Is 2015 the Year of Mac Malware?
Lots of blogs, articles and posts have been circulating recently about the increase in mac malware, mostly due to the publishing of Bit9’s report. I think it is wise to clarify what is really happening in the world of malware for Macs. Yes, there has been an increase in malware but what category do they fall under? What the consumers should be aware of and what they should be less concerned with.
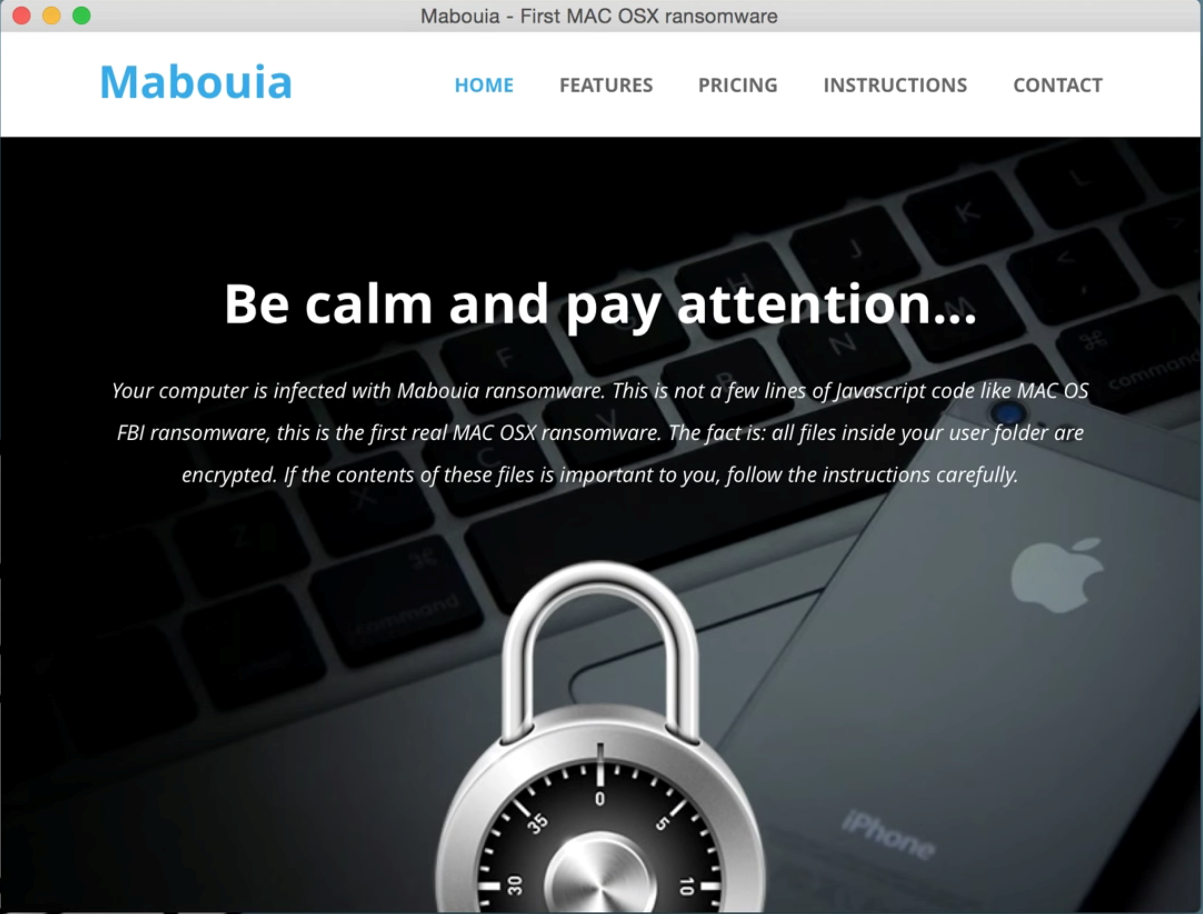
Most recently a Mac ransomware proof of concept was announced and as expected the media lost their minds. I have had the opportunity to speak with the creator of the POC and also was able to look into what it does along with what it means for future malware. The author is a threat researcher/developer named Rafael Marques from Brazil. His POC has brought massive attention to the security needs of OS X and the lack of concern that most people feel about Macs. His motive was not to create a malware to use in public mass but to help educate people that Macs are not as safe as they think. I asked him why he decided to create this and his response was to inform people “about the myth that there is no malware for mac”. I couldn’t agree more with him, I recently wrote a blog about the history of mac malware along with another one on how adware is bypassing popular ad-blockers. Although the program he wrote can do as intended, it would need to bypass a few security features thus making it a little more difficult but not impossible. A quote from Cory Doctorow best sums it up, “never underestimate the determination of a kid who is time-rich and cash-poor.”
This is where the public typically gets lost in the industry terms. The proof of concept that he created is malware, but most of the encounters that we come across on macs are not this intense, these are instead PUAs (potentially unwanted application). PUAs are still considered malware for the most part, but they are not really looked at as something to be as concerned with. 2015 has really been the year of PUAs. Every day I go through samples that contain a majority of these PUAs, most of which are adware. These adware programs will try to hide a legit programs and run in the background just to get you to click on annoying pop-ups. VSearch, Genieo, IronCore, Bundlore, Wedownload… These are just a few that we come across every day.
While these programs don’t cause any real harm to the system they do help in showing consumers that Macs are not invincible. Adware is more like a testing ground for malware authors, they create these to figure out ways around security and users. Once an author is aware of how to bypass all the security measures, what’s to stop them from writing a more complex threat? Of course one could argue that my intentions are to get people to buy anti-virus, but I didn’t go into this career to sell a product, I choose my path to help build security and promote it to the world. I think it is very important that people began taking Mac security serious. The next time a ransomware for mac comes out, it may not have a researcher like Rafael creating it to bring awareness, it may have someone wanting to make money on your expense.
CRYPTOWALL 4.0 (updated)
We know that Cryptowall 3.0 has been hugely successful for the cybercriminals netting them nearly $325 million in its debut year. With over 800 command and control URLs and over 400,000 attempted infections it is easily the most prolific threat of 2015.
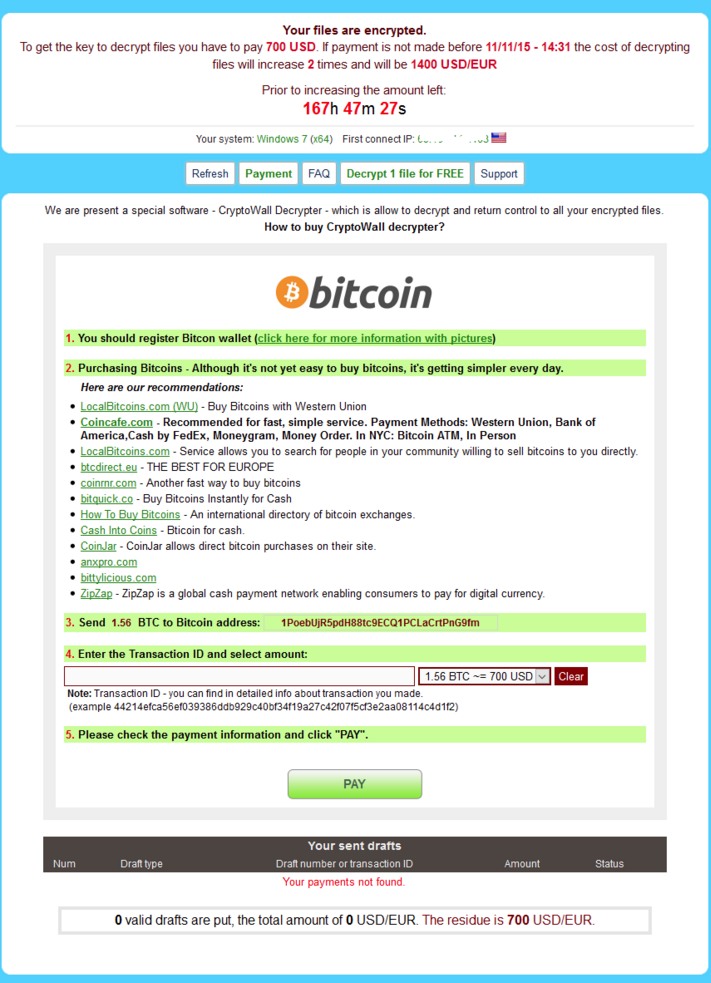
Here it is, what we’ve all been waiting for – the newest edition of Cryptowall. This ransomware comes out with new revisions almost as much as Apple does with iPhones. The bad news is that both will set you back $700.
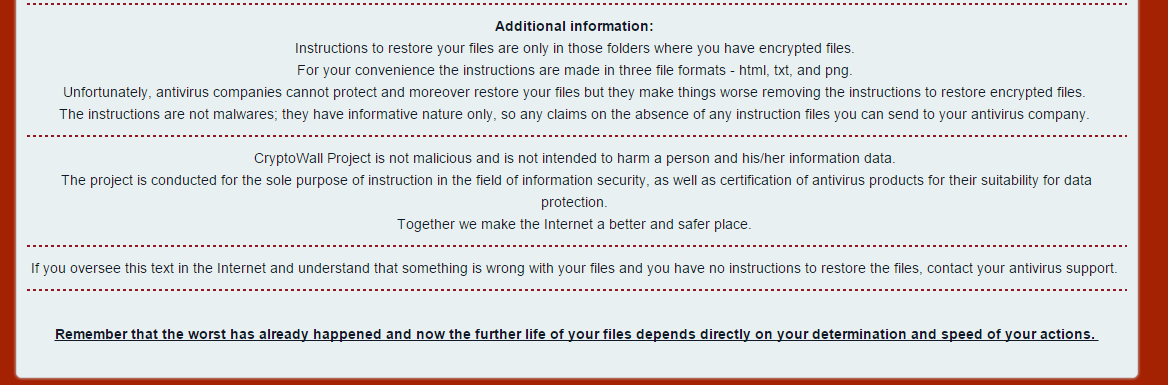
This is the locally saved html web page that it sends you to. If you don’t notice that, you’ll definitely notice that all your files have been encrypted and a new update is that the entire name of the file has been randomized so you no longer know which file is which. This is to create confusion on the severity of damage and increase the chance that you’ll pay out. As you can see from the first image they congratulate and welcome you to CryptoWall community – how nice. The rest of the instructions are pretty standard on informing you how install a layered tor browser and then connect to the darknet to pay them and get your files back. Notice the additional information they have at the bottom:
These guys actually claim that the CryptoWall is NOT malicious and not intended to harm your data “Together we make the Internet a better and safer place” – who are they fooling? Either way this is new and not seen on previous variants.
On to the payment website and and we can see they immediately want $700. It wasn’t even a year ago when the default payment was $300…
There are some new features like the a free decrypt which was first introduced by coinvault that we discovered a while back. It obviously has helped convince people that the decryption routine is fairly easy to get your files back and that the ransom is genuine and you will get your files back.
We’re currently reversing the sample and will have a more in-depth writeup of its infiltration, payload obfuscation, injection, and file encryption next week.
MD5 analyzed: E73806E3F41F61E7C7A364625CD58F65
Additional MD5 seen:
63358929C0628C869627223E910A21BF
5C88FCF39881B9B49DBD4BD3411E1CCF
32ACFA356104A9CE2403798851512654
CE38545D82858C7A7414B4BD660364A9
5384F752E3A2B59FAD9D0F143CE0215A
CF6D69E47B81FA744052DA33917D40F3
53C82D574E054F02B3163271262E0E74
A891CED376809CF05EFE4BB02EB2CBF3
5384F752E3A2B59FAD9D0F143CE0215A
Webroot will catch this specific variant in real time before any encryption takes place. We’re always on the lookout for more, but just in case of new zero day variants, remember that with encrypting ransomware the best protection is going to be a good backup solution. This can be either through the cloud or offline external storage. Keeping it up to date is key so as not to lose productivity. Webroot has backup features built into our consumer product that allow you to have directories constantly synced to the cloud. If you were to get infected by a zero day variant of encrypting ransomware you can just restore your files back as we save a snapshot history for each of your files up to ten previous copies. Please see our community post on best practices for securing your environment against encrypting ransomware.
Cyber Security and the 2016 Presidential Elections
As National Cyber Security Awareness month is coming to an end, the 2016 presidential election cycle is building momentum and increasingly becoming our nation’s primary focus. Love it or hate it, the presidential elections also create an ideal environment for thieves and cybercriminals alike. Preying on the media’s attention to buzzworthy news, hackers are busy preparing scams to exploit the attention and distraction it inevitability causes.
While the election night is still over a year away, there will certainly be a plethora of media attention given to the event. From social media’s nonstop discovery of breaking news stories to the saturation of TV with campaign ads, the election will become more front and center in our everyday lives. And in this flurry of information are many threats and scams.
While I cannot predict the specific events of the future, I can certainly look at the past to identify trends that still occur today. One such trend and tactic is to use large media events and topics as bait to lure people towards less trustworthy websites, or, in the case of an election year, to fake campaign donation websites. There are many examples from the past, from the death of Osama Bin Laden to the tragic disappearance of MH370, fake websites and social media scams were quick to follow.
So how do you stay protected?
In the wake of a big news story, make sure to be on high alert and question your curiosity when reading up on the event online or through social media. Don’t just click without thinking, consider the source of the link you’re about to click and the destination of that website. Using security technology is also helpful when browsing the web. Aside from using WSA, I also recommend using Chrome with a responsible ad-blocking extension. This combination will keep you defended from online attacks in the event you stumble across a malicious website.
Another tactic that has grown considerably in the past year is the use of telephone-based scams. While these attacks often target banking customers, the presidential election cycle creates a perfect opportunity for attacks where scammers will pose as a campaign representative requesting donations. While this isn’t technically cybercrime per se, these attacks often attempt to gain enough information to lead to further compromises in the cybercrime space.
So how can I tell if the caller is a scammer?
As a rule of thumb, I would not provide any personal information, email address, phone number, etc. to anyone who cold calls, no matter who they claim to be. That said, the election cycle creates a temporary exception in where you might not be surprised to receive a call requesting campaign financial support. Phone scammers can be very convincing and have answers to many initial security concerns. The person might suggest sending you an email with more information about the cause they are campaigning for, which will then be used to further the scam along. A good way to handle such callers is being firm in that you don’t give out such information, and request to be removed from their calling list. If you want to donate, call or visit the foundations website directly. You can also improve telephone-based security on a smartphone by using a phone ID app such as TrueCaller. Such a service can provide you with community-based information about an incoming call.
Ultimately, these are just two examples of threats that will use the 2016 presidential election to their advantage. As the election nears, the number of such attacks will increase and so must your security awareness. While National Cybersecurity Awareness Month has wound down, the lessons taught and learned will continue to be important in order to stay in front of the adapting threat environment.
FBI says to just pay the ransom
We all know cryptolocker and we all know the toll it’s taken on many individuals and companies. While the original cryptolocker has been shut down since FBI operation Tovar it has not stalled the many variants of encrypting ransomware from becoming a plague to the user (looking at you cryptowall). The “business model” just isn’t going away and is only seeing improvements as time goes on.
Recently in a blog post it was suggested by the FBI to just pay the ransom. With encryption being so sophisticated and the key never stored on the machine I can honestly say that I agree. If you really need the data that was encrypted and your current backup solution doesn’t suffice for the data you’ve lost there is literally nothing you can do to get that data back other than pay the ransom. It’s a sad state of affairs, but this is where we’re at – proactive backup solutions beforehand or bust. Sure there are tools like Shadow explorer that will work if you’re hit with something that’s not killing the Volume Shadow Service (VSS), but that is an elementary error and most encrypting ransomware campaigns are packing the best payloads that make no mistakes. If you have no recent air gap backup or cloud syncing backup that lets you keep old copies, you really have no options other than starting from scratch again and “sticking it to the hackers” but really only individual consumers have the financial freedom to make that choice. Most scenarios where I know victims paid the ransom are because it was a huge hit to their businesses productivity.
For example, let’s say a small business that works as a reseller ships out thousands of products a day and their label printing machine was hit with cryptowall. They aren’t able to print any of the custom saved labels that use on a daily basis and it’s catastrophic to their business for a couple days. The $300 – $500 ransom really is nothing in comparative to the thousands of orders that they couldn’t ship until they get those shipping labels. Most of the time they spend deciding if they should pay isn’t because it’s too much money, or they “shouldn’t support terrorists” but the concern that they wouldn’t get their files back and would be effectively scammed again. In the end, after failed searches for backups and having this huge await shipment line, they just decide it’s worth it to risk throwing the money away and pay the ransom. They get their files back pretty quickly and now can resume shipping.
Most stories are similar to this and when I’ve asked them how paying the ransom went they’ve said that if they knew it would be that easy to get their files back, they would have paid sooner. This is where we are at – criminals putting a gun to our files and demanding payment. It’s worked great the past couple years since it started and it’s only getting better; I see no end sight to this.
Looking forward is even more troubling since once the bad guys start figuring out who can afford more of ransom is when things start getting real hairy. Sure $500 is nothing to resume business as usual, but what if it was a $50k ransom? There would be entirely different discussions internally before deciding to pay.
Mobile Malware – A problem or not?
Recently I was asked to give my thoughts on mobile malware. I was asked this in relation to a number of reports released earlier in the year that were in my view misinterpreted. At the time many experts claimed mobile malware had been a much-exaggerated threat, based on such a large proportion of unwanted mobile apps/programs were seen to be adware.
Personally, I think it’s better to discuss mobile threats, mobile threats are more than just mobile malware. Many legitimate Apps have been seen over the last few years to be open to serious data leakage and only recently we have seen the discovery of Android’s “Stagefright” vulnerability – pegged as the “worst Android bug to date”. Receiving a simple MMS message with crafted exploit code, and without any interact from the victim, a hacker is able to do anything from stealing private communications to possible taking control of the device itself.
Read more: https://goo.gl/xCvGa6
In September, we saw “XcodeGhost”, this highlights the Apple App Store isn’t immune to serving up compromised apps. The Xcode development tools are used by iOS app makers. The original package was copied, modified, and then re-distributed for download. Apps built using the modified version were injected with malicious code, then published to the App Store.
Read more: http://goo.gl/VYEBgk
Mobile malware is a problem and is getting bigger with the ever increasing growth of the mobile market. There is concern that enterprise decision makers may misinterpret such reports and may not take mobile security as seriously as they should. Enterprises should be very concerned about mobile threats, this includes, mobile malware, mobile vulnerabilities and mobile data loss.
Mobile adware itself is a huge problem and needs to be addressed. Adware can collect personal information from the device it’s installed on, often without consent, including many pieces of PPI. Enterprises allowing such devices to connect to the private network should be seriously concerned, information is power, and company secrets are a secret for a reason.
The recent case of “Gunpoder” also highlights a new strategy malware writers are using. The game emulator app looks and behaves like adware, all while stealing PPI from the infected Android device. Many AV companies classified this malicious app as adware and many users thinking that adware was ‘more annoying than dangerous’ allowed the app to run.
Read more: http://goo.gl/Wm6Oyz
Cyberattacks are more prolific than ever, and businesses are clearly struggling in the battle of keeping their employee and customer data safe. Cybercriminals look for the simplest method to achieve their objective, if that’s through a mobile device and an uneducated user, then so be it. Mobile infiltration is often a precursor to further attacks.
Ignoring mobile malware and security, at any level, could have huge repercussions on a business’ reputation and customer loyalty as well as financially – it’s important not to leave the front door open.
So what can we do?
With all security implementations, striking the balance between mobile security and productivity is an on-going challenge. At present I would suggest it’s weighted towards productivity. Productive employees are great, but at the same time the company’s assets have to be properly secured. Therefore the fight against mobile malware needs to be appropriately evaluated in terms of personnel and monetary resources.
Mobile security is just another problem that arrived on the doorstep of the security and/or IT team, and on many occasions without any extra budget allocation. Like with many facets of cybersecurity it only becomes a priority after the inadequate defences are breached and company stakeholders want answers.
Companies need a mobile security strategy. They also need to follow best practices and keep abreast of industry information and security bulletins. Any strategy must consider corporate devices and BYODs. Organisations need to keep on top of patch management and understand what technologies best address their security needs, these may include centralised app management and app reputation technologies and in case of device loss – consider encryption and remote wiping.
Like with any device on a network, threat protection should be installed and kept up to date. Webroot offers mobile security apps for both Android and iPhone. The corporate network can be protected further by directing mobile traffic through special gateways with customised firewalls and security controls. Mobile devices should be configured to avoid unsecured wireless networks.
It goes without saying that devices need strong authentication and password controls.
Remember, mobile security and security in general is a continuous practice. It’s essential to implement a comprehensive mobile security strategy, then check how well training and policies are being interpreted and implemented with regular mobile security audits and tests. Communication between the organisation and its employees is vital – the risks and potential consequences need to be understood by employees through continued user education. At the same time organisations need to understand and respect the now slightly blurred boundary between business and personal.
Cybercriminals only need to find one hole in the defence, whereas security professionals have to secure all possible points of entry. It’s a battle we may lose from time to time, but we have a responsibility to make it as hard as possible for our adversaries.
Why do we need National Cyber Security Awareness Month?
As the 12th annual National Cyber Security Awareness Month enters its final week, we’ll look at the future of technology and the potential vulnerabilities that come with it. As President Barack Obama has stated, “Cyber threats pose one of the gravest national security dangers the United States faces,” and that is why we all need to be mindful of the “smart world” we now live in. It is our shared responsibility to be aware of the importance of cyber-security as the number of Internet-connected devices around us increase. Surveys show that in 2014, 47% of adults in the United States had their personal information exposed by hackers.
Our phones, tablets, and personal computers are the most obvious devices that need protection, but what about the “Internet-Of-Things” devices? From vehicles to watches to kitchen appliances, more and more of our household objects are becoming “Smart” items, and each device stores and transmits private personal data. Health monitors, baby monitors, coffee makers, home environmental controls; whatever the device, if it connects to the internet, it can potentially be exploited by a determined hacker.
This is something that all device manufacturers need to keep in mind, since most consumers won’t usually have the ability to install security software on these devices themselves. But there are a few security tips that we should all keep in mind:
1. Protect your network. This means changing the default Administrator password on your router, using strong (WPA2) wireless network encryption, and changing your WiFi password occasionally. See our “Tips for Improving Router Security” blog post for more information.
2. Protect the devices you can. Whether you use a PC, Mac, or Android device, you will need an antivirus application to protect you against malware. If your network is breached, having devices that are well protected will sometimes deter a hacker who is looking for easy targets. Webroot provides this defense with cloud-based malware detection that automatically stays up to date.
3. Don’t be an early-adopter. When a cool new device comes out, it’s tempting to be among the first to have it… but the first versions of any “smart” products are the most prone to security flaws. By waiting until a second generation device or a first software update for the device, you may reduce your risk of using an insecure product.
While the technology of the future becomes increasingly Internet-connected, it is our shared responsibility to remain vigilant about security and ensure that it is incorporated at every point of access.
For more information about this month’s themes and events, see the Official Department of Homeland Security National Cyber Security Awareness Month page.
Tips for Card Security and Fraud Protection
Cyber-criminals love to hit consumers where it hurts, and I’d say the most vulnerable location would have to be our wallets.
I frequently receive inquiries asking how a consumer can better secure their credit card and financial accounts. This ultimately led to me authoring this blog as a point of reference. Fortunately the industry is beginning to implement better practice and new methods to prevent this, and as always, someone, somewhere, will eventually find a way around that.
I’ve included a few tips here that everyone should acknowledge, and a few that may not be relevant to your environment. Obviously there are a TON of steps you can take to better your security, but if I wrote them all down, we would have a novel as opposed to a blog post. For the sake of being concise, I’ve kept this short and sweet, so to speak.
- Physical security is important, keep your credit and debit cards in a secure location that only you can access.
- Never write down your PIN, and make sure it is not personally identifiable information such as birthdays, phone numbers, etc. Cover it up when entering it publicly.
- Make sure that you add your signature to your card, this is something that most neglect or have neglected to do in the past. I know I’ve certainly been guilty of it.
- Regularly review your statements for transactions you do not recognize. Cyber criminals will frequently make minuscule charges first to see if you are checking your statements, and if not, make larger transactions. Some of the most successful campaigns such as this have accrued countless amounts of money with charges as small as a penny at a time.
- Before using your card at a public ATM, ensure that the machine has not been tampered with. Skimmers are becoming smaller and more popular methods for scraping card data.
- Confirm that when making a withdrawal, the amount on the receipt matches the amount withdrawn. Shred the receipt before disposing of it.
- If you receive a new card, completely destroy the old one.
- When purchasing anything online, ensure that the website utilizes HTTPS. Never submit financial or personal data via unencrypted connection.
- As stated in my previous blog, always log out of a website, app, or platform when you are done using it. Most websites and banking apps now implement a time-out policy that requires re-authentication after a certain time frame.
- Never write down your entire card number on a physical medium and never mail it.
- Always keep your card within sight of you. If a teller needs to take it to a machine, request that you accompany them, or ask them to bring the machine to you.
- Avoid using public computers whenever possible and never make important transactions on an unsecured network.
- As we move into chipped base cards that offer more protection, cyber criminals now have the ability to scan these cards. While in its early stages and having limited range, this technology will continue to improve. If you utilize one of these cards, invest in an RFID sleeve to prevent your data from being swiped.
There is a lot more that could be added to this and as we see security measures improve, we will also see the technology to compromise them improve as well. What is secure today, may not be tomorrow.
What is a computer virus?
It is a long-standing joke that if you do a web search on any medical symptom, it will always lead to a web diagnosis of cancer. In the same manner, searching for any computer problem will always lead you to conclude that you have a nasty computer virus. Chances are you have never had, and never will have a computer virus, as this handy Venn diagram from XKCD.com demonstrates:
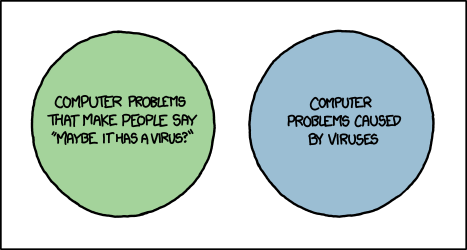
Now perhaps I’m being a bit nit-picky about the connotation of the term “virus” but there is quite a bit of misinformation and FUD (Fear, Uncertainty and Doubt) out there when it comes to computer viruses. Wikipedia defines a computer virus as “a malware program that, when executed, replicates by inserting copies of itself (possibly modified) into other computer programs, data files, or the boot sector of the hard drive.” The key here is that a virus spreads via various methods of replication – infecting other files. The vast majority of malware does not do this, and a virus is not going to change your home page, display pop-up ads, or install a toolbar as adware or Potentially Unwanted Applications (PUAs) may do. Your printer issues are not being caused by a virus either.
If you search for the name of any browser redirect, toolbar, pop-up ad, or any number of other computer problems you will almost always end up on a web page that claims the issue is due to a virus. These pages are rarely from reputable security vendors, and are often security blogs that feature prominent advertising for various legitimate and not-so-legitimate security software. The term “virus” is used to make you think the problem is far worse than it actually is in hopes that you will purchase the advertised security programs. These tactics are similar to those used by Rogue Security Software and tech support scams.
If you are searching for more information on a computer problem, pay attention to the sites that come up in the results, and to the terminology used. If the term “virus” comes up, chances are that the result is not from a trusted security company or computer support forum. There are several general computer support forums out there which offer excellent free support for general computing issues. For issues related to specific programs or hardware, most companies have their own support forums these days, and in many cases someone else has experienced the same issue that you are having.
Are antivirus testing scores a true reflection of our Mac product efficacy? You decide…
In a world full of new malware and various types of cyber threats continuing to pop up on a daily basis, the average consumer has reached a point where a good antivirus security solution is an absolute must; even when dealing with so called “immune” operating systems like Mac OSX. However with so many antivirus products to choose from for the Mac, how is the average consumer supposed to make sound decisions about which product will give them the best protection and the greatest peace of mind?
These days, most consumers in the market for a new product simply jump on Google and look for general product reviews; however with so many mixed results, and an array of product features to choose from and compare, the antivirus playing field can quickly become very confusing and overwhelming. As an alternative, another source of information that consumers turn to for data about antivirus solutions are third party antivirus (AV) testing companies. For years these companies have performed baseline comparative tests on many of the most popular AV products in an effort to test the product’s malware detection and remediation capabilities, as well as looking at how machine performance is affected by the product being installed and run on the user’s machine. In recent years they have also started to do testing for AV products being developed for the Mac OSX platform. The results of these tests are typically published with an overall bottom-line score for each product being tested, which is based on the product’s overall malware/virus detection percentage.
As a result, the average consumer looking at these tests will use some type of previous brand recognition or family/friend influence, in conjunction with the AV testing scores, in order to make a swift decision on the “best” antivirus software for their needs. It is easy for the human psyche to say, “Oh this product scored 100%, so it must be good.” The issue with this type of decision making process is that unfortunately the assumption is made that all AV products are created equal, and that the Mac AV testing platform and testing methodology creates a true simulation of real world execution and installation of the malware being tested. This could not be further from the truth.
In order to test the true efficacy of an antivirus product, AV testing companies should actually be installing the malware and executing the viruses in question, in order to see how the antivirus product handles an actual simulation of an end-user infection. Unfortunately, the reality of the situation is that AV testing companies generally do not use “real world” simulations of malware executions and installs when testing Mac AV products. Instead they perform their tests using a method called “zoo testing,” which involves putting hundreds of malicious file samples into a folder and then putting that folder somewhere on the testing PC before running their test. Often these files do not even reside inside of the full Mac bundles necessary for execution or have even had their executable bit stripped from the binary, in effect making them benign to any system. The issue here is that none of the malware is actually executed or installed on the testing machine, nor does it constitute any kind of real threat to the system. In addition, this type of approach is often easily “gamed” by AV companies that are simply looking to do well on the test.
Without getting too technical, in recent years advancing technologies in the antivirus industry have continued to make leaps and bounds in terms of the detection and remediation methods and backend systems that are being used to detect malicious activity and protect end users from security breaches on their machines. Webroot has been a pioneer in implementing technologies that are forward-thinking, adaptive and have brought our product efficacy to unprecedented levels. Unfortunately, in order to actually be correctly tested on the effectiveness of these newer methods and technologies, it requires AV testing companies to install real infections, rather than a zoo of files that can’t even be executed. AV testing companies have been reluctant to adapt their Mac testing methodologies to changing technologies and approaches. So, what does this say about the validity of AV test scores? Does this approach make AV testing results a useful tool for sound consumer decision making when deciding on a Mac security solution?
AV testing has been a big concern for many companies over the years. We all want our products to perform at a high level and carry a positive market leading reputation. For many AV companies this has been true to the extent that they focus their primary client development efforts towards malware detection for AV tests, rather than real life infections. Isn’t this approach a detriment to the effectiveness of the product for the end-user? Here at Webroot, due to known issues in the AV testing climate, we have shifted priorities in order to drive our efforts and innovation into developing the best security products and customer experience that we can attain. We believe that our excellent standard for real world efficacy, in addition to the many value added features that are built into our products, bring the greatest value to our customer base.
10 Tips for Improving Your Home Router Security
With the recent news of router vulnerabilities, we thought it would be an excellent time to provide a few tips for improving your home router security. While nothing is hack-proof in the world we live in, you can take many steps to deter attackers from targeting you. I have arranged this from easy to do, to increasingly technical.
Simple steps to secure your home router
- Create a unique login. Most routers use a default login username such as “admin”, and a password that is usually just “password”. Be sure to change the login information (username and password) to something unique to you. Please note that this is different than your WiFi name and password.
- Create a username and password for your connection (WiFi). Consider changing it from the default to something that is not personally identifiable. Ideally, you DO NOT want your the manufacturer (Netgear. Linksys, etc.) or address as your WiFi name. Choosing WPA2 over WPA or WEP is also advisable. A long passphrase as your password that contains more than 20 characters is important here. REMINDER: you can disable the SSID broadcast so that only users that know your network name can connect. If you plan on having guests, create an entirely different Guest network. It is never advisable to give the credentials to your main connection.
- Avoid using WiFi Protected Setup (WPS). WPS is a nice convenience, but it leaves your WiFi network vulnerable. Malicious actors can use this to attempt connection with a PIN, possibly leaving you open to brute-force attacks.
- Keep router firmware up-to-date. Unlike your computer, your router doesn’t send reminders for new updates. It will be up to you to make sure you’re logging into your router regularly to check for updates.
More complex security tips
- Disable Remote Administrative Access. In addition, consider disabling administrative access over Wi-Fi. An Admin should only be connecting via a wired Ethernet connection.
- Change the default IP ranges. Almost every router has an IP resembling 192.168.1.1 and changing this can help prevent Cross-Site Request Forgery (CSRF) attacks.
- Restrict access via MAC addresses. Your router gives you the capability to specify exactly what devices you want to connect so that others are not permitted. You can usually identify the address of the specific device in the Admin Console of the router.
- Change from the standard 2.4-GHz band, to the 5-GHz band. If the devices you use are compatible, it is generally advisable to make this change. Taking this step will decrease the range of the signal and could stop a potential attacker that is farther away from your router from discovering it.
- Disable Telnet, PING, UPNP, SSH, and HNAP. You can close them entirely, but I generally advise putting them into what is referred to as “Stealth” mode. This stops your router from responding to external communications.
- Log out! This does not just apply to routers, though. You should log out of any website, utility, or console when you are done using it.
These router security tips should help protect your WiFi data from cybercriminals desiring to hinder your online activities.
Tech Support Scams Continue
We’re regularly asked about phone calls from “Microsoft” claiming that your computer is infected, and whether or not it is a scam – it is. Sometimes it’s a call from another “tech support” company, or a warning message on your screen. The truth is that Microsoft and other companies will not contact you to tell you that you have a computer problem through a phone call, email, or a pop-up warning message.
These scams are nothing new. We blogged about this previously in April of 2013 and a lot has changed in the malware world since then, but these scams continue. That we’re bringing these scams up again tells you one thing though – people continue to fall for them – don’t let yourself become a victim of one of these scammers.
If you’re contacted by one of these scammers, hang up, don’t click that link, and don’t call that number. Usually they’ll try to get them to let you access your computer remotely – don’t let them, and certainly don’t give them any personal information or a credit card number.
As long as you don’t let them log on to your computer remotely or download and install any software because of these scams you probably don’t have anything to worry about. These scammers don’t typically install malware on your computer; the scam is to get you to pay for tech support that you don’t actually need.
More information can be found on scams using the Microsoft name at the following links:
http://www.microsoft.com/security/online-privacy/msname.aspx
http://www.microsoft.com/security/online-privacy/avoid-phone-scams.aspx
http://www.microsoft.com/security/online-privacy/avoid-phone-scams.aspx
Keep your personal data personal
It’s National Cybersecurity Awareness Month in the US and Stay Smart Online Week in Australia, so you might say that security is on the minds of more people around this time. So as we start taking the lessons in and changing some of our habits, there is another area that could use more attention; our personal data.
With a large variety of social networks available around the world, the opportunities to share are endless, but with that, so is the opportunity for information gathering by malicious parties as well as chances that private information could be revealed in a breach. One way to avoid this from occurring is by being careful with your information and be aware with what information you give out. An example of this can be seen from the recent Ashley Madison scandal where people not only posted their real names and personal details, but also linked their work email in some cases, embarrassing not just themselves but the organisations they work for. Also the less information you give out (like emails and phone numbers) the less likely you’re hit with spam.
And then there comes the personal data that you carry with you, be it from home to the office or on your next big vacation. This data could be stolen and compromised for malicious intent such as stolen identities, financial fraud, or even blackmail.
It’s always handy to encrypt your drive, whether you travel with your device or not. It is vital to encrypt a drive if it has sensitive data on it relating to you or the organisation you work for. There has been quite a few cases in this country where unencrypted devices from organisations go missing with customer data on it, then the Data Protection Commissioner will get involved and likely impose penalties on the organisation. An example of this: http://www.independent.ie/irish-news/three-eircom-laptops-containing-customers-data-including-bank-details-stolen-26820140.html. As well as encrypting your drive, don’t keep sensitive data (passwords, security questions, info you don’t want other people to see, etc.) in unencrypted text files lying around your system. If anyone gets access to the computer these files will be compromised.
In this day and age it can never be too much effort to keep personal data personal, and with a few steps, you can help minimize the risk to that information. While some might take time to get used to, a healthy habit of being aware will only help in the long run.