Thanks to the commercial and public availability of DIY (do-it-yourself) modular malware/botnet generating tools, the diverse market segment for Web malware exploitating kits, as well as traffic acquiring/distributing cybercrime-friendly traffic exchanges, cybercriminals continue populating the cybercrime ecosystem with newly launched services offering API-enabled access to Socks4/Socks5 compromised/hacked hosts. Largely relying on the ubiquitous affiliate network revenue sharing/risk-forwarding scheme, vendors of these services, as well as products with built-in Socks4/Socks5 enabled features, continue acquiring new customers and gaining market share to further capitalize on their maliciously obtained assets.
We’ve recently spotted a newly launched affiliate network for a long-run — since 2004 — compromised/hacked hosts as a service. Let’s profile the service, discuss its key differentiation factors, and take a peek inside its Web based interface.
More details:
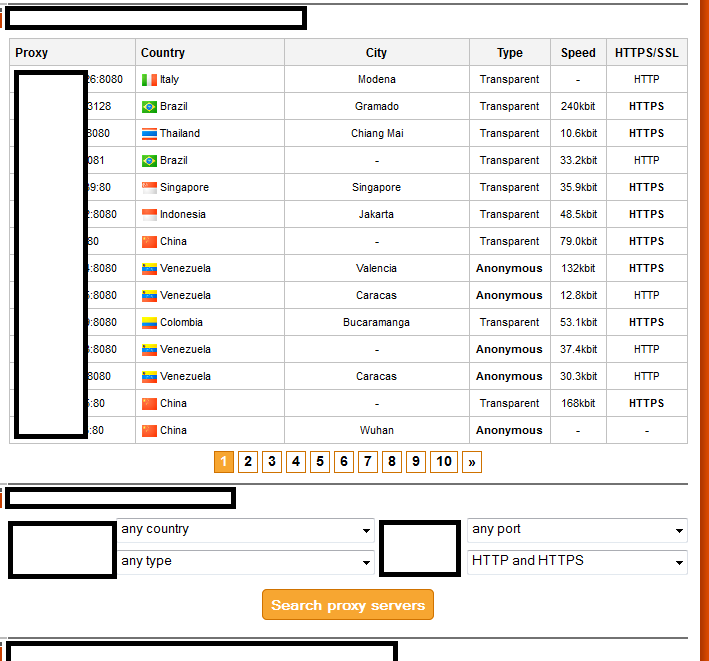
Sample screenshot of the Socks4/Socks5 cybercrime-friendly service:
Supplying fellow cybercriminals with access to compromised/hacked hosts with clean IP reputations empowers them to further commit fraudulent/malicious activities while risk-forwarding the responsibility for their actions to the hundreds of thousands of gullible and socially engineered users across the globe. The service currently has an inventory of 13,798 Socks4/Socks5 enabled hosts and is capable of supplying over 10,000 new hosts on a daily basis. The service’s vendor is ‘naturally’ implying that the hosts can be directly utilized for a variety of fraudulent and malicious TTPs (tactics, techniques and procedures). Let’s take a peek at the Web based interface for the affiliate network.
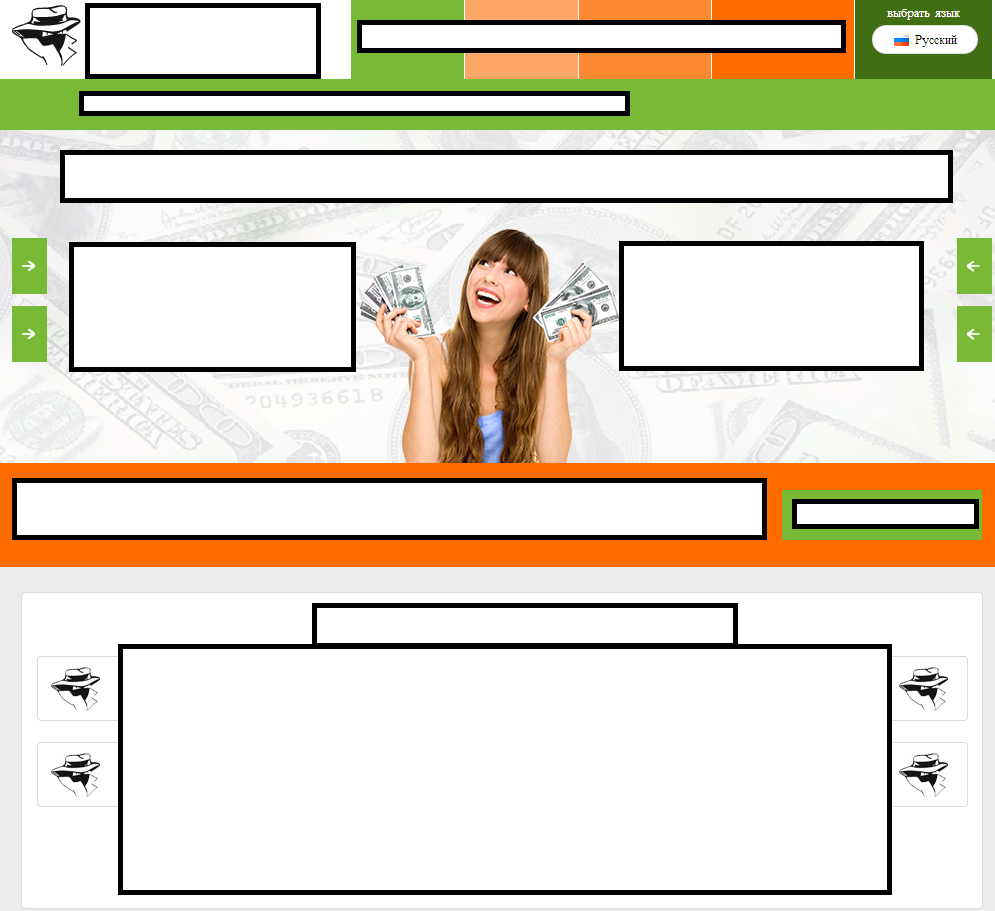
Sample screenshots of the affiliate network’s main site:
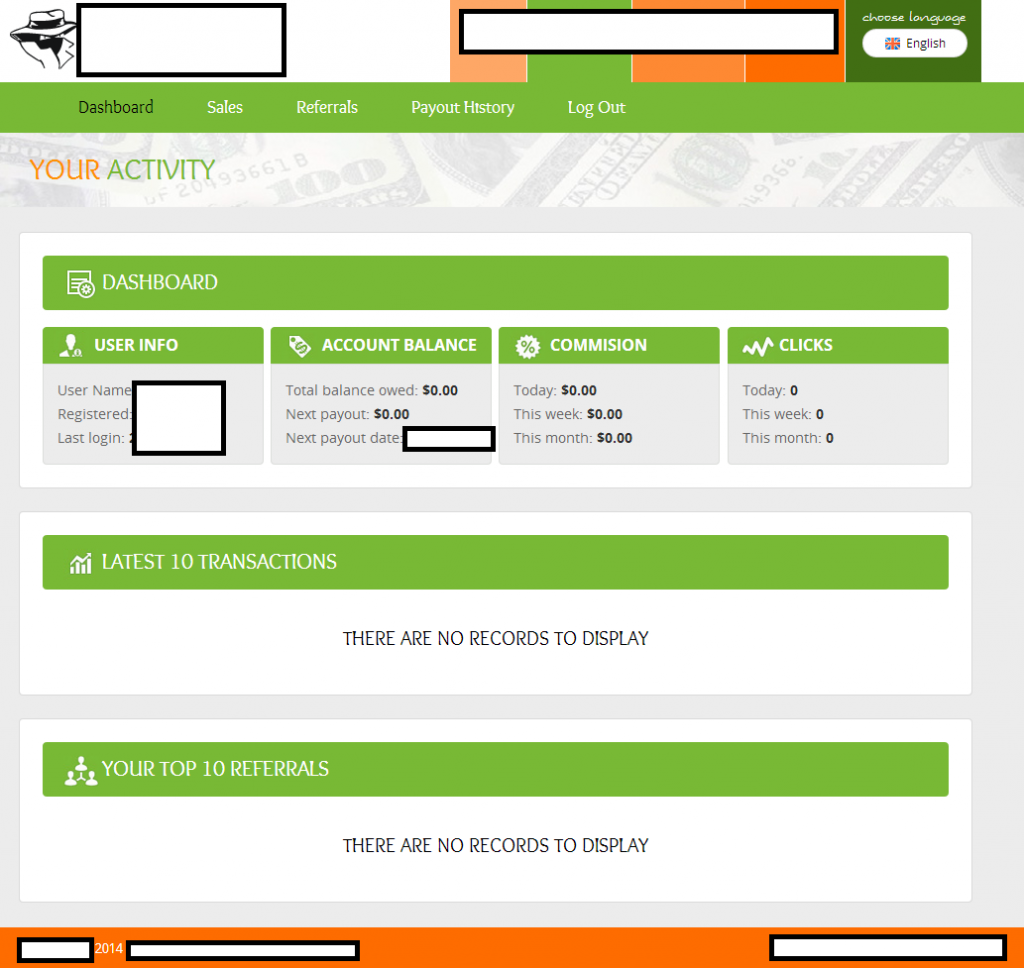
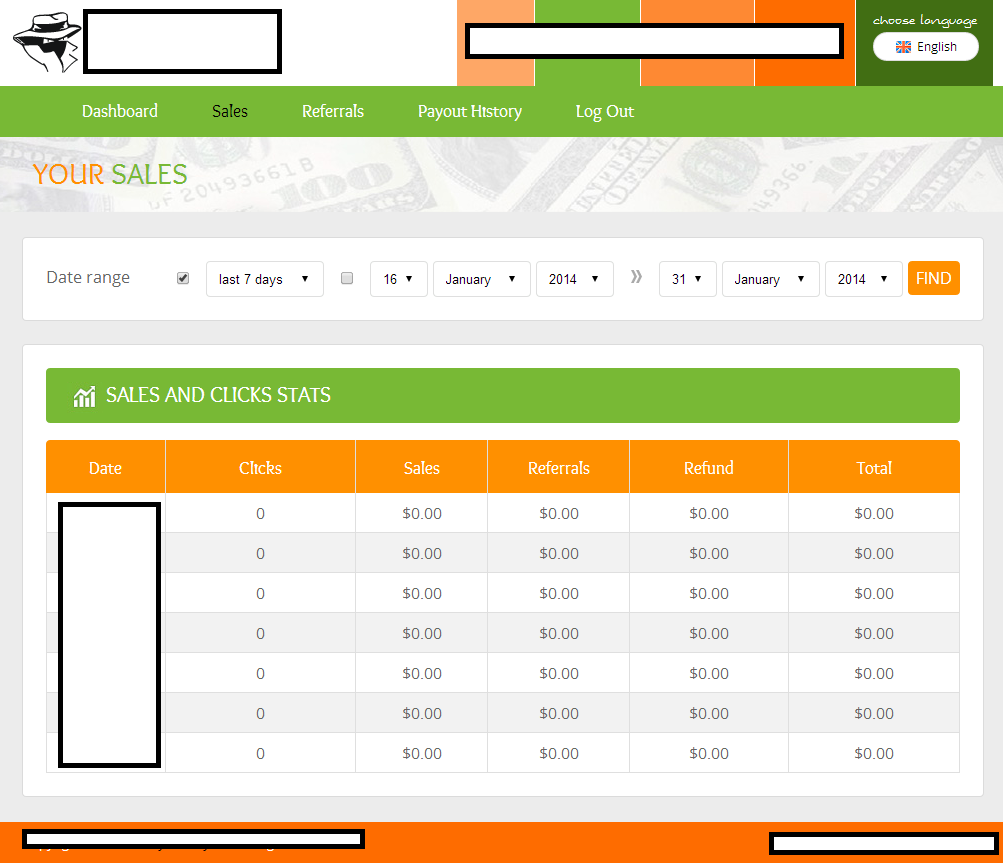
Sample screenshots of the Web based affiliate based interface:
Socks4/Socks5 enabled hosts continue to represent a key driving force behind the growth of the cybercrime ecosystem in terms of non-attributable stepping-stones capabilities and clean IP reputation based managed services. These services further empower vendors of automatic account registration tools with the necessary foundation to continue efficiently abusing legitimate Web properties. Based on our observations, the overall supply of Socks4/Socks5 enabled hosts is also contributing to the development of a vibrant market segment with more vendors pushing new Socks4/Socks4-specific releases that utilize this fraudulently generated infrastructure. We expect this market segment will continue flourishing with more vendors/services popping-up on everyone’s radar.
We’ll continue monitoring the development of the service/market segment and post updates as soon as new developments take place.