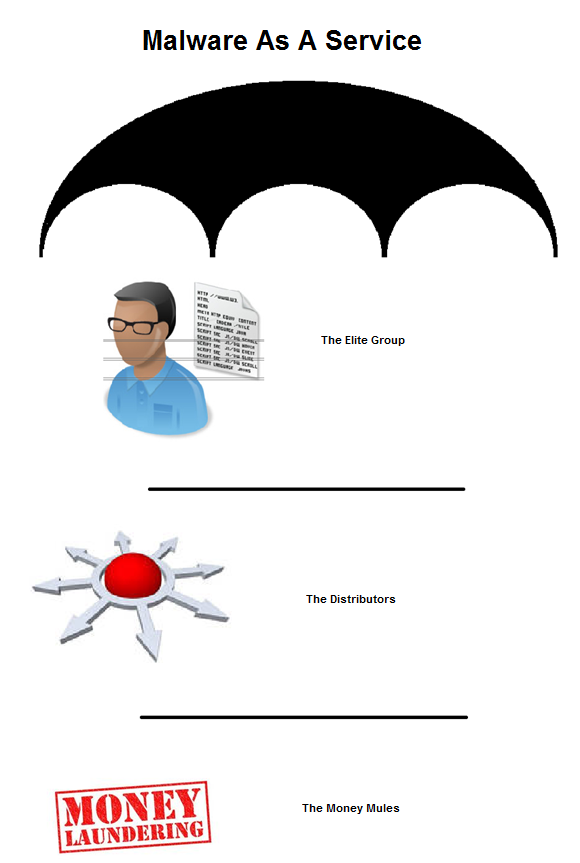
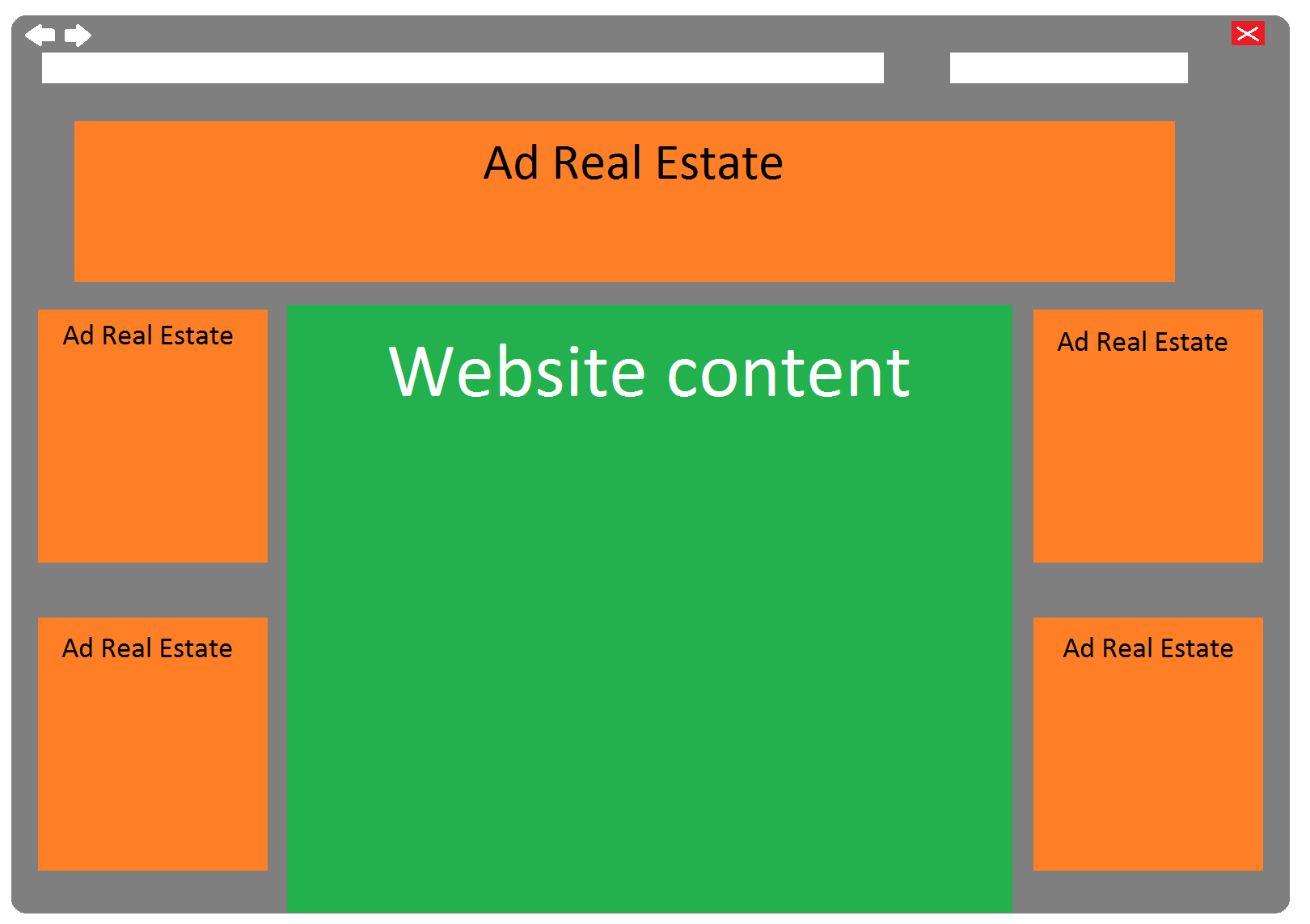
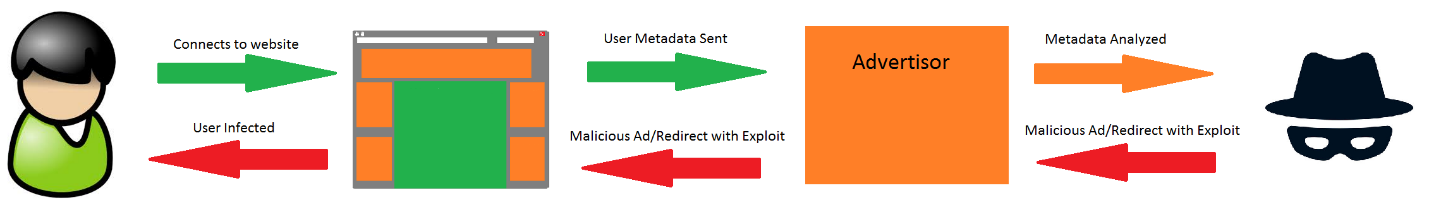
A lot happens in the security world and many stories get lost in the mix. In an effort to keep our readers informed and updated, we present the Webroot Threat Recap, highlighting 5 major security news stories of the week.
Credit Card Breach at Trump Hotels
It has recently been reported that the Trump Hotel chains have been the target of yet another credit card breach, which is currently affecting several locations around the world. This comes less than a year after their last report of suspicious payment activity, in which they confirmed their systems had been hit with info-stealing malware.
http://krebsonsecurity.com/2016/04/sources-trump-hotels-breached-again/
Panama Papers Released
In what is currently considered to be the largest data leak in history (containing over 2.6 TB of information), a laundry list of celebrities and major political figures have been tied to offshore bank accounts. While having an offshore corporation is perfectly legal, many of those listed were using tax havens to hide their considerable wealth by using an offshore law firm, Mossack Fonseca, to manage their funds.
http://www.theguardian.com/news/2016/apr/03/what-you-need-to-know-about-the-panama-papers
Updating Passwords Occurs Less Among IT Admins
Most people understand the importance of changing passwords for sensitive accounts regularly, but those who often recommend these changes are at times ending up as the worst offenders. In a recent survey, IT Admins were shown to insist users change their credentials more often than they changed the credentials themselves. Furthermore, an astounding 10% of IT Admins admitted to having never changed the administrative credentials used in their organizations.
Visa Database Potential Identity Risk
In the past week, an internal study conducted by the U.S. State Dept. revealed vulnerabilities in the visa application database, which contains hundreds of millions of confidential personal records. Currently, there has been no indication of a breach, but work is being done to seek out any vulnerabilities that haven’t already been resolved. Many of the issues they’re facing are related to aging technical systems and lack of upgrades.
LA Times Confirms their Site was Hacked
On Wednesday, it was reported that someone was able to access the LA Times website using a vulnerability in WordPress, and was offering this access for purchase. According to the LA Times, the security flaw has been resolved and they have added additional security precautions to prevent future breaches.