


Charity Scams to Watch Out for During the Holidays
Reading Time: ~ 5 min.
Unsecure RDP Connections are a Widespread Security Failure
Reading Time: ~ 3 min.
Between Two Worlds: An Interview with Reverse Engineer Eric Klonowski
Reading Time: ~ 4 min.
Crime and Crypto: An Evolution in Cyber Threats
Reading Time: ~ 6 min.
Social Media Malware is Deviant, Destructive
Reading Time: ~ 4 min.
Is GDPR a Win for Cybercriminals?
Reading Time: ~ 3 min.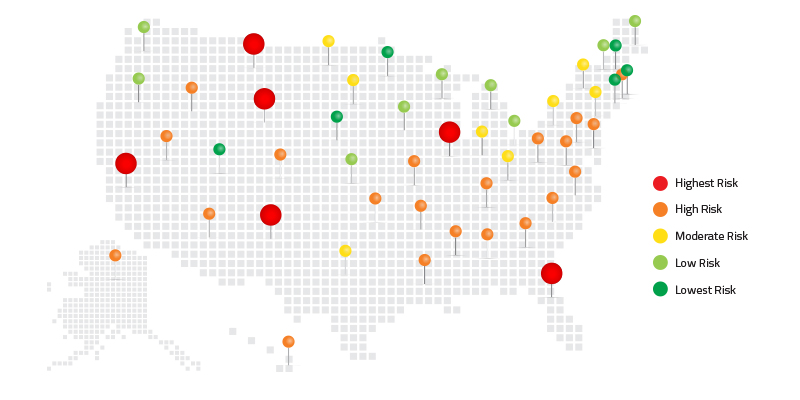
American Cybercrime: The Riskiest States in 2018
Reading Time: ~ 4 min.
Twitter is a Hotbed for Crypto Scam Bots
Reading Time: ~ 3 min.
Valentine’s Day Sends Mobile, Online Dating Scammers on the Prowl
Reading Time: ~ 3 min.
Safe Deposit: How to Keep Your Cryptocurrency Secure
Reading Time: ~ 4 min.





