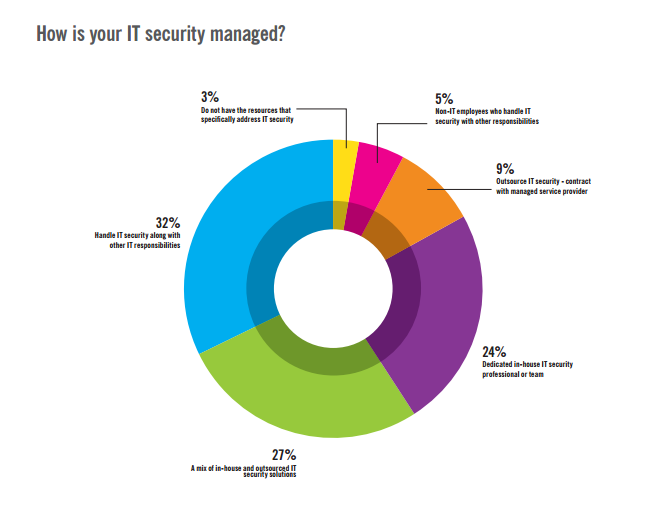
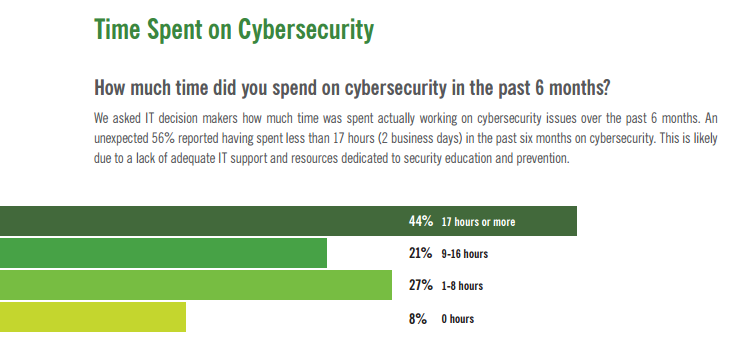
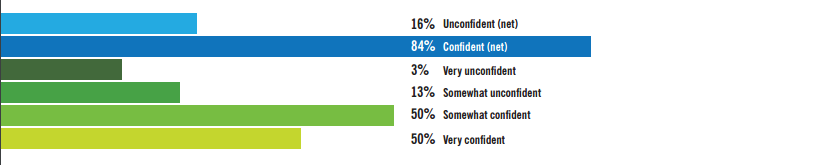
On Monday of this week, Webroot joined Cloudera, the leading provider of modern data management and analytics systems built on Apache Hadoop, in announcing Open Network Insight (ONI) Project, a database and tools designed specifically for cyber security incident response. ONI will enable security analysts and responders to manipulate the massive amounts of data generated within an enterprise to isolate and investigate both internal and external threats. And because we have years of endpoint-to-cloud experience here at Webroot, we will participate in the project by helping to design the data models for endpoint data.
ONI matches our own Webroot vision of security being an information problem. If you can apply the right data at the right time to decide if you’re being attacked or infiltrated, you can defend yourself. Our SecureAnywhere products put this vision into action by applying massive threat intelligence in the cloud to defeat potential threats on our customers’ desktops and smartphones. ONI will enable an organization to bring together all the relevant data about their network, their users, and their devices in one massive, but easily manipulated database, so they can find and defeat attacks.
Hadoop has been growing rapidly in popularity within the cyber security community, being used in building very large-scale databases of security intelligence data such as network logs, event data, and other data types needed by security analysts. Hadoop combines power, speed, and flexibility, which are the hallmarks of a good data platform. Cloudera has extended the open source base with Cloudera Enterprise, a portfolio of tools to create, manage and analyze large scale databases.
The initial prototype of ONI was created by data scientists at Intel. They created a database which is updated with more than 20 billion network events per day within the Intel corporate network. Then, using proprietary and open source visualization tools, they created a security workbench which allows them to identify and investigate potential threats.
Webroot is excited to be part of Open Network Insight, and excited to be working with Cloudera and Intel to bring this vision to reality. We will update the Blog with our progress.