MSPs weigh in: Key SOAR benefits driving MDR success
OpenText recently surveyed 255 MSPs to uncover key trends shaping the future of Managed Detection and Response (MDR). One technology area it explored was security orchestration, automation, and response (SOAR)—the workhorse behind automating security workflows. The survey revealed several key benefits of SOAR in MDR, highlighting how it can help MSPs and SMBs improve incident response, reduce alert fatigue, and deliver round-the-clock security.
SOAR is a technology that enables security teams to automate and streamline their workflows—from threat detection to response. It integrates and coordinates security tools and processes, helping analysts handle and respond to incidents. By automating repetitive tasks, such as triaging alerts and executing response actions, SOAR reduces manual effort and speeds up incident resolution. This improves the overall effectiveness of security operations, making it a critical component of modern MDR solutions.
Real-world benefits of SOAR for MDR solutions
Automation of common tasks
In the survey, 30% of MSPs pointed to automation of common tasks as the most valuable benefit of SOAR within an MDR service—and it’s easy to see why. Automation allows MSPs to streamline repetitive tasks like alert triage and standard response workflows. By speeding up incident resolution and ensuring consistent, accurate responses, SOAR helps MSPs address threats swiftly and effectively. This not only reduces the burden on security teams but also enables them to outpace adversaries and deliver stronger protection for their customers.
Improved 24/7/365 protection and after-hours response
Cybercriminals know that timing is everything. They often strike outside of business hours—late at night, on weekends, or during holidays—because they count on reduced staffing and slower response times to give them the upper hand. However, with MDR services leveraging SOAR, cybercriminals lose their “after hours advantage.”
According to the survey, 27% of MSPs identified improved 24/7/365 protection and after-hours response as a top SOAR benefit as part of an MDR solution. By automating detection and response using customizable workflows, SOAR ensures security measures are always on, regardless of the time or day.
Reduced alert fatigue
Alert fatigue is one of the most pressing challenges for security teams today. When bombarded with an overwhelming number of alerts, it’s easy for critical threats to get lost in the noise. SOAR directly tackles this issue, helping MSPs streamline their processes and focus on what really matters. In fact, 24% of MSPs in the survey noted that SOAR’s ability to reduce alert fatigue thereby improving accuracy and confidence was a key benefit for an MDR solution.
SOAR works by automatically analyzing security alerts against predefined rules and context, escalating the most critical threats to the surface. This not only sharpens the accuracy of responses but also enables security teams to act quickly and decisively. Security teams can use SOAR to create workflows to remediate the high-priority incidents that truly need attention, ensuring that any financial and reputational damage is minimized
Centralized incident management with enriched alerts
When it comes to incident management, having a disjointed view can slow down response times and make it harder to pinpoint the right course of action. That’s why 19% of MSPs in the survey highlighted centralized incident management and enriched alerts as one of the top benefits of SOAR for an MDR solution.
Alerts are enriched with the latest threat intelligence, which provides security teams with vital context. This deeper layer of information helps analysts understand the full scope and severity of an alert, allowing them to make quicker, more informed decisions. With SOAR, all relevant data is centralized in one platform, giving security teams a unified view that enhances their ability to respond effectively and prioritize the most critical threats without missing crucial details.
MDR with SOAR helps MSPs differentiate their offering
For MSPs, leveraging SOAR capabilities in their MDR offerings is a strategic move that can significantly enhance their service delivery. By focusing on the key benefits of automation using workflows, 24/7 protection, reduced alert fatigue, and centralized incident management, MSPs can provide a superior level of security that meets the evolving needs of their SMB clients. This differentiation not only improves client outcomes but also positions MSPs as leaders in the competitive security services market.
Incorporating SOAR into MDR services enables MSPs to offer a more efficient, reliable, and comprehensive security solution. With SOAR automating routine tasks, improving after-hours response, reducing alert fatigue, and centralizing incident management, MSPs can ensure that their clients receive the best possible defense against cyber threats. This approach not only enhances the overall security posture of SMBs but also builds trust and confidence in the MSPs’ ability to safeguard their clients’ digital assets.
Final thoughts
When MSPs choose to partner with a vendor for MDR, it’s important to select one that integrates SOAR into their offering. By doing so, MSPs can deliver a modern, proactive MDR service that improves security posture and provides the best experience for their SMB customers. SOAR accelerates response actions to stop adversaries in their tracks at every turn, ensuring that MSPs can swiftly detect and respond to threats before they inflict damage. With SOAR at the core, MSPs can offer a superior MDR service that adapts to the rapidly changing threat landscape, keeping their customers secure, happy, and confident.
The rising role of cloud-based SIEM in MDR: What MSPs need to know
OpenText recently surveyed 255 MSPs to uncover key trends shaping the future of Managed Detection and Response (MDR). The findings reveal not only what cybersecurity professionals are prioritizing but also how MSPs can better meet the evolving demands of their small and midsize business (SMB) customers.
One key takeaway from the survey: 81% of respondents rated cloud-based SIEM (security information and event management) as important to include in their MDR solution.
Why is cloud-based SIEM such a big deal for an MDR? Because for MSPs delivering MDR services, it’s the backbone that makes scalability, visibility, central and efficient threat management possible.
Cloud-based SIEM is an essential MDR backbone
The modern attack surface is vast. Business customers are spread across hybrid infrastructures with data flowing through endpoints, networks, applications, and the cloud. Cloud-based SIEM-powered MDR services help MSPs stay on top of this complexity by serving as the single source of truth for detecting and responding to threats.
Here’s why it matters:
- Seamless data ingestion
Cloud-based SIEMs ingest security telemetry from diverse sources—EDR solutions, applications, cloud infrastructure, network packet data, and more—to deliver a holistic view of a customer’s environment. - In-depth correlation and analysis
By correlating data across borderless infrastructures, SIEM provides security analysts with the context they need to identify, prioritize, and address the most impactful threats. - Scalability and accessibility
As businesses grow, so do their security needs. Cloud-based SIEM scales effortlessly, ensuring an MSP’s MDR services can handle large data volumes without compromising performance. Plus, analysts can access SIEM insights anywhere, anytime.
In short, a cloud-based SIEM ensures that no corner of the customer’s attack surface is left unseen—from endpoint to cloud. It provides comprehensive visibility, continuously collecting, correlating and analyzing data from every layer of the IT environment. This means the MDR service can detect threats wherever they may arise, whether on-premises, in the cloud, or across hybrid infrastructures, giving MSPs the ability to respond quickly and effectively to any potential risk.
How SIEM drives faster MDR outcomes
Cyberattacks move fast. MSPs delivering MDR services need tools and processes that can keep pace with today’s threats. A cloud-based SIEM is the essential technology that enables the MDR service to deliver rapid detection, triage and investigation. Here’s how SIEM supports faster outcomes across every stage:
- Rapid detection: A cloud-based SIEM continuously ingests and correlates syslog data from all sources, reducing the time it takes to identify a threat after it emerges.
- Time to triage: By consolidating telemetry into a centralized platform, SIEM enables security analysts to quickly assess and prioritize incidents—cutting through the noise to focus on the most critical threats.
- Accelerated investigation: SIEM by leveraging threat intel provides the context analysts need to understand a threat, pinpoint its origin, and determine its potential impact—all without needing to manually stitch together insights.
Expert-led, SIEM-enabled
When MSPs choose an MDR partner solution with a cloud-based SIEM at its core, they unlock more than just a sophisticated tool. They gain the advantage of expert-led security teams that can leverage the full potential of the SIEM platform to deliver rapid, precise, and continuous threat detection.
The survey results highlight that MSPs see the distinct advantage of running an MDR service with a cloud-based SIEM, which enhances their ability to run a 24/7/365 security operations center (SOC). With SIEM as the central hub, security experts can quickly surface suspicious activity, centrally manage investigations and take swift action.
The value of expert-led, SIEM-enabled MDR becomes even clearer when you consider the following benefits:
- Round-the-clock SOC with seamless investigations
The ability to monitor and respond to threats 24/7X365 is critical for an MDR service. By consolidating threat data into a centralized cloud SIEM, experts can detect malicious activity at any time of day or night. This continuous monitoring reduces the risk of attackers moving undetected, ensuring that threats are neutralized before they can cause harm. - Single, integrated tool for investigation
The MDR survey results highlight the value MSPs place on having a unified toolset for threat detection and investigation. A cloud-based SIEM with threat intel provides this central hub, enabling security teams to efficiently assess the scope of incidents, prioritize based on severity, and track the attack’s progress in real-time. The SIEM can correlate data across multiple environments—whether it’s endpoint data, network logs, or cloud infrastructure—ensuring nothing slips through the cracks. - Expert insight into threat context
The SIEM doesn’t just provide raw data; it enriches that data with valuable context from threat intel , helping the MDR security experts to identify the root cause of a threat, its potential impact, and the fastest path to resolution.
As cyber threats become more relentless and attack surfaces continue to expand, MSPs are in a unique position to help SMBs stay secure. OpenText’s MDR survey results highlight what’s clear: a cloud-based SIEM as part of an MSP’s MDR solution is a priority set up. It allows MSPs to deliver consistent, effective threat detection and response.
By combining the right technology with the right expertise, MSPs can navigate the complexity of today’s cybersecurity landscape and give their customers the confidence to focus on what matters most: growing their business.
Protect those you love from internet scams this Valentine’s Day
February is a great month to refresh your cyber awareness skills. February 11 marks Safer Internet Day, encouraging us to work together to make the internet a safer and better place. It’s the perfect time to learn more about cybersecurity risks and best practices for protecting yourself and your loved ones online.
And while February 14 usually means love is in the air, Valentine’s Day is also a popular day with internet scammers. In 2024, romance scams alone led to losses tallied to $3.8 billion according to the Nasdaq 2024 Global Financial Crime Report. Don’t be wooed by too-good-to-be-true offers, online dating scams, and fraudulent websites. Stay informed about common scams and take action to stay safe.
Common Valentine’s Day scams
Online dating scams
AI-powered phishing scams are on the rise, impersonating popular online dating platforms. Scammers send fake match emails with malicious links, pretending to be from legitimate dating websites.
📌 Tip: Look for misspellings in the dating website name or web address and check the “from field” to make sure it’s a real address.
Trust your instincts
If something feels off—like a relationship escalating too quickly or seeming too perfect—listen to your gut.
📌 Tip: Scammers often use rapid declarations of love to emotionally manipulate their victims.
Be cautious with platform switching
Think twice before moving a conversation off a dating app to a less secure platform.
📌 Tip: Scammers often push for this to avoid detection.
Phony gift and delivery services
Scammers often lure victims with heavily discounted flowers, gifts, or even romantic getaway deals on unknown websites. These fraudsters go to great lengths to create the appearance of being legitimate florist, gift basket retailer, or travel agent, setting up websites, placing ads on social media, and sending emails. You go to the website enter your information and credit card details only to receive nothing or something that is not what you ordered.
📌 Tip: Always verify websites by checking for HTTPS in the URL and reading online reviews before making a purchase.
E-card and gift card scams
While digital greeting cards and gift cards are a convenient way to spread love, they’re also a common tool for cybercriminals. Scammers send fake e-cards that contain malware or gift card phishing emails asking you to redeem them on fraudulent websites.
📌 Tip: Never open e-cards from unknown senders, and never purchase gift cards as payment for someone you haven’t met in person.
How to protect your heart, computer, and wallet from these scams
Do your research
Before opening email or clicking links make sure they are being sent to you by a reputable brand. Webroot Secure VPN + AntiVirus offer real-time protection for your connection and devices while you are browsing the internet.
Be cautious sharing personal information
Don’t share sensitive information like credit card details or home address with any website or person unless you are confident in their identity. Consider investing in identity protection security solutions that will monitor the web for unauthorized usage and credit report monitoring, such as Webroot Premium.
Secure your devices and backup your data
Ensure your devices have the latest security updates installed. Use Carbonite’s secure, automatic computer backup solution to protect important files from cyber threats.
Strengthen your passwords and use two-factor authentication
Make sure to use complex and unique passwords, incorporating letters, numbers and symbols. Consider enabling multi-factor authentication (MFA) for extra security—this helps verify your identity with a second step, like a text or email code. Solutions such as Webroot Premium and Webroot AntiVirus include passwords managers to making it easier to remember all your passwords.
Use an all-in-one device, privacy, and protection solution
For complete device, privacy, and identity protection, consider a solution like Webroot Premium and get the best of all worlds –threat detection, password manager, dark web monitoring, and real-time virus protection.
Let’s stay cyber resilient this February and keep Valentine’s Day scam-free! 💙
Looking for more information and solutions?
Passkeys: The future of secure and seamless authentication
What are passkeys?
You may have seen the term “passkeys” appearing more frequently in tech news, app updates, and security discussions. Major companies like Apple, Google, and Microsoft are rolling out passkeys as a replacement for passwords, promising both enhanced security and a smoother user experience. But what exactly are passkeys, and why are they considered the future of authentication?
With Password Day coming up this Saturday, it’s the perfect time to discuss the future of authentication. Passwords have long been the foundation of online security, but they come with significant downsides: they can be stolen, guessed, or reused across multiple sites. Enter passkeys, a next-generation authentication technology designed to replace passwords entirely with a more secure and user-friendly alternative.
Passkeys leverage public-key cryptography to authenticate users without requiring them to remember or type in a password. Instead, passkeys are stored on a trusted device (like your phone, laptop, or tablet) and are accessed using biometrics (Face ID, fingerprint), a PIN, or other device authentication methods. This means no more passwords to remember, reset, or leak in data breaches.
Check out our recent webinar where we discuss passkeys
How do passkeys work?
Passkeys function using a public and private key pair:
- The public key is stored on the website or service you’re signing into.
- The private key stays securely on your device and is never shared.
When you log in, the website asks your device to prove that it holds the correct private key. Your device then uses biometric authentication (like Face ID or a fingerprint) to confirm your identity, and the cryptographic exchange verifies you without transmitting a password over the internet. This makes passkeys resistant to phishing, credential stuffing, and brute-force attacks.
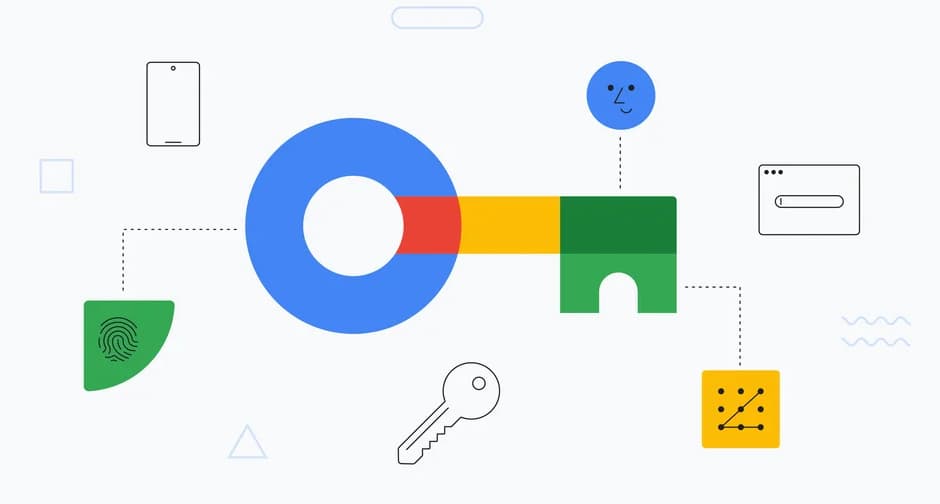
Illustration: Google Ask a Techspert
Pros of passkeys
1. Enhanced security
- No passwords mean no risk of phishing attacks, password leaks, or brute-force attacks.
- Passkeys are unique for every website, preventing credential reuse across multiple accounts.
- Resistant to man-in-the-middle (MitM) attacks because private keys are never shared.
2. Seamless user experience
- No need to remember or type passwords—simply authenticate with Face ID, a fingerprint, or a PIN.
- Logging in is faster and easier, especially on mobile devices.
- Syncs automatically across devices when backed up in Apple iCloud Keychain, Google Password Manager, or Microsoft Account.
3. Built-in multifactor authentication (MFA)
- Traditional MFA often requires entering a one-time passcode (OTP), which can be intercepted.
- Passkeys combine possession (your device) and biometric authentication, making them more secure than passwords + SMS codes.
4. No centralized password database to hack
Unlike traditional login systems that store passwords in a database (which hackers can breach), passkeys store only public keys on websites, reducing the risk of massive data breaches.
5. Reduced risk of social engineering
- Attackers can’t trick users into revealing passkeys like they do with passwords.
- Since passkeys are bound to specific websites, even if a hacker creates a fake login page, they won’t be able to use the stolen passkey elsewhere.
Cons of passkeys
1. Device dependency
- Passkeys are tied to your device, meaning if you lose access to your phone or laptop, you could have trouble logging in.
- Solution: Enable cloud backups through iCloud Keychain (Apple), Google Password Manager (Android/Chrome), or Microsoft Account.
2. Not all websites support passkeys yet
- While adoption is growing, not every website or service currently supports passkeys.
- Workaround: You may still need to use passwords for some sites while passkey adoption expands.
3. Migration challenges
- Users switching between ecosystems (Apple to Android or vice versa) may need to manually transfer passkeys.
- Solution: Some platforms allow exporting and importing passkeys, but it’s not always seamless.
4. Learning curve for some users
- Users unfamiliar with biometrics, password managers, or cryptographic authentication might find passkeys confusing at first.
- Solution: Tech companies are working on better onboarding experiences to help ease the transition.Users unfamiliar with biometrics, password managers, or cryptographic authentication might find passkeys confusing at first.
- Solution: Tech companies are working on better onboarding experiences to help ease the transition.

What happens if you lose your phone?
Losing your device when using passkeys can be a concern, but here’s how to handle it:
1. Use a backup device
If you’ve set up passkeys on multiple devices (e.g., phone, tablet, laptop), you can log in using another device.
2. Restore from cloud backup
- Apple, Google, and Microsoft automatically sync passkeys across devices using their respective cloud services.
- When setting up a new phone, simply log into your cloud account to restore access.
3. Account recovery options
- Many services still offer fallback authentication methods, such as email recovery, SMS codes, or backup keys.
- Some sites allow you to generate a recovery passkey during setup—store this in a safe place!
4. Remote device management
If your phone is lost or stolen, use Find My Device (Apple, Google) to remotely wipe or lock it to prevent unauthorized access.
Why you should consider switching to passkeys
- Stronger security than passwords—no phishing, leaks, or brute-force attacks.
- Faster logins—just use your fingerprint or face instead of typing passwords.
- No password resets—forget the frustration of forgetting your credentials.
- Growing adoption—major companies like Apple, Google, Microsoft, and banks are pushing for passkey implementation.
Passkeys represent a significant shift in authentication, making online accounts more secure and easier to use. While challenges like device loss and adoption gaps still exist, the benefits far outweigh the drawbacks.
If you haven’t tried passkeys yet, consider setting them up on a supported website. As more services move toward this passwordless future, early adopters will enjoy enhanced security and convenience while leaving the hassles of passwords behind.
OpenText Secure Cloud: Streamline workflows with integrations
Simplifying security management is an important step toward better protection without sacrificing operational efficiency. With the added capability of automating processes by integrating with popular tools, security management can also deliver streamlined workflows.
OpenText™ Secure Cloud provides billing reconciliation by integrating with popular tools such as HaloPSA, ConnectWise PSA, AutoTask, and Kaseya BMS so you can automate many of the processes that would typically require manual input. These integrations help boost efficiency and reduce human error.
HaloPSA integration delivers:
Automatic invoice retrieval—The platform retrieves the monthly invoice from AppRiver, listing all recurring services purchased during the previous period.
Effortless invoice comparison—At the touch of a button, you can compare and update any differences directly within HaloPSA.
Simple setup—Link customers, recurring invoices, and products once and the system will remember your settings for next time.
ConnectWise PSA integration delivers:
Seamless invoice management—Similar to HaloPSA, the AppRiver invoice is automatically loaded into the platform, saving you time and effort.
Easy linking—The first time you use the integration you can link companies, agreements, and products, ensuring that future invoice retrieval is smooth and fast.
Customizable—If any agreements or products are missing in ConnectWise you can add them directly from within the platform.
AutoTask integration delivers:
Efficient invoice updates—The integration allows you to load and check AppRiver invoices quickly.
One-time setup—Link your customers, contracts, and services once and the system will remember your settings for next time.
Quick additions—If a contract or service is missing, it’s easy to create it within the platform, reducing downtime.
Kaseya BMS integration delivers:
Invoice and contract validation—AppRiver invoices are automatically retrieved and validated against your Kaseya BMS contracts, offering updates where needed.
Efficiency—If service quantities don’t match, you can update them directly within the system.
Simple linking—Set up by linking customers, contracts, and services once and future updates will be swift and hassle-free.
These integrations with OpenText Secure Cloud help you manage recurring services, validate invoices, and update your systems effortlessly. They save you time, reduce errors, and enable a smoother, more connected workflow across multiple platforms.
To learn more, get in touch with us here.
MDR for MSPs: Navigating EDR compatibility
When it comes to endpoint detection and response (EDR) compatibility within an MDR offering, managed service providers (MSPs) are weighing two key priorities: native EDR integration or the flexibility to support multiple solutions. According to a recent OpenText survey, opinions are split almost evenly. While 52% of MSPs view native compatibility as moderately or very important, 48% place greater value on flexibility.
This divide reflects the unique demands MSPs face. On one hand, native compatibility ensures a tight integration. On the other, the ability to work seamlessly with various EDR tools is critical for MSPs managing diverse client environments. For MSPs managing a mix of EDR tools across their customer base, this adaptability can be the difference between a smooth operation and a logistical headache.
In this blog, we’ll explore why flexibility in EDR compatibility is becoming a critical advantage for MSPs, how it ties into SIEM analysis, and actionable steps MSPs can take when evaluating MDR providers.
The case for native EDR compatibility
For MSPs and their customers, native EDR compatibility can offer advantages, especially when targeting newer companies that have not yet established an EDR infrastructure.
Here’s why:
- Streamlined integration:
Native EDR solutions typically provide seamless integration with the MDR platform, simplifying deployment and reducing setup time. This can be particularly appealing for MSPs looking to quickly onboard new customers who do not yet have an EDR solution in place. - Ease of use:
A native EDR integrated into the MDR platform provides MSPs with a consistent toolset, simplifying training for security teams and boosting overall efficiency and productivity.
However, for MSPs serving established SMBs that already have an EDR solution, the dynamic changes. An MDR capable of working with any EDR solution often delivers greater flexibility and value by complementing the SMBs’ existing setups.
When flexible EDR support wins
For MSPs, flexibility in EDR support provides a more strategic advantage. Managing security for well-established SMBs often means working within complex, diverse environments where a rigid “one-size-fits-all” approach simply doesn’t work. Here’s why flexible EDR support matters:
- Avoiding “rip and replace:”
Many MSP prospects already have an EDR solution in place that they are comfortable with and that meets their needs. Moving to a new, native EDR can impose a “rip and replace” burden, leading to disruptions and additional costs that may not be acceptable to MSPs. - Supporting diverse client environments:
MSPs often manage a variety of EDR products across their customer base. The ability to support multiple EDRs means MSPs can tailor their MDR services to fit the unique needs of each client without forcing them to change their existing security infrastructure. - Future-proofing:
Flexibility allows MSPs to stay ahead of the curve by ensuring their MDR solution can integrate with emerging EDR tools. This adaptability is crucial in a rapidly evolving cybersecurity landscape.
The MDR advantage—unifying EDR telemetry through SIEM
In a modern MDR solution, the SIEM platform serves as the backbone, ingesting security telemetry from across the customer environment. This includes feeds from firewalls, cloud services, identity providers, and—crucially—EDR solutions. The ability to support multiple EDR tools isn’t just about flexibility; it’s about leveraging the full power of SIEM to deliver more effective and unified threat detection and response.
- Centralized visibility:
By aggregating telemetry from diverse EDRs and other security tools into a single SIEM platform, MSPs gain a holistic view of the customer’s security posture. This comprehensive perspective enables faster identification of threats and vulnerabilities across the environment. - Improved threat detection:
SIEM platforms excel at correlating data from multiple sources. By ingesting streams from EDRs alongside other security feeds, the MDR solution enhances its ability to detect sophisticated threats with greater accuracy and precision, reducing false positives and improving response times. - Enhanced reporting and insights:
Unified telemetry within the SIEM allows MSPs to generate detailed, actionable reports that highlight trends, identify gaps, and demonstrate the value of their security services. These insights help MSPs guide their clients in making smarter security investments.
Actionable advice for MSPs
When choosing an MDR provider, MSPs should keep a few key factors in mind:
- EDR compatibility:
Ensure the MDR solution can seamlessly integrate with multiple EDR tools to support your diverse client environments. - SIEM integration:
Look for MDR solutions that can unify EDR telemetry through a centralized SIEM platform. - Scalability:
Choose an MDR provider that can scale with your business and offers the flexibility to adapt to evolving client needs and emerging cybersecurity challenges.
By prioritizing these factors, MSPs can provide their customers with advanced, efficient, and flexible security solutions that meet their unique needs.
6 ways to get the most from Data Privacy Week
Data Privacy Week (Jan. 27-31) is an excellent opportunity to reflect on the importance of protecting one of your most valuable assets: your personal information. Whether you’re browsing online as a consumer or running a business, data privacy is paramount in an environment where cyber threats can lurk around every corner.
In the spirit of Data Privacy Week, here are six ideas to help you protect yourself—and your data:
1. Understand your level of risk
Get acquainted with the phrase personally identifiable information. This includes any data that can be used to identify you, and it ranges from your name and address to more sensitive information like health and financial records. Here are some common examples:
- Health data: Information stored in a patient portal, online pharmacy, or health insurance website.
- Financial data: Details of your bank account, 401K fund, or IRA.
- Apps: Data collected by various applications you use. This information can range from your current location to previous purchasing habits.
- Social media: Information you share on platforms like Facebook, Twitter, and Instagram.
Knowing what kinds of personal data you have out there is the first step toward protecting it.
2. Learn the basics of data privacy self-defense
Protecting your data doesn’t have to be complicated. Here are some basic steps you can take to safeguard your privacy:
- Create secure passwords: Use a combination of letters, numbers, and special characters.
- Use multifactor identification: Add an extra layer of security to your accounts by using a password combined with a code sent to their phone or a fingerprint.
- Limit the number of cookies you accept: Be selective about which websites can track your activity.
- Beware of public Wi-Fi: Avoid accessing sensitive information on unsecured networks.
- Use a virtual private network, or VPN: Encrypt your internet connection to protect your data.
- Keep software up to date: Regular updates can protect you from security vulnerabilities.
3. Update your privacy settings
Take some time to review the privacy settings on the apps, devices, or websites you use most often. You might be surprised at what you find. The nonprofit National Cybersecurity Alliance has compiled a comprehensive list of popular sites’ privacy pages to get you started.
4. Arm yourself with antivirus protection
An effective antivirus program is essential for protecting your devices from malware and other threats. Look for features such as real-time scanning, automatic updates, and comprehensive protection against various types of malware. A product like Webroot offers a variety of antivirus solutions to keep your data safe. Webroot even offers a product selection tool that can help you find a solution tailored to your unique needs.
5. Find an encrypted data backup product
Backing up your data is crucial, but it’s equally important to ensure that those backups are secure. An encrypted data backup solution like Carbonite can protect your data from unauthorized access. Carbonite’s secure, always-on backup ensures that you won’t lose important, irreplaceable files due to accidental deletion or device malfunction.
6. Take in a movie
After all that hard work learning about data privacy, it’s time to reward yourself by doing something fun. Hop on the couch and watch a movie that delves into the topic. Here are some suggestions from the nonprofit group Educause:
- Terms and Conditions May Apply
- Citizen Four
- Code 2600
- Gattaca
- Minority Report
- 1984
- The Lives of Others
Managed Detection and Response: Key trends MSPs can’t afford to ignore
Cyber threats have never been more relentless, and businesses of all sizes are feeling the pressure. That’s where Managed Detection and Response (MDR) comes in—a lifeline for overburdened security teams navigating a threat landscape that’s growing more sophisticated by the day.
At its core, MDR is about augmenting, complementing, and upskilling internal security operations. It’s not just about tools—it’s about the expert humans behind those tools. MDR providers bring battle-tested security practitioners and capabilities with:
- Global visibility into threats and threat actors.
- Detection engineering expertise to uncover what others might miss.
- Strong threat hunting capabilities, working 24/7 to stay ahead of adversaries.
- Seamless integration across diverse security tools and logging ingestion from all corners of the organization’s infrastructure.
What started as an emerging offering has quickly grown into a cornerstone of modern cybersecurity strategy. Today, MDR is a thriving, competitive market. As Forrester notes: “MDR continues its ascent as an established, growing service with expansion, innovation, and an abundance of competition.”
But with maturity comes diversity of capabilities. For Managed Service Providers (MSPs), the challenge isn’t just keeping pace with the evolution of MDR—it’s about understanding what truly matters to their customers and delivering solutions that make an impact.
So, what exactly drives adoption, and which capabilities resonate most with MSPs in supporting their customers?
When it comes to endpoint detection and response (EDR) compatibility, MSPs are split almost evenly—52% of respondents rated native compatibility as moderately or very important, while 48% viewed it as less critical.
This near-even divide underscores an important trend: for many MSPs, the ability to support a range of EDR products is becoming just as crucial as having native EDR integration. Since many MSPs support a variety of EDR products across their customer base, the ability of an MDR solution to seamlessly integrate with multiple tools is often prioritized over a ‘one-size-fits-all’ approach.
For MSPs, this flexibility means they can:
- Tailor MDR services to fit the unique needs of each SMB client
- Avoid being locked into a single EDR vendor, maintaining freedom of choice
- Future-proof their offerings by ensuring compatibility with emerging EDR tools
Ultimately, while native EDR compatibility is still a desirable feature, MSPs are clear: an MDR solution’s real value lies in its versatility across diverse environments.
Cloud-based SIEM—The backbone of MDR
The survey revealed that 81% of respondents rated cloud-based SIEM (security information and event management) as important—whether slightly, moderately, or very—to be included in their MDR solution. This emphasizes the shift toward scalable, centralized solutions designed to enhance visibility and efficiency in managing threats across the full breadth of the MSP customer’s environment.
This highlights how cloud-based SIEMs empower MSPs to:
- Scale with ease as their SMB customers grow and threats evolve
- Stay connected with anywhere-accessible platforms
- Streamline operations by correlating andcentralizing threat management and response
For MSPs, incorporating cloud-based SIEM into their MDR offerings is no longer just a nice-to-have—it’s a competitive differentiator.
SOAR capabilities—Automation in MDR services takes center stage
In the world of Managed Detection and Response (MDR), security orchestration, automation, and response (SOAR) capabilities are rapidly becoming game-changers. For MSPs, the most valuable benefit from SOAR is clear: automation. When asked to identify the most valuable benefit from SOAR, the results revealed key insights:
- 30%—Automation of common tasks
Automating routine tasks significantly via workflows reduces the time spent on manual processes, leading to faster, more efficient incident resolution and freeing up teams to focus on higher-value activities. - 27%—Improved 24/7/365 protection
Enhanced after-hours response capabilities are critical for ensuring continuous protection, especially for SMBs that need around-the-clock vigilance. - 24%—Reduced alert fatigue
Prioritizing actionable alerts enables more accurate threat detection, helping MSPs build greater confidence in their systems and focus on the threats that truly matter.
This prioritization reflects a preference for efficiency and proactive threat management in MDR workflows. For MSPs, SOAR isn’t just a tool for automation—it’s a critical enabler of better resource management, helping them reduce the burden on their teams while offering enhanced, after-hours response to their customers.
The survey highlights key priorities for MSPs in the MDR landscape: flexibility, scalability, and efficiency. These qualities are critical for MSPs to meet the diverse and evolving needs of their SMB customers. For both MSPs and their customers, this focus translates into enhanced access to advanced threat detection and response capabilities, even when resources are constrained.
Up next—Deep dives into MDR’s most Important capabilities
This blog kicks off a four-part series exploring key insights from our OpenText MDR survey. Over the next few weeks, we’ll take a deeper look at the essential capabilities MSPs need to stay ahead of the curve and provide maximum value to their customers.
We’ll dive into:
- EDR compatibility: Why it’s crucial for your MDR offering—and when flexibility wins.
- Cloud-based SIEM: Why it’s a must have for MSPs in an MDR offering.
- SOAR benefits: How SOAR is elevating MDR services and improving efficiency.
Stay tuned for actionable insights that will help MSPs navigate the rapidly evolving world of MDR.
Why MSPs need proactive, 24/7 threat hunting
Cybercriminals are becoming increasingly sophisticated, agile, and fast. For managed service providers (MSPs) supporting small and medium-sized businesses (SMBs) with cybersecurity services, staying ahead of these adversaries is crucial. One of the most effective ways to do so is through round-the-clock threat hunting.
In this blog, we’ll explore why constant threat hunting is essential, the challenges MSPs face in providing it, and how OpenText MDR can help overcome these challenges while offering SMBs the protection they need.
The critical edge of 24/7 threat hunting
The pace of cyberattacks has never been faster. Modern threat actors are well-organized and highly skilled, using a range of attack methods to infiltrate systems, escalate privileges, and exfiltrate valuable data. The days of simplistic attacks that can be thwarted by basic defenses are long gone. Today’s adversaries employ advanced tactics like cross-domain attacks, use of stolen credentials, and sophisticated social engineering campaigns to infiltrate systems.
In addition to their increasing sophistication, adversaries are also incredibly fast. Breakout time, the window of time it takes for an attacker to gain initial access and the point at which they can move laterally to other critical systems, can be measured in minutes.
Given this reality, each minute lost in detection can give attackers the critical time they need to entrench themselves deeper within the organization’s environment. That’s why faster detection and response times are essential, delaying the response only increases the damage. That’s where 24/7 threat hunting becomes indispensable for MSPs looking to stay one step ahead of cybercriminals and protect their SMB customers.
Proactive threat hunting is the key to proactively identifying suspicious activity. It’s not just about waiting for an alert; it’s about actively searching for hidden threats in real-time. Threat hunting involves a combination of human expertise and advanced technologies that continuously analyze system data, identifying suspicious patterns or behaviors. By leveraging threat intelligence, threat hunters can spot emerging tactics, techniques, and procedures (TTPs) used by adversaries, often before they’re seen in traditional threat intelligence feeds.
The challenge of building 24/7 threat hunting
in-house
While 24/7 threat hunting is undeniably essential for protecting SMBs, building and delivering this capability in-house presents significant challenges for many MSPs. Providing round-the-clock monitoring and expert threat hunting requires not only advanced technology but also skilled cybersecurity professionals—resources that can be costly, complex to manage, and hard to scale. Here are some of the main challenges MSPs face when trying to provide 24/7 threat hunting:
- High financial investment
A fully staffed threat hunting team with a security operations center (SOC) requires significant financial investment. In-house teams need to be equipped with advanced security tools, threat intelligence, and continuous training. - Complexity of management
Threat hunting is not a simple task. It involves gathering and analyzing vast amounts of data from a range of endpoints, networks, and cloud to identify and track suspicious activity. With the growing number of tools and services available, managing these resources can quickly become overwhelming. MSPs may lack the expertise to tie everything together or the time to continuously monitor and analyze threat hunting data. - Resources
Maintaining 24/7 monitoring requires ongoing staffing, training, and operational management, which can stretch MSP resources thin. It’s hard to find skilled professionals who can perform threat hunting and respond to incidents in real-time. Cybersecurity talent is in high demand, and the shortage of skilled security experts makes it even more difficult for MSPs to maintain a robust in-house security operation.
Given these challenges, how can MSPs continue to provide best-in-class security services to their SMB customers? The answer lies in outsourcing to a fully managed solution that offers 24/7 threat hunting without the need for large internal teams or heavy financial investment.
That’s where OpenText MDR comes in.
OpenText MDR: The MSP solution for 24/7 threat hunting
For MSPs looking to provide round-the-clock threat hunting without the overhead of building an in-house solution, OpenText MDR offers a fully managed detection and response service that provides continuous monitoring, expert threat hunting, and rapid incident response—backed by a 24/7/365 SOC.
Here’s how OpenText MDR addresses the challenges MSPs face:
- Comprehensive, scalable SOC
OpenText MDR comes with 24/7/365 coverage staffed by experienced cybersecurity professionals. This means MSPs can offer their clients continuous monitoring and rapid incident response, without the need to invest in expensive infrastructure or manage the in-house complexities. - Expert threat hunting
At the heart of OpenText MDR’s threat hunting is our team of security experts who work around the clock, 24/7, to proactively hunt for emerging threats. Leveraging a combination of AI-driven analytics and real-time data analysis, our threat hunters can identify suspicious activity and potential risks long before they escalate into full-blown attacks. With a deep understanding of adversary tradecraft and advanced threat intelligence, our experts are equipped to detect sophisticated attack methods. This combination of human expertise and cutting-edge technology enables our team to spot attack patterns as they emerge. - Integrated SIEM & SOAR capabilities
OpenText MDR combines cloud based SIEM and SOAR capabilities in one platform. This integration simplifies threat detection, prioritization, containment, and enables remediation through automated and customizable workflows, enabling a swift and coordinated response when a threat arises. - Seamless integration with existing tools
OpenText MDR integrates with over 500 security tools and services, allowing MSPs to leverage their existing investments while enhancing their capabilities with advanced threat detection and response. This collaborative approach streamlines the process, making it easier for MSPs to implement and manage without starting from scratch. - Cost-effective solution
Instead of investing heavily in tools, infrastructure, and talent to build an in-house solution, MSPs can rely on OpenText MDR as either a fully managed or co-managed service. This enables MSPs to offer cutting-edge protection to their SMB clients at a fraction of the cost and complexity of running their own SOC.
By partnering with OpenText MDR, MSPs can provide their SMB customers with proactive, 24/7 threat hunting and comprehensive protection against sophisticated cyber threats. This simplifies security, allowing MSPs to stay competitive while ensuring their clients are safeguarded without the burden of building and managing an in-house threat hunting team.
Why MSPs must offer 24/7 cybersecurity protection and response — and how OpenText MDR can help
In today’s cyber threat landscape, good enough is no longer good enough. Cyberattacks don’t clock out at 5 PM, and neither can your security strategy. For Managed Service Providers (MSPs), offering customers 24/7 cybersecurity protection and response isn’t just a competitive advantage—it’s an essential service for business continuity, customer trust, and staying ahead of attackers.
But delivering round-the-clock security coverage is easier said than done. It requires the right tools, expertise, and scale. This is why partnering with OpenText for offering managed detection and response (MDR) can help MSPs deliver on this critical need without overburdening their resources.
The case for 24/7 cybersecurity protection
Let’s face it: the cyber threat landscape is relentless, and the game is changing fast. Small and medium-sized businesses (SMBs) make up the core customer base for MSPs and are often top targets for cyberattacks. Cybercriminals see SMBs as easier to exploit—with fewer resources for advanced defenses and treasure troves of valuable data.
But what makes the modern threat landscape even more dangerous is the speed and sophistication with which cybercriminals operate. Attackers are no longer lone actors poking at vulnerabilities. They are part of well-funded by rogue nations, highly organized operations using advanced techniques, automation, and artificial intelligence to breach systems faster than ever.
- The numbers don’t lie: SMBs are the victims of 43% of cyberattacks. And many of these attacks happen outside of business hours.
- Cybercrime costs are skyrocketing: Global cybercrime damages are expected to hit $10.5 trillion annually by 2025, and businesses without adequate security measures face steep financial and reputational losses.
- Compliance mandates are tightening: Regulations like GDPR, CCPA, and PCI DSS mean SMBs are under growing pressure to protect their sensitive data 24/7.
For MSPs, this means your customers need more than basic firewalls and endpoint protection. They need real-time monitoring, proactive threat hunting, and rapid incident response—all delivered 24/7. Anything less, and you risk leaving customers vulnerable to costly breaches.
The challenge for MSPs: Scaling 24/7 coverage
For MSPs, managing a large number of customers, the question becomes: How do you respond in real-time to stop these lightning-fast threats before they cause irreparable damage? Providing 24/7 cybersecurity protection is no easy task for MSPs. Building an in-house security operations center (SOC) to handle threats around the clock is both costly and resource-intensive.
Some common challenges include:
- Talent shortages: The cybersecurity industry faces a well-documented skills gap, making it hard for MSPs to find and keep experienced analysts. This challenge is so widespread that 43% of MSPs cite it as their biggest obstacle to delivering security services.
- High costs: The expense of creating an in-house SOC can be astronomical, often reaching millions. In fact, 33% of MSPs identify the overwhelming cost of needing numerous cybersecurity tools as a major barrier to offering security services.
- Evolving threats: Cybercriminals are constantly adapting and refining their attack strategies, making it essential for MSPs to stay ahead. This ongoing evolution demands continuous investment in both training for an MSP’s security team and the latest technologies to effectively detect and mitigate new types of threats.
This is where OpenText MDR comes in, empowering MSPs to deliver enterprise-grade protection without the heavy lifting of building your own in-house SOC.
Why MSPs should partner with OpenText MDR
OpenText MDR combines cutting-edge technology, human expertise, and 24/7 monitoring to help MSPs meet their customers’ growing cybersecurity demands. Here’s why OpenText MDR is the ideal solution:
- 24/7/365 threat monitoring and response
OpenText MDR provides constant vigilance, ensuring your customers are protected day and night. With advanced threat detection and remediation powered by SIEM and SOAR technology, it quickly spots and shuts down threats before they can do any damage. - Access to cybersecurity experts
You don’t need to recruit, train, or retain a team of highly skilled security analysts. OpenText MDR’s team of experts, including threat hunters, incident responders, and forensic analysts, acts as an extension of your team, empowering you to provide your customers with a proactive defense without the burden of recruiting an in-house team. - Scalability without complexity
As your customer base grows, OpenText’s Secure Cloud Platform scales effortlessly to meet demand. OpenText MDR simplifies security management with automation that processes vast amounts of data quickly and integrates seamlessly with over 500 tools and services. Its lightweight agent ensures effortless deployment across multiple environments, providing end-to-end data visibility in a single dashboard, while leveraging existing investments and guided by expert human analysts - Proven threat intelligence
Leverage OpenText’s global network and AI-driven threat intelligence and over 35 different threat intel feeds to stay ahead of emerging attack vectors. With automated and customizable workflows, continuous threat prioritization, containment, and remediation, you gain a proactive and collaborative approach to securing endpoints, networks, and cloud—reducing the likelihood of breaches and minimizing downtime.
Why MSPs can’t afford to wait
In a world where attackers can compromise a network in under an hour, every second counts. Without the ability to detect, analyze, and respond to security threats in real time, your customers face serious risks:
- Downtime from a successful attack, leading to lost revenue.
- Loss of sensitive data, with potential regulatory fines to follow.
- Reputational damage that’s hard to repair.
MSPs that partner with OpenText MDR gain the speed, expertise, and oversight needed to combat these threats head-on. By combining advanced technology with human expertise, OpenText MDR delivers the constant vigilance your customers need to stay secure in the face of ever-evolving cyber threats.
Let’s work together to give your customers the 24/7 protection they deserve.
Contact us today to learn more.
6 reasons why SMBs love OpenText MDR
In today’s digital-first world, small and medium-sized businesses (SMBs) face cybersecurity challenges that grow more complex by the day. SMBs are prime targets for attackers hoping to gain a foothold inside any organization that doesn’t have extensive security measures. As threats increase, so does the need for comprehensive, reliable, and accessible protection.
This is where managed detection and response (MDR) services come in. MDR combines threat detection, investigation, and response, offering businesses the support from a team of security experts who monitor the environment 24/7 to identify and respond to threats. For many SMBs, MDR is an ideal solution because it provides a level of protection and expertise that would otherwise require building an in-house security operations center (SOC).
With OpenText MDR, SMBs get exactly this level of protection, backed by a trusted name in cybersecurity. Delivered through our extensive network of leading MSPs, OpenText MDR offers the power of an enterprise-grade SOC, helping SMBs fortify their defenses, protect their data, and stay operational no matter the time of day.
SMBs are turning to OpenText MDR for several key reasons that make a difference in their security approach:
1. 24/7/365 monitoring and threat response
Cyber threats don’t follow a 9-to-5 schedule—they’re more likely to strike after hours or on weekends, when in-house teams may be offline. That’s why around-the-clock protection is crucial.
Working together with your MSP, OpenText provides robust, continuous protection supported by a skilled team of security experts. This around-the-clock vigilance offers invaluable peace of mind, knowing that security professionals are actively monitoring and defending your infrastructure from evolving threats, day and night.
2. Fast incident response
In the face of a cyber-attack, every second matters, and a rapid response can mean the difference between a minor incident and a major disruption.
With dedicated analysts for investigation and escalation within 15 minutes, OpenText MDR collaborates seamlessly with your MSP to deliver rapid incident response within critical time frames. This swift action minimizes potential damage, safeguards business continuity, and helps companies avoid costly disruptions.
3. Meet regulatory compliance requirements
Compliance can be tough, especially for SMBs with limited resources. OpenText MDR makes it easier by helping businesses meet key standards like NIST, PCI, HIPAA, and SOC 2.
With built-in security controls, reporting, and documentation, OpenText helps protect customer data, reduce risks, and keep you clear of costly fines. Plus, it frees up your team to focus on running the business, knowing that OpenText MDR is supporting your compliance requirements.
4. Low total cost of ownership (TCO)
Building an in-house SOC requires a significant investment that goes beyond just the initial setup. The costs quickly add up when factoring in the specialized hardware, advanced software, and the need to recruit and retain highly skilled security professionals. For many SMBs, these expenses are simply out of reach, which makes it challenging to keep up with the level of protection needed to guard against sophisticated cyber threats.
OpenText MDR solves this by offering a fully managed or co-managed SOC-as-a-Service model through your MSP, which cuts down on costs by eliminating the need for an in-house infrastructure and dedicated security team. With OpenText MDR, businesses can optimize their security budget without sacrificing the level of protection that’s required to counteract today’s cyber threats.
5. Enhanced protection beyond endpoint security
SMBs are increasingly investing in endpoint security, which is a crucial first step. However, today’s sophisticated adversaries often bypass these initial defenses, making it critical to have more than endpoint security alone.
OpenText MDR enhances an organization’s existing endpoint protection by integrating AI-driven automation, SOAR workflows, and a turnkey cloud SIEM into the security environment. This enables active monitoring and protection across the attack surface, while automating threat response and accelerating remediation times. With OpenText MDR, businesses benefit from a comprehensive, streamlined security service that operates continuously, working smarter, faster, and more efficiently to safeguard against evolving threats.
6. Advanced threat intelligence and threat hunting
Cyber threats are constantly evolving, and OpenText MDR stays ahead with threat intelligence from over 35 sources worldwide. SMBs gain valuable insights into emerging threats and can protect their business with OpenText’s security experts conducting threat hunting to proactively identify and neutralize potential risks before they escalate. This intelligence-driven approach provides an essential security practice that gives businesses the edge to thwart sophisticated attacks.
Cyber-attacks can bring business operations to a grinding halt, leading to reputational damage and substantial financial loss. In this climate, having a trusted security partner like OpenText—a provider known for its reliable and innovative security solutions—is essential for businesses looking to stay secure, resilient, and prepared for whatever cyber threats may come their way.
Ready to protect your business with comprehensive, around-the-clock security?
Discover how OpenText MDR can safeguard your organization today.
Top 5 roadblocks for MSPs and how OpenText MDR clears the way
The managed service provider (MSP) industry is booming with opportunities. At the same time, MSPs face the challenge of balancing customer satisfaction with profitability, making strategic decisions more important than ever. For 35% of MSPs, building cyber resiliency for customers is a top strategic priority, but that goal often runs up against resource constraints and rising operational costs.[i] To stay competitive, MSPs are focusing on improving operational efficiency (35%) and keeping costs under control (33%).[ii]
One of the smartest ways to tackle these strategic goals is by partnering with OpenText to deliver managed detection and response (MDR) services. This partnership empowers MSPs to offer a cutting-edge, fully managed detection and response service, taking the weight off operational costs and simplifying the complexity of building and managing an in-house MDR solution.
Here are five ways OpenText MDR helps MSPs overcome their biggest challenges:
1. Filling the security staff resource and skills gap
Staffing can be a perpetual challenge for MSPs, particularly when it comes to hiring and retaining skilled cybersecurity professionals. With a global shortage of 4.8 million cybersecurity experts, this issue is only becoming more pressing. MSPs feel the strain in several key areas, including:
- Managing an overwhelming volume of alerts with a limited team
- Cultivating the advanced skills needed to thoroughly investigate and prioritize threats
- Attracting and retaining top security talent to close skills gaps and support business growth
OpenText MDR tackles this challenge for MSPs head-on by providing you with a fully managed or co-managed MDR partnership. With OpenText MDR, MSPs can access 24/7/365 security expertise and continuous threat monitoring without the cost or complexity of building an in-house SOC. This not only eases the pressure on your internal teams but ensures a high-level of security coverage for your customers at all times.
2. Streamlining alert management
Detecting advanced threats requires a sophisticated approach to monitoring a customer’s attack surface. This is where SIEMs come in—essential for correlating data and identifying threats. However, SIEMs can be complex to configure, manage, and tune, which can lead to a high volume of false positives. For MSPs with limited resources, this flood of irrelevant alerts can overwhelm teams and drain operational efficiency.
OpenText MDR solves this by leveraging advanced threat intelligence to correlate security logs and reduce false positives, all while managing the SIEM and monitoring alerts for you. By continuously prioritizing critical threats, our experts handle the complexity of alert management, allowing MSPs to focus on what matters most—securing their customers—without the burden of filtering through a flood of false alarms.
3. Accelerating incident response
With a flood of alerts constantly coming in and the need to pivot between multiple consoles to investigate, MSP security teams often struggle with slow, time-consuming incident response. The pressure to act quickly is high, as swift action is essential to prevent the disastrous outcomes of a breach. However, many teams find themselves bogged down, bouncing between disparate tools and struggling to identify and respond to threats in real-time.
OpenText MDR addresses this challenge with fast, proactive monitoring and continuous threat hunting to detect suspicious activity early. Our dedicated experts streamline incident response by quickly identifying threats and escalating them within 15 minutes, ensuring MSPs can act fast and minimize the impact of potential breaches.
4. Simplifying security management across complex environments
Managing a customer’s complex environment can be challenging for MSPs. With diverse security tools, large volumes of data, and multi-environment deployments, the complexity of managing each unique environment can overwhelm MSP teams, stretching resources thin and hindering effective security management. Delivering cybersecurity services that support your diverse customer environments requires a solution that integrates seamlessly and simplifies management without adding to the burden.
OpenText MDR makes it easy to support your customer environments by offering a fully integrated solution that seamlessly supports your MSP partner and tools ecosystem. With AI-driven automation, OpenText MDR processes vast amounts of data quickly, integrating effortlessly with over 500 tools and services. Its lightweight agent ensures easy deployment across multiple environments, providing end-to-end visibility through a single dashboard. This not only streamlines security management but also helps MSPs leverage their existing investments while benefiting from expert human analysts guiding the process.
5. Driving revenue growth without barriers to entry
For MSPs, staying competitive and standing out in your region requires offering innovative solutions that meet customer needs without the complexity and barriers often associated with new vendor partnerships. Having an MDR offering can be a key driver for growth, but the challenge lies in finding an MDR vendor that has both a cutting-edge solution and flexible licensing, without the constraints of long-term contracts or rigid terms.
OpenText MDR addresses this by offering a subscription-based model with no minimum contract, making it easy to integrate into your existing service offerings. MSPs can access additional services like penetration testing, vulnerability management, and custom incident response plans as needed, with simple, integrated billing through OpenText’s Secure Cloud Platform. This flexibility allows you to scale your MSPs cybersecurity services as your business grows.
Discover how OpenText MDR can empower your MSP to overcome challenges and drive growth.

















