Despite the intent of ensuring safe transit of information to and from a trusted website, encrypted protocols (usually HTTPS) do little to validate that the content of certified websites is safe.
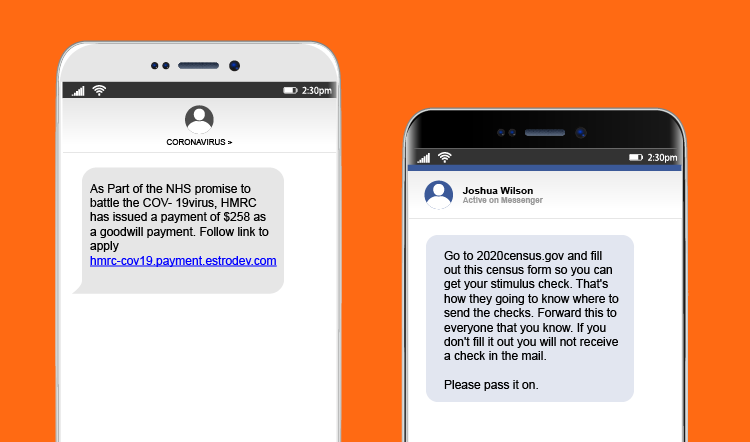
With the widespread usage of HTTPS protocols on major websites, network and security devices relying on interception of user traffic to apply filtering policies have lost visibility into page-level traffic. Cybercriminals can take advantage of this encryption to hide malicious content on secure connections, leaving users vulnerable to visiting malicious URLs within supposedly benign domains.
This limited visibility affects network devices that are unable to implement SSL/TLS decrypt functionality due to limited resources, cost, and capabilities. These devices are typically meant for home or small business use, but are also found in the enterprise arena, meaning the impact of this limited visibility can be widespread.
With 25% of malicious URLs identified by Webroot hosted within benign domains in 2019, a deeper view into underlying URLs is necessary to provide additional context to make better, more informed decisions when the exact URL path isn’t available.
Digging Deeper with Advanced Threat Intel
The BrightCloud® Web Classification and Web Reputation Services offers technology providers the most effective way to supplement domain-level visibility. Using cloud-based analytics and machine learning with more than 10 years of real-world refinement, BrightCloud® Threat Intelligence services have classified more than 842 million domains and 37 billion URLs to-date and can generate a predictive risk score for every domain on the internet.
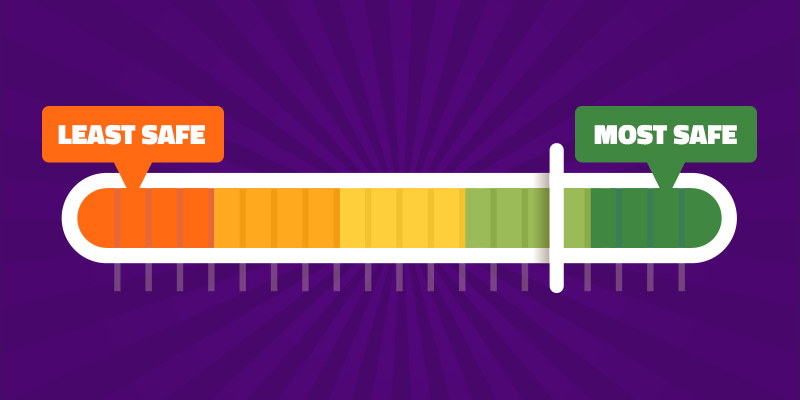
The Domain Safety Score, available as a premium feature with BrightCloud® Web Classification and Reputation services, can be a valuable metric for filtering decisions when there is lack of path-level visibility on websites using HTTPs protocols. Even technology partners who do have path-level visibility can benefit from using the Domain Safety Score to avoid the complexity and compliance hurdles of deciding when to decrypt user traffic.
The Domain Safety Score is available for every domain and represents the estimated safety of the content found within that domain, ranging from 1 to 100, with 1 being the least safe. A domain with a low score has a higher predictive risk of having content within its pages that could compromise the security of users and systems, such as phishing forms or malicious downloads.
Using these services, organizations can implement and enforce effective web policies that protect users against web threats, whether encrypted through HTTPs or not.
Devising Domain Safety Scores
As mentioned, a Domain Safety Score represents the estimated safety of the content found within that domain. This enables better security filtering decisions for devices with minimal page-level visibility due to increasing adoption of HTTPS encryption.
How do we do it?
BrightCloud uses high-level input features to help determine Domain Safety Scores, including:
- Domain attribute data, including publicly available information associated with the domain, such as registry information, certificate information, IP address information, and the domain name itself.
- Behavioral features obtained from historical records of known communication events with the domain, gathered from real-world endpoints.
- A novel deep-learning architecture employing multiple deep, recurrent neural networks to extract sequence information, feeding them into a classification network that is fully differentiable. This allows us to use the most cutting-edge technology to leverage as much information possible from a domain to determine a safety score.
- Model training using a standard backpropagation through time algorithm, fully unrolling all sequences to calculate gradients. In order to train such a network on a huge dataset, we have developed a custom framework that optimizes the memory footprint to run efficiently on GPU resources in a supercomputing cluster. This approach allows us to train models faster and iterate quickly so we can remain responsive and adapt to large changes in the threat landscape over time.
A secure connection doesn’t have to compromise your privacy. That’s why Webroot’s Domain Safety Scores peek below the domain level to the places where up to a quarter of online threats lurk.
Learn more about Domain Safety Scores, here.