We analyze Cryptobot, aka Paycrypt
Recently during some research on encrypting ransomware we came across a new variant that brings some new features to the table. It will encrypt by utilizing the following javascript from being opened as an attachment from email (posing as some document file).

Malicious script from email
Once full encrypted you’ll get a popup text document informing you that all your files have been encrypted and how to pay money to get your key to decrypt. This specific sample is Russian, and the instructions were also in Russian so I didn’t show it here. The really interesting thing about this variant that I wanted to share is that once it finishes it actually shows you a twitter feed that populates a tweet every time someone pays the ransom. I suspect this does increase the chance that people will pay the ransom.

Blurred out emails of the victims who paid
Webroot will catch this specific variant in real time before any encryption takes place. We’re always on the look out for more, but just in case of new zero day variants – remember that with encrypting ransomware the best protection is going to be a good backup solution. This can be either through the cloud or offline external storage. Keeping it up to date is key so as not to lose productivity. Webroot has backup features built into our product that allow you to have directories constantly synced to the cloud. If you were to get infected by a zero day variant of encrypting ransomware you can just restore your files back as we save a snapshot history for each of your files up to ten previous copies.
What To Know About Apple and WireLurker
Everyone’s heard the saying ‘Macs aren’t malware-proof’, right? Oh, you haven’t? Count me not surprised.
It could be due to the fact that that’s not an actual saying, but the more likely reason is that there is a deep-rooted belief among Apple users that Apple products and services are somehow, by default, impervious to viruses, malware, hackers, etc. Allow me to reiterate: THEY’RE NOT!
Need proof? Well, we could look back two years ago to Dexter (not the hit Showtime show). Or let’s rewind to early this year, when researchers learned that Macs were still vulnerable to 2011’s famous ‘Flashback Trojan’? Or how about iDroid, the mobile trojan capable of infecting both Android and iOS devices? Then there was September’s iCloud hack fiasco that started the wave of nude celebrity photos across the world wide web. And then, just yesterday, it came to light that two of Apple’s security tools, Gatekeeper and XProtect may not pick up the recently-discovered iWorm malware.
But just in case all that isn’t enough, enter WireLurker, the newest piece of evidence to back up the ‘Mac-and-iOS-malware-is-real’ school of thought.
(Source: Mashable)
Discovered by security researchers from Palo Alto Networks (you can download the report here), WireLurker is a new family of malware that was found in the wild on a popular third-party Chinese app store called Maiyadi, and that allows hackers to infiltrate iOS devices through an infected Mac via a USB connection (only the second known instance of this kind of iOS attack). But what truly makes it unique is that it’s able to infect iOS apps in a fashion similar to a traditional virus and, even more importantly, it doesn’t require for the iOS device to be jailbroken to do its damage.
According to the report, WireLurker has already ‘trojanized’ 467 OSX apps in the Maiyadi App Store. Those apps have been downloaded 356,104 times.
The (relatively) good news is that this malware attack is pretty limited in scope. We were able to secure a quote from Ryan Olson of Palo Alto Networks, one of Webroot’s technology partners:
“Our lead researcher on this effort, Claud Xiao, first began investigating the malware after seeing reports of strange activity on Mac OS and iOS devices in China. He tracked the attack back to it’s source and took a deep dive into the malware to discover how it works. We don’t expect this WireLurker malware to spread to the United States, but the tactics that it uses are likely to be copied by new attackers who could have new targets in mind.”
An Apple spokesperson offered some more good news:
“We are aware of malicious software available from a download site aimed at users in China, and we’ve blocked the identified apps to prevent them from launching. As always, we recommend that users download and install software from trusted sources.”
The fact that WireLurker is only targeting users in China may be a sign of relief for the West, but, as Olson pointed out, it doesn’t mean a similar attack couldn’t be expanded to wreak havoc outside of China. iOS (unlike OSX) has had a fairly spotless record when it comes to malware up until this point (if you don’t factor in ‘jailbroken’ devices), but WireLurker is the first real virus scare for the OS because it doesn’t require a jailbreak to infect the device, making it an exception to the ‘the Apple App Store is the best protection against viruses’ rule.
So what does all of this mean for Apple device users?
Michael Sweeting, one of our Senior Threat Analysts and who specializes in Apple devices sums it up nicely:
“End users of non-jailbroken iOS devices are typically unable to load third party applications, and are therefore somewhat protected from malware attacks propagated through app installs. OSX.WireLurker however is a new approach to infecting iOS devices with information stealing malware, by infecting third party application installers for OSX, and in turn infecting the iOS device once connected to the Mac via USB. This type of infection should once again remind Mac and iOS users alike that these devices are not immune to attacks, and even bigger more sophisticated attacks may be on the horizon. Users should continue to exercise caution and prudence, and should avoid downloading Mac software from third party app stores.”
That ‘caution and prudence’ doesn’t only mean updating iOS, avoiding connecting your iPhone or iPad to unknown/untrusted computers, and not jailbreaking your device and sticking to the App Store (all of which are encouraged security tips, by the way). It may also mean safeguarding your Mac with an internet security solution.
Or maybe most importantly, it may mean finally accepting that Apple devices aren’t unhackable machines. But hey, if you already exercise the former precautions, you probably already take Apple security seriously and the last point likely doesn’t apply to you.
Son of a Breach! Can Companies Just Safeguard Their Customers’ Data?
Just when consumers were starting to regain some company trust and safe-shopping stability after last year’s massive Target breach, a string of new large-scale company breaches quickly reminded us consumers just how insecure our personal data can be.
Needless to say, it’s been a rough year for some major companies and an even rougher year for thousands of unlucky customers. Let’s look at three of the major breaches of the last couple of months.
Home Depot
(Source: Krebs On Security)
Early last month, reports started coming in that the home improvement giant was investigating “some unusual activity with regards to its customer data.” Security reporter Brian Krebs immediately called credit card breach, especially since multiple banks came out to say that they were seeing evidence that Home Depot was the likely source of a batch of stolen credit and debit cards that went on sale in the cybercrime black market that morning.
Sure enough, six days later, the company admitted that its payment systems were in fact breached and that the hack was going on for months. They went on to say that while credit card data was exposed, personal pins were not. Reassurance (not really). And while the exact number of affected cards wasn’t known at that time, one thing was for certain: If you used a credit card at one of Home Depot’s U.S or Canadian stores in the past 4-5 months, you needed to consider your credit card stolen and get on the phone with your bank ASAP.
About two weeks later (September 18th), Home Depot announced the number. A whopping 56 million cards were impacted, making the incident the biggest retail card breach…ever (on record, at least). The ‘silver lining’? Home Depot also said that the malware was now contained.
Japan Airlines
(Source: Google Images)
Before the month of September passed (and with Home Depot still fresh on everyone’s minds), another large company from a completely different industry had some bad news to share with its customers…
On September 30th, Japan Airlines (JAL) confirmed that as many as 750,000 JAL Mileage Bank (JMB) frequent flyer club members’ personal info was at risk thanks to a breach. Apparently, hackers were able to get into JAL’s ‘Customer Information Management System’ by installing malware onto computers that had access to the system. The data that was accessed? Everything from names to home addresses to birthdates to JMB member numbers and enrollment dates. The good news is that credit card numbers and passwords did not appear to be exposed.
There have not been any new developments about this breach, but you here is the official statement by JAL from September 29th.
JP Morgan
(Source: Reuters)
October 2014 was only two days young when yet another major company confirmed a data breach. This time, the victim was JP Morgan. Or rather, JP Morgan customers who used Chase.com and JPMorganOnline websites, as well as the Chase and JP Morgan mobile apps.
Last Thursday, the nation’s largest bank revealed that a mid-August cyberattack exposed personal info for 76 million households, as well as 7 million small businesses. More specifically, names, email addresses, phone numbers and addresses were stolen, while JP Morgan went on to say that there was no evidence that account numbers, passwords, Social Security numbers or birthdates were exposed. While the bank found out about the breach of it’s servers in August, it has since been determined that it began as early as June.
Unfortunately, not much else is certain at this time. What we do know is that Russian hackers are suspected (still not confirmed), over 90 over JP Morgan’s servers were affected, and it is believed that nine other financial institutions were also targeted (although we don’t know their identities). The lack of concrete information is scary in it’s own right, but the fact that JP Morgan is staying mum on the matter is even more troubling. According to a Huffington Post report from earlier today, the bank is refusing to say how many people were actually hit by the breach, with spokeswoman Trish Wexler saying that JP Morgan isn’t offering more details beyond what was announced last Thursday. This could mean that the breach, already the largest (against a bank) in history, could potentially be even larger than the reported 76 million households and 7 million small businesses, keeping in mind that ‘households’ is not the same thing as ‘individuals’.
Additionally, Fox Business is reporting that the bank is now bracing for a massive-scale spear-phishing campaign in the wake of the breach. according to their sources. Considering that no bank info was compromised in the original breach (JP Morgan said in a statement that they haven’t “seen unusual fraud activity related to the incident”), this is a plausible next-step. Using the personal info obtained in the ‘first wave’, the attackers can send out legitimate-looking emails to the affected customers that say there is a problem with the user’s account and ask for Social Security numbers, passwords, etc. Alternatively, the emails could ask the customer to click an embedded link to update their account info, but in reality, the customer is taken to a official-looking fake site from which the attackers can nab the important financial information. In either case, the virtual trap is activated at that point.
What to do?
It’s no secret that data breaches are on a steep rise. According to a the Identity Theft Research center, there have been 579 data breaches this year, 27.5% more than there were at this time last year. And that number is only going to continue to increase.
In any of these three breaches, it’s important for customers to take basic security steps to ensure their information is safe, whether that means calling your bank and getting a new credit card issued (in the case of Home Depot), changing your password if you’re a JAL frequent flyer and JMB club member, or changing your log-in information and monitoring your online accounts if you bank with JP Morgan or Chase.
As more and more people choose to bank online (and become more internet-dependent in general), it’s also no secret that employing powerful and always up-to-date internet security on your devices is more crucial than ever before. Company breaches and spear-phishing attacks aren’t going anywhere. Take the necessary steps to keep your personal info protected!
‘Bash’ Shellshocks the Internet – Here’s What You Should Know
Update: Apple has patched the Bash bug. For more info (including links to download the updates on your Mac), check out this TechCrunch report.
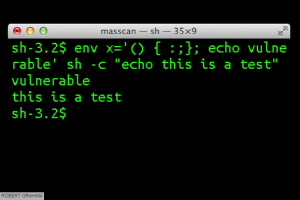
As of last week, there’s a new security bug in the news, and it’s wreaking havoc on the Internet.
(Source: Macworld/Errata Security)
Discovered by Stephane Chazelas, a security researcher for Akamai (who revealed the bad news to the world last Thursday), the ‘Bash bug, or ‘Shellshock’, is a particularly nasty vulnerability affecting the Bourne-Again Shell (thus the Bash acronym) of certain versions of the Unix and Linux operating systems. Yes, that includes derivatives like the Mac OS. In other words, it’s everywhere, and could affect a countless number of devices that connect to the internet.
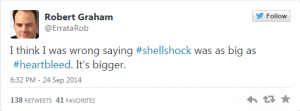
Remember Heartbleed? This is scarier. And potentially a bigger deal, too.
Why? According to Robert Graham of Errata Security:
“Unlike Heartbleed, which only affected a specific version of OpenSSL, this bash bug has been around for a long, long time. That means there are lots of old devices on the network vulnerable to this bug. The number of systems needing to be patched, but which won’t be, is much larger than Heartbleed.”
Oh, and it IS old. How old? Graham said in a different blog post that the bash issue has been around for 20 years.
For the record, the National Vulnerability Database gave Bash a 10/10! Here’s what you should know.
What is it?
As previously mentioned, it’s vulnerability, a bug affecting the Bash shell used in many Unix and Linux operating systems. Think of the Bash shell as the command-line shell. This means that a hacker could take over and issue remote commands to web servers that aren’t patched. As a result, private information could quickly become public information.
Is every device running Linux or Unix vulnerable?
No. According to Rapid7 Global Security Strategist Trey Ford, there are certain requirements that make a server vulnerable. More specifically, servers capable of passing commands over the internet remotely, are susceptible.
What makes it so dangerous?
Bash may not affect as many devices as Heartbleed, but that may be the only consolation. Because (unlike Heartbleed) Bash lets hackers execute commands remotely, the repercussions could be a lot more serious.
Who should be worried? Should you?
While network administrators who manage internet presence for their companies (particularly those running a CGI app written in Bash or using Bash script), should be concerned, the everyday desktop user probably doesn’t have as much to worry about. That is unless you have a bunch of connected ‘Internet-of-things devices’
What about those Internet-of-Things Devices?
This is largely about patching updates, so while the aforementioned everyday desktop user may not be affected by Bash, that doesn’t necessarily mean his or her connected devices aren’t vulnerable. From home automation systems to routers to webcams to refrigerators, there are many Internet-of-things devices that use the Bash script. And most users would probably never think twice about installing software updates on something like a fridge. Now they should.
What’s being done?
Companies like Google and Amazon were quick to react, rushing Thursday to patch this latest vulnerability on their end. And because recent versions of the Mac OS are vulnerable, Apple quickly responded, saying that while most OSX users aren’t at risk, the company was quickly working on patching the flaw. You can read more about that here.
What should you do?
Unfortunately, there’s not much you can do as this is a widespread vulnerability rather than say, a sneaky piece of malware. And because this is the case, you, as a consumer, can’t contain it by yourself. Rather, it’s up to the those maintaining the web servers. But absolutely do pay attention, run updates, and look for notifications from service providers who are vulnerable to Bash. And if a company tells you to take action and change your password because their servers are affected, listen to them and get on that immediately.
What about Webroot Servers?
We took all the necessary precautions and upgraded all of our systems to the patched version. We can verify that none of our services are susceptible. You can find our official statement on this support section of our site.
We’ll be keeping a close watch to see how this story unfolds, but in the meantime, take the necessary steps to ensure you’re as protected as possible and install necessary updates as they become available.
5 million GMail accounts breached, and I was one of them
There is a bit of irony in this blog post, if you will. Over my time at Webroot, I have become a major advocate and vocal evangelist of digital security, from talking about major level breaches to sharing my experiences with dating-website scams. My work has focused around the education of those who will listen and read my work on the value of keeping one’s self safe at home, work, and while traveling. Like many others, I never thought (often quite ignorantly) that my information could get out there in a breach. And if it did, I was sure I would be still protected.
This morning, we found out that there was a breach of over 5 million Gmail accounts, all hosted in a plain text file on Russian hacker forums. Naturally, we wanted to see what the data was like, and there it was, plain as day for everyone to see. We started to look up our various accounts, and out of my whole team, I was the only one to appear. Right in front of me, on a list with 5 million other people, was my information. My heart sank a little, followed by the sort of nervous laugh I get at times all while I played through the major steps I had taken to protect myself prior, and what I needed to go change. Luckily, at the beginning of the year, I did my own security update and implemented two-factor authentication across all my major accounts, changed my standard passwords, and updated my security settings. And while we have covered these tips in the past (along with Tyler Moffitt’s security tips), there is no reason we shouldn’t all go back and just do a quick audit to make sure. In this case, there are two major steps I took to ensure my security online with this breach; changing my passwords and making certain that I have two-factor authentication turned on.
Change your passwords: Every three months is the average for a company for changing of passwords, often not allowing you to repeat for at least 10 passwords. This may be an annoyance, but with breaches like this occurring on a daily basis, it’s a necessary step that you should be following at home as well. It’s no longer simply about someone figuring your password out, but rather the idea that any level of breach can grab your standard password and e-mail address, and attempt it across multiple channels until success is found. Changing your password removes this ability. Need help figuring out a new password you can remember? Take your standard password and move one key left or right for each letter. The keystrokes will be similar and it will help product a difficult password. Remember, characters and numbers should be intermixed to increase the difficulty. Reminding yourself with a calendar note to change all your passwords on the same day every three months. I would also recommend looking into a password manager, such as the one included in Webroot SecureAnywhere™ Internet Security Complete for home users, to help with the difficult passwords you now have to remember.
Enable Two Factor Authentication: I have talked about this before (and shared links), and I cannot stress enough the importance of this level of security. With cell phones being at the ready in almost all aspects of our daily lives, this is one of the most convenient and easy layers to implement. By adding this layer, the service will authenticate any login attempt through an independent channel, allowing you to know if someone is attempting unauthorized access. Below are links to the sites listed above for their steps on enabling this step.
- Gmail: https://www.google.com/landing/2step/
- Amazon: http://aws.amazon.com/iam/details/mfa/
- PayPal: https://www.paypal.com/us/cgi-bin?cmd=xpt/Marketing_CommandDriven/securitycenter/PayPalSecurityKey-outside&bn_r=o
- Facebook: https://www.facebook.com/note.php?note_id=10150172618258920
- Twitter: https://blog.twitter.com/2013/getting-started-with-login-verification
While we are still unsure how the hacker was able to get all this information, it’s clear as day that it is out there, and because of that, vigilance is key. Just as you wouldn’t leave your credit cards laying around, you shouldn’t risk your passwords being out there either. Data is valuable, and the more private or financially focused it is, the more we need to take it seriously. So take these simple steps, get another layer of security established, and make it a habit to change passwords so you don’t become another name on the list as I did. In the mean time, you can check and see if your e-mail is apart of the breach by following this link: https://isleaked.com/en.php
Other helpful links:
- Google Security: https://www.google.com/settings/security
- Facebook Security: https://www.facebook.com/help/securitytips
- Twitter Security: https://support.twitter.com/articles/76036-safe-tweeting-the-basics
- Secure Password Generator: http://passwordsgenerator.net/
- Google Chrome Security Settings: https://support.google.com/chrome/answer/114836?hl=en
- Firefox Security Settings: https://support.mozilla.org/en-US/products/firefox/privacy-and-security
- Internet Explorer Security Settings: http://windows.microsoft.com/en-us/windows/change-internet-explorer-security-settings#1TC=windows-7
- Microsoft Outlook Two-step authentication: http://windows.microsoft.com/en-us/windows/two-step-verification-faq
- Google Two-Step authentication: https://support.google.com/a/answer/175197?hl=en
Apple’s Sept 9 Event: New (and larger) iPhones and (gasp), a Watch!
Well, September 9th is here, and the launch of Destiny, one of the most (if not the most) anticipated video games ever, isn’t the only major piece of news coming out of the tech world today.
You may have heard that one Cupertino fruit-logo’d tech company had an event today. And now the details of Apple’s next big(ger) things are official. Initial takeaway? They’re pretty in-line with the the rumors that have been swirling around for months now.
In other words, people got a lot of what they were expecting. Is that a good or bad thing? Depends on what camp you’re in. Probably.
Similar Phones, New Sizes
If you’re an Apple fan who’s only gripe was the small-by-today’s-smartphone-standards screen, your wish is (finally) Apple’s command. The company announced two new phones, each with a never before used (by Apple) size: the new iPhone 6 has a 4.7 inch screen while the new iPhone 6 Plus sports a 5.5 inch one. Yep, the iPhone will finally be competing in the phablet category.
(Source: ARS Technica)
The new devices are also thinner than the current 7.6 mm enclosure of the 5s, with the iPhone 6 measuring 6.9 mm and the iPhone 6 Plus coming in just slightly chubbier at 7.1 mm. To accompany these ‘gains’, Apple also introduces a new ‘Horizontal Mode’, which will help retain comfortable one-handed use and make everything within reach.
The glass now curves around the edges of the phones, but the screen isn’t the sapphire one many people expected, but rather incorporates “a slightly different design element”, according to CNET’s report. The phones’ power/lock button make a move from the top edge to the right spine.
The colors remain unchanged. You will be able to get the new devices in gold, silver, or space gray.
(Source: PC Mag)
What about the display? The regular 6 gets a 1334×750 resolution with 326 PPI (Pixels Per Inch) while the 6 Plus gets a slightly crisper 1920×1080 resolution with 401 PPI. Both iPhones sport Apple’s familiar ‘Retina Display’ (although it’s now being called ‘Retina HD’). While these numbers improve on the 1136×640 (326 PPI) display of the 5s, they still lag behind many of today’s higher-end Android devices, a few of which (LG G3 and the newly-announced Galaxy Note 4 and Note Edge) pack 2560×1440 displays.
But pixels don’t always tell the whole story and it’s very difficult to tell the difference between 1080p and 1440p on such (relatively) small devices. That, and battery life typically suffers from a higher resolution. Speaking of…
The Internals
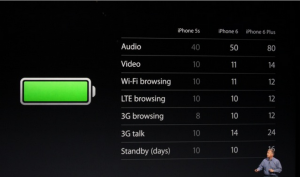
When it comes to battery life, Apple is claiming an improvement in battery life in both phones over the current 5s (see chart below)
(Source: ARS Technica)
The devices’ internal hardware gets a boost as well. The new iPhones are powered by Apple’s new A8 processor, which Apple says has 50% faster graphics and a 25% faster CPU. The transistor count has also been bumped up to 2 billion from the A7’s 1 billion. This should all lead to better efficiency and performance.
There’s also the M8 co-processor, which improves on the 5s’ co-processor and will assist the health-conscious iPhone users keep track of their activity and take better advantage of the iPhone’s fitness apps. It’ll also be handing the data coming from the new barometer sensor.
The phones also get upgraded LTE connectivity, bumping speeds up to 150Mbps. Wi-Fi speeds should also clock in at about three times faster than those of the 5s, thanks to Wi-Fi 802.11 support. VoLTE (Voice over LTE) and Wi-Fi calling are also now supported.
Camera
Updated rather than upgraded (if pixel count is your measurement), the camera in the iPhone 6 and iPhone 6 Plus retains its 8MP, but gets a new sensor with ‘Focus Pixels’ technology, which Apple claims uses DSLR-style phase detection autofocus, helping the new devices autofocus lock up to 2x faster than previous iPhones. Users will be able to record 30 and 60 FPS videos in 1080p and capture slow motion videos at 120 or 240 FPS, an improvement.
As far as image stabilization goes, the iPhone 6 gets digital stabilization, but you’ll have to purchase the bigger and more expensive (more on that later) 6 Plus if you want optical image stabilization.
If selfies are your thing, Apple also didn’t forget about its Face-Time camera (otherwise known as the front-facing camera), which receives a larger f/2.2 aperture plus a new sensor for better lighting and sharper image quality. Video capture remains at 720p and there’s also now a burst mode.
NFC/Apple Pay
(Source: Macworld)
Apple has resisted the NFC (Near Field Communication) push for years, but that no longer the case with the new iPhones. With the 6 and the 6 Plus, Apple not only added the protocol, but have also built their new Apple Pay payments system entirely for this cause. It works with the Passport app (as well as without it) and will finally allow users to use their new iPhone to purchase things. For more on Apple Pay, check out this Macworld article.
iOS 8
Apple announced that the new operating system will be available Wednesday, September 17th. For a detailed breakdown of the new features of iOS 8, check out this CNET article.
Pricing and Availability
The new iPhone 6 and 6 Plus will launch in eight countries on September 19th. Pre-orders begin on September 12th.
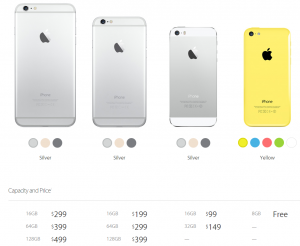
So far, Apple has only released US pricing, but, as you might expect, the new iPhones ain’t cheap. The iPhone 6 starts at $199 for the 16GB version. $299 will get you 64GB, and if you want the max 128 GB of storage, you’ll need to dish out $399. Tack on $100 across the board (for the same amount of storage) and voila, that’s how much the iPhone 6 plus will cost you. Yep, that means on-contract pricing for a 128 GB iPhone 6 Plus is a whopping $499!
In the US, the new iPhones will be available on AT&T, Verizon, T-mobile, Sprint, and US Cellular to start.
The other seven countries that get the September 19 launch are UK, Australia, Canada, France, Germany, Hong Kong, Japan, Puerto Rico, and Singapore.
This also means that the iPhone 5C’s price will drop to ‘Free’ and the iPhone 5S’s price goes down to $99 (for the 16 GB version).
(Source: Apple.com)
‘One More Thing’: The Apple Watch
Apple didn’t end with the iPhone 6 and 6 Plus reveal, however. It wouldn’t be an Apple event if they did, would it? As many people expected, they introduced a new wearable device, called the Apple Watch (interestingly not iWatch like most predicted).
(Source: CNET)
The Verge has a very visual ‘hands-on’ write up and you can read it in its entirety here. Nevertheless, here’s some basic info on Apple’s long-rumored entry into the wearables market:
- Will be available ‘Early 2015’ starting at $349
- Will come in three collections – all different versions (with different finishes) of the same watch. The Apple Watch Edition will be finished in 18K gold.
- Touch-screen (flexible Retina) display, digital crown, infrared LEDs, and photo diodes
- Runs on an S1 Processor
- Equipped with gyro accelerometer
- Has NFC
- You need an iPhone 5 or better to use it
Security
Many people forget that iPhones are not malware-proof. I won’t dive deep into this, but it’s important to keep your new devices protected, whether you’re an iPhone or Android user. We offer protection for both.
Concluding Thoughts
It will be interesting to see how consumers will react to the new iPhones. Many Android vs. Apple battles are already raging on in pretty much every comment section of every story written up on the iPhone 6 and 6 Plus.
The thing is, most Android and Apple users are already dedicated to their respective camps and I don’t think these new iPhones have enough revolutionary features that will lure many Android users away from their Google-powered machines, most of which already have the screen sizes Apple is finally embracing.
But because the 4.7 and 5.5 inch screens are a first for Apple, the real question comes down to the Apple fans themselves. Will the new screen sizes be the must-have addition many previous iPhone users were wishing for or will it alienate the fan base that loved Apple for offering a pocket-friendly premium smartphone?
For now, all we can do is wait and see.
Cryptographic Locker
It seems as though every few weeks we see a new encrypting ransomware variant. It’s not surprising either since the business model of ransoming files for money is tried and true. Whether it’s important work documents, treasured wedding pictures, or complete discographies of your favorite artists, everyone has valuable data they don’t want taken.
This is the last thing anyone wants to see.
This variant does bring some new features to the scene, but also fails at other lessons learnt by previous variants. Starting with the new features this variant will now just “delete” the files after encrypting them (it just hides them from you). This doesn’t add any more intangibility since they are encrypted with AES-128 anyway, but it does add a greater sense of loss and panic since all of your common data directories will appear to have been cleaned out. Another new feature is the constant raise in price every 24 hours. While price bumping was used on previous variants, this one doesn’t have a limit and will increase by .2 bitcoins (~$97) every 24 hours until you crack or make peace with this loss.
Where this variant falls short on overall volatility is in the failure to delete the VSS (Volume Shadow Service) so using tools like Shadow Explorer will work to retrieve your files and circumvent paying the ransom. As I’ve said in previous blogs I do expect issues like this to be fixed once this malware is adopted by more botnets for widespread distribution.
Webroot will catch this specific variant in real time before any encryption takes place. We’re always on the look out for more, but just in case of new zero day variants – remember that with encrypting ransomware the best protection is going to be a good backup solution. This can be either through the cloud or offline external storage. Keeping it up to date is key so as not to lose productivity. Webroot has backup features built into our product that allow you to have directories constantly synced to the cloud. If you were to get infected by a zero day variant of encrypting ransomware you can just restore your files back as we save a snapshot history for each of your files up to ten previous copies.
The Weekend of Nude Celebrity Selfies, iCloud, and How to Protect Your Personal Info
What do celebrities (mostly young and female), 4chan, hackers, Bitcoin, and iCloud have in common?
They’re all ingredients of a scandalous Labor Day Weekend, one that was filled with celebrity ‘skin’, outrage, confirmation (and denial)…and now an FBI investigation into the crazy incident that has everyone talking.
But is it the ultimate internet scandal or a sobering reality of the importance of safeguarding your content to reduce the risk of it being stolen? Both.
Before we go into that, however, in a nutshell (and in case you don’t know by now), here’s what happened:
On Sunday, users of the often-controversial message-board 4chan, saw a large trove of nude celebrity pics posted on the /b/ (also known as the ‘random’) thread. The extensive list of celebrity ‘victims’ included Jennifer Lawrence, Kate Upton, Mary Elizabeth Winstead, Kirsten Dunst, Ariana Grande, Kim Kardashian, Victoria Justice and many others. Afterwards, the photos quickly spread to Reddit.
Then the reactions started to come in.
While Jennifer Lawrence didn’t respond herself, here was her spokesman’s reaction (which confirmed the pictures’ legitimacy): “This is a flagrant violation of privacy. The authorities have been contacted and will prosecute anyone who posts the stolen photos of Jennifer Lawrence.”
(Source: Washington Post)
Not surprisingly, many of the celebrities were quick to respond themselves, taking to Twitter, some denying the legitimacy of the photos while others admitting that they were real. Below are some of the celebrity reactions on Twitter.
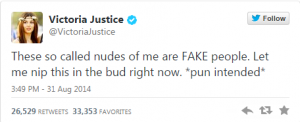
Actress and singer Victoria Justice took the humorous route as she called ‘her’ pics ‘fake’:
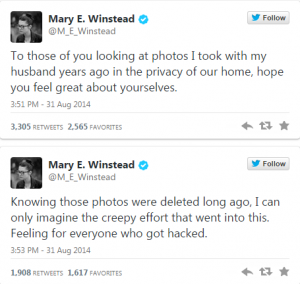
On the other end of the spectrum, actress Mary Elizabeth Winstead took a very serious tone as she confirmed that her stolen photos were real:
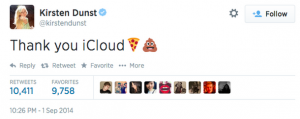
And here was Kirsten Dunst’s reaction:
But why is Dunst ‘thanking’ iCloud? And who was behind this ‘leak’? Million-dollar questions. Let’s start with the ‘who’.
It’s still uncertain exactly who the perpetrator (or perpetrators) are. According to reports, 4chan apparently hosted a shady, unorganized ‘black market’ for celebrity photos where users would sell, buy and/or swap these photos and often boast of their ‘collection’. And while some Redditors have put the blame on Bryan Hamade, a 27-year-old man from Georgia, he is ‘vehemently denying’ the claims (he did an interview with BuzzFeed yesterday morning). You can read it here (warning: could have some NSFW content).
Now back to the iCloud bit…
Some 4chan hackers claimed that they exploited a previously-unknown flaw in Apple’s iCloud, more specifically the photos, contacts, and music syncing feature.
After ‘more than 40 hours’ of investigation, however, Apple is claiming that its systems aren’t the ones to blame for the breach, saying that this was a targeted attack on the celebrities rather than a widespread breach. Here is part of their statement: “None of the cases we have investigated has resulted from any breach in any of Apple’s systems including iCloud or Find My iPhone.” For more on Apple’s take, you can read the CNET report here.
Also, as mentioned before, the FBI is now involved. The following is a comment from FBI spokesperson Laura Eimeiller regarding the matter: “[The FBI is] aware of the allegations concerning computer intrusions and the unlawful release of material involving high profile individuals, and is addressing the matter. Any further comment would be inappropriate at this time.”
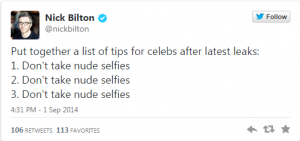
As this story continues to develop, many of you are probably wondering (and worrying) about the security of your own, personal (and possibly sensitive) information. Some people are arguing that the easiest way to avoid these scandals would be to not take nude selfies in the first place, (NYT Colunmnist Nick Bilton and comedian/actor Ricky Gervais both made similar jokes on Twitter about it – see below), while others are calling that ‘gross advice’ (read Amanda Hess’ Slate article here).
Gervais ended up deleting his Tweet, but here’s what he said originally: “Celebrities, make it harder for hackers to get nude pics of you from your computer by not putting nude pics of yourself on your computer.”
Here was Bilton’s Tweet (he later apologized):
A major takeaway, regardless of your opinion on this matter (or whether you snap revealing pics of yourself on your iPhone), is that many people take internet and mobile security for granted and don’t do enough to protect their personal information.
Here are some general tips safeguarding tips that will help reduce the risk of losing or unwillingly exposing your personal info:
- Malware often targets user log-in details. Use security software to protect yourself, particularly one with a secure web browser. We here at Webroot have found that over 50% of internet traffic stems from mobile devices, and web browsing is the most likely source of attacks.
- Have a different secure password for each place you store important data – pictures, documents, etc. is critical – and change the password often (at least once every few months). This will keep you a step ahead of cyber criminals.
- Watch out for phishing attacks! Never click on a link in an email except from a trusted party. Never enter your login information just because a company sends you an email with a link to a page that looks like the real company page – it could be a fake phishing page.
- Use passwords that are difficult for automated computer programs to crack. Use phrases or even whole short sentences like CowboysNeverbeat49ers!! Change it often.
- Pet names, birth dates, and simple number combinations are not secure passwords, nor a replacement for real-time protection software and basic security practices.
And one tip for Apple iCloud users – Apple is saying that its internal systems aren’t to blame and they’re probably telling the truth. But the fact that iCloud wasn’t breached isn’t an excuse to use a weak password or have a simple (or honest) answer for your security question. Remember, the easier it is for you to log in to an account, the easier it else for somebody else to do so, too.
Oh, an one last thing. Just because you delete a photo from your iPhone doesn’t mean it’s automatically deleted from iCloud (or wherever else you may have stored it). Stay secure!
A Primer on BitCoin
Editors Note: One day, we found ourselves discussing the security of bitcoin, only to realize that many readers may not truly understand the digital currency. Luckily, a team member’s father, Eoin Meehan, is well versed in the subject and has submitted a guest blog to help everyone understand this popular form of cryptocurrency.

Bitcoin is a cryptocurrency, reportedly designed by Satoshi Nakamoto in 2008. To fully understand how it works we must look at how “ordinary” currencies work.
To quote Sheldon Cooper “It was a warm, summer’s evening in ancient Greece …”
Well, no, we don’t need to go back THAT far.
Currencies evolved as people used bits of precious metals as tokens to exchange for goods and services, rather than using OTHER goods and services (which is barter). Gold and silver served this purpose well because they were
- Rare metals and durable
- Elements, so it was easy to see if they had been tampered with and
- Acceptable by everyone who traded with them – a common medium of exchange
Eventually someone realised that physically moving large amounts of precious metals was both cumbersome and risky, and came up with the idea of a paper token denoting ownership of a piece of gold that was held somewhere secure. The paper token said that whoever held this piece of paper could go to where the gold was stored and demand it to be handed over (which is why notes used to have “I promise to pay the bearer on demand the sum of x pounds” – its x pounds worth of gold).
Everyone accepted the concept of the paper representing the gold and so it took on the value of the gold itself. This became known as the “Gold Standard”
Then someone realised that because everyone was happy with the pieces of paper representing “value” there was really no need to keep tons of gold in a secure location, in case somebody actually turned up and asked for their pound of gold. And that’s what we have today with currencies such as the Euro.
So today, a currency has to have three attributes to be a currency:
- The tokens are rare or controlled.
- The tokens representing that value are very difficult to generate and replicate
- A value accepted and agreed by everyone who uses it – a common medium of exchange
Bitcoins are tokens that can be exchanged between parties in a transaction, just like physical notes. There are no physical bitcoins, so the transfer happens just like transferring money between bank accounts.
These “bank accounts” do not exist in any institution, but as “wallets” on electronic devices. These wallets are encrypted files on a PC, laptop, tablet or smartphone, managed by a Bitcoin-compliant application. The Bitcoin standard uses public/private key pairs to authorise and authenticate transfers between wallets, and each wallet has its own private/public key pair.
The transfer happens across a peer-to-peer network similar to Tor or Bittorrent.
But what happens if Alice sends 5 Bitcoins (BTCs) to Bob, and ALSO tries to send the SAME 5 BTCs to Carol?
To stop this happening there is a data construct called the block-chain which is held on all nodes participating in the Bitcoin network. The blockchain is an encrypted list of all transactions that have been “approved” in the Bitcoin universe, and acts as a shared ledger. Once Alice sends her 5 BTCs to Bob, those 5 BTCs are logged in the blockchain as a transfer between Alice’s wallet and Bob’s wallet. If Alice tries to send the SAME BTC’s again, the network will reject the transaction, as the BTCs are already “accounted for”
So how are the transactions added and “approved” to the blockchain? This is done by special nodes called “miners”. Miners have two functions – to authorise transactions and to generate new Bitcoins (hence the name).
When Alice sends Bob the 5 BTCs, the transaction is broadcast the Bitcoin network, and the transaction is marked pending (not complete). Miners listen for these broadcasts and begin working on adding the transaction to the blockchain.
The process of adding the transaction to the blockchain is computationally intensive. The miner has to apply a hash-function to the block-chain + the new block to generate a hash. Normally for hashing purposes we can just stop there. One computationally intensive process to create a number. But Bitcoin applies a ceiling such that the hash created must be equal-to or less-than the ceiling. This means the miner must recalculate the hash many times until it returns an acceptable value. If two miners return values, then the lower one “wins”. Once the hash is created and accepted, working backwards to see if this hash is valid for this block is trivial. So verification is easy.
This ceiling value is also how the network “self-regulates”. The more miners there are connected, the lower that ceiling value goes (the harder the task).
Once a miner successfully calculates the hash value, the block-chain is updated and the wallet applications notified. (Because of the intensity of the calculations, there is about 10 minutes between the transaction and its confirmation).
Now we come to the second function of the miner. As a reward for calculating the hash, the miner is allowed create a certain number of new bitcoins, and these are recorded as part of the verified transaction. They are then transferred to the miner’s appropriate wallet and “come into circulation”.
The number of bitcoins a miner is allowed create is a function of the total number of bitcoins that will ever be allowed. Currently its 25 BTCs. For every 210,000 blocks added to the blockchain, this number is halved. So Bitcoins become harder to generate the more that are in circulation. There is an arbitrary limit in the protocol that there will only ever be 21,000,000 bitcoins.
So one question you might ask is – what happens when all bitcoins are mined? What incentive is there for miners to keep, eh, mining? The protocol considers this. In each block record in the block-chain, a miner can charge a fee or commission for calculating the hash and verifying the transaction. So miners will still be mining bitcoins for their owners except they will be paid by other members to verify transactions.
Once Bitcoin is accepted a medium of exchange each BC has a value. This value can then be “matched” with real-world currencies just like a foreign-exchange transaction. There are a number of electronic exchanges set up which will perform this forex transaction … for a fee of course! The most notable one is probably is MtGox.
Sony’s PSN Network Haymaker’d by DDoS Attack; Exec’s Plane Grounded Over Bomb Threat
Sony had a rough weekend. And not just Sony; last weekend wasn’t the best time to be a gamer. Here’s the skinny…
Early yesterday morning, Sony’s PlayStation Network (PSN for short) was hit with a massive Distributed Denial of Service (DDoS) attack, causing it to crash temporarily and hamper online play for many PlayStation gamers.
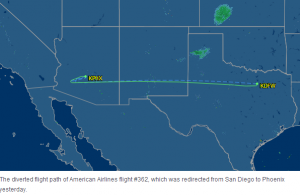
Sony Online Entertainment President John Smedley quickly took to Twitter to let users know about the attack before tweeting that he’d be offline for three hours as he flew back to San Diego from Dallas on AA Flight #362. Well, not long after the plane took off, someone tweeted to American Airlines that “it was receiving reports that [Sony Online Entertainment CEO John Smedley]’s plane #362 from DFW to SAN has explosives on-board, please look into this.” That, plus a handful of references to the 9/11 attacks.
The plane was quickly diverted to Phoenix, where it would be checked for explosives (thankfully, there were none to be found as far as anyone knows).
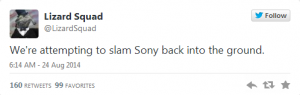
Was the DDoS attack connected to the bomb scare? At first, it sounded like it. The tie? ‘Lizard Squad’.
Who? Let’s start at the beginning, Aka, last Saturday.
According to an ARS Technica report:
“It all started Saturday, when a group going by the handle “Lizard Squad” tweeted links to a number of prominent Twitch streamers, directing followers to target DDoS attacks at servers for Blizzard and League of Legends maker Riot Games. The group’s sophomoric MO: demand that the streamers write “LIZARD SQUAD” on their forehead in marker to get their games back online.”
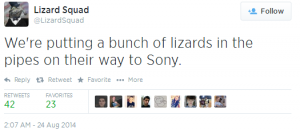
But what’s the tie to Sony’s PSN going down? @LizardSquad started taking aim at Sony early Sunday morning, coinciding with the outage, and posting the following:
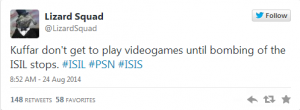
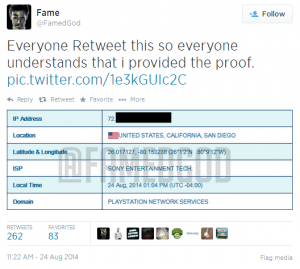
But now, Lizard Squad’s responsibility for the initial PSN attacks is in question. According to numerous reports, a hacker going by the handle @FamedGod is taking credit for the attack. He’s tweeted ‘proof’ (see below) and posted a on YouTube (link below).
PSN Vulnerability (YouTube Video)
While the origin of the attack remains a mystery (we’ll be keeping eye on the story as new details emerge), it’s now clear that Sony wasn’t the only target of the DDoS attacks. As mentioned in the aforementioned ARS Technica piece, Blizzard (more specifically its Battle.net game services) and Riot Games servers were affected. Xbox Live and Grinding Gear’s ‘Path of Exile’ were also reportedly hit.
Now what?
As far as the DDoS attacks are concerned, Blizzard tweeted 19 hours ago, saying that “services appear to be stabilizing”… while PSN and Xbox Live seem to be back to their normal, pre-DDoS states.
What about the bomb scare? According to USA Today, an American Airlines spokesperson says the FBI is investigating the issue.
ZeroLocker
Recently in the news we saw FireEye and Fox-IT provide the ability to decrypt files encrypted by older crpytolocker variants. They used the command and control servers seized by the FBI during operation Tovar. Since they have access to those RSA keys they essentially have the password required for every single file encrypted by a Cryptolocker variant that used Evgeniy Bogachev’s botnet. That is a major portion of the traditional red GUI cryptolocker that became famous. Any previous victims from these variants that still have encrypted files left on their machine should be able to decrypt them with ease. All they have to do is upload a single encrypted file to this webpage and their server will email you your RSA key. Then you can just download their tool (dubbed “DeCryptolocker”) and input the key and it will decrypt all files that are still encrypted. Sadly, anyone that was hit with different variants of encrypting ransomware are still out of luck.
However, since the emergence of their tool to decrypt files for free, there has been a new encrypting ransomware going around that aims at scamming you into thinking this is a similar helpful tool – except that it demands something all scams do….payment.
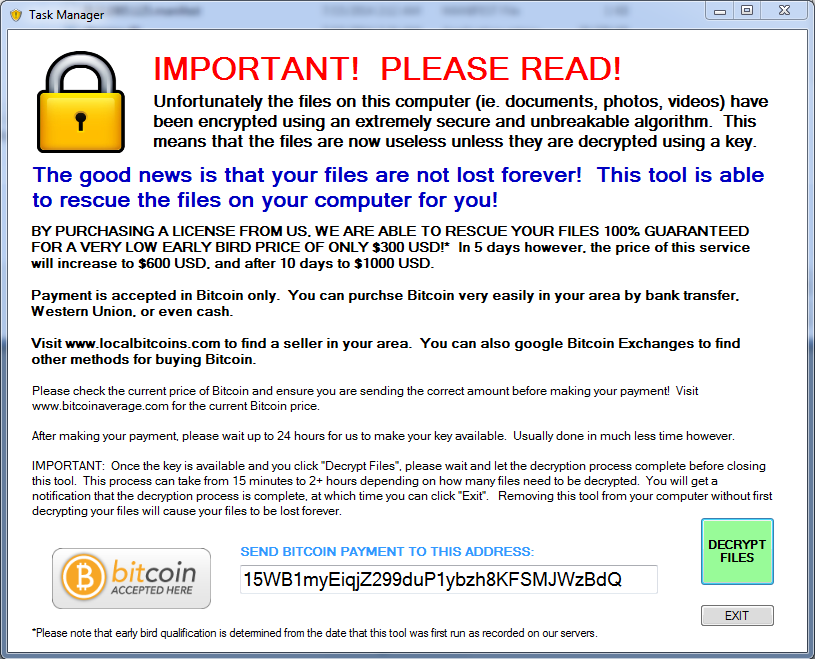
Presenting ZeroLocker
At least they have a 100% guarantee…
This newest edition to the ever popular business model that is encrypting ransomware doesn’t really have many improvements over the others we’ve already seen. Using Bitcoin for payment is standard now. This variant doesn’t show the GUI untill all encryption is completed and the computer is suddenly restarted. Upon restart this window is presented and threatens that you will lose all your files if you close or remove it. The payment structure is right where industry average is – PAINFUL. This specific variant we analyzed does not delete the VSS (Volume Shadow Service) and you can get all your files back by using programs like Shadow Explorer. Once again I expect issues like this to be fixed once this malware is adopted by more botnets for widespread distribution.
Webroot will catch this specific variant in real time before any encryption takes place. We’re always on the look out for more, but just in case of new zero day variants – remember that with encrypting ransomware the best protection is going to be a good backup solution. This can be either through the cloud or offline external storage. Keeping it up to date is key so as not to lose productivity. Webroot has backup features built into our product that allow you to have directories constantly synced to the cloud. If you were to get infected by a zero day variant of encrypting ransomware you can just restore your files back as we save a snapshot history for each of your files up to ten previous copies.
8 Tips to Stay Safe Online
Yesterday, the New York Times published an exclusive story on what many are stating to be the largest series of hacks ever, all revealed by Hold Security in their latest report. With a report of over 1.2 billion unique username-password combinations and over 500 million e-mail addressed amassed by a Russian hacker group dubbed CyberVol (vol is Russian for thief). While the reactions among the security industry are mixed, with some researchers raising a few questions of the masterwork behind the hack, the story does bring to the public’s attention the necessity of strong, personal, online security policies for all aspects of the connected life.
As our researchers have shown in the past, gathering a collection of username and passwords can be easier than many think, with many scraping programs being sold on the deep-web market to the highest bidders. And while some companies, including Hold Security, are offering paid solutions to help detect and monitor if their accounts have been breached, this does not change the fact that the first layer of security begins at the user.
8 tips to help you stay safe and secure on the internet
- Use two-factor authentication whenever possible. Two-factor authentication adds another layer of security when logging into a website, be it e-mail, banking, or other websites. Some websites, such as Google, will text you a code when you login to verify your identity, while others have small devices that you can carry around to generate the code. Authenticator apps are also available on all major smartphone platforms. Other types of two-factor authentication do exist as well, so look in the settings of your banking, shopping, and e-mail hosts for the option.
- Signup for login notifications. This security layer is often used in place of two-factor authentication, including by websites such as Facebook. If your account is accessed from an unfamiliar location, a notification is sent via e-mail, app, or text-message to the account holder. This is a great layer of security that offers you on-the-go protection. This feature, if offered, can usually be found in the security settings of the website, such as banking and social media, you are accessing.
- Use a secure password. We have all signed up for some website with a basic password, thinking there is no way that someone would want to hack our account. But that may not be the case. Setting an easy password on one website often leads to that password being used across many websites. The easier you make it for a thief to brute-force access your account, the more likely you are to have your other accounts hacked. By establishing a mixture of characters, numbers, and letters into a password, recommended to be 10 characters or more, you add a high level of difficulty for any brute-force password theft. Password managers like the one included in our Internet Security Plus and Complete antivirus programs can help make managing this easier.
- Change your passwords regularly. There is a reason your office requires regular password changes for your e-mail. Even if your password is compromised, by changing it regularly across all your accounts, you remove the chance of your account being accessed. A pro-tip would be to set a reminder for every 90 days on your calendar with a link to all your accounts settings pages. It makes it easiest to click through and make the changes regularly.
- Only access your accounts from secure locations. It might only be 30 seconds of access to your bank account on that free WiFi at the coffee shop, but if the network has been compromised, that is more than enough time to collect all the data needed for a thief. While the convenience factor is there, if you must access the accounts, you might want to look into a VPN (Virtual Private Network) to ensure an encrypted connection to your home or work network.
- HTTPS access. In most browsers and information heavy websites, there is a way to force a HTTPS connection when available. This connection adds another level of encrypted security when logging in, making it even more difficult for data thieves to gather your information when logging in. To check if you are on a HTTPS connection, look for a padlock in the URL bar in the browser or check the URL itself for it to begin with HTTPS.
- Increase junk filtering and avoid clicking through on e-mails. You just received an e-mail letting you know that you have a new deposit pending and need to login and verify. Many phishing schemes start with something looking very innocent and official, but lead unassuming users to websites designed to collect the information direct from you. If you receive an e-mail from one of the account-holding websites, open a new tab and go direct to the website instead of clicking the links provided. It adds only a few seconds to the access, but keeps you out of any legit-looking phishing websites. Most legitimate services will never ask you for your login credentials, so make sure to avoid giving out this information. By increasing your level of junk filtering with your e-mail client as well, many of these e-mails will be caught before making it to your inbox.
- Use an up-to-date security program. Ensure you have the most up-to-date version and have the correct security settings enabled. Security AV programs are designed to keep the malicious files such as keyloggers and data-miners off your computer and the user protected. This direct layer of security ensures your devices, from phones to tablets to computers, are all protected when you are downloading and accessing files. Note that some programs, such as Webroot SecureAnywhere, are always up-to-date and require no further action from the user.
While the threats to online accounts are out there, the tips to staying safe can help you stay protected and utilize features often already available by the companies and their websites, and most without costing you additional money. These internet safety tips should help ensure your security online while still providing the convenience online access offers.
Helpful links:
- Google Security: https://www.google.com/settings/security
- Facebook Security: https://www.facebook.com/help/securitytips
- Twitter Security: https://support.twitter.com/articles/76036-safe-tweeting-the-basics
- Secure Password Generator: http://passwordsgenerator.net/
- Google Chrome Security Settings: https://support.google.com/chrome/answer/114836?hl=en
- Firefox Security Settings: https://support.mozilla.org/en-US/products/firefox/privacy-and-security
- Internet Explorer Security Settings: http://windows.microsoft.com/en-us/windows/change-internet-explorer-security-settings#1TC=windows-7
- Microsoft Outlook Two-step authentication: http://windows.microsoft.com/en-us/windows/two-step-verification-faq
- Google Two-Step authentication: https://support.google.com/a/answer/175197?hl=en