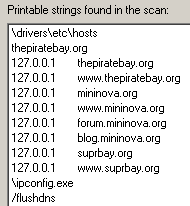
Yesterday, two different 0 day exploits against Internet Explorer were published, just in time for the holidays when most of you (and many security researchers as well) are taking time off from work. The exploit, named CVE-2010-3971, is fairly serious, affecting the latest builds of IE versions 6 through 8.
Yesterday, two different 0 day exploits against Internet Explorer were published, just in time for the holidays when most of you (and many security researchers as well) are taking time off from work. The exploit, named CVE-2010-3971, is fairly serious, affecting the latest builds of IE versions 6 through 8.
Well, I’d normally get all hot and bothered about the fact that this kind of event might force some of our research team to spend their precious vacation time working the problem and coming up with a comprehensive solution. Normally, but not this time.
This time we headed the Black Hats off at the pass, and put a stop to these shenanigans before they started. Word from the Webroot Web Security Service team — the builders of our very slick cloud protection service for businesses — is that their Javascript heuristics engine is able to block any Web page that’s trying to use the exploits to try to take over your computer. The screenshot above shows what happened when we tried to browse to the proof-of-concept exploit page on a machine protected by the Web Security Service.
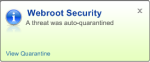 Of course, that’s great for corporate folks, but what about our home users running Webroot Antivirus or Internet Security Essentials or Complete? Well, we block it there, too. If you happened to stumble upon a Web page with the exploit running inside it, you might see a popup like the screenshot here, which is just telling you that we’ve prevented the page containing the exploit from loading in your browser. For the people playing at home, please ensure that you’re running the latest version of your antivirus with the most current updates, with the File System Shield and the Execution Shield turned on (and turn Gamer Mode off while you’re surfing).
Of course, that’s great for corporate folks, but what about our home users running Webroot Antivirus or Internet Security Essentials or Complete? Well, we block it there, too. If you happened to stumble upon a Web page with the exploit running inside it, you might see a popup like the screenshot here, which is just telling you that we’ve prevented the page containing the exploit from loading in your browser. For the people playing at home, please ensure that you’re running the latest version of your antivirus with the most current updates, with the File System Shield and the Execution Shield turned on (and turn Gamer Mode off while you’re surfing).
So, tough luck exploit writer guys. Better luck next time. I know someone is getting a bigger lump of coal than usual in his stocking this year, and I can’t think of anybody who deserves it more.