Top 5 reasons MSPs choose OpenText MDR
It’s an exciting time to be a managed service provider (MSP). More than ever, small and medium businesses (SMBs) are looking to MSPs as trusted advisors to help safeguard them from today’s growing cyber threats. One of the services in high demand right now? Managed detection and response (MDR). When asked about their biggest growth drivers, MSPs cite addressing clients’ cybersecurity concerns and awareness as the top new-business drivers (54%).1
For MSPs, adding MDR to your lineup can create new revenue streams while enhancing the value you bring to your clients. By offering OpenText MDR to your MSP clients, you gain access to skilled security experts and advanced technology infrastructure—without the complexity and cost of building it all in-house.
Here’s why more MSPs are partnering with OpenText to power their MDR security services:
1. Seamless integration with your existing tools
One of the greatest advantages of choosing OpenText MDR is its compatibility with your existing tools. OpenText MDR easily integrates with over 500 third-party tools, using APIs so you can add MDR services to your offerings without disrupting your current technology stack.
This flexibility also extends to popular professional services automation (PSA) tools, allowing for smooth incident ticketing and vulnerability management within your established workflows. With OpenText MDR, you can confidently grow your service portfolio while keeping your partner ecosystem intact.
2. Grow your revenue with flexible, hassle-free licensing
With cybersecurity top of mind, MSPs are seeing a surge in demand for security services. OpenText MDR helps you capitalize on this opportunity with a subscription-based model designed to grow with you—risk-free.
There are no long-term contracts, hidden fees, or minimums—just the freedom to scale your MDR services month-to-month, at your own pace, and based on your clients’ evolving needs. This flexibility lets you capture new revenue streams without overextending your resources.
3. Enhancing EDR with SIEM and SOAR capabilities
Effective MDR requires more than simply monitoring a client’s endpoint detection and response (EDR) solution—it demands a comprehensive view of the entire attack surface. OpenText MDR delivers this by enhancing your client’s EDR with advanced SIEM and SOAR capabilities.
The platform features real-time monitoring—integrated SIEM and SOAR capabilities—enabling rapid threat detection and automated response across your clients’ environments. This advanced approach safeguards your clients from evolving threats on all fronts—from endpoint to cloud.
4. Automation combined with human expertise
OpenText MDR brings together the speed of automation and the skill of experienced security analysts. This blend ensures that threats are detected quickly, incidents are prioritized with care, and responses are expertly managed around the clock, every day of the year. You get the best of both worlds—cutting-edge technology and dedicated human oversight that augments your MSP team.
With OpenText MDR, you can confidently offer clients a proactive, always-on defense against evolving threats—without the need to build up your own in-house security team.
5. Rapid incident response and proactive threat hunting
A speedy response is crucial to stopping adversaries in their tracks before they gain a foothold. MSPs can count on OpenText’s rapid incident response support, complete with dedicated escalation paths for high-priority threats, ensuring swift action when it matters most. You have the flexibility to choose whether you want the OpenText MDR team to completely manage threat response, or opt for co-managed support, where your team takes the lead with OpenText offering expert backup and resources.
OpenText MDR also delivers continuous, proactive threat hunting to identify and neutralize risks before they can affect client environments. This powerful combination of active threat hunting and fast response equips MSPs to provide clients with a robust, preemptive defense against emerging threats.
A speedy response is crucial to stopping adversaries in their tracks before they gain a foothold. MSPs can count on OpenText’s rapid incident response support, complete with dedicated escalation paths for high-priority threats, ensuring swift action when it matters most. You have the flexibility to choose whether you want the OpenText MDR team to completely manage threat response, or opt for co-managed support, where your team takes the lead with OpenText offering expert backup and resources.
OpenText MDR also delivers continuous, proactive threat hunting to identify and neutralize risks before they can affect client environments. This powerful combination of active threat hunting and fast response equips MSPs to provide clients with a robust, preemptive defense against emerging threats.
Stand out and succeed with OpenText MDR
By adding OpenText MDR to your portfolio, you can differentiate yourself in the market, offering SMBs a level of protection that goes above and beyond the competition. With 24x7x365 coverage, over 500 third-party integrations, SIEM and SOAR at no additional cost , and proven value, you’ll be able to deliver superior MDR service that not only meets but exceeds customer expectations.
Do you actually need a VPN? Your guide to staying safe online!
With the rise of online scams and privacy risks, virtual private networks (VPNs) are becoming more popular for day-to-day use. Or at least I feel like they are based on the number of ads I hear for them on my favorite podcasts.
So maybe you’ve heard of VPNs but aren’t actually sure what they are. Simply put, a VPN creates a safe, anonymous pathway for the data you send and receive over a Wi-Fi network, allowing you to browse anonymously and access content as if you were in a different location.
Maybe you’ve used VPNs as a remote worker to access resources and applications for your job, or as a student to connect to your university network. Do you really need a VPN for personal use? The short answer—absolutely! Keep reading for the long answer and for tips on choosing the right VPN.
How do VPNs work?
Essentially, VPNs create a secure tunnel for your data. The five core components of a VPN are:
- Encryption: The conversion of information into a coded format that can only be read by someone who has the decryption key. It ensures that data remains secure and private during transmission or storage.
- VPN servers: Usually located all over the world, VPN servers act as intermediaries between your device and the internet and maintain your privacy by masking your IP address and location.
- Kill switch: Blocks your device’s internet access if the VPN connection drops. This way, the VPN app makes sure you’re always protected.
- Split tunneling: Allows you to choose which internet traffic goes through the VPN (with encryption) and which goes directly to the internet.
- VPN protocols: Transmits your data according to protocols like OpenVPN, IKEv2, and WireGuard. Each cover different use cases like streaming or gaming or are required for certain types of devices.
Why use a VPN?
Maybe you already have other personal cybersecurity tools for personal user and think you don’t need a VPN. Consider the following and see if you still feel that way:
Privacy protection
Because a VPN creates a secure tunnel for your data, you don’t have to worry about bad actors peeping in on your activity and private information. This is especially important when using public Wi-Fi at coffee shops, airports, malls or hotels, where hackers can easily overcome public Wi-Fi security protocols to gain access to your device.
Antivirus augmentation
Even if you already have antivirus software, using a VPN enhances your personal cybersecurity.
Personal privacy:
- Antivirus software: Primarily protects your device from malware, viruses, and other malicious software.
- VPN: Encrypts your internet connection, hiding your online activities from ISPs, hackers, and even government surveillance. Keeps your browsing history and personal data private and anonymous.
Secure public Wi-Fi use:
- Antivirus software: Can detect and block malicious files or websites, but it doesn’t secure your internet connection.
- VPN: Protects your data on public Wi-Fi networks, which are often unsecured and a hotspot for hackers. A VPN encrypts your connection, making it much harder for anyone to intercept your data.
Accessing restricted content
I have a friend who loves British television but can’t always access it due to living in America. So she uses a VPN to set the United Kingdom as her virtual location and then watches all the BBC murder mysteries she wants.
This capability is extremely useful if you’re someone who travels a lot. For example, if you find yourself in a country with strict censorship laws, a VPN can help you access your usual content—even if it is restricted.
Which VPN should you choose?
Consider the following when researching VPNs:
- Connection speed
- Unlimited data and bandwidth
- Number and location of servers across the globe
- No-log policy*
- Security features and protocols
- Ease of use
- Brand reputation and customer support
While some VPNs may be free, they often come with limited performance, data caps, and lower security and log standards.
What steps should you take next?
Cybersecurity is only going to get more important as technology—and cyberthreats—advance. To protect your private, sensitive data, you’ll need all the tools at your disposal to keep out criminals. Add a VPN such as Webroot™ Secure VPN to your arsenal of cybersecurity tools to browse the internet safely and privately.
*A no-log policy means that the provider doesn’t keep any records of your online activities, ensuring your privacy and anonymity. This policy protects you from tracking, reduces the risk of data breaches, and prevents third-party access to your information. It also builds trust and gives you peace of mind, knowing your online activities are not being recorded or shared.
Nastiest Malware 2024
Steam the Webinar on demand HERE
As we look back on the cybersecurity landscape of 2024, it’s clear that the world of digital threats continues to evolve at an alarming pace in parallel with AI. This year has seen ransomware groups adapt and innovate, pushing the boundaries of their malicious capabilities and evasiveness from law enforcement. In our annual “Nastiest Malware” report, now in its sixth year, we’ve observed a steady increase in both the number and sophistication of malware attacks. The ransomware sector, in particular, has witnessed the emergence of “business models,” with ransomware-as-a-service (RaaS) dominating the scene. Elite ransomware authors have concluded that profit sharing and risk mitigation are key contributors to their consistent success and evasion of authorities.
The saga of LockBit in 2024 exemplifies the resilience and adaptability of these cybercriminal groups. Despite a major law enforcement operation in February, dubbed “Operation Cronos,” which saw the FBI and international partners seize LockBit’s infrastructure and obtain over 7,000 decryption keys, the group managed to resurface within days. This cat-and-mouse game between LockBit and law enforcement agencies has continued throughout the year, with the group’s leader even taunting the FBI, claiming that their efforts only make LockBit stronger. The LockBit story underscores a crucial point: while law enforcement operations can disrupt cybercriminal activities, they often fall short of delivering a knockout blow. These groups have become adept at rebuilding their infrastructure, rebranding when necessary, and continuing their operations with minimal downtime.
As we detail our analysis of the six most notorious ransomware and malware groups that have dominated headlines in 2024, it’s important to note that the threat landscape extends beyond just these actors. The rise of AI-driven phishing and social engineering, increased targeting of critical infrastructure, and the emergence of more sophisticated fileless malware are all trends that have shaped the cybersecurity battlefield this year.
In this report, we’ll explore how these groups have evolved, their most significant attacks, and the broader implications for cybersecurity. We’ll also provide updated survival tips for both businesses and individual users, reflecting the ever-changing nature of these threats.
Ransomware
Over the past decade, ransomware has established itself as the pinnacle of cybercriminal exploits. It is the most successful and lucrative avenue for monetizing a breach of a victim. Every year we see more and more data stolen and higher ransom demands dominating headlines. Each ransomware group on our Nastiest Malware list utilizes the double-extortion method where the data stolen is leveraged for leak potential on dark web leak sites. The impending damage to brand and reputation that comes with the public disclosure of a breach are massive threats to companies of any size. Not to mention the impending regulatory fines that come with the breach. This strategy has shown it’s resilience over the past few years since it became mainstream and it seems to be as robust as ever. Let’s take a look at what the payment numbers look like so far in 2024.
Source: Coveware
We’ve seen a drop-off from the highs last year – fueled by Cl0p ransomware group making over $100 Million in a few months in late 2023. But when we zoom out you can see that it will be going up over time. This time next year we anticipate the amounts to be higher than what they are now. Some of this will be fueled by inflation, some will be an increase in effectiveness in tactics, and some by the anticipated 2025 “bull run” price spike in crypto – the only payment method these criminals accept.
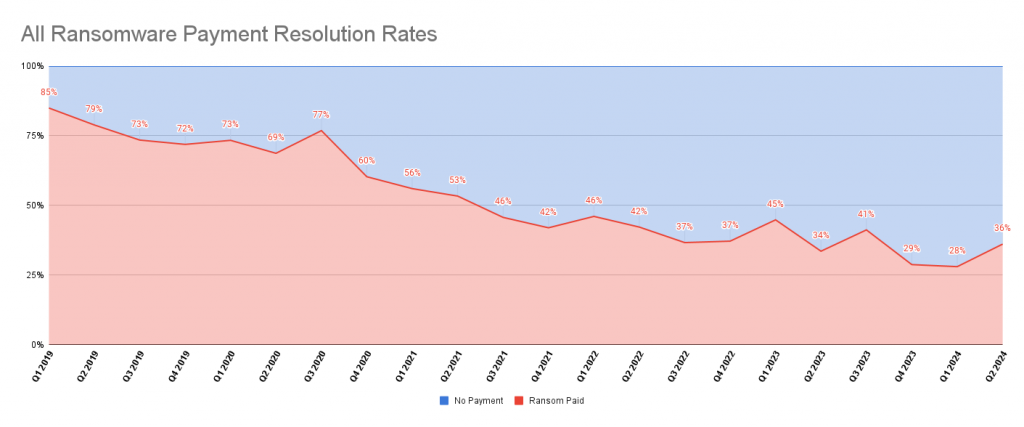
Looking at the payment resolution rates – meaning the percentage of people that end up paying the ransom, we can see a slight increase during this year. Zooming out the trend does indicate an overall decline which is good news and reflects that the industry is taking serious precautions in their security posture. We expect that this slight increase is only temporary and will continue the trend of decreasing for next year.
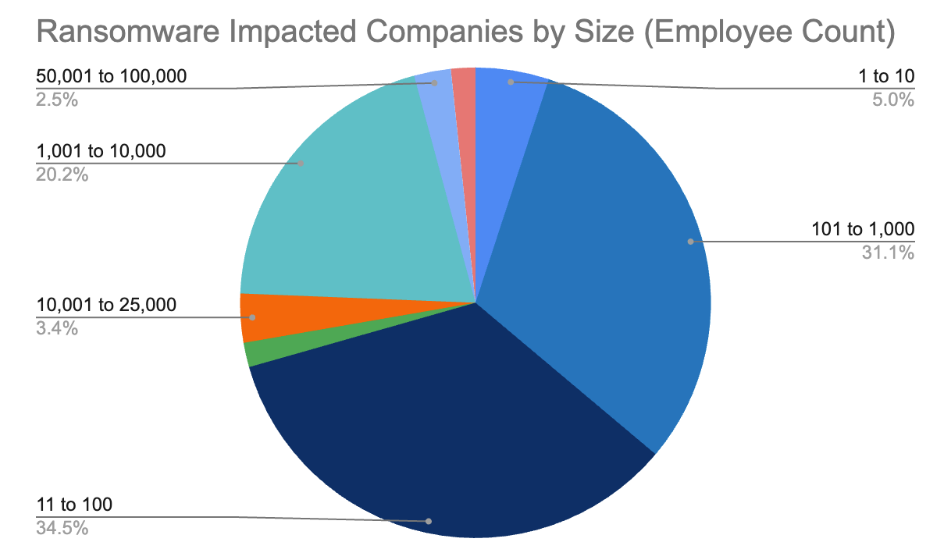
One nasty change this year is the increase of ransomware attacks on smaller sized businesses. The market share of ransomware attacks on business with under 100 employees is now almost 40%. While the media headlines of record breaking ransoms against fortune 500 companies will always take center stage, the small to mid market has always been the bread and butter for cybercriminals. The amount of effort and return on investment of time is too good for criminals not to be attracted to these easier and weaker targets. Now let’s take a look at this year’s Nastiest Malware.
LockBit: The Resilient Threat

One of the most notorious ransomware groups, LockBit, faced significant challenges and disruptions in 2024 due to coordinated international law enforcement efforts. The year began with “Operation Cronos,” a major strike against LockBit’s infrastructure in February. Led by the UK’s National Crime Agency (NCA) and involving agencies from multiple countries, including the FBI, this operation resulted in the seizure of LockBit’s leak sites and the exposure of information about nearly 200 affiliates. A pivotal moment came when the FBI obtained over 7,000 decryption keys, allowing victims to unlock their encrypted data for free. This dealt a severe blow to LockBit’s operations and credibility – remember that most of the success and money is from the affiliates that choose thier ransomware payload over another’s group so credibility and trust are paramount in this criminals scene.
Despite these setbacks, LockBit attempted to maintain its operations, quickly adapting by changing encryption methods and shifting its leak site strategy. However, law enforcement continued to apply pressure throughout the year. In May, authorities revealed the identity of LockBit’s alleged mastermind, Dmitry Yuryevich Khoroshev, and offered a $10 Million reward for information leading to his arrest. The culmination of these efforts came in October when law enforcement agencies announced additional arrests and disruptions. Four individuals connected to LockBit were arrested, including a major developer and two affiliates. Notably, Aleksandr Ryzhenkov, linked to both LockBit and the infamous Evil Corp group, was unmasked and sanctioned. These actions, part of the ongoing Operation Cronos, significantly impacted LockBit’s operations, leading to a noticeable decrease in their attack frequency and causing distrust within the cybercriminal community.
Despite LockBit’s attempts to maintain its fearsome reputation, including false claims of attacks, the group’s activities were impacted throughout 2024, marking a significant victory for global cybersecurity efforts. However, LockBit is still a major player in the RaaS scene and the leader and his affiliates are still making millions in ransoms. LockBit has proven its resilience in the face of law enforcement efforts, presenting the group’s adaptability and persistence. The leader has boasted that he loves the FBI and that they only make his group stronger, and he wants to hit one million businesses before retirement. This is a stark contrast from most ransomware groups when hit by law enforcement as they will quickly retire the brand and repivot to another. This RaaS has been on the Nastiest Malware for over three years maintaining its status as a top contender in the Ransomware scene in 2024.
Akira: The Healthcare Menace
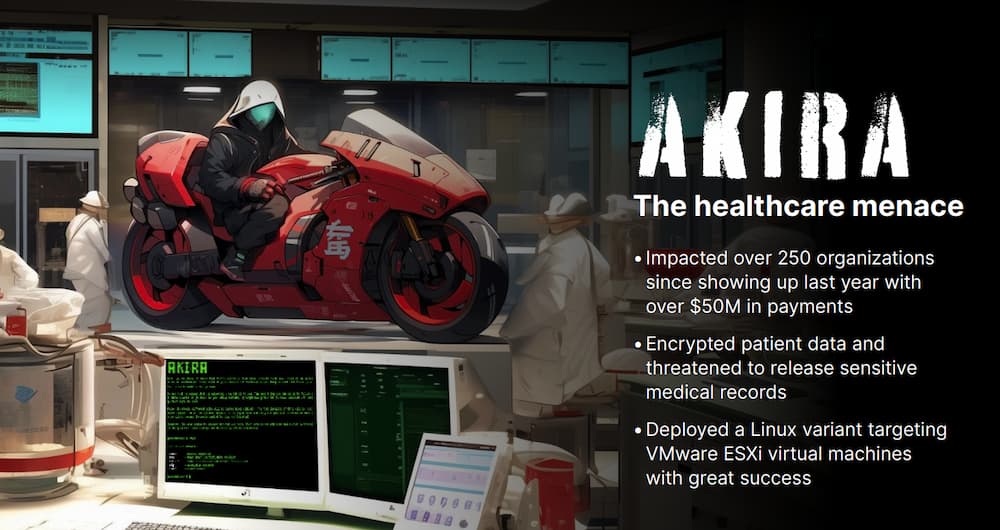
The Akira ransomware group was first observed in March 2023 and immediately became one of the most formidable threats in the threat landscape. By January 2024, the group had impacted over 250 organizations and claimed approximately $42 million in ransomware proceeds. Akira’s rapid rise to the top was marked by its versatility and constant evolution of tactics. In 2024, Akira expanded its capabilities significantly. Initially focused on Windows systems, the group deployed a Linux variant targeting VMware ESXi virtual machines in April. Throughout the year, Akira demonstrated a pattern of swift adaptation to new vulnerabilities. They actively exploited several critical vulnerabilities, including SonicWall SonicOS, Cisco Adaptive Security Appliance (ASA), and FortiClientEMS software. These exploits allowed Akira to gain initial access, escalate privileges, and move laterally within compromised networks.
A notable shift in Akira’s tactics occurred in early 2024 when they appeared to sideline encryption tactics, focusing primarily on data exfiltration. However, by September 2024, there were indications of a potential return to previous tactics using Windows and Linux payloads written in C++. This adaptability was further evidenced in a June 2024 attack on a Latin American airline, where Akira operators exploited vulnerable services to deploy ransomware and exfiltrate data.
Akira’s victims spanned a wide range of sectors, with a particular focus on manufacturing, professional services, healthcare, and critical infrastructure. The group’s success was attributed to its constant evolution, sophisticated attack methods, and the employment of double-extortion tactics. As of 2024, Akira had solidified its position as one of the most prevalent and dangerous ransomware operations in the cybersecurity threat landscape.
RansomHub: The High-Profile Attacker

RansomHub emerged as a formidable new player in the ransomware landscape in February 2024, quickly establishing itself as one of the most prolific and dangerous ransomware groups. Operating on a RaaS model, RansomHub attracted high-profile affiliates from other prominent groups like BlackCat/ALPHV following their FBI takedown in December 2023. This is likely due to its attractive payment structure where affiliates receive up to 90% of the ransom – compared to around 30-50% with other groups.
By August 2024, RansomHub had breached at least 210 victims across various critical U.S. infrastructure sectors, including healthcare, government services, financial services, and critical manufacturing. Notable attacks included breaches of Planned Parenthood, the Rite Aid drugstore chain, Christie’s auction house, and Frontier Communications, with the latter resulting in the exposure of personal information of over 750,000 customers. RansomHub’s tactics evolved throughout the year, employing sophisticated methods such as exploiting various software vulnerabilities, using intermittent encryption to speed up attacks, and leveraging double extortion techniques. The group’s data leak site became a significant threat, with stolen data being published for 3-90 days if ransom demands were not met.
The attack on Planned Parenthood not only demonstrated RansomHub’s capability to breach highly sensitive networks but also highlighted their willingness to target organizations with high reputational risks. This sparked widespread concern and discussions on cybersecurity measures within nonprofit organizations. By October 2024, RansomHub had overtaken LockBit as the most prolific ransomware group in terms of claimed successful attacks, solidifying its position as a major threat in the cybersecurity landscape.
Dark Angels: The Whaling Experts

Dark Angels emerged as one of the most formidable ransomware threats in 2024, gaining notoriety for their highly targeted “big game hunting” approach and record-breaking ransom demands. The group, which has been active since 2022, made headlines in early 2024 when they reportedly received a staggering $75 million ransom payment from a Fortune 50 company. This payment would be nearly double the previous record of $40 million paid by CNA Financial in 2021.The group’s modus operandi involves targeting a small number of high-value organizations, often exfiltrating massive amounts of data (typically 10-100 terabytes for large businesses) before considering encryption. This strategy allows Dark Angels to maintain a low profile while maximizing their profits.
In 2024, they continued to evolve their tactics, switching from a Babuk-ESXi-based ransomware to a variant of Ragnar Locker. Notable attacks attributed to Dark Angels in 2024 included a breach of a high-profile media company, where they stole proprietary information and engaged in lengthy negotiations before the ransom was paid. The group’s data leak site, named “Dunghill Leak,” is used to pressure victims into paying, though the group often prefers to avoid public attention. Dark Angels’ success in 2024, particularly the record-breaking ransom payment, has raised concerns that their tactics may be emulated by other cybercriminal groups, potentially leading to an increase in highly targeted, high-value ransomware attacks across various sectors.
RedLine: The Credential Thief

Not all of our Nastiest Malware are ransomware groups and RedLine Stealer has become one of the most prominent threats in 2024, particularly due to its capability to steal credentials and sensitive data across a wide array of sectors. Throughout 2024, RedLine demonstrated its effectiveness by stealing over 170 million passwords in just a six-month period, highlighting its massive impact. The malware’s capabilities expanded to include stealing not only passwords but also credit card details, cryptocurrency wallets, and browser data. Its adaptability and frequent updates allowed it to evade many security measures, making it a persistent threat across various sectors.
RedLine’s distribution methods remained diverse, with phishing emails and malicious websites being the primary vectors. The malware’s operators continued to refine their tactics, often disguising RedLine as legitimate software updates or enticing downloads. This approach allowed them to bypass traditional security measures and infect a large number of systems. The impact of RedLine extended beyond individual users to affect major corporations and critical infrastructure. Several high-profile breaches attributed to RedLine in 2024 resulted in significant financial losses and reputational damage for the affected organizations.
Breaking news!
In late October 2024 – RedLine suffered a takedown from a coordinated international law enforcement operation dubbed “Operation Magnus.” Led by the Dutch National Police and supported by agencies including the FBI, UK’s National Crime Agency, the operation successfully disrupted RedLine’s infrastructure and operations. The authorities gained full access to RedLine’s servers, obtaining crucial data including usernames, passwords, IP addresses, and even the source code of the malware. This breakthrough allowed law enforcement to retrieve a database of thousands of RedLine clients, paving the way for further investigations and potential legal actions against cybercriminals who used the malware. The U.S. Department of Justice charged Maxim Rudometov, a Russian national, as the suspected developer and leader of the RedLine malware operation. If convicted, Rudometov faces up to 35 years in prison on charges including access device fraud, conspiracy to commit computer intrusion, and money laundering.
Only time will tell if this seizure of assets is enough to shutdown the operations of RedLine and prevent them from bouncing back like we’ve seen time and time again from other resilient groups on this list.
Play Ransomware: The Versatile Threat

Play ransomware continued to be a significant threat in the cybersecurity landscape throughout 2024. The group, which first appeared in 2022, maintained its position as one of the most active ransomware operations, consistently ranking among the top threat actors. In 2024 a notable shift occurred when the group transitioned from its previous double-extortion tactics to specifically targeting ESXi environments. This change in focus allowed Play to exploit vulnerabilities in virtual machine infrastructures, increasing the impact of their attacks.
A significant attack attributed to Play Ransomware targeted a major utility provider, resulting in widespread service disruptions and raising concerns about critical infrastructure vulnerabilities. The attack began with the exploitation of unpatched FortiOS vulnerabilities in the company’s VPN infrastructure, allowing initial access to the network. From there, the attackers leveraged exposed RDP services to move laterally within the network, eventually gaining the access needed to deploy their ransomware payload.
The group’s use of intermittent encryption continued to be a defining characteristic, allowing them to evade many endpoint security solutions while still rendering files inaccessible to victims. Play’s attacks were particularly damaging in the IT services sector, suggesting a strategic focus on organizations that could lead to supply chain impacts.

AI-Driven Phishing and Social Engineering:
- The use of AI and machine learning in crafting phishing emails has made these lures more convincing and harder to detect. Cybercriminals are leveraging AI to personalize attacks, increasing their success rates
Targeting of Critical Infrastructure:
- There has been a noticeable increase in attacks targeting critical infrastructure, including utilities and healthcare sectors, raising concerns about national security and public safety
Fileless Malware:
- Fileless attacks aren’t new, and neither is bypassing security protections but there has been an increase in harder to detect kill chains, more sophisticated attacks, more complex persistence, that are more effective at bypassing security than ever.
New Malware Language:
- Malware written in Golang continues to trend in both scale and complexity

Businesses:
- Lock down Remote Desktop Protocols (RDP) – this infiltration tactic has been around for a while, but it’s still one of the top infection vectors!
- Enhance Employee Training: Go beyond basic awareness. Implement regular, interactive cybersecurity simulations and scenario-based training.
- PATCH OR DIE!
- Implement a Multi-layered security and defense in depth posture.
- Adopt a Comprehensive Backup Strategy: Implement the 3-2-1 backup rule with immutable backups to protect against ransomware attacks.
- Develop and Test Incident Response Plans: Create, regularly update, and practice cybersecurity incident response plans.
Individual Users:
- Use Password Managers: Employ a reputable password manager to create and store strong, unique passwords for all accounts – consider passphrases.
- Enable Multi-Factor Authentication (MFA): Activate MFA on all accounts that offer it, preferably using authenticator apps or hardware keys.
- Keep Software Updated: Enable automatic updates for your operating system, applications, and security software.
- Be Cautious with Smart Devices: Secure your IoT devices by changing default passwords and keeping firmware updated.
- Practice Safe Social Media: Be cautious about the personal information you share on social media platforms.
- Use Virtual Private Networks (VPNs): Employ a reliable VPN service, especially when using public Wi-Fi networks.
Download the infographic HERE
The new Webroot PC Optimizer boosts computer performance
Think back to when your brand new laptop or desktop ran the smoothest, operating at peak performance. Is it still that fast, or does even the simplest task seem to take forever? Before you ditch your current PC, there’s a way to get it running like new again.
First things first, though—you have to understand why your PC is running slowly.
Do computers slow down with age?
If you’ve had your PC for a while, you might think it’s running slower because of aging hardware. But not even brand-new computers run at their optimal speed due to preinstalled bloatware.
What is bloatware?
Any application or software you don’t install on your device is bloatware. For example, the last laptop I got had an antivirus software trial preinstalled—not necessarily a bad thing, but still bloatware. Maybe you have a MacBook that has creative applications like GarageBand preinstalled. That’s bloatware too.
Bloatware isn’t always preinstalled. Some applications you download may include adware or utilities that slow down your PC.
How do I get my PC to run faster?
The tricky part about optimizing your PC is that the things that slow it down can be difficult to pinpoint. Maybe you’ve deleted all your unwanted and unused apps and data, but your computer is still running slowly. If this is the case, you need a PC optimization tool .
How does PC optimization improve performance?
With PC optimization software, you can:
- Declutter your PC of junk files, unnecessary programs, and temporary files.
- Remove unneeded background processes and programs to improve speed.
- Free up bandwidth to browse and stream faster.
Why is it important to optimize your PC?
It can be tempting to give up on your current PC and just go buy a new one. But consider sustainability issues, your budget, or even the hassle of transferring all your data to a new PC and spending time configuring it. If other parts of your hardware work perfectly—the screen, keyboard, speakers, battery, and so on—it’s worth optimizing and keeping your current hardware.
From a day-to-day perspective, your PC helps you create or enjoy videos, music, photos, documents, and much more to unleash your creativity, plan your life, and run your business. You need it operating at its full power and performance to handle demanding apps like video editing or 3D gaming.
What kind of PC optimization software should you get?
Look for these five features when researching PC optimization tools:
- Registry tuner: Cleans up the repository that contains massive amount of data about your PC.
- Hard drive defragmenter: Moves scattered data blocks closer together to improve read times.
- Startup manager: Manages which applications and utilities open when you start your computer.
- Junk file remover: Finds and deletes bloatware and junk files.
- Internet connection booster: Improves your internet speed.
Webroot™ PC Optimizer check all these boxes. Along with antivirus protection and data backup, Webroot keeps your computer running smoothly. Make PC optimization part of your regular digital hygiene and see the benefits firsthand with Webroot.
10 steps to safeguarding your privacy online
The more devices, digital apps and online accounts you use, the more efficient and convenient your life becomes. But all that ease of use comes with a price. Your devices are constantly collecting your personal data to fine-tune your user experience. At the same time, hackers, and other cyber criminals are working round the clock to steal this sensitive information.
Think of your digital identity as a confidential file full of high-value information – passwords, credit card numbers, bank account details, social security numbers and more. If you’re not taking the proper steps to guard your online privacy, you could end up handing over the files to a vast army of cybercriminals.
According to the Identity Theft Resource Center, there were 3,205 data compromises in 2023. That’s a 20% increase over the previous year. A data compromise can consist of any of the following:
- Data breach: Unauthorized access to your confidential information (i.e. social security number, date of birth, credit card number, address, etc.)
- Data exposure: Confidential information is likely exposed, but may or may not have been accessed
- Data leak: Accidental exposure of sensitive information, which may or may not have been accessed
High-profile companies and organizations are not immune to these attacks. many of which resulted in consumer data exposure. Here’s just a few that happened this last year that may have impacted your personal data.
- National Public Data: Nearly 3 billion Americans had their personal records, including social security numbers, hacked and leaked on to the dark web.
- T-Mobile: About 37 million T-Mobile customers had their personal data compromised in a January 2023 hack that accessed names, addresses and birth dates.
- Ticketmaster: In May, 2024, over 560 million customer records, including names, addresses, emails, order history and payment information, were leaked online and offered for sale by hackers who infiltrated Ticketmaster.
The best defense to counter these cyberattacks is always a good offense, so be proactive and protect yourself. Here are some essential tips for safeguarding your online identity:
- Create secure passwords: When it comes to passwords – longer is stronger. Make them complex and unique, incorporating letters, numbers and symbols.
- Turn on multifactor authentication: Add multi-factor authentication to your logins for extra security. This second step helps confirm your identity by sending a text or email with a security code or question.
- Limit how much personal information you share online: Be wary of oversharing on social media. Cybercriminals can act like detectives, putting personal details together to steal your identity.
- Limit app access to your information: Apps collect your data and share it, so be sure to manage your app permissions and control how much access they have to your information.
- Adopt safe browsing habits: Update browser privacy settings and avoid suspicious websites. Also, limit the number of cookies you accept and clear your browsing history and cache regularly.
- Beware of phishing scams: Phishing scams appear in our email inboxes, text messages, social media, and even voicemails. They’re designed to trick you into giving up your personal and financial information, so learn the tell-tale signs and avoid these scammers.
- Beware of public Wi-Fi: Public Wi-Fi networks often lack security, giving hackers easy access to your data. Always confirm your connection is encrypted and avoid making financial transactions unless you’re on a private network.
- Use a VPN: A VPN (virtual private network) protects your online identity and information. A trusted VPN will encrypt your internet connection and hide your IP address from potential hackers
- Use an all-in-one device, privacy, and protection solution: For ultimate device, privacy, and identity protection, use an all-in-one device solution like Webroot Premium and get the best of all worlds –threat detection, password manager, dark web monitoring, and real-time virus protection.
- Keep your devices and apps up to date: Install updates to get the newest features and latest security upgrades. Enable automatic updates to make sure you’re always protected.
Remember that the tech that makes your life easier is also tracking you and gathering your sensitive details. Cyber thieves will never stop trying to crack the safe and steal your precious data, but with a few smart moves, you can lock them out and protect what might be your most valuable asset of all – your online privacy.
Looking for more information and solutions?
8 Tips to protect your devices from malware attacks
Unfortunately, when your devices are infected with a virus, it’s not as easy as a little bed rest for them to recover, and the damage can be long-lasting. A cyberattack can compromise your computers, phones and tablets, and open the door for cyber thieves to steal your sensitive personal information.
According to a study by the University of Maryland’s A. James Clark School of Engineering, there is a cyberattack approximately every 39 seconds. The most common form of cyberattack is malware, a type of software that’s used to break into your computer system. Last year alone, there were more than 6 billion malware attacks detected worldwide. Some of the many forms of malware include:
- Ransomware: Prevents you from accessing your files, devices or network unless you pay money.
- Spyware: Secretly monitors your online behavior and shares your personal information.
- Keylogger: Records your keystrokes as you type, then sends sensitive information like passwords and credit card numbers to hackers.
- Trojan: Disguises itself as legitimate files to monitor your online activity and steal sensitive data.
- Computer virus: Infects files and hard drives and spreads from device to device, damaging and destroying data and software.
- Adware: Installs itself on your device and displays unwanted online advertisements and pop-ups.
- Cryptojacking: Hides on your device and steals its computing resources to mine cryptocurrencies like Bitcoin.
Malware can affect any device with computing capability and it’s commonly spread through email attachments. If malware goes undetected, your devices can become locked or unstable. Here are some telltale signs that your phone, tablet or computer may have been infected with malware:
- Sudden slowdowns, repeated crashes or error messages that won’t shut down or restart
- Will not let you remove software
- Frequent pop-ups, inappropriate ads or ads that interfere with page content
- New toolbars or icons in your browser or on your desktop
- New default search engine
- New tabs or websites you didn’t open
- Sends emails you didn’t write
- Runs out of battery more quickly than it should
Ransomware is one of the most common forms of malware, and the costliest. Cyber Security Ventures predicts by 2031 a new ransomware attack will occur every 2 seconds, costing its victims nearly $265 billion. These attacks are aimed at consumers, small businesses and enterprises. Last year, there were a record number of ransomware attacks impacting consumer data at high-profile organizations such as Bank of America, Rite Aid, and MGM Resorts.
So how do we protect ourselves from this type of cybercrime? Here are a few tips for protecting your devices and information from malware attacks:
- Update your devices regularly to get the latest security patches. Most updates are easy to install and can be setup to update automatically.
- Use antivirus software like Webroot Premium to protect all your devices.
- Don’t visit suspicious websites, just block them!
- Don’t click on web pop-ups and consider using a pop-up blocker. Webroot’s Web Threat Shield detects and blocks malicious websites before you visit them.
- Don’t open emails, attachments, and click links unless they’re from email addresses you trust.
- Don’t download software unless it is from a website you know and trust.
- Use multi-factor authentication. Using more than one form of authentication to access your accounts, make it more difficult for malicious actors to gain access.
- Backup your devices regularly using solutions like Carbonite.
It may not be possible for you to avoid catching a cold now and then, but it is possible to keep your devices safe from threatening viruses. By staying vigilant, you can keep your private information out of the hands of online criminals. Because when it comes to your cyber health, an ounce of prevention really is worth a pound of cure.
For more information and solutions:
- Federal Trade Commission How to Recognize, Remove, and Avoid Malware
- 7 cyber safety tips to outsmart scammers
- Uncover the nastiest malware of 2023
- Cyber threats in gaming–and 3 tips for staying safe
- Webroot Premium, all-in-one device, privacy, and identity protection
- Carbonite, continuous and unlimited cloud backup
The state of generative AI in 2024
Generative AI has taken the world by storm, transforming how individuals and businesses interact with and trust this new technology. With tools like ChatGPT, Grok, DALL-E, and Microsoft Copilot, everyday users are finding new ways to enhance productivity, creativity, and efficiency. However, as the integration of AI into daily life accelerates, so do the concerns around privacy and security.
We’ll explore key findings from the 2024 Generative AI Consumer Trends and Privacy Survey and examine how these results are shaping the future of generative AI.
Generative AI usage: Who’s using it and why?
The survey of over 1,000 U.S. consumers reveals that generative AI is becoming a mainstream tool. Nearly 40% of respondents reported using AI tools at least weekly, with 19% using them daily. While text-based generation tools such as ChatGPT lead the pack, image creation tools like Midjourney and DALL-E are also seeing substantial use.
Top reasons for using AI
- Curiosity: 40% of respondents cited curiosity as their primary reason for trying generative AI tools. The surge in AI innovation has made people eager to explore its capabilities.
- Productivity and creativity: 24% use AI to enhance productivity, while 26% use it to boost creativity. AI is now a staple for professionals looking to streamline tasks and individuals wanting to experiment with new ideas or freshen up old ones.
AI adoption across age groups
Generative AI adoption varies widely across age groups. Younger respondents, aged 20-30, are leading the charge, with only 22% stating they have never used AI. In contrast, older users, particularly those aged 41-50, are more hesitant, with 41% saying they have never used AI. Despite this generational gap, the trend toward AI adoption is undeniable. Over half of respondents (56%) expect to increase their usage in the next year, and 63% foresee increased usage in the next five years.
Privacy concerns loom large
- 67% of respondents believe stricter privacy regulations are needed for AI tools.
- Two-thirds of respondents expressed concern about AI systems collecting and misusing personal data.
Interestingly, while many people have taken steps to protect their personal data—such as using VPNs, password managers, and antivirus software—workplace privacy protection is lagging. Only 27% of employed respondents use privacy tools and settings to safeguard workplace data when using AI.
This imbalance between personal and professional data protection underscores the need for stronger workplace policies and more awareness around data privacy at work.
Parents and AI: A growing concern
Generative AI isn’t just a concern for individual users; it’s also a pressing issue for parents. The survey revealed:
- 77% of parents are concerned about their children’s use of AI, especially around privacy.
- 49% of parents are very concerned about their children’s privacy when using AI tools.
While many parents express concern about privacy with generative AI, a significant portion of them aren’t sure if or how their children are using these tools. According to the survey:
- 29% of parents are unsure whether their children are using generative AI at all.
- 28% of parents that do know their kids are using AI, are not certain what their kids are using it for, highlighting a gap in understanding how these tools are being applied in their children’s lives.
When it comes to the specific uses of AI among children, the survey reveals that:
- 32% of children use AI for schoolwork, such as research.
- 27% use it to create images and videos.
- 32% of parents selected “Other,” indicating a broad range of possible uses beyond what parents may commonly understand.
This uncertainty shows that while parents may be concerned about AI’s impact, many are in the dark about how or even if their children are engaging with these powerful tools. This lack of knowledge highlights the need for better communication and education for parents around generative AI, particularly as it becomes more integrated into educational and recreational activities for young people.
AI’s future: Growth amid caution
Despite the growing concerns around privacy, the future of generative AI is one of expansion. A majority of respondents (56%) expect their AI usage to grow in the next year, with many anticipating the integration of AI into even more aspects of personal and professional life.
However, with this growth comes the responsibility to ensure that privacy is safeguarded. As OpenText’s Muhi Majzoub, EVP and Chief Product Officer, points out: “As personal and family AI use increases, it’s essential to have straightforward privacy and security solutions and transparent data collection practices so everyone can use generative AI safely.”
Steps to safeguard your privacy
The survey reveals that consumers are increasingly aware of the need to protect their personal data when using generative AI. Here are some common steps taken by respondents:
- Use Strong, Unique Passwords: 76% of respondents use strong passwords to protect their accounts.
- Enable Two-Factor Authentication: 64% have activated two-factor authentication for an added layer of security.
- Regularly Update Software: 69% ensure their AI tools and devices are updated regularly to avoid vulnerabilities.
Despite these protective measures, 16% of users admitted they do not know how to protect their personal information, underscoring the need for greater awareness and education on digital privacy.
Navigating the AI frontier
The 2024 survey paints a clear picture: Generative AI is here to stay, but the road ahead is fraught with challenges, especially regarding privacy. While AI continues to evolve, it’s crucial that both individual users and businesses take steps to protect their data and remain vigilant about potential security risks.
As AI continues to integrate into every facet of life, from the workplace to personal tasks, the balance between innovation and privacy protection will be key in ensuring that everyone can harness the power of AI safely.
AI and deepfakes: How to be AI-savvy
From the apps on our smartphones to chatbot assistant services, artificial intelligence (AI) is transforming our lives in both big and small ways. But as exciting as AI can be, it’s also important to understand its potential risks. October is Cybersecurity Awareness Month, making it the perfect time to become more cyber-savvy about AI. Let’s dive in.
What is AI?
AI is a technology that enables machines to perform tasks that typically require human intelligence, such as understanding language, recognizing patterns, and making decisions. In everyday life, AI is behind many of the technologies we use. It powers recommendations on streaming TV services like Netflix, improves photo quality on your smartphone, and even aids in driving cars. AI is like having a smart assistant that can process information quickly, automate daily tasks, and make technology more intuitive.
What are the benefits for everyday life?
AI offers plenty of benefits that can make our lives easier—often without us even realizing it. Here are a few everyday examples:
- Smart shopping
Ever notice how your online shopping recommendations seem to know exactly what you want? That’s the power of AI at work analyzing your preferences and making product suggestions that match your tastes. - Virtual assistants
Alexa, Siri, and Google Assistant are some of the most popular examples of AI-powered virtual assistants that simplify daily tasks through voice commands. These assistants can do things like set reminders, send texts, play music, and even provide weather updates.. - Personalized content
Whether you’re binge-watching a new TV show or scrolling through social media, AI algorithms like Netflix’s recommendation system tailor content based on your interests, ensuring you see things you’re likely to enjoy.
The drawbacks of AI
The convenience AI offers can be amazing, but with great power comes great responsibility. As AI becomes more sophisticated, criminals are finding ways to exploit it, particularly in the area of identity theft and misinformation. One of the biggest concerns today is the rise of deepfakes.
What are deepfakes?
Deepfakes are media—like photos, videos, and audio clips—created using AI to manipulate real footage or voices. These can be highly realistic, which makes it difficult to tell what’s genuine and what’s fake.
For example, imagine seeing a video of a public figure saying something controversial. At first glance, it might look entirely believable. However, with deepfake technology, their face, voice, and even gestures could have been artificially generated.
Chances are, you’ve already encountered content created by AI—whether it’s in the form of fake social media posts or altered videos. Cybercriminals can use deepfakes for malicious intent to spread misinformation, ruin reputations, or commit fraud. Criminals can also use them to impersonate individuals in video calls or to fake authority figures to carry out scams.
How to be savvy with AI
Since AI deepfakes are so lifelike, they pose a threat to our ability to trust digital content, especially as the technology continues to improve. So, how can you protect yourself from AI-driven scams like deepfakes? It’s all about becoming more aware and taking the time to analyze what you see online.
One useful approach to help you sort truth from fiction is to use the SIFT method:
- Stop – Take a moment to pause before you react to information.
- Investigate the source – Is the information coming from a reliable and trustworthy source?
- Find better coverage – Look for other news outlets or websites that cover the same topic. Do they all report the same thing?
- Trace the original context – Make sure the story or video hasn’t been taken out of context or manipulated.
The overall idea is to slow down and do your research before accepting information as true. By applying the SIFT model, you can spot deepfakes more easily and avoid falling for misleading content.
Protecting your identity from AI-driven threats
As AI technology advances, so do the tactics used by cybercriminals. They can use deepfakes to trick you into revealing sensitive information or falling for scams that seem remarkably genuine. To safeguard your identity from these AI-driven threats, here are four essential tips:
- Shield your computer and smartphone
Make sure your devices are protected with antivirus software and firewalls. Also, always update your operating systems and apps to close security gaps that hackers could exploit. - Use identity protection services
Services like Webroot’s identity protection help you monitor for suspicious identity theft activity, keeping an eye on things like the Dark Web, financial transactions, and credit bureau data. You’ll get an alert if there’s any unusual activity so you can act quickly before any serious damage is done. - Polish your password practices
Using weak or repetitive passwords makes it easier for hackers to break into your accounts. Use strong, unique passwords for each account, and consider using a password manager to help you keep track of them. - Don’t overshare on social media
The more personal information you share online, the more cybercriminals have to work with. Avoid posting things like your full name, birthdate, and home address. Cyber thieves can use these details to steal your identity or gain access to your accounts.
Final thoughts
AI has the power to make our lives easier, but it also opens the door to new kinds of threats. By becoming more cyber-savvy, you can enjoy the benefits of AI while staying safe from its risks.
This Cybersecurity Awareness Month, take the time to protect yourself and your identity from the growing influence of AI. After all, in today’s digital world, a little extra caution can go a long way in keeping you and your personal information secure.
Cyber Security Awareness Month: Cyber tune-up checklist
October is the month for pumpkin spice and all things spooky. But protecting your personal information online doesn’t need to be scary. For more than 20 years now, October has also been recognized as Cybersecurity Awareness Month.
In our digitally connected world, apps and online accounts can make our lives much more convenient. Sadly, they can also make our personal data more vulnerable to cyber threats. Each year, a shocking number of people become victims of sophisticated cyberattacks. In one recent data breach, 2.9 billion people had their social security numbers and other personal information hacked, and all that stolen data ended up for sale on the dark web.
Created by the National Security Division within the Department of Homeland Security and the National Cyber Security Alliance, Cyber Security Awareness Month promotes online safety and security for both individuals and small businesses. Its theme is Secure Our World, and its mission is to raise awareness about the importance of cybersecurity and showcase some of the easy ways we can all become more cyber resilient. By safeguarding our information from cyber threats, we can all help keep the digital world we live in more secure.
Password best practices
One of the best ways to keep your personal data out of the hands of hackers is also one of the simplest. Create strong passwords. Here are some tips for creating unbreakable passwords.
- Keep it complicated
We juggle so many passwords, it’s tempting to use something easy to remember. Unfortunately, using “12345” or “Password” just doesn’t cut it anymore. Each of your passwords needs to incorporate numbers, symbols and capital letters, use at least 16 characters. Do not use your pet’s name! - Use a password manager
Keeping track of complex passwords for each of your accounts can seem overwhelming, but a password manager offers a simple and safe solution. Quality password managers like the one included with Webroot Premium will generate, store and encrypt all your passwords, requiring you to only remember one password. - Turn on multi-factor authentication
Using multi-factor authentication adds a layer of security to your passwords by having you prove your identity in multiple ways. This means getting a text or email with a security code or answering a security question.
Identifying phishing scams
Phishing scams appear in our email inboxes, text messages and even voicemails on a daily basis. Designed to trick you into giving up your personal and financial information, knowledge is power when identifying what is real and what is in fact, fake.
Research from Deloitte found that 91% of all cyber attacks begin with a phishing email.
- Urgent requests
Beware of messages that demand immediate action and threaten consequences if you don’t respond. - Suspicious email domains
If an email is really from your bank, the address should contain the official domain name (e.g., noreply@yourbank.com.) Authentic company emails do not usually come from addresses like @gmail.com. - Poor grammar
If an email contains awkward phrases, misspellings, and grammatical errors, it probably didn’t come from a legitimate company. - Generic greetings
Your bank is probably never going to address you as “Dear Customer”. They know your name, and if they’re really trying to contact you, they’re going to use it.
If you think you’ve been a target of phishing, you can report it at reportphishing@apwg.org. For added safety, products Webroot Premium will protect you from identity theft and keep your personal and financial data out of the hands of cyber thieves.
Keeping technology up to date
Another simple weapon in the war on cybercrime – keeping your devices, software and apps up to date. When you install the latest updates you receive all the newest features, as well as the latest security upgrades. Here are some easy tips to stay continuously up-to-date.
- Enable automatic updates
Adjust the settings on your apps, software and devices to automatically update. You can schedule updates to happen overnight, so they never interrupt your screen time. - Verify your sources
Download software from known sources and only download apps from your device’s official app store. Pirated or unlicensed software can spread dangerous malware and viruses to your devices. - Avoid software updates in pop-up windows
Pop-up windows that demand a software update may be phishing scams. Close your browser and don’t take the bait.
Because we’re all connected to multiple software services, apps and devices, it’s easy to forget all the updates you need to make on a regular basis. Don’t forget to add your smart TVs, streaming services, routers and gaming devices to your update checklist. If you’re using products like Apple Watch, Google Nest or a Ring doorbell, you need to keep them updated as well.
Identity protection
Cybercriminals relentlessly scour the internet in search of leaked personal data. Guarding your personal data, especially financial details, is crucial. Here are some more steps you can take to protect your online identity.
- Invest in the latest antivirus protection
Reliable antivirus software acts like an anti-missile shield, keeping hackers from attacking your devices, including PCs, Macs, phones and tablets. - Beware of public Wi-Fi
Using public Wi-Fi networks is convenient, but not necessarily safe. Always confirm your connection is encrypted when you’re out and about, and don’t make any financial transactions unless you’re on a private Wi-Fi network. - Use a VPN
A virtual private network (VPN) protects your online privacy and helps keep your information safe. A trusted VPN encrypts your internet connection, which masks your IP address and keeps hackers away. - Keep data private when using AI
With AI so prevalent it’s important to understand how it works, be aware of how vendors handle your data, and avoid entering private data into AI apps. - Don’t let your browser store your login details
It certainly makes life easier when you let your browser remember your passwords for you, but that can backfire if your devices fall into the wrong hands. It’s always safest to enter your passwords each time you log in. - Use automatic backup
Individuals and businesses alike can keep digital information secure by enabling automatic backup. Consider using a service like Carbonite, which offers encrypted cloud backup. If your data is ever lost, a backup solution provides an extra layer of safety, offering seamless recovery of all your files and other information.
World Economic Forum estimated that 95% of cybersecurity breaches are due to human error, making it more important than ever to take steps to protect yourself online and build more cyber resilience. So, grab a pumpkin spice latte and let’s work together to create a safer online environment. October is the perfect time to make sure you don’t get spooked by cybercrime.
Looking for more information and solutions?
Protecting your identity: Stay one step ahead of cybercriminals
As October rolls around, it’s time to focus on cybersecurity. After all, it’s Cybersecurity Awareness Month—a perfect reminder to check in on the safety of your identity. If you’ve ever had your identity stolen or know someone who has, you understand how serious the problem is. From text scams to stolen passwords, criminals are finding new ways to steal personal information.
So, how can you protect yourself and your loved ones? Follow these four identity protection strategies, and you’ll be in a good position to keep your digital identity safe and sound.
1. Get informed!
- Learn about scams
Identity thieves use various tactics to trick people. Some of the most common scams include phishing emails where criminals pretend to be a trusted organization like your bank, and phone calls or texts from fake customer service representatives asking for personal details. Being aware of these tactics is your first line of defense. - Check with your bank
Most financial institutions have strict policies in place to protect your account. Get familiar with what your bank and credit card companies do to prevent identity theft. For example, many banks will never ask for your password or request sensitive information through email or text messages. Knowing their security protocols can help you spot a scam.
2. Know the warning signs
Cybercriminals are clever, and new scams pop up all the time. Here are a few things you should always be cautious about:
- Unsolicited messages
Be wary of unexpected emails, phone calls, and text messages that ask for your personal information or password details. Scammers often impersonate legitimate companies to make their requests seem official. If you receive a suspicious communication, always reach out to the company directly through their official website or customer service line. - Too-good-to-be-true offers
If something sounds too good to be true, it probably is. Handle these communications with a healthy amount of skepticism. Offers like “free money” or “prizes” that require you to share your personal information are almost always scams. Look out for common warning signs, such as a sense of urgency. Scams will often pressure you to act quickly to claim your “reward.” When in doubt, pause and investigate the offer before responding. You can search online for the company or offer name to confirm its legitimacy.
3. Know what not to share
- Social security number
Keep this number private. Only share it when absolutely necessary, such as with your employer or financial institutions. - Passwords
Never share your passwords with anyone. No legitimate company will ask for them. - Full date of birth
While some websites and services require your date of birth for verification, sharing it publicly—especially on social media—can increase your risk of identity theft. Consider only sharing part of the date, such as the month and day, and leave the year off your public profiles. - Credit card details
Be extra careful with your credit card information. Don’t email your credit card number or input it on suspicious-looking websites. Make sure you’re on a secure site (look for the padlock symbol in the address bar) before making any online purchase transactions.
4. Get proactive with your identity protection
- Monitor your credit
One of the best ways to catch identity theft early is by keeping a close eye on your credit reports. Services like AnnualCreditReport.com let you monitor your credit activity for free. If you see any unfamiliar accounts or activities, report them immediately. - Invest in identity protection services
Companies like Webroot offer services that monitor your personal information for any suspicious activity. These services can alert you if there’s a suspicious financial transaction on your accounts or if your data is found on the dark web. - Freeze your credit
If you’re not planning on applying for new credit anytime soon, consider freezing your credit. This prevents anyone from opening new accounts in your name. You can unfreeze your credit at any time, and it’s free to do so through major credit bureaus like Experian, TransUnion, and Equifax.
As cyber threats grow more sophisticated, protecting your identity has never been more important. While October is Cybersecurity Awareness, it serves as a year-long reminder to remain vigilant about your personal information. By staying informed, recognizing potential threats, and using the right tools and services, you can safeguard yourself against identity theft. Remember, the best defense is a proactive one!
What you need to know: The biggest cyber threats in 2024
In today’s world, both small businesses and everyday consumers face a growing number of cyber threats. From ransomware attacks to phishing scams, hackers are becoming more sophisticated. OpenText’s 2024 Threat Hunter Perspective sheds light on what’s coming next and how to protect yourself. Whether you’re running a small business or managing personal data at home, here’s what you need to know.
Nation-states are teaming up with cybercrime gangs
Cybercrime is no longer just about lone hackers. Now, nation-states like Russia and China are working with organized cybercrime groups to launch highly targeted attacks on businesses, governments, and even individuals.
- Russia has been particularly active, coordinating with groups like Killnet to attack critical infrastructure in countries supporting Ukraine.
- China is focusing on its political goals in the South China Sea, often collaborating with cybercrime rings like Storm-0558.
For SMBs: Be aware that even smaller businesses can be collateral damage in nation-state cyber wars, especially if you’re part of a critical supply chain. Strengthen your security measures to avoid becoming an easy target.
For consumers: Stay alert to potential phishing attacks or scams related to global events. Hackers often exploit moments of political tension or publicized aid efforts.
Timing is everything for hackers
One of the key insights from the report is how hackers choose the most disruptive moments to strike. Whether it’s during an election, the holiday season, a big sporting event, or a major business transaction, cybercriminals wait for the right moment to maximize damage.
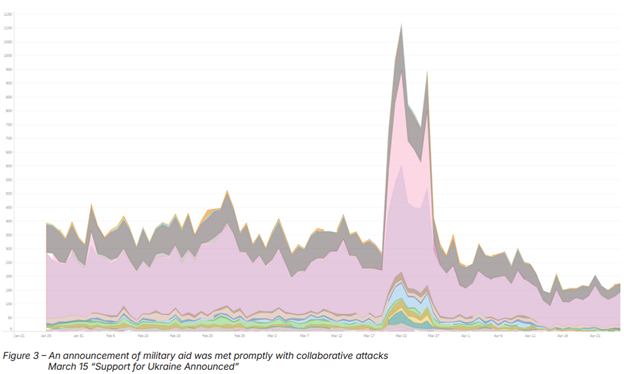
For example, businesses supporting Ukraine saw a significant increase in attacks within 24-48 hours of announcing aid. This shows that hackers pay attention to the news—and use it to time their attacks for maximum chaos.
For SMBs: Be especially vigilant during peak business times or important events, like product launches, financial closings, or holiday seasons. These are moments when your business may be more vulnerable due to distractions or heavy workloads.
For consumers: During holidays or big events (like the Super Bowl or Black Friday), be cautious of unexpected emails, texts, or promotions. Scammers love to take advantage of busy times to trick people into clicking malicious links.
Top cyber threats you need to know about in 2024
The OpenText report highlights some of the most dangerous cyber threats we’ll be facing this year. Whether you run a small business or manage your own personal data, these threats are ones to watch out for:
- Killnet and Storm0558 (nation-state-linked groups)
- Akira and Black Basta (ransomware gangs targeting businesses of all sizes)
These groups are known for launching ransomware attacks, where they lock down your systems or steal data, demanding a hefty ransom to get it back.
For SMBs: Invest in ransomware prevention and always back up your data. Having regular backups means you can recover without having to pay a ransom.
For consumers: Keep personal backups of important files (photos, documents, etc.) on an external drive or in the cloud. That way, even if your devices get infected, you won’t lose everything.
What to expect this fall: U.S. election and beyond
With the U.S. presidential election in fall 2024, the cyber landscape is expected to get even more dangerous. Cybercriminals and nation-states alike will likely target key services and use misinformation to influence the public.
In addition, the report predicts an increase in attacks on critical infrastructure—things like power grids, water systems, and hospitals—throughout 2024, as part of the growing cyber arms race.
For SMBs: Be prepared for increased cyber activity around major political events, as hackers may use the chaos to launch broader attacks. Ensure your cybersecurity measures are updated and your employees are trained to spot phishing attempts.
For consumers: Be skeptical of political content online, especially as we approach the election. Deepfake videos and fake news are expected to rise, making it harder to tell fact from fiction.
AI: Both a help and a threat
AI is playing a bigger role in cybersecurity, but it’s also giving hackers new tools. Cybercriminals are using AI to create more convincing scams, such as deepfake videos and phishing emails that are harder to detect. But at the same time, AI can help businesses defend themselves by detecting threats faster and automating security responses.
For SMBs: AI tools can help boost your cybersecurity efforts by automating threat detection, but remember that AI is not a fix-all solution. Human oversight is still crucial to ensure your defenses are robust.
For consumers: Be wary of AI-driven scams. If you receive a message, video, or email that seems suspicious—even if it looks real—double-check before sharing any information or clicking on a link.
Practical security tips for SMBs and consumers
The report emphasizes simple yet effective security measures that can protect both businesses and individuals from cyber threats.
- Keep software updated: Whether you’re running a business or just protecting personal devices, always update your software and security tools. Patches often fix vulnerabilities that hackers could exploit.
- Use strong, unique passwords: Weak or reused passwords are an easy way in for cybercriminals. Use a password manager to create and store strong passwords.
- Enable two-factor authentication (MFA): For added protection, enable two-factor authentication on your accounts. This ensures that even if a hacker gets your password, they can’t access your account without a second step.
- Train employees on security basics: If you run a business, make sure your team is aware of common threats like phishing emails and knows how to report suspicious activity.
For SMBs: Consider a cybersecurity audit to identify any weaknesses in your system, and make sure your backup plans are up to date. Cyber insurance might also be worth looking into as an additional safety net.
For consumers: Keep an eye out for phishing scams, especially during high-risk times like holidays or after major news events. When in doubt, verify the source before clicking.
Download your copy of OpenText’s 2024 Threat Hunter Perspective today
Webroot SecureAnywhere Internet Security Ranks #1 Among 8 Competitors for Overall Performance
Webroot® once again outperformed competitors in its latest round of testing by the performance benchmarking firm PassMark for February, 2023. In taking the highest score in the category, Webroot beat out competitors including BitDefender™, McAfee®, Norton, and ESET® security products.
PassMark® Software Party, Ltd. specializes in “the development of high quality performance benchmarking solutions as well as providing expert independent IT consultancy services to clients ranging from government organizations to major IT heavyweights.”
For this report, the company conducted objective testing of nine endpoint security products, including Webroot® SecureAnywhere Internet Security with Antivirus. Tests measured efficacy and performance in 15 categories including:
- Scan Time
- Scheduled scan time
- Installation size
- Installation time
- Registry Key added
- Boot time
- Use interface launch time
- Chrome Launch Time
- Memory Usage during System Idle
- Memory Usage during Initial Scan
- Browse time
- File Copy, Move and Delete
- File Format Conversion
- File Compression and Decompression
- File Write, Open and Close
The table below shows overall scores achieved by the tested products, with a score of 100 being an ideal product achieving the highest possible score in each of the selected test metrics. Antivirus products have been ranked by their overall scores:
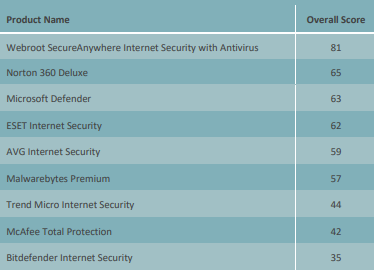
The overall scores above are only part of the story. Here’s some additional findings:
- Security scans 6x faster than average competitor
- 21x faster to install than average competitor
- Taking up 50x less space than average competitor (on hard drive)
- Uses 4 times less memory than average competitor (RAM, during system idle and initial scan)
- Fastest PC boot time compared with competitors
Not only did Webroot ranked first overall, but it also did in 7 specific benchmarks:
- Scheduled scan time
- Installation size
- Installation time
- Registry Key added
- Boot time
- Memory Usage during Initial Scan
- File Write, Open and Close
Why is this important?
Enjoying your digital life to the fullest means you can stay safe online and leverage the full power of your devices and your connections without security getting in the way. Choosing a comprehensive Internet Security solution that has little to no impact on your device’s performance helps you ensures you can work, shop, bank, play, connect, stream online without worry!
For more, check out the PassMark report.


















