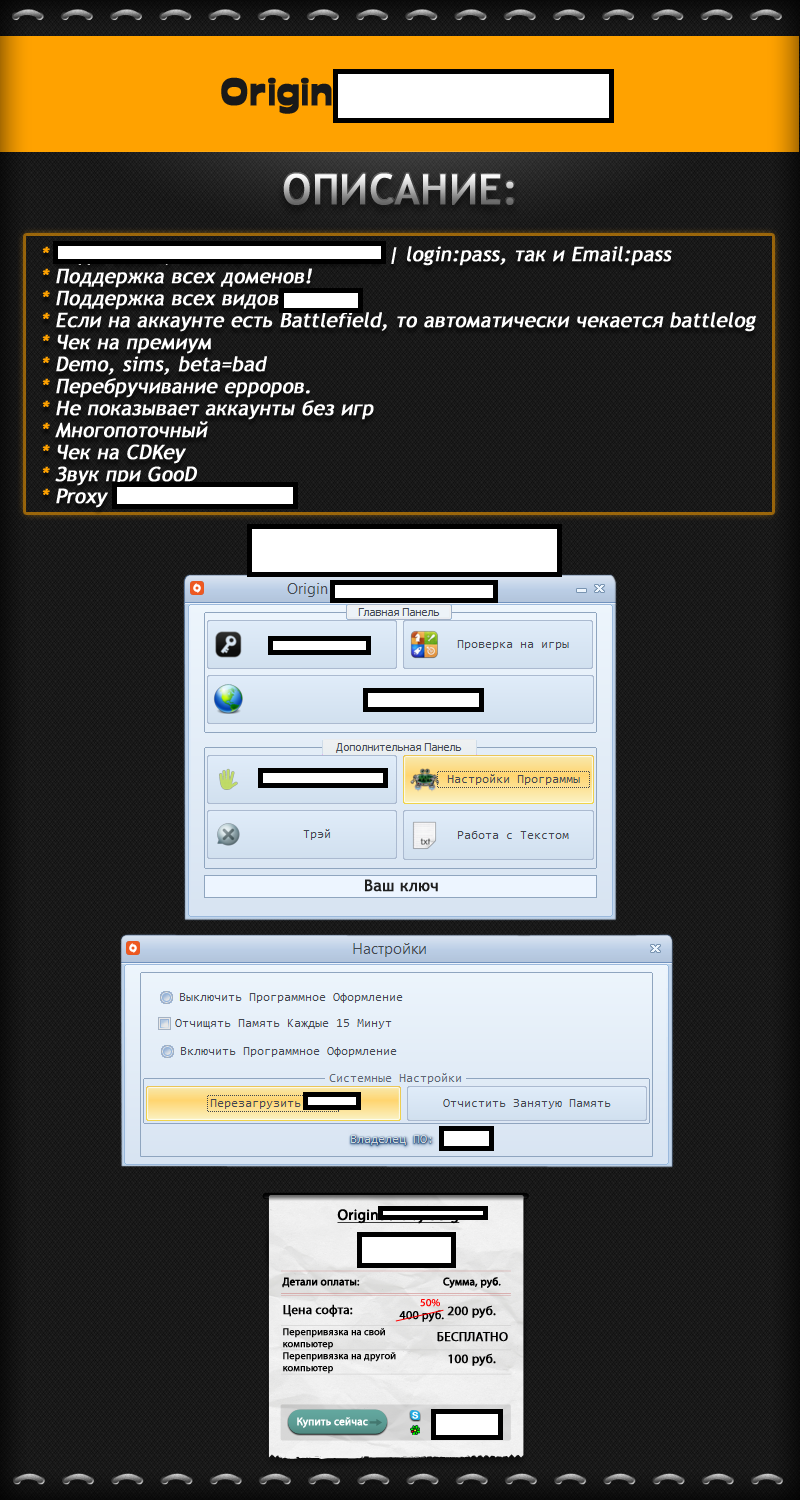
In need of a good reason to immediately improve the strength of your Origin password, in case you don’t want to lose access to your inventory of games, as well as your gaming reputation? We’re about to give you a pretty good one. A newly released proxy-supporting Origin brute-forcing tool is not just efficiency verifying an end user’s understanding of basic security practices, but also, has built-in option for parsing an affected user’s inventory of games, as well as related gaming information. Why would a cybercriminal want to gain access to someone’s gaming account in the first place, besides the most logical reason of gaining access to their gaming inventory? Simple. To set up the foundations for a successful business model relying on standardized E-shops for selling access to compromised gaming/accounting data.
Sample screenshot of the actual advertisement:
The software has built-in support for proxies (malware-infected hosts) syndication, as well as the ability to obtain the CD key for a particular game it has detected as part of the affected user’s inventory, allowing the cybercriminal operating it to easily build up inventories of fraudulently obtained gaming assets to be later on sold to potential buyers. The tools is just the tip of the iceberg in the ever-green market segment for brute forcing tools and services. It’s such tools that empower novice cybercriminals with the necessary capabilities to launch managed email hacking services, or target a specific set of Web sites, running, for instance, WordPress or Joomla, in combination with the ubiquitous in 2013, option to solve CAPTCHAs in an API-friendly, cost-effective manner.
Gamers are advised to go through EA’s recommended account security settings, as well as to active Steam Guard.