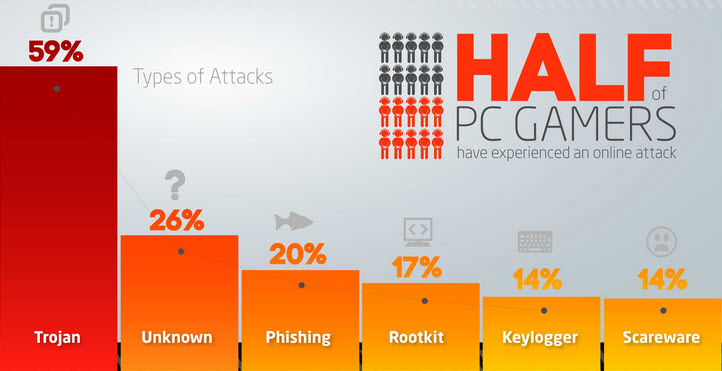
Yesterday, the New York Times published an exclusive story on what many are stating to be the largest series of hacks ever, all revealed by Hold Security in their latest report. With a report of over 1.2 billion unique username-password combinations and over 500 million e-mail addressed amassed by a Russian hacker group dubbed CyberVol (vol is Russian for thief). While the reactions among the security industry are mixed, with some researchers raising a few questions of the masterwork behind the hack, the story does bring to the public’s attention the necessity of strong, personal, online security policies for all aspects of the connected life.
As our researchers have shown in the past, gathering a collection of username and passwords can be easier than many think, with many scraping programs being sold on the deep-web market to the highest bidders. And while some companies, including Hold Security, are offering paid solutions to help detect and monitor if their accounts have been breached, this does not change the fact that the first layer of security begins at the user.
8 tips to help you stay safe and secure on the internet
- Use two-factor authentication whenever possible. Two-factor authentication adds another layer of security when logging into a website, be it e-mail, banking, or other websites. Some websites, such as Google, will text you a code when you login to verify your identity, while others have small devices that you can carry around to generate the code. Authenticator apps are also available on all major smartphone platforms. Other types of two-factor authentication do exist as well, so look in the settings of your banking, shopping, and e-mail hosts for the option.
- Signup for login notifications. This security layer is often used in place of two-factor authentication, including by websites such as Facebook. If your account is accessed from an unfamiliar location, a notification is sent via e-mail, app, or text-message to the account holder. This is a great layer of security that offers you on-the-go protection. This feature, if offered, can usually be found in the security settings of the website, such as banking and social media, you are accessing.
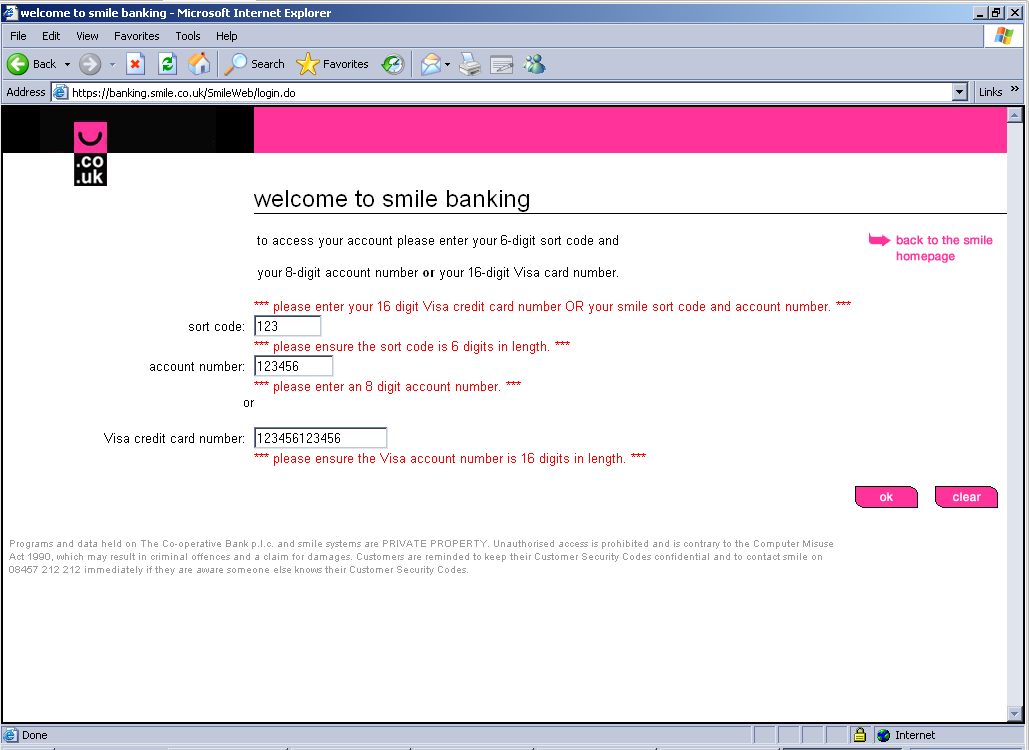
- Use a secure password. We have all signed up for some website with a basic password, thinking there is no way that someone would want to hack our account. But that may not be the case. Setting an easy password on one website often leads to that password being used across many websites. The easier you make it for a thief to brute-force access your account, the more likely you are to have your other accounts hacked. By establishing a mixture of characters, numbers, and letters into a password, recommended to be 10 characters or more, you add a high level of difficulty for any brute-force password theft. Password managers like the one included in our Internet Security Plus and Complete antivirus programs can help make managing this easier.
- Change your passwords regularly. There is a reason your office requires regular password changes for your e-mail. Even if your password is compromised, by changing it regularly across all your accounts, you remove the chance of your account being accessed. A pro-tip would be to set a reminder for every 90 days on your calendar with a link to all your accounts settings pages. It makes it easiest to click through and make the changes regularly.
- Only access your accounts from secure locations. It might only be 30 seconds of access to your bank account on that free WiFi at the coffee shop, but if the network has been compromised, that is more than enough time to collect all the data needed for a thief. While the convenience factor is there, if you must access the accounts, you might want to look into a VPN (Virtual Private Network) to ensure an encrypted connection to your home or work network.
- HTTPS access. In most browsers and information heavy websites, there is a way to force a HTTPS connection when available. This connection adds another level of encrypted security when logging in, making it even more difficult for data thieves to gather your information when logging in. To check if you are on a HTTPS connection, look for a padlock in the URL bar in the browser or check the URL itself for it to begin with HTTPS.
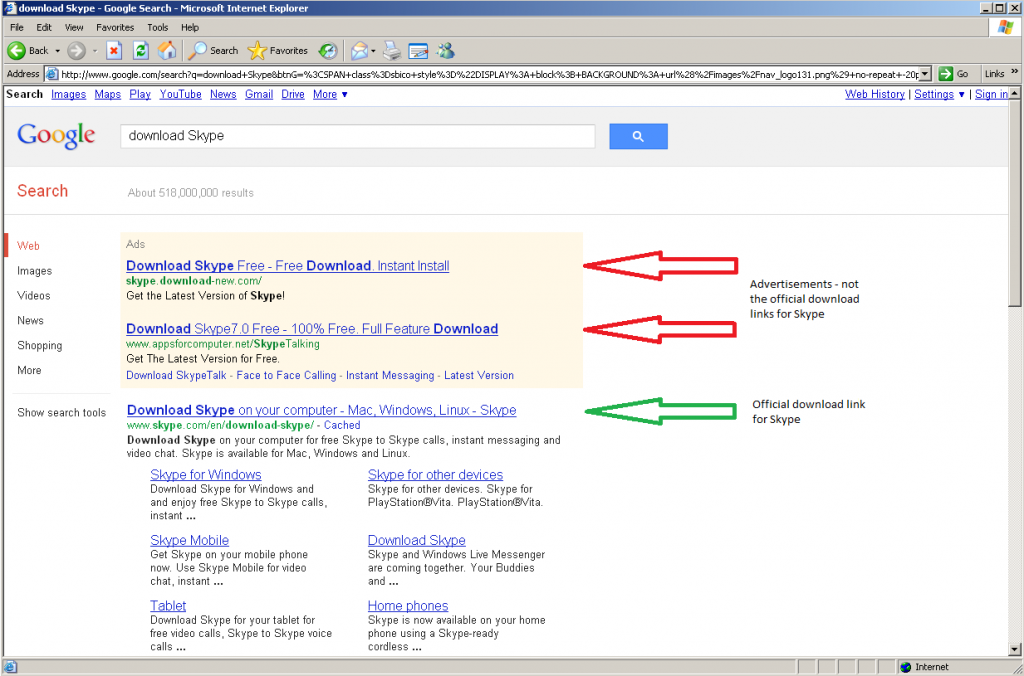
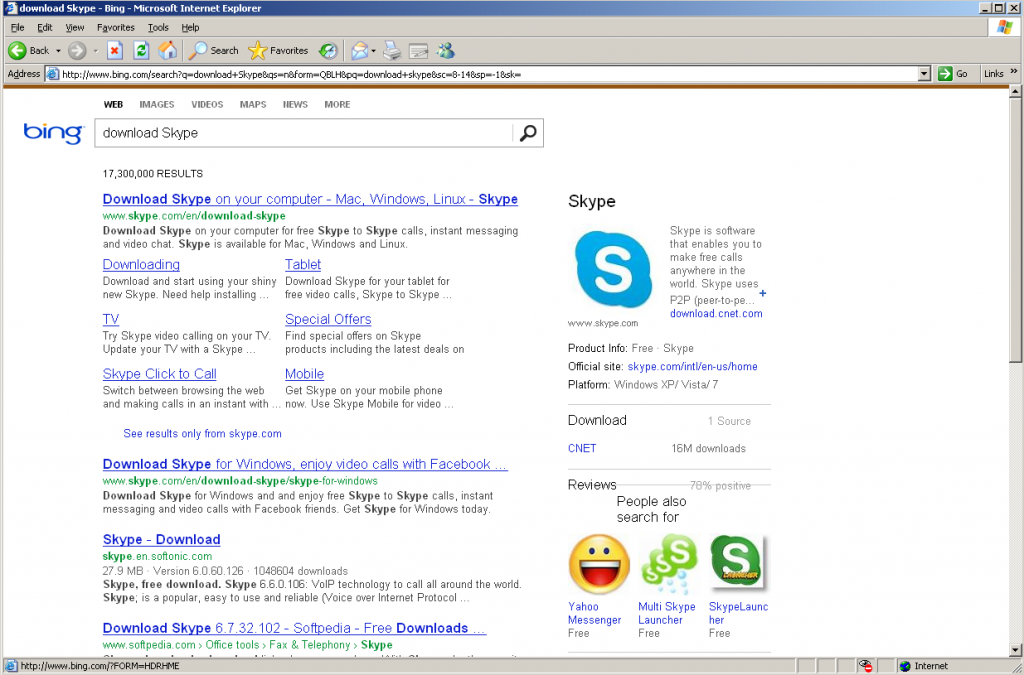
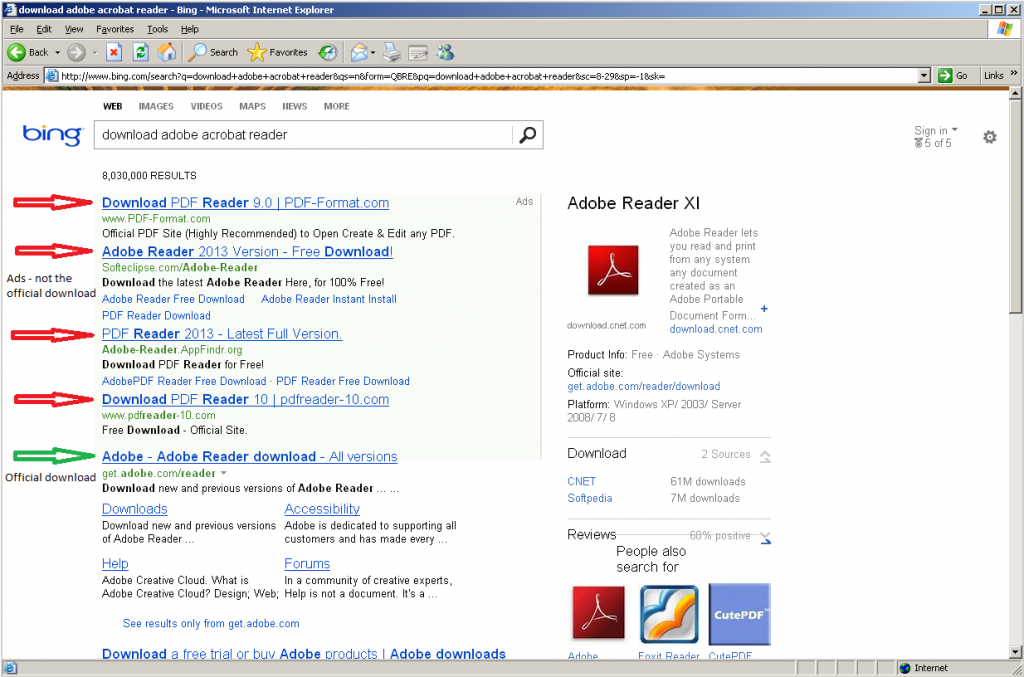
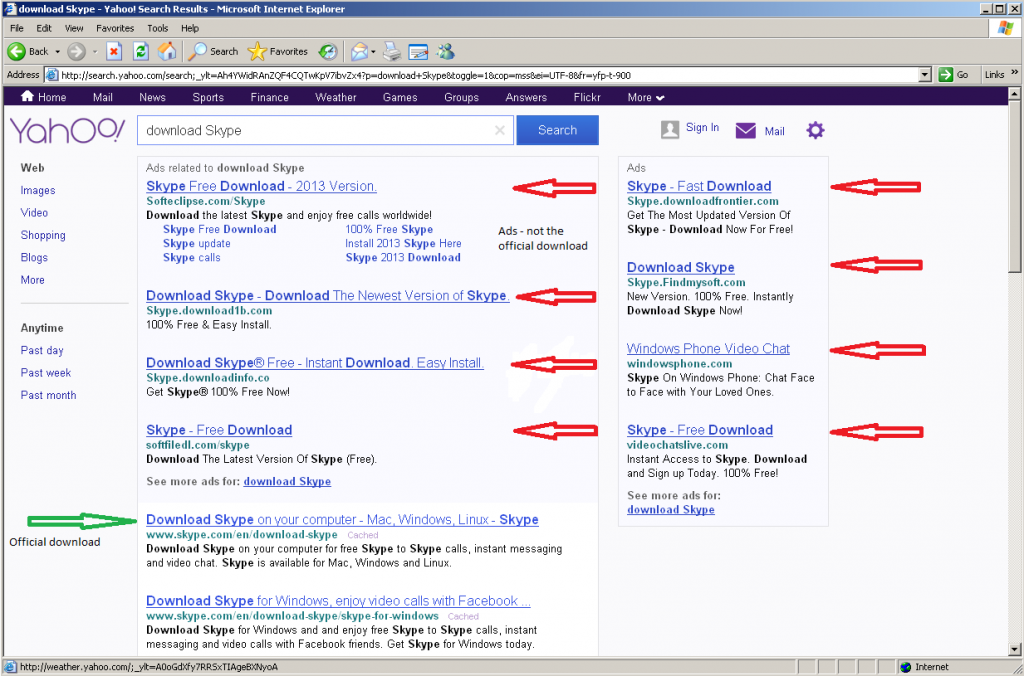
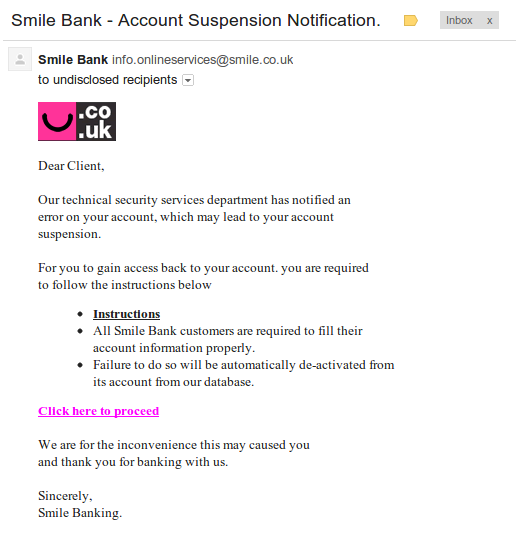
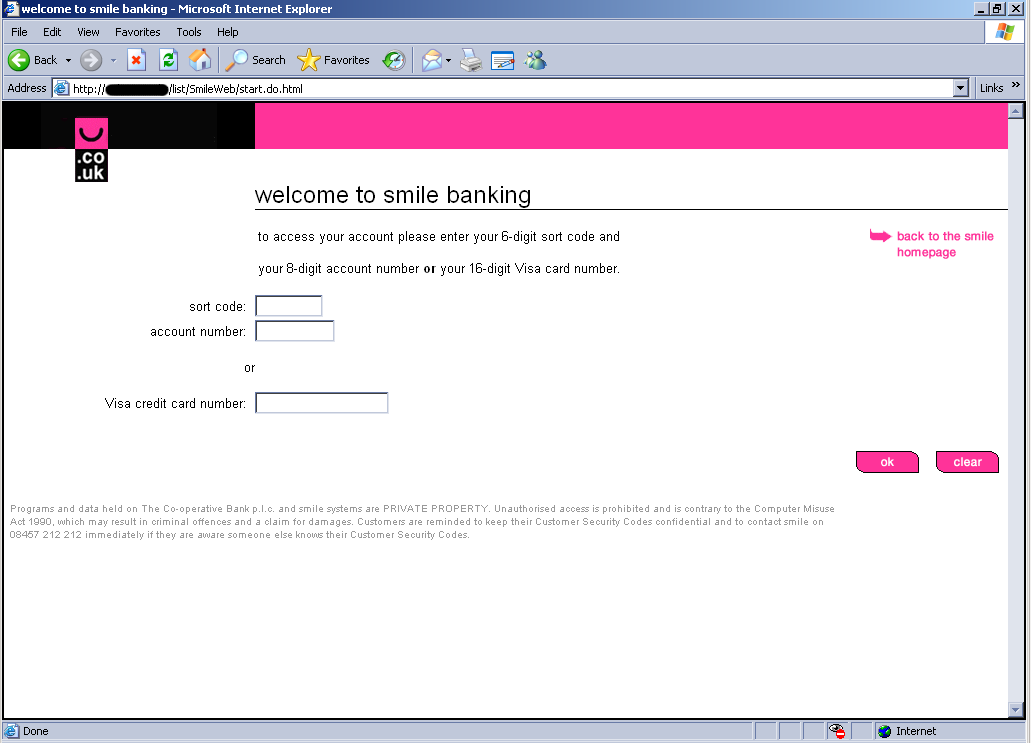
- Increase junk filtering and avoid clicking through on e-mails. You just received an e-mail letting you know that you have a new deposit pending and need to login and verify. Many phishing schemes start with something looking very innocent and official, but lead unassuming users to websites designed to collect the information direct from you. If you receive an e-mail from one of the account-holding websites, open a new tab and go direct to the website instead of clicking the links provided. It adds only a few seconds to the access, but keeps you out of any legit-looking phishing websites. Most legitimate services will never ask you for your login credentials, so make sure to avoid giving out this information. By increasing your level of junk filtering with your e-mail client as well, many of these e-mails will be caught before making it to your inbox.
- Use an up-to-date security program. Ensure you have the most up-to-date version and have the correct security settings enabled. Security AV programs are designed to keep the malicious files such as keyloggers and data-miners off your computer and the user protected. This direct layer of security ensures your devices, from phones to tablets to computers, are all protected when you are downloading and accessing files. Note that some programs, such as Webroot SecureAnywhere, are always up-to-date and require no further action from the user.
While the threats to online accounts are out there, the tips to staying safe can help you stay protected and utilize features often already available by the companies and their websites, and most without costing you additional money. These internet safety tips should help ensure your security online while still providing the convenience online access offers.
Helpful links:
- Google Security: https://www.google.com/settings/security
- Facebook Security: https://www.facebook.com/help/securitytips
- Twitter Security: https://support.twitter.com/articles/76036-safe-tweeting-the-basics
- Secure Password Generator: http://passwordsgenerator.net/
- Google Chrome Security Settings: https://support.google.com/chrome/answer/114836?hl=en
- Firefox Security Settings: https://support.mozilla.org/en-US/products/firefox/privacy-and-security
- Internet Explorer Security Settings: http://windows.microsoft.com/en-us/windows/change-internet-explorer-security-settings#1TC=windows-7
- Microsoft Outlook Two-step authentication: http://windows.microsoft.com/en-us/windows/two-step-verification-faq
- Google Two-Step authentication: https://support.google.com/a/answer/175197?hl=en








































 E3
E3