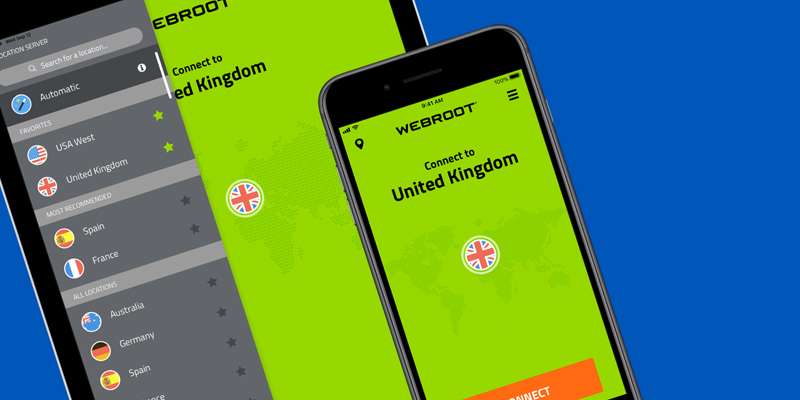
Virtual Private Networks (VPNs) are quickly becoming a fundamental necessity for staying safe online. From large corporations to family households, people are turning to VPNs to ensure their data is encrypted end to end. But as with any emerging technology, it’s easy to become overwhelmed with new and untested VPN options. So, how does Webroot® WiFi Security distinguish itself from other VPNs?
Whether or not you can trust your VPN provider should be the first thing to consider when selecting a VPN. A recent analysis of nearly 300 mobile VPN services on the Google Play store found that, unlike Webroot WiFi Security, almost one in five didn’t encrypt data as it was transmitted through their private network, a core tenant of VPN protection. At Webroot we have decades of cybersecurity experience. We’ve built confidence with every customer, from the world’s leading IT security vendors to families just like yours. Security and privacy are what we do best, and Webroot WiFi Security was purpose-built to always encrypt your data without screening, storing, or selling your private information.
“New products from unknown companies can be risky—what data are they capturing, what are they doing with the data, and how are they protecting that information?” notes Andy Mallinger, Webroot director of product. “Webroot has been in the security business for more than 20 years, and has built machine learning-based security systems for more than a decade. We designed our products to evolve with the ever-changing threat landscape. Adding VPN protection with Webroot WiFi Security, is a perfect next step in our continued evolution.”
Best-in-class security
Webroot WiFi Security was built to provide best-in-class security, while still being easy to use. A one-click setup automatically enables security features without any confusion or missed steps. For extra security, Android®, Mac®, and Windows® users can enable Webroot WiFi Security’s unique “killswitch” feature. If your VPN connection is lost, the kill switch prevents the transmission of your data over an unsecure network until you are reconnected to the VPN.
“Webroot WiFi Security also helps protect your privacy by obscuring your location,” says Randy Abrams, senior security analyst at Webroot. “Websites are able to precisely pinpoint your location and use that information to track your browsing habits. With Webroot WiFi Security, you can be in Broomfield, Colorado, but your VPN IP address can make it look like you are in any one of the more than 30 countries where our VPN servers are located.”
Privacy plus security
Webroot WiFi Security also offers Web Filtering powered by BrightCloud® Threat Intelligence*. This feature provides an extra layer of protection that keeps your financial information, passwords, and personal files from being exploited. Webroot goes a step above other VPNs by safeguarding users from visiting malicious or risky websites known to be associated with malware, phishing, key logging spyware, and botnets. Web Filtering is a feature that the user can choose to enable or disable.
The combination of consumer trust and the power of best-in-class threat intelligence makes Webroot WiFi Security one of the most unique and secure VPN offerings on the market. Webroot has a deep history of protecting its customers’ privacy, and we are excited to showcase this dedication in the VPN market.
Ready to make the switch to Webroot WiFi Security? Learn more after the jump.
*The BrightCloud Web Filtering feature is only available on Windows®, Mac®, and Android® systems.