
by Blog Staff | Oct 18, 2013 | Industry Intel, Threat Lab
At Webroot’s Threat Blog, we often discuss the dynamics of the cybercrime ecosystem. Through the prism of basic business, marketing and economic theories, the idea is to help make them easy to comprehend by most readers. Constructively raising awareness on some of the driving factors behind the epidemic growth of cybercrime. We also often emphasize on concepts such as standardization, vertical integration, for hire, rent or on demand business models, commoditization and economies of scale. This further highlights the legitimate market-like state of the underground marketplace, in terms of the variety of business models, pricing schemes, and current/long term centered business strategies.
In this post, we’ll put the spotlight on an efficiency-centered administration panel for a DIY (do it yourself), self-service type of E-shop script, to be used by prospective cybercriminals as a turn-key conversion solution for their fraudulently obtained assets. In this case, the ability to efficiently sell access to compromised accounts. Not only has this E-shop script have the potential to empower virtually anyone with the ability to sell their goods, but in this particular case, the vendor is promising to donate some of the revenue for philanthropic purposes.
(more…)

by Blog Staff | Oct 18, 2013 | Industry Intel, Threat Lab
Potentially Unwanted Applications (PUAs) continue to visually social engineer users into installing virtually useless applications. They monetize each and every install by relying on ‘bundling’ which often comes in the form of a privacy-violating toolbar or third-party application. We recently intercepted a rogue ad that entices users into downloading the Mipony Download Accelerator that is bundled with the privacy-invading FunMoods toolbar PUA, an unnecessary bargain with the integrity and confidentiality of your PC.
(more…)

by Blog Staff | Oct 17, 2013 | Industry Intel, Threat Lab
We’ve intercepted an ongoing malicious campaign, relying on injected/embedded iFrames at Web sites acting as intermediaries for a successful client-side exploits to take place. Let’s dissect the campaign, expose the malicious domains portfolio/infrastructure it relies on, as well as directly connect it with historical malicious activity, in this particular case, a social engineering campaign pushing fake browser updates.
(more…)

by Blog Staff | Oct 16, 2013 | Industry Intel, Threat Lab
Think someone forwarded you an important attachment? Think twice. Cybercriminals are currently mass mailing tens of thousands of malicious emails attempting to trick the recipient into thinking that someone has forwarded a file to them. In reality, once socially engineered users execute the malicious attachments, their PCs automatically become part of the botnet operated by the cybercriminals behind the campaign, allowing them to gain complete control over the affected PCs, and consequently abuse the access for related fraudulent purposes.
(more…)

by Blog Staff | Oct 16, 2013 | Industry Intel, Threat Lab
The never-ending supply of access to compromised/hacked PCs — the direct result of the general availability of DIY/cracked/leaked malware/botnet generating tools — continues to grow in terms of the number and variety of such type of underground market propositions. With more cybercriminals entering this lucrative market segment, on their way to apply well proven and efficient monetization schemes to these hacked PCs, cybercrime-friendly affiliate networks naturally capitalize on the momentum, ensuring a win-win business process for the participants and the actual owners of the network.
In this post, I’ll highlight yet another newly launched such E-shop, currently possessing access to over 30,000 malware-infected hosts.
(more…)

by Blog Staff | Oct 14, 2013 | Industry Intel, Threat Lab
The cybercriminals behind last week’s profiled fake T-Mobile themed email campaign have resumed operations, and have just spamvertised another round of tens of thousands of malicious emails impersonating the company, in order to trick its customers into executing the malicious attachment, which in this case is once again supposedly a legitimate MMS notification message.
(more…)

by Blog Staff | Oct 11, 2013 | Industry Intel, Threat Lab
With the increased public availability of leaked/cracked DIY malware/botnet generating tools, cybercriminals continue practically generating new botnets on the fly, in order to monetize the process by offering access to these very same botnets at a later stage in the botnet generation process. In addition to monetizing the actual process of setting up and hosting the botnet’s C&C (command and control) servers, novice cybercriminals continue selling direct access to their newly generated botnets, empowering other novice cybercriminals with the foundations for further disseminating and later on monetizing other pieces of malicious software, part of their own arsenal of fraudulent/malicious tools.
Let’s discuss one such sample service run by novice cybercriminals, once again targeting cybercriminals, that’s selling direct access to mini botnets generated using what appears to be a cracked version of a popular DIY malware/botnet generating kit, and emphasize on the service’s potential in the broader context of today’s highly professionalized cybercrime ecosystem.
(more…)

by Marcus Moreno | Oct 10, 2013 | Industry Intel, Threat Lab
In this episode of the ThreatVlog, Marcus talks about the DNS hijack that took down a slew of popular websites, including WhatsApp, AVG, and Avira. These accounts were all compromised through one simple phishing scheme going after the Network Solutions accounts. Marcus also discusses the basics of the Adobe hack.
http://youtu.be/QIPX4r3NygQ

by Blog Staff | Oct 10, 2013 | Industry Intel, Threat Lab
Our sensors just picked up an interesting Web site infection, this time affecting a Web server belonging to the Turkish government, where the cybercriminals behind the campaign have uploaded a malware-serving fake ‘DivX plug-in Required!” Facebook-themed Web page. Once socially engineered users execute the malware variant, their PCs automatically join the botnet operated by the cybercriminals behind the campaign.
(more…)

by Blog Staff | Oct 9, 2013 | Industry Intel, Threat Lab
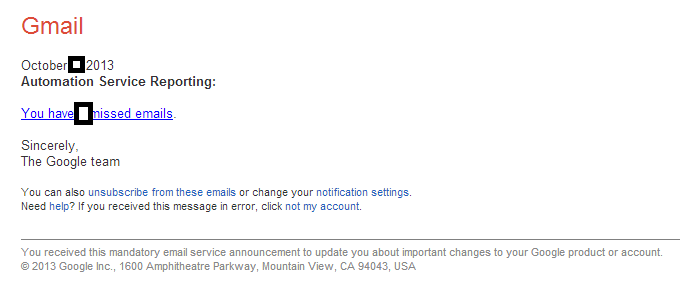
Pharmaceutical scammers are currently mass mailing tens of thousands of fake emails, impersonating Google’s GMail in an attempt to trick its users into clicking on the links found in the spamvertised emails. Once users click on them, they’re automatically exposed to counterfeit pharmaceutical items, with the scammers behind the campaign attempting to capitalize on the ‘impulsive purchase’ type of social engineering tactic typical for this kind of campaign.
Sample screenshot of the spamvertised email:
Sample screenshot of the landing pharmacautical scams page:
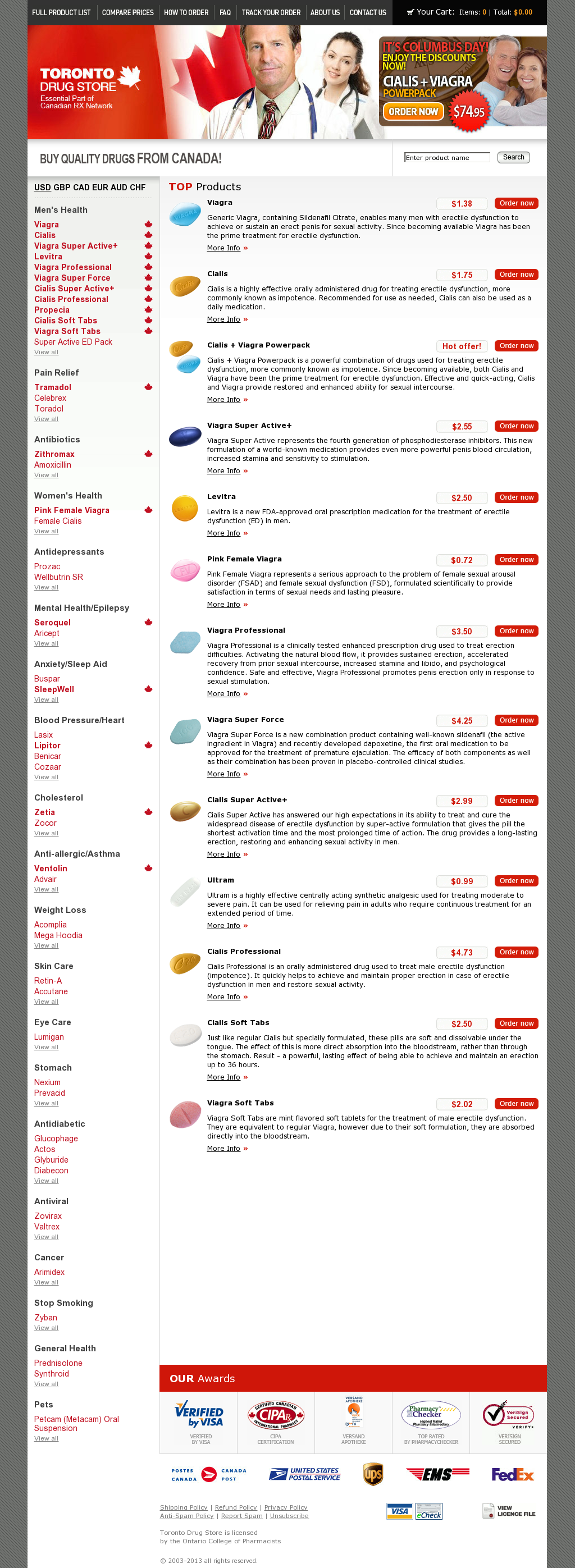
Landing URL: shirazrx.com – 85.95.236.188 – Email: ganzhorn@shirazrx.com
The following pharmaceutical scam domains also respond to the same IP:
asqrtplc.com
pharmlevitrafitch.com
myprescriptionhealth.com
viagrasequester.com
rxjeanstra.at
medoverdose.at
rxtreatments.ru
The following pharmaceutical scam domains are also known to have responded to the same IP (85.95.236.188):
albertapharm.com
albertapharm.net
antacid.fatwelnessdiet.com
anticlockwise.medwelopioid.com
antiquarianism.medwelopioid.com
assignment.healthcareviagrabiotech.com
canadaprescriptioninc.at
carburettors.opioidsalemeds.com
debars.dentalcarepharmacy.com
deliquescent.homemedicalrx.com
dipoles.fatdietpharm.com
drughealthcareprescription.com
drugstoreabortion.com
drugstorepharmetro.com
heads.fatpillsdiet.com
hebalk.ru
herbalviagrasildenafil.com
inflammatory.patientsprescriptionmedical.com
levitrachrome.at
levitrapillkorsinsky.com
This isn’t the first, and definitely not the last time pharmaceutical scammers brand-jack reputable brands in order to trick users into clicking on the links found in the fake emails, as we’ve already seen them brand-jack Facebook’s Notification System, YouTube, as well as the non-existent Google Pharmacy. Thanks to the (natural) existence of affiliate networks for pharmaceutical items, we expect that users will continue falling victim to these pseudo-bargain deals, fueling the the growth of the cybercrime economy and the need for more cybersecurity awareness.
Our advice? Never bargain with your health, spot the scam and report it.








