“What’s an evasive attack? At a very basic level, it’s exactly what it sounds like; it’s a cyberattack that’s designed to hide from you,” says Grayson Milbourne, Security Intelligence Director at Webroot, an OpenText company.
Based on Grayson’s initial explanation, you can imagine that evasive tactics are pretty common throughout cybercriminal activities. But they’re especially prevalent in the context of scripts. Scripts are pieces of code that can automate processes on a computer system. They have tons of legitimate uses, but, when used maliciously, they can be extremely effective and difficult to detect or block.
With Grayson’s help, we’ll talk you through some of the common script evasion techniques that criminals use.
LolBins
Living off the Land Binaries (“LoLBins”) are applications that a Windows® system already has on it by default. Funny name aside, they’re extremely useful for attackers because they provide a way to carry out common steps of an attack without having to download anything new onto the target system. For example, criminals can use them to create persistency (i.e. enable the infection to continue operating after a reboot), spread throughout networked devices, bypass user access controls, and extracting passwords or other sensitive information.
There are dozens of LoLBins for criminals to choose from that are native to the Windows OS, such as powershell.exe, certutil.exe, regsr32.exe, and many more. Additionally, there are a variety of common third party applications that are pretty easy to exploit if present, such as java.exe, winword.exe, and excel.exe.
According to Grayson, this is one of the ways malicious hackers disguise their activities, because default OS applications are unlikely to be detected or blocked by an antimalware solution. He warns, “unless you have strong visibility into the exact commands that these processes are executing, then it can be very hard to detect malicious behavior originating from LoLBins.
Script Content Obfuscation
Like LoLBins and scripting overall, hiding the true content or behavior of a script—or content “obfuscation”—has completely legitimate purposes. But, in terms of malicious hacking, it’s pretty self-explanatory why obfuscation would lend itself to criminal activities. The whole point is not to get caught, right? So it makes sense that you’d take steps to hide bad activities to avoid detection. The screenshots below show an example of obfuscated code (top), with its de-obfuscated version (bottom).
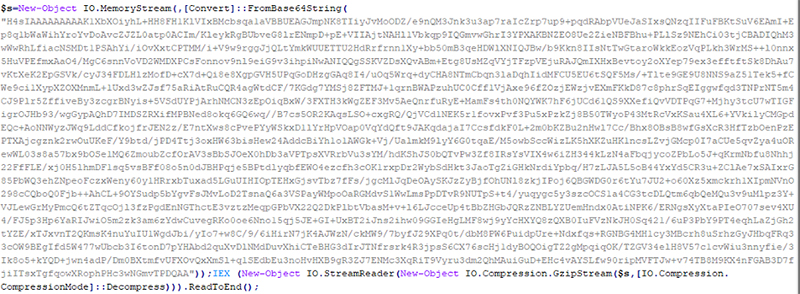
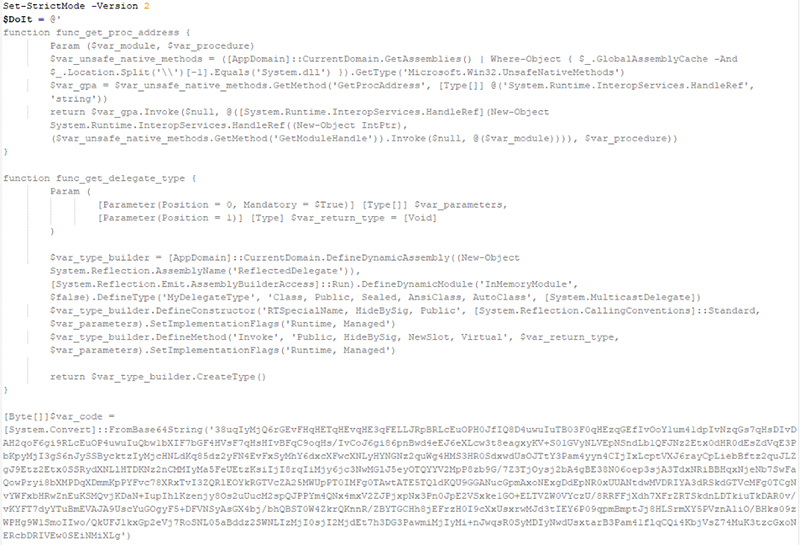
Fileless and Evasive Execution
Using scripts, it’s actually possible to execute actions on a system without needing a file. Basically, a script can be written to allocate memory on the system, then write shellcode to that memory, then pass control to that memory. That means the malicious functions are carried out in memory, without a file, which makes detecting the origin of the infection (not to mention stopping it) extremely difficult.
Grayson explains, “one of the issues with fileless execution is that, usually, the memory gets cleared when you reboot your computer. That means a fileless infection’s execution could be stopped just be restarting the system. Persistence after a reboot is pretty top-of-mind for cybercriminals, and they’re always working on new methods to do it.”
Staying Protected
The Windows® 10 operating system now includes Microsoft’s Anti-Malware Scan Interface (AMSI) to help combat the growing use of malicious and obfuscated scripts. That means one of the first things you can do to help keep yourself safe is to ensure any Windows devices you own are on the most up-to-date OS version.
Additionally, there are several other easy steps that can help ensure an effective and resilient cybersecurity strategy.
- Keep
all applications up to date
Check all Windows and third party apps regularly for updates (and actually run them) to decrease the risk of having outdated software that contains vulnerabilities criminals could exploit. - Disable
macros and script interpreters
Although enabling macros has legitimate applications, the average home or business user is unlikely to need them. If a file you’ve downloaded gives you a warning that you need to enable macros, DON’T. This is another common evasive tactic that cybercriminals use to get malware onto your system. IT admins should ensure macros and script interpreters are fully disabled to help prevent script-based attacks. You can do this relatively easily through Group Policy. - Remove
unused 3rd party apps
Applications such as Python and Java are often unnecessary. If present and unused, simply remove them to help close a number of potential security gaps. - Educate
end users
End users continue to be a business’ greatest vulnerability. Cybercriminals specifically design attacks to take advantage of their trust, naiveté, fear, and general lack of technical or security expertise. By educating end users on the risks, how to avoid them, and when and how to report them to IT personnel, businesses can drastically improve their overall security posture. - Use
endpoint security that includes evasive script protection
In a recent update to Webroot® Business Endpoint Protection, we released a new Evasion Shield policy. This shield leverages AMSI, as well as new, proprietary, patented detection capabilities to detect, block, and quarantine evasive script attacks, including file-based, fileless, obfuscated, and encrypted threats. It also works to prevent malicious behaviors from executing in PowerShell, JavaScript, and VBScript files, which are often used to launch evasive attacks
Malicious hackers are always looking to come up with new ways to outsmart defenses. Grayson reminds us, “It’s up to all of us in cybersecurity to research these new tactics and innovate just as quickly, to help keep today’s businesses and home users safe from tomorrow’s threats. There’s always more work to be done, and that’s a big part of what drives us here at Webroot.”
To learn more about evasive scripts and what Webroot is doing to combat them,
we recommend the following resources: