—was spared the wrath of serious data leaks. Unfortunately, there is no easy remedy in sight, and the ongoing global invasion of user privacy is forcing new regulatory oversight, such as the upcoming GDPR to protect EU citizens. The accelerated growth of technology, while connecting our world in ways never thought possible, has also completely upended traditional notions surrounding privacy.
The months ahead beg the question:

Talent vacuum
The third big issue that will continue to impact privacy across the board is the current lack of young talent in the cybersecurity industry. This shortfall is a real and present danger. According to a report by Frost & Sullivan, the information security workforce will face a worldwide talent shortage of 1.5 million by 2020.
Some of this shortfall is partly to blame on HR teams that fail to fully understand what they need to look for when assessing job candidates. The reality is that the field as a whole is still relatively new and is constantly evolving. Cybersecurity leaders looking to build out diverse teams are wise to search beyond the traditional background in computer science. Webroot Vice President and CISO Gary Hayslip explained that a computer science degree is not something on his radar when recruiting top talent for his teams.
“In cyber today, it’s about having the drive to continually educate yourself on the field, technologies, threats and innovations,” said Hayslip. “It’s about being able to work in teams, manage the resources given to you, and think proactively to protect your organization and reduce the risk exposure to business operations.
Beyond shoring up recruiting practices for information security roles, organizations of all types should consider other tactics, such as providing continual education opportunities, advocating in local and online communities, and inevitably replacing some of that human talent with automation.

by Austin Castle | Jan 22, 2018 | Webroot Blog
From Facebook to LinkedIn, social media is flat-out rife with phishing attacks. You’ve probably encountered one before… Do fake Oakley sunglasses sales ring a bell?
Phishing attacks attempt to steal your most private information, posing major risks to your online safety. It’s more pressing than ever to have a trained eye to spot and avoid even the most cunning phishing attacks on social media.
Troubled waters
Spammers on social media are masters of their craft and their tactics are demonstrably more effective than their email-based counterparts. According to a report by ZeroFOX, This compares to a roughly 30 percent success rate of spear phishing emails, based on findings by Verizon.
Facebook has warned of cybercriminals targeting personal accounts in order to steal information that can be used to launch more effective spear phishing attacks. The social network is taking steps to protect users’ accounts from hostile data collection, including more customizable security and privacy features such as two-factor authentication. Facebook has also been more active in encouraging users to adopt these enhanced security features, as seen in the in-app message below.
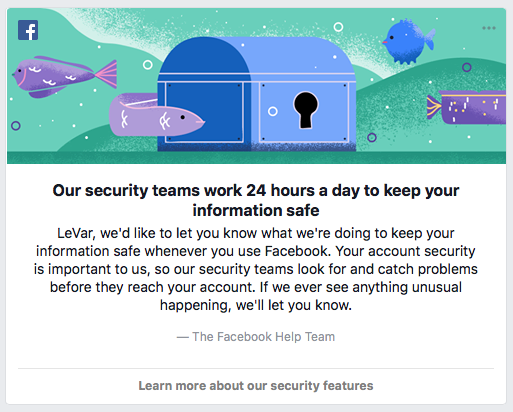
Types of social phishing attacks
Fake customer support accounts
The rise of social media has changed the way customers seek support from brands, with many people turning to Twitter or Facebook over traditional customer support channels. Scammers are taking advantage of this by impersonating the support accounts of major brands such as Amazon, PayPal, and Samsung. This tactic, dubbed ‘angler phishing’ for its deepened deception, is rather prevalent. A 2016 study by Proofpoint found that 19% of social media accounts appearing to represent top brands were fake.
To avoid angler phishing, watch out for slight misspellings or variations in account handles. For example, the Twitter handle @Amazon_Help might be used to impersonate the real support account @AmazonHelp. Also, the blue checkmark badges next to account names on Twitter, Facebook, and Instagram let you know those accounts are verified as being authentic.
Spambot comments
Trending content such as Facebook Live streams are often plagued with spammy comments from accounts that are typically part of an intricate botnet. These spam comments contain URLs that link to phishing sites that try to trick you into entering your personal information, such as a username and password to an online account.
It is best to avoid clicking any links on social media from accounts you are unfamiliar with or otherwise can’t trust. You can also take advantage of security software features such as real-time anti-phishing to automatically block fake sites if you accidently visit them.
Dangerous DMs
Yes, phishing happens within Direct Messages, too. This is often seen from the accounts of friends or family that might be compromised. Hacked social media accounts can be used to send phishing links through direct messages, gaming trust and familiarity to fool you. These phishing attacks trick you into visiting malicious websites or downloading file attachments.
For example, a friend’s Twitter account that has been compromised might send you a direct message with a fake link to connect with them on LinkedIn. This link could direct to a phishing site like the one below in order to trick you into giving up your LinkedIn login.
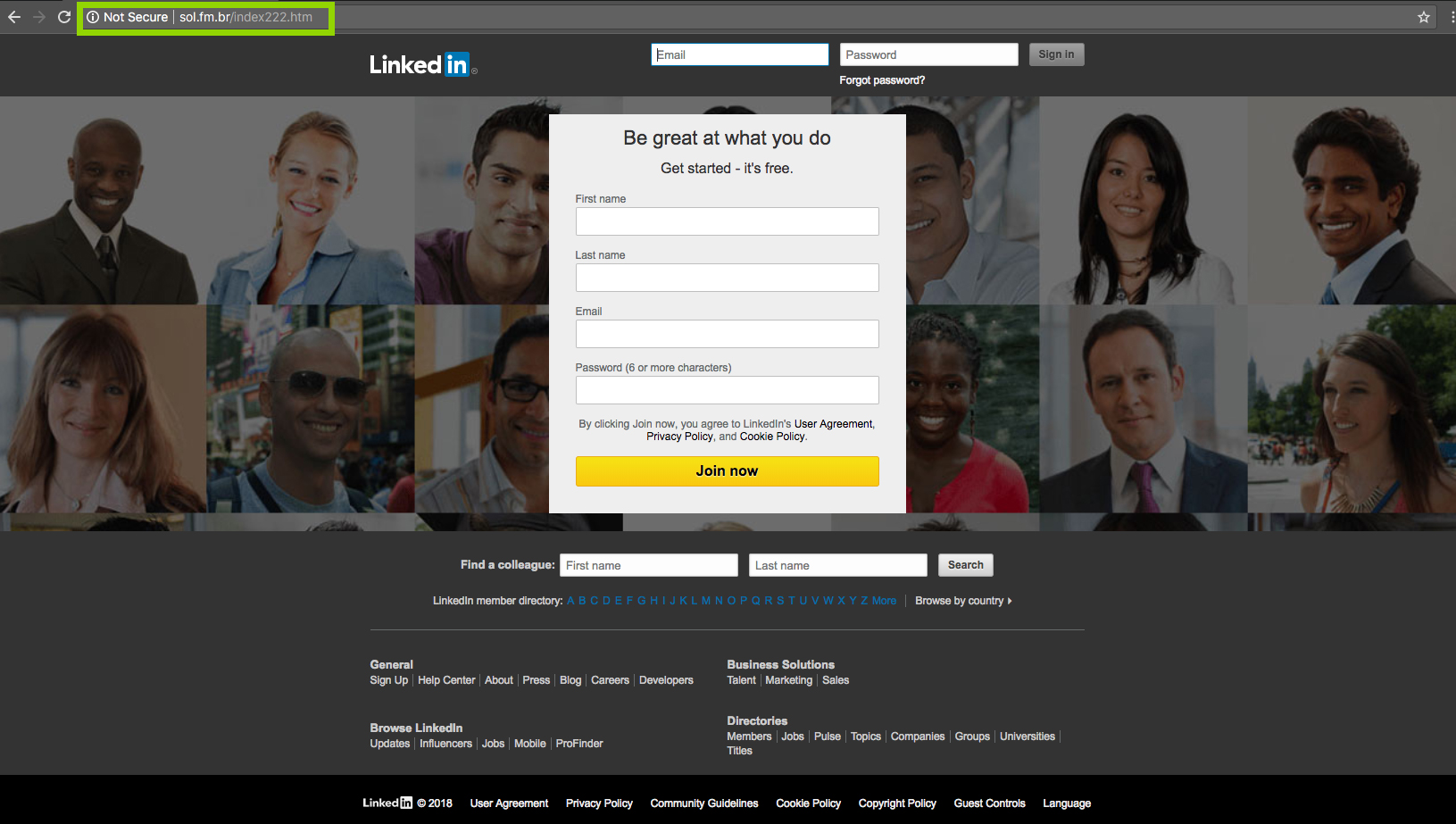
While this site may appear to look like the real LinkedIn sign-on page, the site URL in the browser address bar reveals it is indeed a fake phishing site.
Phony promotions & contests
Fraudsters are also known to impersonate brands on social media in order to advertise nonexistent promotions. Oftentimes, these phishing attacks will coerce victims into giving up their private information in order to redeem some type of discount or enter a contest. Know the common signs of these scams such as low follower counts, poor grammar and spelling, or a form asking you to give up personal information or make a purchase.
The best way to make sure you are interacting with a brand’s official page on social media is to navigate to their social pages directly from the company’s website. This way you can verify the account is legitimate and you can follow the page from there.

by Connor Madsen | Jan 19, 2018 | Threat Lab
The Cyber News Rundown brings you the latest happenings in cybersecurity news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst, and a guy with a passion for all things security. Any questions? Just ask.
Hospital Pays Ransom to Restore Systems, Despite Having Backups
In the first cyberattack of 2018 to hit a healthcare organization, an Indiana hospital’s entire network was taken offline. Despite having full backups on-hand, the hospital paid the $55,000 Bitcoin ransom right away. Officials stated they paid the ransom to get the systems back to normal as quickly as possible, since restoring everything from their backups could have taken weeks. Fortunately for patients, no data was stolen, and the staff could continue assisting new arrivals the old-fashioned way (that’s right: pen and paper) until system functionality was restored.
Audio Attacks Used for Damaging Hard Drives
A recent collaborative study performed by two universities proved that, within a reasonable proximity, an attacker could use acoustic signals to target a hard disk drive, leading to data corruption on the device. While many people could explain why this type of attack is possible, the study determined that the attacks required not only a specific frequency based on the hard drive in question, but also a precise distance from the drive and angle of sound projection to execute a successful attack.
New Android Platform Takes Spying to New Heights
A new Android spying platform has been discovered that puts all its predecessors to shame. By implementing several new features, such as location-based audio recording, compromising WhatsApp messages, and even allowing attackers to connect the device to malicious WiFi networks, this software platform gives attackers an all-new range of methods to target victims. The platform is based around five known exploits in the Android OS, and it uses them to gain administrative access to the device.
Latest Netflix Phish Asks for User Selfie
Within the last week, a new email phishing campaign has been spotted targeting Netflix users. The email informs users that a “hold” has been placed on their account pending further information. It requests users upload a photo of themselves with an ID card and prompts them to update their billing information, before redirecting them to the real Netflix login page.
RubyMiner Found on Older Linux and Windows Servers
A new cryptocurrency miner variant has been targeting outdated system servers that run both Linux and Windows. The variant, known as RubyMiner, identifies the unsecured servers using a web server tool, then gains access via a variety of exploits to install a modified Monero miner. RubyMiner deviates from similar miners in that it focuses on machines that have likely been forgotten about, and so remain on without being regularly patched.

by Tyler Moffitt | Jan 18, 2018 | Threat Lab
“How to buy Bitcoin” dominated Google how-to searches in 2017, ranking third overall. With the hype surrounding cryptocurrency at an all-time high, now is a better time than ever to cover the essentials of keeping cryptocurrencies safe.
If you are just getting into the crypto space or you’ve known what ‘HODL’ means for a while now, there are some basics everyone should know about protecting their holdings.
Need-to-know: private keys
Let’s start with the basics. First and foremost, you should know the difference between your public and private wallet addresses (aka keys). A convenient analogy here is that most cryptocurrency wallets essentially operate like a postal box.
Each wallet has a unique public address that can be given out freely to anyone, much like you would give out your P.O. box address at a post office. This public address will only allow people to send coins to the wallet.
You also have a private address that unlocks your wallet and allows you to send coins out of it, similar to how your mail key allows you to unlock your P.O. box and withdraw your mail. This key is yours and yours only. Never share your private address with anyone.
Keeping up with your wallets’ private addresses is an exercise in personal responsibility. You don’t have a physical key to save you, and instead need to carefully store your private address (which is simply a long string of characters). Above all, storing private keys insecurely on your computer is an easy target for cybercriminals who use malware capable of sniffing out and copying your private keys.
If you choose to store private wallet addresses on your devices, never keep them in plain text format, and instead store them on a password-protected, encrypted drive. For maximum security, only print paper versions of your wallet and store multiple copies in secure places, such as a home safe or a bank safety deposit box. This technique is referred to as cold-storage, as your wallet is not stored on an internet-connected device. Hardware wallets, such as those made by Trezor or Ledger, are other options for secure storage of your crypto assets.
Risky business
Buying and storing coins on an exchange such as Coinbase is inherently risky, especially the storage part as you don’t have access to your wallets’ private addresses on an exchange. The convenience factor may be great—user-friendly apps, pretty charts, and a multitude of coins to explore—but on an exchange, you do not have access to your private wallet addresses.
To be fair, that’s part of the ease-of-use exchanges provide since you don’t have to worry about copy and pasting a private address every time you want to unlock a wallet to send from. But this also means that you are not in full control of your coins and if you were to violate any terms of the exchange (knowingly or unknowingly), they could ban your account and you would lose access to your coins. The same is true if the exchange was hacked. If they were improperly storing private keys, you could lose your coins forever.
Staying in full control of your wallet also has additional perks. In the case of a ‘hard fork’ or ‘airdrop’ to holders of a certain coin, you would be able to claim those. As it currently stands, most exchanges do not give you hard fork coins or airdrops, and instead keep those assets for themselves to increase profitability.
‘All your Bitcoin are belong to us’
Perhaps only one thing is certain in the crypto-world: hackers can and WILL try to steal your cryptocurrency.
While blockchain technology is considered an incredibly reliable, real-time database that’s proven resistant to attack and manipulation, wallet- and exchange-side security have shown numerous vulnerabilities over the years. Perhaps you’ve heard of the infamous Parity wallet hack in which an attacker exploited a wallet vulnerability to steal over 150,000 ETH (today that’s $165 million USD).
Just last week, a Google researcher discovered a bug in the popular Electrum wallet that would allow websites to steal the wallet’s contents, causing the Electrum team to quickly release a patch to fix the bug. Case in point—do your homework on any desktop, browser, or mobile wallets you plan to use. Don’t trust blindly.
Phish food
Beware of tried-and-true phishing attacks. Phishing attempts to steal private keys are abundant and targeted specifically toward unwitting investors chasing the crypto rush. Below is a phishing site that visually copies a legitimate site belonging to the wallet app Bread. Notice that the malicious URL (hxxp://breadtokenapp.com/sign.php) is just barely different than the legitimate URL (hxxps://token.breadapp.com/en/).
Dead giveaway. No website should ever ask for your private address. The same is true for exchanges as they manage wallets on their side and would never need your private keys either. The only circumstance where your private address needs to be inputted is to access a wallet. It’s a good idea to bookmark wallet sites such as the popular myetherwallet.com to make sure that you are always using the correct URL and not a phishing site.
It might seem obvious, but making sure your computer is free from malware is mission critical when dealing with cryptocurrencies. A trusted antivirus solution, secure password manager, and browser security can help protect you from would-be crypto thieves.
Have questions or concerns specific to cryptocurrency wallet security? Drop me a line in the comments below.
Update 2/8/2018:
Reports have surfaced recently that Ledger Nano S hardware wallets are susceptible to potential man-in-the-middle attacks.
The Ledger, while safe in offline storage, must still be connected to the internet to make transactions. Ledger has confirmed that their device is vulnerable to man-in-the-middle attacks (using malware that scans for the recipient’s address and changes it to the hacker’s own address). This reiterates the importance of always double-checking the wallet address that you intend to send to, as well as ensuring your computer is free from malware.

by Connor Madsen | Jan 12, 2018 | Threat Lab
The Cyber News Rundown brings you the latest happenings in cyber news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst with a passion for all things security. Any questions? Just ask.
Exploitable Backdoor Found in Western Digital NAS Drives
Western Digital has recently released numerous patches for the vulnerabilities that were found and reported to the vendor nearly six months ago. The prominent issue revolved around a hard-coded administrative backdoor that could allow attackers to remotely execute files on the drives. Unfortunately for Western Digital, this series of vulnerabilities comes not long after the same generation of drives were found with 85 different exploits (and the company waited to push out patches until after the exploits had come to public attention.)
Welsh Restaurant Closes After Cyberattack
In the past month, the owner of a Welsh restaurant has been struggling to keep the doors open on the Seafood Shack following a cyberattack that completely cleared out the restaurant’s reservation system in the weeks before to Christmas. The restaurant is currently closed after nearly a month without patronage. The systems weren’t being monitored manually, so every diner’s booked tables were left empty. In addition to the cyberattack, the restaurant also faced licensing issues after a supervisor left their employ.
Winter Olympics Organizers Targeted by Phishing Attacks
Officials working on the Pyeongchang Winter Olympics have been under a constant stream of phishing attacks disguised as Microsoft® Word documents from a South Korean intelligence agency. The documents work like normal ones, but request that the user enable macros to launch a PowerShell script. Another version of the malware even bypassed the need for user permission, and instead waited for the user to click the .docx icon to change the language to Korean before launching the same PowerShell script.
Older Zero-Day Exploit Released on New Year’s Eve
In an unusual finish for 2017, one researcher chose to release a 15-year-old macOS® exploit into the wild. The exploit requires local access to the device, but, once active, would give any attacker full root access to the machine after the user logged out of their session. Even though all Mac® operating systems are susceptible to this vulnerability, it’s only a matter of time until Apple steps in and corrects the issue and give their massive client-base some piece of mind.
Opera Browser Implements Anti-Cryptojacking Functions
With the recent emergence of cryptojacking (i.e., exploiting an unwitting user’s CPU to mine cryptocurrency while they visit a hijacked website), Opera has taken a stand and implemented crypto-mining protection called “NoCoin” in their current ad blocking filter. NoCoin works by detecting any mining activity on a visited website and stops the mining, freeing up the system’s processor for actual user-initiated applications.

by Connor Madsen | Jan 5, 2018 | Threat Lab
The Cyber News Rundown brings you the latest happenings in cyber news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst with a passion for all things security. Any questions? Just ask.
Researchers Find Major Security Flaws in Modern Processors
Newly discovered bugs, Meltdown and Spectre, exploit critical flaws in the architecture of many modern processors to leak system memory and view information that should remain hidden at the application level. This vulnerability would allow hackers to steal secret information, such as stored passwords, although there are no known exploits currently in use. Experts speculate these flaws will impact the security industry for many years to come.
‘Trackmageddon’ Bugs Leave GPS Data Open to Hackers
Two security researches have uncovered several vulnerabilities that affect GPS tracking services, including those used in child and pet trackers. These vulnerabilities range from weak passwords and unsecured folders to unprotected API endpoints, according a report issued by the research team. Hackers could potentially exploit these flaws to collect private data from these location-tracking services.
Clothing Retailer Finds Malware on PoS Devices
The LA-based fashion retailer Forever 21 revealed that a recent data breach resulted in the theft of customer credit card information. Following an investigation, While it’s still unclear how many stores and customers have been affected, the retailer advises all customers to keep a close eye on their financial statements and credit reports for suspicious activity.
Cancer Care Provider Reaches Settlement over HIPAA Violations
21st Century Oncology has reached a $2.3 million settlement agreement with the US Department of Health and Human Services following a data breach that leaked patient records and Social Security numbers of some 2 million patients. According to a press release from HHS, the breach was uncovered after an FBI informant was able to illegally obtain the company’s private patient files from a third party.
Android Malware Variant Steals Uber Data
Fakeapp malware found on Android devices spoofs Uber app to appear legitimate to users. This new malware tricks users into entering their account credentials by imitating the Uber app’s user interface. This attack underscores the need for caution when downloading apps, even from the Google Play store, as well as using a trusted a mobile security solution.


















