A Look at PC Gamer Security

In the new study on security and PC gamers, Webroot found that many gamers sacrifice their protection to maximize system performance and leave themselves vulnerable to phishing attacks and gaming-focused malware. The study also provides tips for protecting gaming credentials and safeguarding against phishing attacks.
Webroot PC Gamer Security Study Findings:
- 47% experienced an online attack with 55% of the attacks impacting system performance.
- 35% of PC gamers choose not to use security or rely on free clean-up tools.
- “Does not slow down system performance” ranked among the most important security program characteristic to gamers and Webroot has the first antivirus for PC gamers without system impact.
- Trojans, Phishing, and Rootkits ranked as the top attacks against PC gamers.
- The top source for information about Internet security were from forums and fellow gamers.
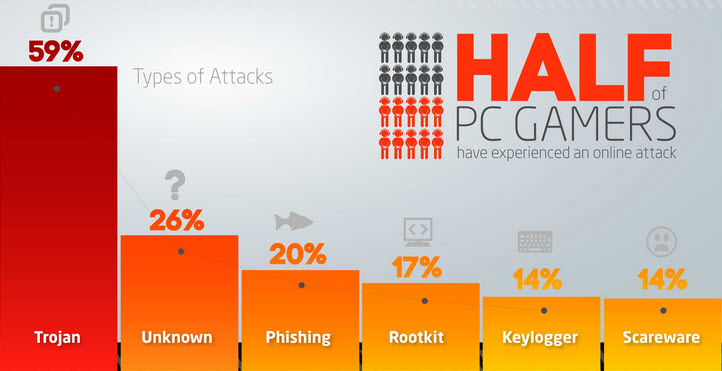
The survey was conducted during E3 2014 and was based on the responses gathered from over 1,200 PC gamers. The conclusion was that one third of PC gamers do not use a security program while gaming, although 47% have experienced a malware or phishing attack.
“We understand the high expectations that gamers have of their systems, and the frustration they have had with traditional antivirus programs. But the desire for performance can’t be at the expense of protection – there’s too much to lose,” said Mike Malloy, executive vice president of products and strategy at Webroot. “We believe by following some basic best practices and using a cloud-based security program that is very light on system resources, such as Webroot SecureAnywhere Gamer Edition, PC users don’t have to choose between performance and protection.”
Running a gaming system without traditional antivirus security can improve gameplay performance, but it leaves gamers vulnerable to identity theft and online attacks that can jeopardize both their real and in-game lives. This is why Webroot created the first cloud-based antivirus for PC gamers and developed a list of tips for staying safe online.
Tips for Gaming Securely:
- Use browser-based URL filtering.
- Deploy anti-phishing detection.
- Avoid public Wi-Fi and use a cloud-based anti-malware program.
To read the full press release, please click here.
If you’d like to view or download the infographic on the report, you can do so by clicking here.
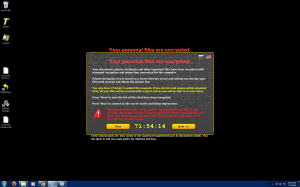
Critroni/Onion – Newest Addition to Encrypting Ransomware
In my last blog post about a week ago, I talked about how Cryptolocker and the like are not dead and we will continue to see more of them in action. It’s a successful “business model” and I don’t see it going away anytime soon. Not even a few days after my post a new encrypting ransomware emerged. This one even targets Russians!
Presenting Critroni (aka. Onion)
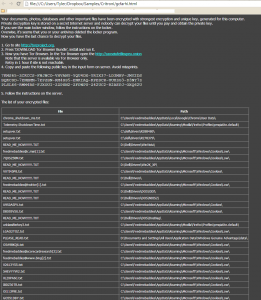
This newest edition of encrypting ransomware uses the same tactics of contemporary variants including: paying through anonymous tor, using Bitcoin as the currency, changing the background, dropping instructions in common directories on how to pay the scam. Some upgrades that are new to the encrypting ransomware scene are logging the entire directory list of files that were encrypted. They store this list in your documents folder for your convenience come decryption time (how nice of them).
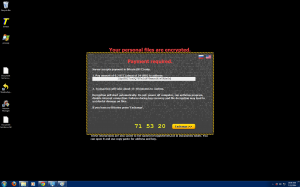
The ransom amount scales with how many files are encrypted. My specific encryption only wanted “.2 Bitcoin (about 24USD)” Please note that the exchange rate displayed by the malware is extremely wrong and .2 Bitcoin is about $120.
This specific variant we analyzed does not delete the VSS (Volume Shadow Service) and you can get all your files back by using programs like Shadow Explorer. I expect that once this malware goes into widespread distribution for the US and UK that “issues” like this will get fixed and the price will rise to around .5 BTC (around $300) on average. Webroot will catch this specific variant in real time before any encryption takes place. We’re always on the look out for more, but just in case of new zero day variants – remember that with encrypting ransomware the best protection is going to be a good backup solution. This can be either through the cloud or offline external storage. Keeping it up to date is key so as not to lose productivity. Webroot has backup features built into our product that allow you to have directories constantly synced to the cloud. If you were to get infected by a zero day variant of encrypting ransomware you can just restore your files back as we save a snapshot history for each of your files up to ten previous copies.
Please note there are variations in the naming of this file, including Onion and Critroni.A.
Cryptolocker is not dead
Recently in the news the FBI filed a status report updating on the court-authorized measures to neutralize GameOver Zeus and Cryptolocker. While the report states that “all or nearly all” of the active computers infected with GameOver Zeus have been liberated from the criminals’ control, they also stated that Cryptolocker is “effectively non-functional and unable to encrypt newly infected computers.” Their reasoning for this is that Cryptolocker has been neutralized by the disruption and cannot communicate with the command and control servers to receive instructions or send RSA keys after encryption. Read more here
While seizing the majority of the GameOver Zeus Botnets from the suspected “mastermind” Evgeniy Bogachev was a big impact to the number of computers infected with GameOver Zeus – about a 31 percent decrease, it’s a very bold claim to state that Cryptolocker has been “neutralized”. The reason why this claim should be scrutinized is because it is only the samples dropped on victims computers that communicated to those specific servers seized that are no longer a threat. All samples currently being deployed by different botnets that communicate to different command and control servers are unaffected by this siege – the majority of encrypting ransomware. Although Evgeniy Bogachev and his group had control of a major chunk of zeus botnets and command and control servers that deployed cryptolocker, it was certainly not all or even the majority of zeus botnets in existence. Most malware authors spread their samples through botnets that they either accumulated themselves (Evgeniy), or just rent time on a botnet from someone like Evgeniy (most common). So now that Evgeniy’s servers are seized, malware authors are just going to rent from some of the many other botnets out there that are still for lease.
Here are some pictures of samples that we’ve encountered that are still hard at work at infecting users.
All of these work in almost exactly the same way as the infamous traditional cryptolocker we’ve all seen, but they have some improvements. First is that there is no GUI and instead just background changes and texts instructions in every directory that was encrypted. Second is that you no longer pay using a moneypak key in the GUI, but instead you have to install tor or another layered encryption browser to pay them securely and directly. This allows malware authors to skip money mules and increase the percent of profits. The best way to stay protected by attacks like this is to utilize backups to either the cloud or offline external storage. Webroot has backup features built into our product that allow you to have directories constantly synced to the cloud. If you were to get infected by a zero day variant of encrypting ransomware you can just restore your files back as we save a snapshot history for each of your files up to ten previous copies.
So while this is a great win on behalf of the FBI, it’s very bold to claim that cryptolocker is now dead. A better way to put it would be that Evgeniy M. Bogachev’s brand of cryptolocker and anyone who purchased time on his botnet is now useless.
New Study Reveals Disparities Between Corporate Mobile Security Policies and BYOD Practice

In the new BYOD Security Report conducted by Webroot through first-of-its-kind research, Webroot examined the use and security of personal mobile devices in the work environment, looking at the prevalence of employee-owned devices. The initial survey, conducted in late 2013, explored the prevalence of employee-owned devices, how they are being secured, and employee concerns regarding company-mandated security programs. The second survey, conducted in March 2014, looked at how IT managers view the risk of employee-owned devices, the prevalence of formal mobile security policies, and the extent to which employee input is included in developing BYOD policies.
Pulling from that report are some interesting key facts and findings, including:
- Although 98% of employers have a security policy in place for mobile access to corporate data, 21% allow employee access with no security at all.
- Over 60% of IT managers surveyed reported the use of personal devices by their employees and 58% indicated they were ‘very’ or ‘extremely’ concerned about the security risk from this practice.
- Most employee devices are lacking real security with only 19% installing a full security app and 64% of employees limited to using only the security features that came with their devices.
- Over 60% of employers indicated they seek employee input on mobile device security policies, but over 60% also said employee preference has little or no influence on mobile security decisions.
- Top concerns from employees regarding a company-mandated security app include employer access to personal data, personal data being wiped by an employer, and employers tracking the location of the device. Other concerns included impact on device performance and battery consumption.
- 46% of employees using personal devices said they would stop using their devices for business purposes if their employer mandated installation of a specific security app.
All in all, the report shows that there are striking signs that many employers and employees do not take necessary steps to ensure the protection of the corporate data on their personal devices. While this is a weakness in the systems now, tools such as Webroot Business Endpoint Protection and SecureAnywhere Business Mobile Protection do exist to help implement security policies, and when paired with new, forward-thinking BYOD policies, can prove to be effective in keeping the corporate data secure.
A successful Gartner Summit for Webroot
 Webroot, the market leader in cloud-based, real-time Internet threat detection, recently returned from the 20th annual Gartner Security and Risk Management Summit in National Harbor, Maryland. Attended by many of the world’s top business and IT professionals in industries ranging from finance to information technology to government, the focus of this year’s conference was enablement of an organization to move forward towards its objectives, while ensuring security and protection. The show’s theme at this year’s conference, “Smart Risk: Balancing Security and Opportunity”, summarized the challenges that many large companies are experiencing today, as they work to ensure the safeguarding of their information without slowing down the company’s productivity.
Webroot, the market leader in cloud-based, real-time Internet threat detection, recently returned from the 20th annual Gartner Security and Risk Management Summit in National Harbor, Maryland. Attended by many of the world’s top business and IT professionals in industries ranging from finance to information technology to government, the focus of this year’s conference was enablement of an organization to move forward towards its objectives, while ensuring security and protection. The show’s theme at this year’s conference, “Smart Risk: Balancing Security and Opportunity”, summarized the challenges that many large companies are experiencing today, as they work to ensure the safeguarding of their information without slowing down the company’s productivity.
As a ‘Premier Sponsor’, Webroot attended the Gartner Summit to introduce the next generation threat intelligence services for enterprises, BrightCloud Security Services for Enterprise, which collects and analyzes threat intelligence across multiple vectors – IP, URL, File and Application – from a massive network of nearly 35 million users protected by Webroot endpoint security solutions as well as Webroot technology partners. The team was also on-hand to demonstrate Webroot SecureAnywhere Business-Endpoint Protection, which recently was updated with enhanced management capabilities to help protect large, complex network environments.
With a busy booth during the three days of exhibit time, there was a great deal of interest in Webroot’s Threat Intelligence Server and BrightCloud Services as well as the SecureAnywhere Endpoint Protection solution. The solutions that were introduced aligned well with two key areas that the security community is interested in – namely finding better protection for their endpoints and using external threat intelligence to make their current devices smarter and optimized for more rapid incident response – as well as fitting in with the conference’s overall theme.
While at the event, Webroot was also part of various security discussions and presentations, including two sessions where CISO’s talked endpoint protection and threat intelligence. Webroot’s Dave Dufour and Chip Witt both presented on real-time intelligence gathering, and Webroot CTO Hal Lonas presented on the difference between threat data and threat intelligence. Mike Malloy, VP of Products and Strategy, also gave a talk on ‘the death of traditional antivirus’, a theme that forms the foundation of the Webroot security product lineup.
Thanks largely to a combination of a strong security-focused presence as well as a seamless merging of security goals between attendees and Webroot’s product offerings, the company’s presence at this year’s 2014 Gartner Security and Risk Management Summit was a major success. Webroot is already planning on similar attendance at the coming Japanese and APAC Gartner summits to continue to drive the momentum forward.
A peek inside the online romance scam.
 Online dating can be rough, and no matter how many safeguards are in place in the multiple legitimate dating websites out there, the scammers are getting around the blocks and still luring in potential victims. While the reports of these types of scams are out there (even with copy and paste examples of the e-mails used), people still fall for the scams every day. In this particular case, it was my profile on eHarmony that was targeted, and this is my recount of it.
Online dating can be rough, and no matter how many safeguards are in place in the multiple legitimate dating websites out there, the scammers are getting around the blocks and still luring in potential victims. While the reports of these types of scams are out there (even with copy and paste examples of the e-mails used), people still fall for the scams every day. In this particular case, it was my profile on eHarmony that was targeted, and this is my recount of it.
It started with a potential match; a profile with a collection of tasteful photos of a beautiful woman, not too ‘out there’, but a face that stood out from the crowd. The profile was fairly complete, with a few of the smaller-scale questions not answered. Overall, the profile initially raised no suspicion for me. So, I started the song and dance that is the eHarmony way, and back and forth we went with questions and such. That is, until the last stage when the match sent over a cryptic message of not being able to communicate via the system and that I should e-mail her. And up went the red flag.
Now, most systems out there allow communication up to a certain point, and in this case, eHarmony was on a free communication week, and even if it hadn’t been, we had not reached that final ‘free’ part yet. Assuming that many of the companies have basic language and text scanned in their internal mail systems, it can be supposed that the person on the other end was avoiding being flagged.
So with this e-mail in hand (my inbox), I decided to see how far this rabbit hole went. Using a non-personal e-mail address that I setup for mailing lists, I contacted my match with a basic re-introduction and waited. A few hours later, I received back an incredibly long, detailed e-mail with a few photos attached. The e-mail was not well written, and the local geographic locations mentioned in it did not make sense in the description. At this point, I was 100% sure it was a scam and decided to reverse image search the photos, which lead me to a model out of Australia, and then searched the generic line of text to find over 78,000 results showing almost exact copies of the e-mail I had received.
A quick reply back lead to an even longer response from the scammer, again using photos from the model’s profile page and the same content found on many scam reporting websites. But this time, I was being asked for money, as ‘she’ was stuck in London, unable to get home. Conveniently, there was already a bank account setup for me to transfer money. At this point, I had what I needed for this write-up, and so I marked the account as ‘spam’ and reported the profile to the eHarmony team.
So what can we learn from this little experience? Well, a few things. Despite the safeguards in place to help protect those looking for a relationship online, the protection is not perfect, and users need to be educated. Here are a few tips for you to help spot a potential scammer:
- Claims of being from the United States but currently visiting overseas
- Making claims of wanting to fly back to meet, but unable to do so because of work or a tragic incident.
- Wanting to leave a dating site immediately and use personal e-mail addresses to communicate.
- Irregular use of the English language, improper use of slang, and over punctuation.
- Hinting at or asking for money to help secure travel back ‘home’
- Professionally taken photographs that look straight-out of a runway magazine
Remember, you will never know who is on the other side of that screen until you meet them. Use safe and cautious measures, never give out personal information, and be aware of the tricks being used on the digital daters of today.
A peek inside a commercially available Android-based botnet for hire
Relying on the systematic release of DIY (do-it-yourself) mobile malware generating tools, commercial availability of mobile malware releases intersecting with the efficient exploitation of legitimate Web sites through fraudulent underground traffic exchanges, as well as the utilization of cybercrime-friendly affiliate based revenue sharing schemes, cybercriminals continue capitalizing on the ever-growing Android mobile market segment for the purpose of achieving a positive ROI (return on investment) for their fraudulent activities.
We’ve recently spotted yet another underground market proposition offering access to Android-based infected devices. Let’s take a peek inside its Web-based command and control interface, discuss its features, as well as the proposition’s relevance within the cybercrime ecosystem.
More details:
Sample screenshots of the commercially available Android-based botnet for hire:
Spamvertised ‘Customer Daily Statement’ themed emails lead to malware
Cybercriminals continue to efficiently populate their botnets, through the systematic and persistent spamvertising of tens of thousands of fake emails, for the purpose of socially engineering gullible end users into executing the malicious attachments found in the rogue emails.
We’ve recently intercepted a currently circulating malicious campaign, impersonating Barkeley Futures Limited, tricking users into thinking that they’ve received a legitimate “Customer Daily Statement”.
Successful Launch of Webroot for Gamer at E3
 Webroot, the market leader in cloud-based, real-time Internet threat detection, recently returned from the 18th annual Electronic Entertainment Expo, or E3 for short, hosted by the Entertainment Software Association. Used by many of the video game manufacturers across the various platforms, as well as hardware and software developers, the trade show is used to show off the next generation of games-related products. Hosted at the Los Angeles Convention Center, the 2014 conference had over 50,000 reported attendees between June 9th and 12th, 2014.
Webroot, the market leader in cloud-based, real-time Internet threat detection, recently returned from the 18th annual Electronic Entertainment Expo, or E3 for short, hosted by the Entertainment Software Association. Used by many of the video game manufacturers across the various platforms, as well as hardware and software developers, the trade show is used to show off the next generation of games-related products. Hosted at the Los Angeles Convention Center, the 2014 conference had over 50,000 reported attendees between June 9th and 12th, 2014.
With this being Webroot’s first appearance at E3, the company was on site to show off Webroot’s new gaming specific antivirus, SecureAnywhere™ AntiVirus for PC Gamers. Designed to keep users protected with maximum performance and protection, the newest protection offering for consumers garnered a large amount of interest from those in attendance, with a busy booth all day. From the gamers themselves to the industry experts, many were impressed with the performance, speed, and direct gaming focus that Webroot was providing with the gamer protection product.
Along with the booth presence, Webroot’s team hosted an online campaign to drive awareness of the products with the #CyborgSelfie giveaway, a contest where entrants had to submit a selfie of themselves with the specific Twitter hashtag in hopes of winning a custom built Origin PC protected by Webroot. With over 40,000 entries, the winner, Johnny Interiano, was drawn at random, and will soon have one of the most powerful Origin PC machines at their disposal for their next gaming conquests. And to not pass an opportunity to work with Webroot’s newest partner Plantronics, twelve runner-up winners from the same contest won Plantronics RIG gaming headsets.
Through a strong awareness campaign and booth presence, all backed by an innovative security product designed specifically for gamers, Webroot’s presence at E3 was a major success for all that were involved.
Spamvertised ‘June invoice” themed emails lead to malware
Cybercriminals continue spamvertising tens of thousands of malicious emails on their way to socially engineer gullible end users, ultimately increasing their botnet’s infected population through the systematic and persistent rotation of popular brands.
We’ve recently intercepted a currently circulating malicious campaign enticing users into executing the fake attachment.
More details:
Malicious Web-based Java applet generating tool spotted in the wild
Despite the prevalence of Web based client-side exploitation tools as the cybercrime ecosystem’s primary infection vector, in a series of blog posts, we’ve been emphasizing on the emergence of managed/hosted/DIY malicious Java applet generating tools/platforms, highlighting the existence of a growing market segment relying on ‘visual social engineering’ vectors for the purpose of tricking end users into executing malicious/rogue/fake Java applets, ultimately joining a cybercriminal’s botnet.
We’ve recently spotted yet another Web based Java drive-by generating tool, and decided to take a peek inside the malicious infrastructure supporting it. read more…
Webroot returns from Automation Nation 2014
 Webroot, the market leader in cloud-based, real-time Internet threat detection, recently returned from the fifth annual Automation Nation in Orlando, hosted by LabTech Software. Labtech, a robust remote monitoring and management (RMM) platform design and built for managed service providers, hosted the event at the Hilton Bonnet Creek from June 2nd through the 4th. Hosting over 425 MSP partners and 600 attendees, the event has grown significantly since the previous years. This was Webroot’s first time attending the conference, coming in as a Diamond Sponsor.
Webroot, the market leader in cloud-based, real-time Internet threat detection, recently returned from the fifth annual Automation Nation in Orlando, hosted by LabTech Software. Labtech, a robust remote monitoring and management (RMM) platform design and built for managed service providers, hosted the event at the Hilton Bonnet Creek from June 2nd through the 4th. Hosting over 425 MSP partners and 600 attendees, the event has grown significantly since the previous years. This was Webroot’s first time attending the conference, coming in as a Diamond Sponsor.
Kicking off the event, Webroot CMO David Duncan helped present during the keynote with the support of Andrew Bagnato, a system engineer for Webroot. Speaking on how security doesn’t have to suck, and that with the integration into LabTech and the advances in the Webroot Intelligence Network (WIN), MSPs had the opportunity to not only manage their clients remotely, but ensure they are protected as well.
Talking about the Webroot Partner Program and the security solutions offered, the onsite team showed that the solutions provided just work, can drive profits, and ultimately don’t suck. With pigs flying left and right, over hear and over there, it was not long until the booth was filled to capacity with partners wanting to learn about the intelligent cloud-based security solutions. Also shown were demos of LabTech Software integration, which was designed to bring the tools of the Webroot console direct to the MSP’s most used console, saving time in the monitoring of Webroot protected endpoints.
While at the conference, Andrew Bagnato also hosted a breakout session presenting on the next generation of anti-malware, packing the room beyond capacity. Showing how legacy solutions were not keeping up with the new tricks of incoming threats, Andrew presented on the power of the Webroot Intelligence Network and just how it can help protect endpoints across all the networks from even the most advanced threats.
With the event going non-stop for 3 days, the team is glad to have some rest, but excited to have introduced the security offerings to the LabTech partners.