It’s that magical time of year for all technically minded folks: sysadmins, IT pros, nerds and gamers. It’s that time where you get to go home to family, gather around the fire, and fix their computers.
That’s right; it’s not about the turkey or the giving of presents, it’s about cleaning toolbars off grandma’s computer.
For those of you who go through this annual ritual, here’s a few things to make the process easier for everyone:
- Facelift: SSD, memory, larger screen. One of the cheapest ways to give aging hardware a boost is getting easier every day. SSD prices are bombing like your boss’s jokes at the holiday party, RAM has been cheap for a while, and bigger screens are always cheap around the holidays. Replacing an HDD with an SSD will make them think you gave them a whole new computer. For moving the boot drive, I recommend Paragon Software’s Migrate OS to SSD software: https://www.paragon-software.com/technologies/components/migrate-OS-to-SSD/ That way you don’t have to do a fresh install, and you can just leave the migration running while you eat dessert. Combine that with a USB to SATA cable: http://www.amazon.com/gp/product/B00HJZJI84 and you only have to open up the case once to swap the drive out after the migration is complete. While the case is open, slap in some extra RAM so that when Chrome tabs gobble up all the memory their computer doesn’t grind to a halt. And finally those aging eyes will benefit from the jump to a larger screen. 27 inches seems to be the pricing sweet spot lately. And you can take home the replaced screens to use as second, third, fourth and fifth monitors for yourself while playing Fallout 4.
- Auto-reset the internet. How tired are you of asking people if they’ve tried turning it off and on again? For one aspect you can now automate the process. They make plugs that detect when the Internet connection goes down that automatically power cycle the cable modem and/or router: http://www.amazon.com/PI-Manufacturing-Internet-Controllable-Automatic/dp/B006PPISCG That will save you from having to explain to your parents which device they have to try turning off and on again when the Internet goes out.
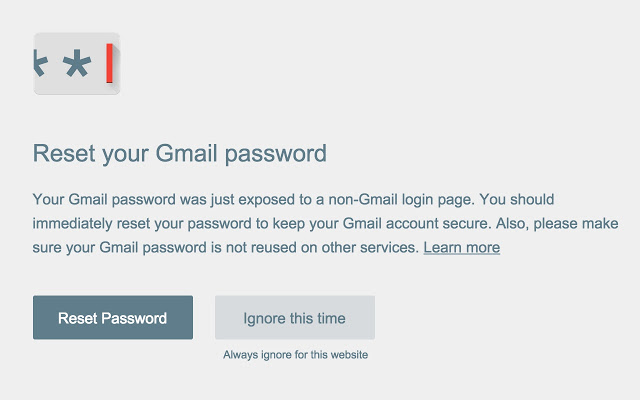
- Setup easier remote access – Have you ever had this conversation: “Go to the address bar. That thing at the top. Type in: H-T-T-P-colon-slash – the one that leans to the right, not the left, now another slash. Yes the same direction as the last one. Now L-O-G. No, G as in Get a clue…” You get the picture. While you’re home, why not setup a shortcut on the desktop that goes directly to your preferred remote support website? That way grandma knows what to click on when you have to remote in to uninstall the latest toolbar she installed.
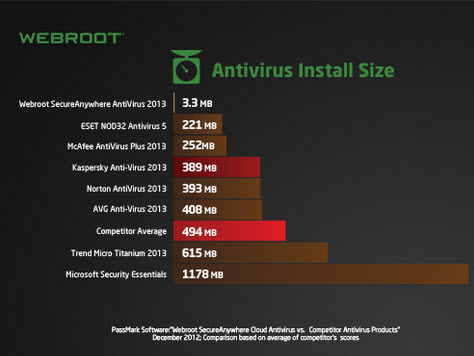
- Install antivirus that allows central management – obviously I’m going to recommend Webroot: https://www.webroot.com/us/en/home But no matter what you choose, it’s nice to have something that has a central online console. This allows you to see whether mom’s computer has run a scan in the last decade and how many viruses your younger brother managed to catch while visiting those sites he likes to go to. With Webroot you can also kick off scans and reboots from anywhere you can get online.
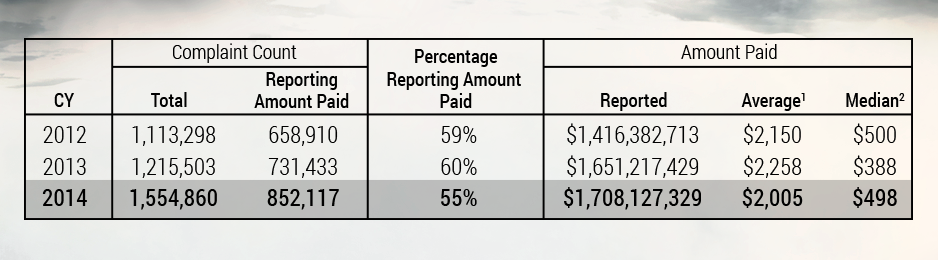
- Protect their credit – everyone’s had their information stolen at this point so you might as well put a freeze on your credit. Mom and dad probably aren’t getting a lot of loans these days therefore this won’t be a big inconvenience for them. Here’s how to go about it: http://www.consumer.ftc.gov/articles/0497-credit-freeze-faqs This just means they’ll need to call in and unfreeze with their password before they get any more lines of credit, and it will stop the bad guys from taking out loans in their name. Because face it, they already have all of your personal information. Protect your inheritance.
- Install an ad blocker and privacy protection – ads are a huge vector for malware these days. I like uBlock Origin to stop ads and Privacy Badger to stop companies following you around the web with tracking cookies. Put those browser extensions in place and teach mom and dad how to turn them on or off for individual sites for when they break core functionality.
- Get them on a better browser – if they’re still using Internet Explorer then you should be ashamed of yourself. Protip: change the existing IE icon on the desktop to open up Chrome or Firefox instead, so they don’t have to learn to click on anything new.
- Power protection – get some cheap UPS and surge protection so that any desktop devices & cable modems won’t go haywire if the power blips: http://www.amazon.com/Eaton-Electrical-3S350-External-UPS/dp/B00906CH8S
- Setup online backup – I like Backblaze: https://www.backblaze.com/ $5 a month for unlimited storage on each computer. Now your baby pictures aren’t in danger of going up in a puff of magic smoke. Restores are easy and you get email reports letting you know that the backups are successful.
- Get better wireless – Ubiquiti has awesome and affordable prosumer APs that will give you a signal from two streets over: http://www.amazon.com/Ubiquiti-Networks-Enterprise-Unifi-UAP/dp/B00HXT8R2O No longer will the neighbor’s Wifi interfere. I use one to cover an entire three-story house from top to bottom.
- Connect the house with powerline Ethernet – save the wireless for devices that move. For anything static, from streaming devices on your TV to media servers, wired is the way to go. Powerline Ethernet is now rock solid and you can turn your whole house into a hub by plugging these into any outlet: http://www.amazon.com/TP-LINK-TL-PA4010KIT-Powerline-Adapter-Starter/dp/B00AWRUICG No running cables throughout the house required.
- Stop bundleware – next time dad installs an update, you don’t have to worry about uninstalling a toolbar with this one simple trick: http://unchecky.com/ This software automatically unchecks the bundleware checkboxes so that you don’t have to use a cattle prod to train family to uncheck anything.
- Install a password manager – anything to get people to use good passwords without having to teach their aging brains to remember anything new. If you use an online password manager, then you can automatically change their passwords and update the password manager for them whenever there’s a report of a breach on a site your family uses.
- Follow Swift on Security on Twitter. A parody account that is both funny and useful. Taylor Swift’s Infosec alter ego will keep you up-to-date on the latest security news and breaches, all while serenading you with the latest hits: https://twitter.com/swiftonsecurity/
Hopefully this list will help you get through the holidays at home without having to resort to hiding in the basement. Make a few of these changes and it should make the next year of family tech support that much easier. May the force help you live long and prosper.